Month: April 2022
Not Your Average Bug Bounty: How an Email, a Shirt, and a Sticker Compromised a High Security Datacenter
Recent Posts
Forbes: Beyond Bitcoin: Understanding Blockchain Security Implications
On April 27, 2022, NetSPI CTO Travis Hoyt published an article in the Forbes Technology Council called Beyond Bitcoin: Understanding Blockchain Security Implications. Preview the article below, or read the full article online.
+++
The blockchain market is expected to grow 68.4% over the next four years, with 86% of senior executives believing blockchain will become a mainstream-adopted technology. While the majority of the world has been fixated on various cryptocurrencies – including bitcoin, ethereum and the emerging non-fungible token (NFT) market – organizations have adopted blockchain technology behind the scenes. To do this, the right education and implementation strategies are needed because without proper implementation strategies factoring in architectural nuances, organizations are opening their business up to security risks.
There are a handful of blockchain deployment models: private (or internal), permissioned/consortium and public. While they all possess some common traits, each has its own nuances when it comes to its use and associated security risks.
Private (Or Internal) Deployment
Blockchains on a private network are generally isolated but are intended to solve internal operational efficiency problems. They offer an alternative data plane to traditional database architectures, with smart contracts serving as stored procedures.
Private networks are quicker than other deployment models—largely because all of the infrastructure is within the four walls of the organization –– but most importantly because the consensus model doesn’t require trustless verification that public chains do. When deployed internally, processes become more efficient, so the steps to protect business assets are more controlled. We see this specifically with an organization’s internal supply chain—the blockchain enables a faster and more cost-efficient delivery of services.
The organization that controls the blockchains can set permission requirements and implement its own security precautions. By controlling which users can view, add or change data within the blockchain, private information is protected from third parties.
Alternatively, private blockchains are potentially more vulnerable to fraud, so organizations must understand the interworking of the network in order to patch a vulnerability effectively. If a malicious insider or cyberattack presents itself, the steps to mitigate are essentially the same as with any other cyberthreat: conduct risk assessments, have penetration testing in place to identify security gaps and build a threat detection and response plan. Organizations that have neglected to address blockchain acumen gaps in their IT and cyber resources may find their response playbooks aren’t completely meeting their needs.
Read the full article online.
Recent Posts
Getting Started as a Pentester: Cybersecurity Career Q&A
At NetSPI, we invest heavily in our processes and technology to continuously perform high-quality penetration testing services for our clients. But ask any of our clients and they’ll tell you that the greatest quality that sets NetSPI apart from other pentesting vendors is our people – arguably the greatest and most important investment we can make.
It’s no secret that the cybersecurity and technology industry is experiencing 0% unemployment rates. And the competition is fierce for qualified talent that is not only technical but also understands the implications of cybersecurity.
Case-in-point: NetSPI recently attended the Secure World Boston cybersecurity event. In one session, the presenter asked the room of more than 50 CISOs and other security leaders to raise their hand if they had open cybersecurity positions that they were struggling to fill. Nearly every single hand went up in the room.
One way NetSPI is investing and bringing in new and qualified talent is the NetSPI University (NetSPI U) program. This penetration testing training program is specifically for entry-level talent looking to begin their career in cybersecurity.
Since its inception in 2018, 83% of all NetSPI U “graduates” have continued their careers at NetSPI today – many of which are now in leadership positions.
This competitive training program is available in Minneapolis, Portland (OR), Lehi, and Pune. You join as an Associate Security Consultant (or remote depending on the situation) and receive hands-on penetration testing training focused on NetSPI’s proven testing methodology. Not to mention the competitive benefits and opportunities to be mentored by some of the best talent in cybersecurity. [To view our open pentesting jobs, visit our careers page]
To share a first-hand perspective on what it’s like to become a pentester, in this blog, we asked four NetSPI U alumni to share their experiences getting into and working in the pentesting industry.
What did you wish you knew before you transitioned into cybersecurity?
Karin Knapp, Security Consultant (NetSPI U Class of 2021):
“I wish I had known more about a career in cybersecurity while in school. With limited experience in cybersecurity before I applied to NetSPI U, I wish I had taken more electives that would’ve been more applicable to my current role instead of what I thought I wanted to do before I graduated.”
Matt Ostrom, Managing Consultant (NetSPI U Class of 2018):
“Pentesting is a team job. There is no room, nor should there be room for ‘rockstars’.”
Marissa Allen, Security Consultant II (NetSPI U Class of 2020):
“I wish I had known more certainly what cybersecurity career path I wanted to take. Everything is interesting, and it can take a while to narrow down your interests in the field given there are so many paths you can take.”
Sam Horvath, Technical Client Director (NetSPI U Class of 2018):
“Ignorance is bliss – once you know how insecure most systems are, you’ll be perpetually ‘paranoid’ to some degree.”
What is one piece of advice you’d give to someone who wants to get started in pentesting?
Karin:
“Take a look at websites designed to help you practice your pentesting skills like PortSwigger, HacktheBox, or TryHackMe. These are great ways to familiarize yourself with the basics of pentesting with hands-on, guided practice.”
Matt:
“Start gathering knowledge however you can. Whether that be through reading books or blogs, setting up your home lab of virtual machines – in a cloud environment or something like VirtualBox – testing vulnerable web applications, etc. Every little bit helps.”
Marissa:
“I think the best advice I can give is don’t be afraid to ask questions. There is a ton of information out there, and it can be difficult to sort through. There are many great sites that you can learn new skills from and people that will be willing to guide you if you reach out.”
Sam:
“Start meditating and/or doing intense cardio daily. Being able to put your brain in a calm space at the end of the day after exhausting your critical thinking/problem-solving centers is the key to rejuvenation and rest.”
What characteristics make a great pentester? Why?
Karin:
“Having a passion to always want to learn more about cybersecurity and pentesting is probably the best characteristic in my opinion. The ability to get creative and think outside of the box, and to not give up on difficult problems is also super valuable.”
Matt:
“First, someone who is determined to succeed. Sometimes, we’ll have to go through 99 different failures on exploiting a vulnerability before finding the one that works. Second, someone who loves learning. The cybersecurity industry is constantly changing and keeping pace with those changes is important. And lastly, someone who genuinely wants to make a difference. The work we do is incredibly important, and I feel like our work matters in keeping our clients safe.”
Marissa:
“If you like research, puzzles, and problem solving, then you’ve got this. You’ll come across areas in your penetration tests where you will need to dig into a problem. If you have an investigative personality, then you have the tenacity to go down the rabbit hole and find out if there is a vulnerability or not.”
Sam:
“Perseverance. Cracking the hardest problems and puzzles means you can’t get discouraged easily. 99% of people won’t get it on the first try, and that’s okay.”
What was the most rewarding/beneficial part of your NetSPI U experience?
Karin:
“I realized shortly before NetSPI U that I wanted a career in cybersecurity, but I thought I would have to go back to school to be able to get a job in the field. NetSPI U taught me everything that I needed to know and helped me build a solid foundation to be a successful pentester. In addition, I got to meet some awesome people such as those from my NetSPI U class and people who were my mentors in the program. They are the reason I look forward to coming into the office even a year after I ’graduated’.”
Matt:
“NetSPI U gives people the opportunity to break into the cybersecurity industry. The idea/concept of the NetSPI U program is a rarity. Being able to go from having a little bit of cybersecurity experience to feeling like I’m confident and ready to start executing on client projects after the program was, and continues to be, invaluable. Additionally, learning from people who have spent years in the industry was crucial. The depth of knowledge they were able to share during the program is the reason why it keeps succeeding and producing stellar pentesters.”
Marissa:
“NetSPI U gave me the knowledge and tools to succeed in my career. The program helps future pentesters succeed in that aspect by pairing them with a seasoned pentester as their mentor to provide guidance and answer any questions. It helped me better understand the breadth of work being performed. The program ultimately enabled me to figure out which direction I wanted to grow in my career.”
Sam:
“Learning that I had the ability and the drive to develop and succeed in the information security space was a validation of years of work in learning the basics of computer science. Finding a fantastic set of colleagues to learn, grow, and develop friendships within that process was just a bonus.”
The Future of Penetration Testing
A career in cybersecurity is a lucrative and rewarding one to get into in the foreseeable future. As cybercrime continues to be on the rise, companies will only continue to invest in services such as penetration testing. Becoming a pentester is not for the faint of heart, but if you have the perseverance to see a project to the end like how Karin, Matt, Marissa, and Sam described, penetration testing could be for you.
Want more information about NetSPI U?
Recent Posts
CSO: SolarWinds breach lawsuits: 6 takeaways for CISOs
On April 25, 2022, Nabil Hannan was featured in the CSO article, SolarWinds breach lawsuits: 6 takeaways for CISOs. Preview the article below, or read the full article online.
+ + +
The SolarWinds compromise of 2020 had a global impact and garnered the resources of both public and private sectors in an all-hands-on-deck remediation effort. The event also had a deleterious effect on the SolarWinds stock price. These two events, were, predictably, followed by a bevy of civil lawsuits. Fast forward to late March 2022 and we have a federal court saying the suit that named SolarWinds; its vice president of security and CISO, Tim Brown; as well as two prime investor groups Silver Lake and Thoma Bravo may go forward.
As Violet Sullivan, cybersecurity and privacy attorney of client engagement at Redpoint Cybersecurity, observes, the judge finds that the plaintiffs “may have a claim, so the judge is going to hear it.” She explains, “It’s not what is being said in the order that is interesting. It’s what will be shown during the discovery process that is interesting. There will be questions in this suit including: Will the forensic reports be available during the discovery or covered by attorney-client privilege?”
Resource Cybersecurity According to Risk
CISOs are uniquely positioned to provide insight on the threat landscape to business operations and together create the appropriate risk management plan. I recently mentioned how cybersecurity is often something companies get around to. The SolarWinds cyberattack and the resultant civil lawsuits are demonstrating the need for the well-documented investment in cybersecurity must be at the forefront.
The managing director of NetSPI, Nabil Hannan, says, “Internal threats are still a lingering and often under-addressed cybersecurity threat within organizations, especially when compared to the resources applied toward external threats. But, with buy-in from an organization’s leadership team, CISOs can have the resources needed to develop a proactive and ongoing threat detection governance program.”
Those who hesitate may find themselves playing catch up as they are spurred along by the new U.S. Securities and Exchange Commission initiative on the need for publicly sharing information security breach information within four days of discovery that the breach is material will affect direct change. Similarly, the SEC’s desire to have companies describe how they address cybersecurity will drive greater transparency within many companies. This SEC effort will pull infosec out of the back room and to the forefront, like policies, procedures, resourcing, and expertise will be on full display via the required SEC filings.
Recent Posts
Authority Magazine: Cyber Defense: Aaron Shilts of NetSPI On The 5 Things Every American Business Leader Should Do To Shield Themselves From A Cyberattack
On April 24, 2022, Aaron Shilts was featured in the Authority Magazine article, Cyber Defense: Aaron Shilts of NetSPI On The 5 Things Every American Business Leader Should Do To Shield Themselves From A Cyberattack. Preview the article below, or read the full article online.
+++
In our uncertain and turbulent world, cyberattacks on private businesses are sadly a common tactic of hostile foreign regimes as well as criminal gangs. Cyberattacks and ransomware have crippled large multinational organizations and even governments. What does every company need to do to protect itself from a cyberattack?
In this series called “5 Things Every American Business Leader Should Do To Shield Themselves From A Cyberattack” we are talking to cybersecurity experts and chief information security officers who can share insights from their experience, with all of us.
As a part of this series, I had the pleasure of interviewing Aaron Shilts, CEO of NetSPI.
As President and CEO of NetSPI with 20+ years of industry leadership, Aaron Shilts is known for his honest, open, and energizing leadership and his undeniable focus on corporate culture, collaboration, and business growth. Under Aaron’s leadership, NetSPI has experienced 35% and 50% Organic Revenue Growth in 2020 and 2021 respectively. In addition to his work at NetSPI, Aaron is the co-founder of “Change Starts With Me,” a Minneapolis non-profit, and advises several global firms. Aaron earned his B.S. from St. Cloud State University and proudly served in the Army National Guard.
Who has to be most concerned about a cyber attack? Is it primarily businesses or even private individuals?
In today’s evolving threat landscape where cybercriminals have become more sophisticated and motivated than ever before, cybersecurity is now everyone’s responsibility. In fact, the weakest link within any organization is typically its employees. Everyone working for, or with, the business should understand that security is everyone’s business — from the CEO down to the seasonal intern, and even the third-party contractor.
For this reason, organizations should implement frequent, hands-on security training, and regularly test the effectiveness of such training with simulated attacks to determine if more work needs to be done. After all, it only takes one accidental click on a malicious link to cripple an entire organization and its assets.
Read the full interview online.
Recent Posts
NetSPI CEO Aaron Shilts Featured on the CyberWire Daily Podcast
On April 14, 2022, NetSPI President and CEO, Aaron Shilts, was featured on the CyberWire Daily podcast. Listen to the interview (begins at 11:00) to hear Aaron’s insights on:
- Proactive public-private sector security collaboration
- How legislation like the Strengthening American Cybersecurity Act of 2022 enables the overall industry to be better at reporting cyberattacks
- The complexity of reporting cyberattacks while maintaining federal and state regulations
- Recommendations on building intentional relationships between organizations in the private and public sectors
Recent Posts
Abusing Azure Hybrid Workers for Privilege Escalation – Part 2: An Azure PrivEsc Story
The NetSPI team recently discovered a set of issues that allows any Azure user with the Subscription Reader role to dump saved credentials and certificates from Automation Accounts. In cases where Run As accounts were used, this allowed for a Reader to Contributor privilege escalation path.
This is part two of a two-part blog series. In part one, we walked through a privilege escalation scenario by abusing Azure hybrid workers. In this blog, we’ll dig a little deeper and explain how we utilized an undocumented internal API to poll information about the Automation Account (Runbooks, Credentials, Jobs).
Note: The scope of this bug is limited to a subscription. A subscription Reader account is necessary to exploit this bug, and it is not a cross-tenant issue.
Background: Azure Hybrid Worker Groups
The genesis of this research stemmed from studying any potential abuse mechanisms from how Azure Automation handled authenticating Hybrid Worker nodes.
Azure Automation’s core feature is Runbooks, which are pieces of code that can be run on Azure’s Infrastructure or customer-owned Azure Virtual Machines (VMs). These are often used to run scheduled tasks or manage Azure resources. To accomplish this, the runbooks must be authenticated, which can be accomplished through several methods.
Users can store credentials in Automation Accounts (AA) and access them via Runbooks. Automation Accounts can also use Run As accounts to create a Service Principal that will be used for authentication via a certificate stored in the Automation Account.
The third option is using Managed Identities, which is what Microsoft is pushing users towards. Managed Identities allow the user to obtain a token at runtime to authenticate and eliminate the issue of stored credentials. The Get-AzPasswords script from the MicroBurst project supports dumping all three kinds of authentication, so long as you have Contributor access.
Normally, a Runbook is executed in a sandbox on Azure’s infrastructure. However, this comes with certain constraints, namely processing power and execution time. Any long running or resource intensive code may be ill-suited to run in this manner.
To bridge this gap, Azure offers Hybrid Worker Groups (HWG). HWGs offer users the ability to run Runbooks on their own Azure Virtual Machines, so they can run on more powerful machines for longer.
Normally, this is accomplished by deploying a Virtual Machine Extension to the desired Virtual Machine to register the Virtual Machine as a HWG node. Then, the user can execute Runbooks on those Hybrid Worker nodes.
There are also two types of HWGs: User and System. System HWGs are used for Update Management and don’t have the necessary permissions for what we’re interested in, so we’ll be focusing on User HWGs.
The First Set of Issues: Compromising Credentials
We began our research with a registered Hybrid Worker node. When you execute a runbook on the host, the HybridWorkerService process spawns the Orchestrator.Sandbox process. The command line for the latter is as follows.
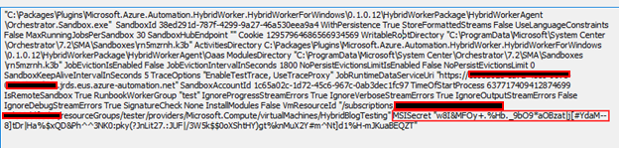
Next, we focused on MSISecret. At first glance, it appears that the Hybrid Worker node must be able to use this to request an MSI token externally. After reversing the binary, this turned out to be true.
Every Automation Account has a “Job Runtime Data Service” endpoint, or JRDS, which Hybrid Workers use to poll for jobs and request credentials. You can see the JRDS URL supplied in the command line above. Below is what the full path to request a token looks like in the binary.
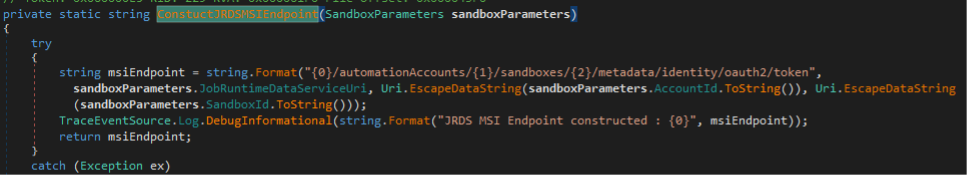
And here you can see this in action.
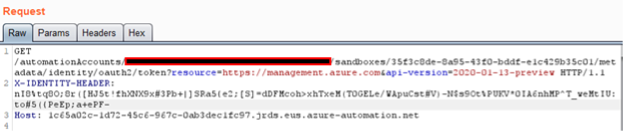
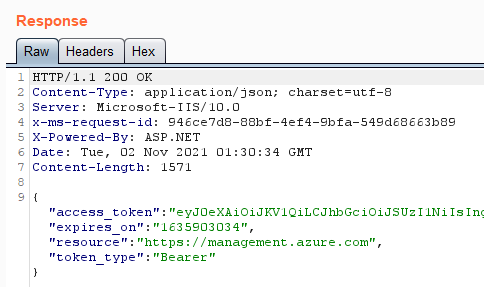
You can only get that MSI secret after receiving a job from the JRDS endpoint. This can be achieved by polling the /sandboxes endpoint. HWGs handle jobs in a first-come-first-serve fashion, so whichever node polls the endpoint first starts first. By default, nodes will poll every 60 seconds so if polled constantly, then we should almost always beat out the other nodes and get a job with a secret. However, this only works if Runbooks jobs are actively being run through the HWG.
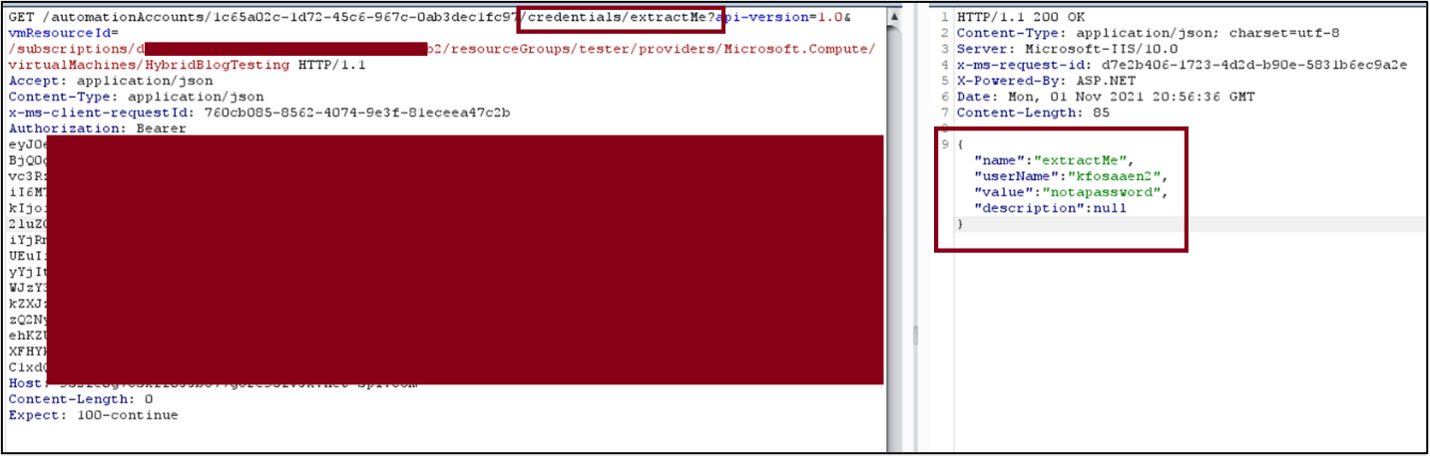
Since we’re able to request Managed Identity tokens, it would make sense that we can request other forms of authentication. A quick grep through of the decompiled binary makes this apparent, and a quick request to these endpoints will yield results.
The JSON Web Token (JWT) in these requests is for the System Assigned MI of the Virtual Machine, not a management token for Azure.
Requesting all certificates:
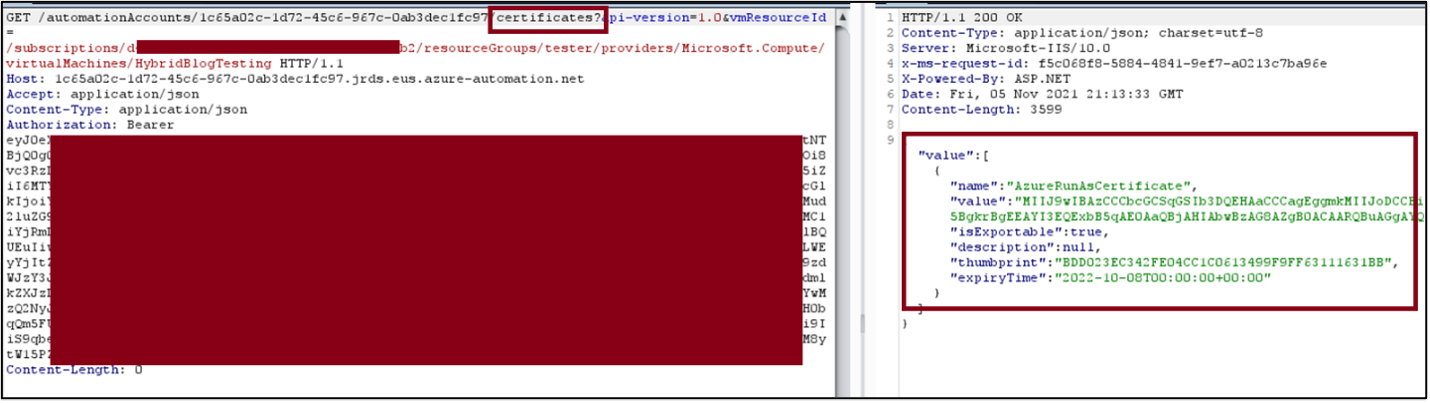
We were satisfied with these findings. We figured that this represented an escalation path from Virtual Machine Contributor to Subscription Contributor if Hybrid Worker nodes were in use and reported our findings to Microsoft.
Escalating Our Findings
After we had submitted our report, we found a recently published blog that detailed some of these same ideas, though their thesis was obtaining lateral movement after an administrator pushed a certificate to the Virtual Machine. The author also demonstrated that you could register a new Hybrid Worker node to an Automation Account using the Automation Account key and Log Analytics Workspace key. We wondered if we could abuse this route to escalate the severity of our previous findings.
To read Automation Account keys, a user only needs the Reader role. To exploit this, we hacked up some source code from Microsoft’s Desired State Configuration (DSC) repository.
The repository contained some scripts that are used to register a new Hybrid Worker node, so we bypassed some environment checks and created users/groups that are expected to exist. The registration process looks like this:
- Generate a new self-signed certificate or use an existing one
- Create a payload with some details: HWG name, IP address, certificate thumbprint, etc.
- Sign the payload with the AA key
- Send a PUT request to the AA with all the above info
This also does not require Hybrid Worker Groups to already be in use; we can supply an arbitrary group name and it will be created. After registering, we can use the certificate and key generated during this process to access the same endpoints that we identified earlier. You also don’t need a Log Analytics workspace key to register because not all AAs are linked to a workspace.
From start to finish, this exploit works as follows:
- Attacker with Reader access reads the victim Automation Account key
- Attacker uses this key to register their own Virtual Machine in their own tenant as a Hybrid Worker node
- Attacker can dump any credentials or certificates from the victim AA and use them to authenticate
We reported this issue to MSRC in a separate report. Below is the timeline for this case:
- October 25, 2021: Initial report submitted
- December 13, 2021: Second report submitted with details of full privilege escalation
- December 31, 2021: $10k bounty awarded
- March 14, 2022: Patch is applied
Microsoft’s Response to the Azure Automation Account Vulnerabilities
After reporting our findings, Microsoft identified the Azure Automation customers vulnerable to this exploit and notified them through the Azure portal. A fix has been rolled out to all customers.
Additionally, Microsoft has updated their documentation with mitigation steps for customers. They’ve updated the Reader role so that it no longer has the ListKeys permission on Automation Accounts and can no longer fetch Automation Account keys. They recommend that customers switch to custom roles if they need a Reader to fetch the Automation Account keys.
Microsoft has also provided the following guidance for deploying Hybrid Workers:
Microsoft recommends installing Hybrid workers using the Hybrid Runbook Worker Virtual Machine extension – without using the automation account keys – for registration of hybrid worker. Microsoft recommends this platform as it leverages a secure Azure AD based authentication mechanism and centralizes the control and management of identities and other resource credentials. Refer to the security best practices for Hybrid worker role.
Conclusion
This issue allowed any user who could read Automation Account keys to extract any credentials or certificates from the affected Automation Account. This issue was not particularly technical or difficult to exploit, and only abused the intended methods for registration and credential retrieval.
This is a good reminder that even low privileged role assignments such as Reader can have unintended consequences in your cloud environment.
Want to learn more about cloud penetration testing? Explore our Azure cloud penetration testing service.
Recent Posts
Application Security: Shifting Left to the Right Degree
In application security, DevOps, and DevSecOps, “shift left” is a guiding principle for how organizations should implement security practices into the development process. For this reason, today’s application security testing tools and technologies are built to facilitate a shift left approach, but the term has taken on a new meaning compared to when it first entered the scene years ago.
Over the past decade, software development has drastically changed with the proliferation of impactful technology, such as APIs and open-source code. However, shift left has remained a North Star for organizations seeking to improve application security. Its meaning has become more nuanced for those attempting to achieve a mature application security framework.
I recently sat down with Maty Siman, Founder and CTO at Checkmarx on our Agent of Influence podcast to discuss application security and the concept of shift left. You can listen to the full episode here. Let’s explore four highlights from the discussion:
The “Lego-ization” of Software
In the past, developers would build their solutions from the ground up, developing unique libraries to carry out any desired functionality within an application. Today, developers leverage a wide range of tools and technologies, such as web services, open-source code, third party solutions and more, creating software that is ultimately composed of a variety of different components.
As Maty alluded to during the Agent of Influence podcast, many in the industry have referred to this practice as the “lego-ization” of software, piecing together different premade, standardized Lego blocks to form a unique, sound structure.
While both traditional and modern, lego-ized methods are forms of software development, they demand a different set of expertise. This is where mature application security frameworks become invaluable. Maty explains that today’s developers are often working around the clock to keep up with the pace of digital transformation; they cannot just focus on code for vulnerabilities. They must also look at how the different components are connected and how they communicate with one another.
Each connection point between these components represents a potential attack surface that must be secured – but addressing this can also become a source of friction and perceived inconvenience for developers.
The Impact of Today’s Open Source and API Proliferation
The recent proliferation of software supply chain security threats has made the situation even more complex and dire for software developers, as malicious actors look to sneak malicious code into software as it’s being built.
As Siman explains during our podcast conversation, open source code makes up anywhere from 80 to 90 percent of modern applications. Still, developers are pulling these resources from a site like GitHub often without checking to see if the developer who created the package is trustworthy. This further exacerbates the security risk posed by the lego-ized development practices we see today, Maty warns.
Additionally, in recent years, there has been an explosive growth in the usage of APIs in software development. Organizations now leverage thousands of APIs to manage both internal and external processes but have not paid enough attention to the challenge of securing these deployments, according to Maty.
However, efforts have been made to set organizations on the right path in securing APIs, such as the OWASP API Security Project – but there is still a lot of work to be done. Check out the OWASP API Top 10 list, co-written by Checkmarx’s Vice President of Security Research, Erez Yalon.
Read: AppSec Experts React to the OWASP Top 10 2021
Many organizations are not aware of which or how many APIs their services take advantage of, which presents an obstacle towards securing them. As a result, Maty explains that the concept of a “software bill of materials,” or SBOM, is beginning to take shape as organizations seek to better understand the task at hand.
With APIs quickly becoming a favored attack vector for cybercriminals, the importance of developers getting a handle on API security cannot be overstated, which is especially crucial for application penetration testing. Simultaneously, the task is an immense one that many developers see as a headache or hindrance to their main goal, which is to deliver new software as quickly as possible.
Shifting Left in an Evolving Application Development Landscape
While the trends outlined above certainly present significant challenges when it comes to application security, they are not insurmountable. Maty advises that organizations can and should implement certain changes in their approach to application security to better support developers with appropriate application security testing tools and other resources.
One of the main issues organizations face in modern application security testing, including application penetration testing or secure code review, lies in the effort to shift left. Shift left is sometimes seen as a source of friction in the developer community. It is about finding and managing vulnerabilities as early as possible, which has only become more difficult and complex as development has evolved.
Read: Shifting Left to Move Forward: Five Steps for Building an Effective Secure Code Review Program
The amount of innovation in software development and implementation means that shifting as far left as possible is not always feasible or even the best approach. While detecting vulnerabilities in code as early as possible is a priority in application security, attempting to force developers to do so too early in the development process can exhaust developers and slow software delivery, as Maty advises.
For example, the use of integrated development environment (IDE) plugins can often make developers feel hindered and nagged by security rather than empowered by it. While they represent a shift to the extreme left in terms of security, they are not always a good idea to impose on developers.
No Right Way to Shift Left in Application Security
Ultimately, the proper way to shift left is going to vary across organizations, depending on the software they are building and what is going into it. It is paramount to take a tailored approach that balances the security responsibilities placed on developers with the need to maintain agility and deliver software quickly.
Application development has changed significantly, and we can expect it to continue to change in the coming years. Creating and maintaining a mature application security framework will depend on maintaining a proper understanding of the tools and technologies developers are using and adjusting the organizational approach to application security accordingly.
For more, listen to episode 32 of Agent of Influence with Maty of Checkmarx:

Recent Posts
Blockworks: The Purpose and Perils of Crypto Privacy Tools
On April 11, 2022, Travis Hoyt was featured in the Blockworks article, The Purpose and Perils of Crypto Privacy Tools. Preview the article below, or read the full article online.
+ + +
Crypto services designed to improve transaction privacy continue to be used in illegal activities, but using so-called mixers for nefarious purposes is becoming increasingly risky.
A cryptocurrency mixing service is used to privately transfer cryptoassets between wallets by comingling funds in a pool of assets belonging to many participants.
The hacker who last month exploited the Ronin Network for roughly $625 million recently transferred thousands of ether to Tornado Cash, a privacy tool for Ethereum. More than 165,000 ETH remains in the attacker’s wallet.
Tornado Cash, a decentralized protocol for private transactions on Ethereum, breaks the on-chain link between source and destination addresses, according to its website. The protocol uses a smart contract accepting ETH deposits that can be withdrawn by a different address. The longer the funds remain in the pool before being withdrawn, the greater the privacy protections.
“While Tornado Cash can be used for illegal activities, like money laundering or tax fraud, many believe that it is a crucial tool for maintaining financial anonymity,” NetSPI Chief Technology Officer Travis Hoyt told Blockworks.
“Due to the nature of mixers like Tornado Cash obscuring transactions, consumers that lack a full understanding of crypto’s security infrastructure may be susceptible to risks such as inadvertent money laundering.”
The Latest Seizures
The ethos behind mixers is to harbor more financial freedom and privacy, bringing cash-like anonymity to otherwise public transaction ledgers, by deliberately making transactions hard to regulate, Hoyt said. Such technology can be used lawfully or unlawfully; the only way to avoid risk completely is to not engage at all.
“While there are a plethora of general resources about crypto available, the industry must prioritize education on the inherent security risks and how to best mitigate these risks,” Hoyt said. “Aside from consumers actively choosing to not utilize mixers, this is the best way to ensure ethical crypto traders remain protected.”