
Strategic Security Success with NetSPI’s New Threat Modeling Solution
Companies are constantly working to innovate. Updates are made to existing solutions, new solutions are launched, processes are refined, new technologies are implemented, etc. and as these changes are made it is normal for new threats to be introduced. The companies take on the risks and responsibilities of new system attack vectors created by these choices. It is critical that companies review these threats, ideally early in the planning phase, but also as an on-going practice throughout the product lifecycle to allow for information-based decision making with all needed data.
NetSPI’s new Threat Modeling service takes a holistic approach to identifying potential threats to your company’s systems and applications. Leveraging a proprietary methodology developed from over 20 years of hands-on penetration testing experience, as well as other widely adopted methodologies such as STRIDE, PASTA, and more, each engagement provides a detailed technical analysis that enables stakeholders to make strategic decisions based on prioritized vulnerabilities, enumerated attack scenarios, and customized remediation recommendations through a 6-step process:
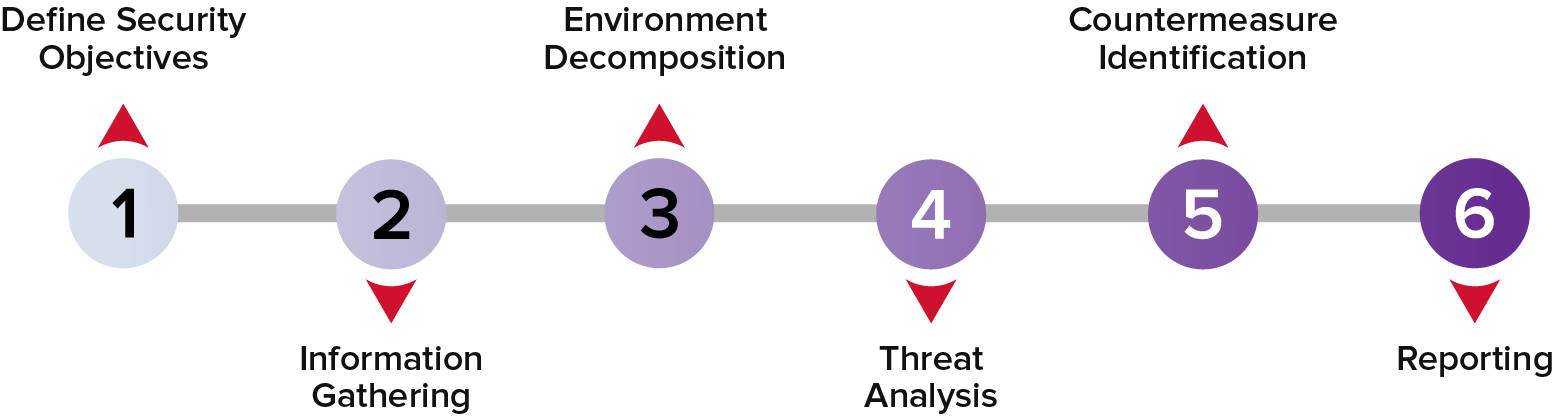
1. Define Security Objectives:
Establish specific security objectives for the engagement and prioritize in alignment with your company’s overall mission and risk tolerance.
2. Information Gathering:
NetSPI collects and reviews all available documentation. We also identify and interview system stakeholders such as: security personnel, developers, architects, business owners, project managers, operations staff, and more. These interviews are designed to provide information about both the architecture and context in which the system(s) function.
3. Environment Decomposition:
We build a component diagram of the most relevant deployment models and information flows between system components, then work to enumerate the system components and trust zones within the environment.
4. Threat Analysis:
Then, we develop a threat analysis based on the assets and system environment. Leveraging NetSPI’s extensive threat library, along with the client-provided information, we enumerate threats, classify severity, define attack scenarios, and identify additional security measurements that can be implemented based on business risks and organizational goals.
5. Countermeasure Identification:
We produce a threat traceability matrix by enumerating actions, devices, procedures, and techniques that prevent or mitigate threats to assets and system components.
6. Reporting:
Lastly, we produce a threat traceability matrix, mapping threats and threat scenarios to their trust zones, components, assets, and controls, and providing a summary of insufficient security controls and related threats.
If you would like to learn more about our Threat Modeling solution, check out our data sheet, or contact us for a demo.
This blog post is a part of our offensive security solutions update series. Stay tuned for additional innovations within Resolve (PTaaS), ASM (Attack Surface Management), and BAS (Breach and Attack Simulation).
Read past solutions update blogs:
Explore More Blog Posts

Extracting Sensitive Information from Azure Load Testing
Learn how Azure Load Testing's JMeter JMX and Locust support enables code execution, metadata queries, reverse shells, and Key Vault secret extraction vulnerabilities.

3 Key Takeaways from Continuous Threat Exposure Management (CTEM) For Dummies, NetSPI Special Edition
Discover continuous threat exposure management (CTEM) to learn how to bring a proactive approach to cybersecurity and prioritize the most important risks to your business.

How Often Should Organizations Conduct Penetration Tests?
Learn how often organizations should conduct penetration tests. Discover industry best practices, key factors influencing testing frequency, and why regular pentesting is essential for business security.