NetSPI Attack Surface Management Updates: Portfolio Dashboard & Perceptual Hashing
Hackers are highly motivated and incentivized to find new ways to gain access to your systems, expose your information, or even target your customers. To deliver the highest level of security and maintain a leadership position in the global offensive security space, NetSPI continues to invest in new technology, updated service capabilities, and the highest-quality teams.
“On average, attack surface management tools initially discover 30% more cloud assets than security and IT teams even know they have,” according to Forrester’s Find And Cover Your Assets With Attack Surface Management report. Although some tools discovered several hundred percent more assets than they originally knew about.
Top use cases for attack surface management technologies are asset discovery and inventory, supply chain and third-party risk management, M&A due diligence, and compliance management. NetSPI’s Attack Surface Management (ASM) development team recognized these common use cases and saw the need to categorize and sort information faster, easier, and in a more intelligent way.
The IT and SOC teams we work with are not simply looking for more data – they are looking for more meaningful and actionable data, and our recent developments have been targeted towards that.
As a result, we are proud to introduce two new features into NetSPI’s ASM solution: the Portfolio Dashboard and Perceptual Hashing.
The Portfolio Dashboard
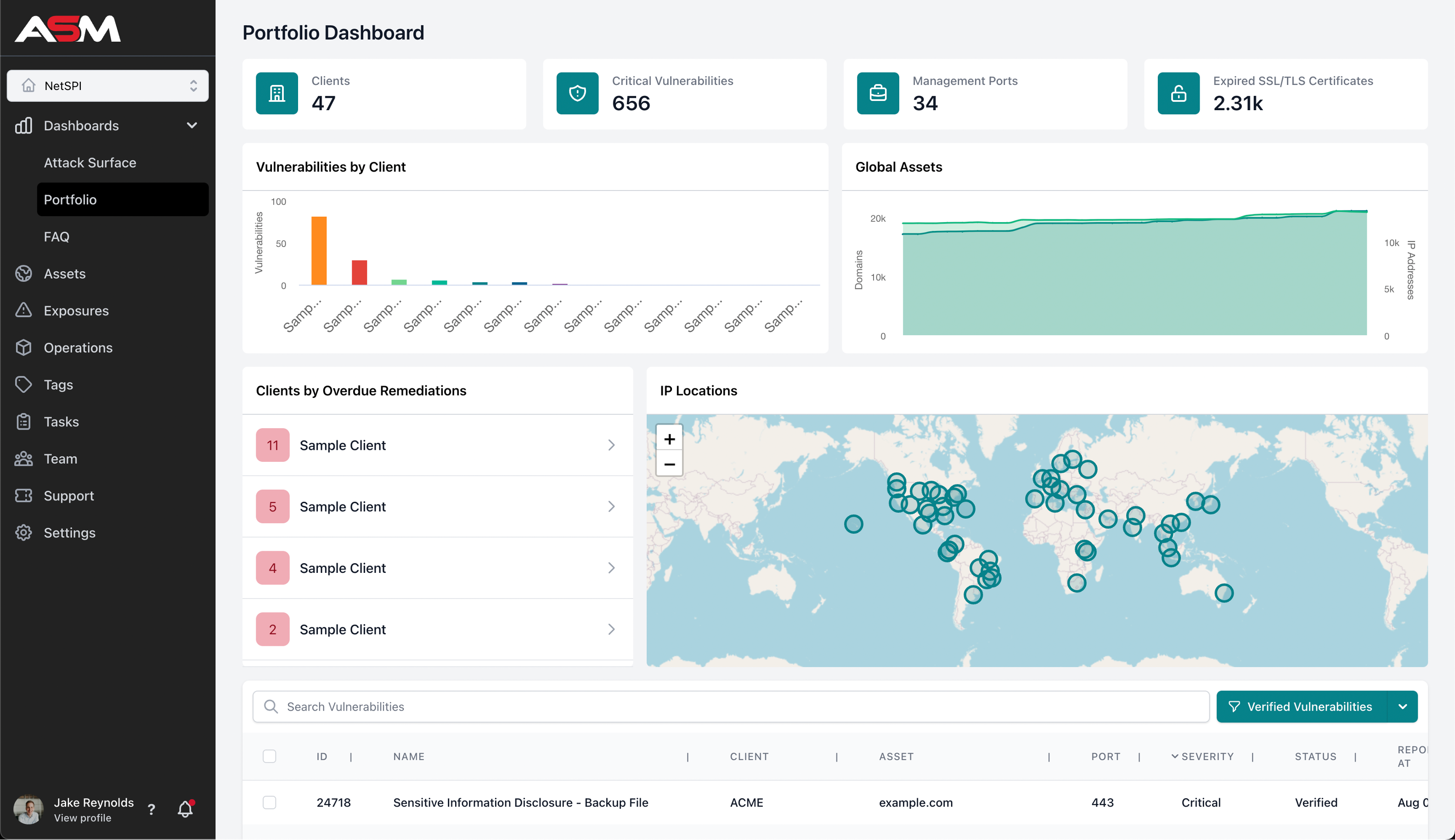
The Portfolio Dashboard is, simply put, a dashboard. This dashboard allows your company a global risk view of your attack surface, specifically showing your corporate network along with all portfolio or client networks. We’ve seen the most benefit from this feature in companies going through M&A processes, private equity firms, cyber insurance companies, parent companies, and conglomerates, along with many others.
Organizations using ASM can now search and filter for a specific threat or technology within their entire portfolio. This enables them to clearly display the specific assets that have potential vulnerabilities and provide actionable information in seconds.
A well-known example where NetSPI’s ASM Portfolio Dashboard would have proven valuable is Log4Shell. Log4Shell is a remote code execution vulnerability in Apache Log4j that allowed attackers to place malware on a targeted system, leading to the potential of a completely compromised network, theft of sensitive information, and more.
Not good!
In this example, non-portfolio companies were struggling to identify all affected assets within their network. Portfolio companies and cyber-insurance companies needed to not only identify assets within their own network, but they also needed to identify affected assets in their clients’ networks – searching every known potentially vulnerable asset to better understand their risk, while still missing every unknown asset.
Again, not good!
If the Log4j crisis happened today however, companies could leverage NetPI’s ASM portfolio dashboard to quickly and easily search for any affected device across their global attack surface. The potentially vulnerable assets would be displayed in a simple dashboard (as seen in the screenshot above) and allow IT and security teams to react accordingly, letting them efficiently target the most vulnerable areas, potentially saving the company and their customers from catastrophic damage.
This is just one example of how the portfolio dashboard can benefit companies today. Although many organizations have remediated Log4Shell today, this feature can help in much the same way with other threats or technologies that may arise tomorrow, next week, or in the future.
Perceptual Hashing
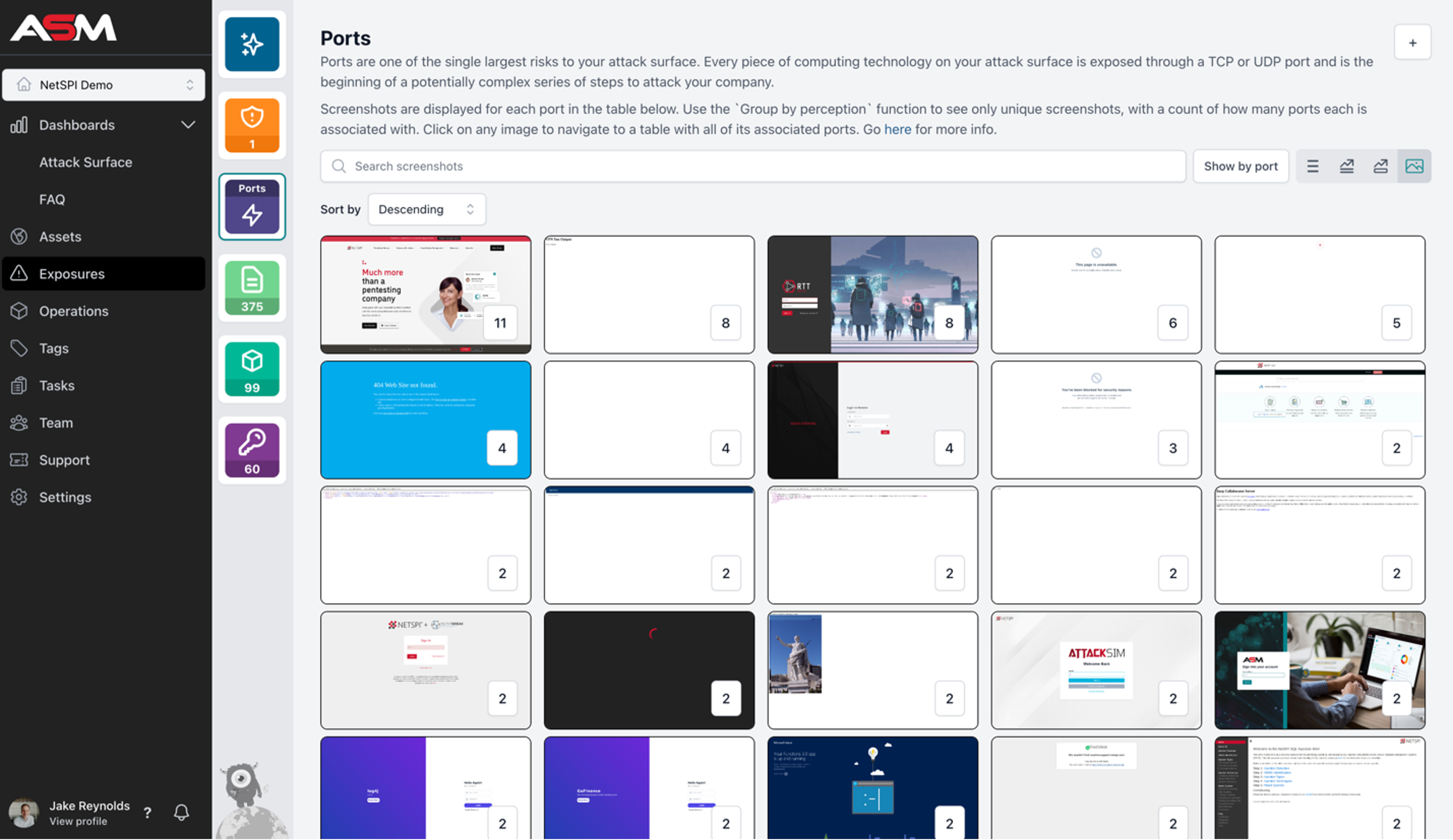
NetSPI’s current ASM offering routinely takes screenshots of all websites on your global attack surface. And we’re excited to share that the platform now includes Perceptual Hashing.
Perceptual Hashing, sometimes referred to as Perceptual Image Hashing or Perceptual Sorting, analyzes these screenshots and categorizes them based on similar looks, styles, layouts, and images. These groups of screenshots are then reviewed by NetSPI’s ASM Operations Team to identify trends in your network or find outliers of websites running on your perimeter, and then notify your team.
There are other types of hashing, such as average hashing, cryptographic hashing, geometric hashing, etc., however perceptual hashing is the most effective in cybersecurity because it is designed to recognize and group similar items even if minor modifications are made to the images such as compression, brightness, etc. As a result, images that are similar will be grouped together, however outliers will be detected and grouped separately.
The intention is that if there is a vulnerability found on one of your public facing websites, Perceptual Hashing will allow you to search for similar webpages so you can review and take action. With NetSPI’s ASM continuous penetration testing capabilities and real-time reporting, teams will know if there are any publicly exposed management interfaces almost instantly and can respond accordingly.
One of NetSPI’s ASM clients, a Fortune 500 technology company, recently used Perceptual Hashing to efficiently identify a vulnerability across various servers. The ASM Operations Team discovered a publicly exposed management interface in a proprietary web application during a routine scan, which left them vulnerable to external unauthenticated users accessing administrative functionality. The ASM team was able to take this finding and search the entirety of their other websites with the equivalent perceptual hash, identifying multiple other vulnerable servers. Once all were searched and the vulnerabilities were discovered, the team was able to report back to the company and guide them to remediate accordingly.
Other cases where NetSPI’s Perceptual Hashing feature can be used are:
- Servers using specific landing pages or technologies
- Publicly exposed interface management
- Digital rights management
- Data deduplication
- Image searching
These are just two examples of recent innovations added to NetSPI’s Attack Surface Management solution. Although Perceptual Hashing is my current favorite feature, there are many innovations in the works right now to continue delivering the highest quality security for customers with our technology driven, human delivered methodology.
Other noteworthy updates to our ASM solution include:
- New intelligent search help – when users click on the search inputs, they are presented with helpful suggestions to deliver the best results.
- Users in the Domain, IP Address, and Port table views can now copy selected assets and port URLs to the clipboard.
- Users can add an attribution statement when adding assets.
- Domain and IP address exports have been updated to include ports and associated assets.
- Domains, Ports, and IP Addresses now have all associated screenshots available to view.
- When viewing the full details page for a Domain, you can now use the “Generate Report” button to get a summary report specifically for that domain.
- The main dashboard now shows you trends of all vulnerabilities on your attack surface over time, separated by severity.
- On the ASNs page, the ‘Scan for ASNs’ button now validates and updates existing ASN associations in addition to inserting newly identified ASNs.
- The Port Gallery has been converted to an Explore page with left-hand facet searches.
- SAML SSO now supports users from multiple domains.
- Ability to automatically transform invalid CIDR ranges when adding assets.
- New port intelligence, including status code, content type, content length, site title, JARM, and HTTP reachability.
Additional updates can be found on the Attack Surface Management changelog: https://asm.netspi.com/guide/changelog/.
To learn more about NetSPI’s Attack Surface Management, contact your rep or connect with us here.
This blog post is a part of our offensive security product update series. Stay tuned for additional innovations within Resolve (PTaaS), ASM (Attack Surface Management), and AttackSim (Breach and Attack Simulation).