Virtual Application
Penetration Testing
NetSPI identifies the risks specific to applications published through virtualization platforms and uses traditional application penetration testing to help ensure that your company protects its attack surface while adapting to evolving business needs. We also identify security vulnerabilities that provide unauthorized access to the operating system through applications published via virtualization platforms.
Improve Application Security
NetSPI’s virtual application penetration testing reduces organizational risk and improves application security
It has become common for companies to make traditional desktop applications accessible from the internet by publishing them through virtualization platforms such as Citrix and VMware. These platforms make it easy for remote employees, partners, and vendors to access existing desktop applications without requiring the large investment that comes with rewriting legacy apps for the web. However, with the ease of access comes additional risks that don’t have to be considered when desktop applications live behind a firewall.
NetSPI also offers host-based pentests and red team operations that focus on virtualization platforms.
Virtual Application Penetration Testing
During virtual application penetration testing, NetSPI identifies the risks specific to applications published through virtualization platforms along with traditional application penetration testing to help ensure that your company is protecting its attack surface while adapting to evolving business needs.

Virtual Application Breakout Assessments
During virtual application breakout assessments, NetSPI identifies security vulnerabilities that provide unauthorized access to the operating system through applications published via virtualization platforms such as Citrix and VMware.
Virtual Application Penetration Testing and Breakout Assessment Services
NetSPI pentests your virtual application where it is hosted internally or in a virtualized environment. NetSPI’s approach to virtual application security assessments includes reviewing server-side controls, data communication paths, and potential client-related security issues. We employ manual and automated pentesting processes using commercial, open source, and proprietary cybersecurity testing tools to evaluate your application.
Below is the full process that includes breakout testing. If you are only interested in breakout testing, this can be completed as a standalone project.

Static Analysis
During the static analysis phase of testing, NetSPI reviews the follow areas:
- Service account roles and permissions (e.g. client, application server, database server)
- Application file, folder, and registry permissions
- Application service, provider, WMI subscription, task, and other permissions
- Assembly compilation security flags
- Protection of data in transit
- Hardcoded sensitive data and authentication tokens (e.g. passwords, private keys)
- Hardcoded encryption material (e.g. keys, IVs)
- Use of insecure encryption and hashing algorithms
- Database user roles and permissions
- Database and server configurations

Dynamic Analysis
During the dynamic analysis phase of testing, NetSPI tests and reviews the following areas:
- Authentication and authorization controls enforced on the client and server
- Application user roles and permissions
- Application workflow logic between GUI elements
- Web services utilized by the application
- File system changes including file and folder creation, deletion, and modification
- Registry changes including creation, deletion, and modification of keys and values
- Application objects and information stored in memory during runtime
- Use of insecure encryption and hashing algorithms
- Network protocols utilized by the application (e.g. SMB, FTP, TFTP)
- Database connections

Breakout Testing
During breakout testing, NetSPI identifies configuration and application functionality that may allow a remote attacker to access the operating system through the published application:
- Virtualization platform vulnerabilities and misconfigurations
- Application-specific functionality
- Operating system configurations and security controls
- Ingress and egress configurations and security controls
*Note: If you are only interested in breakout testing, this can be completed as a standalone project.
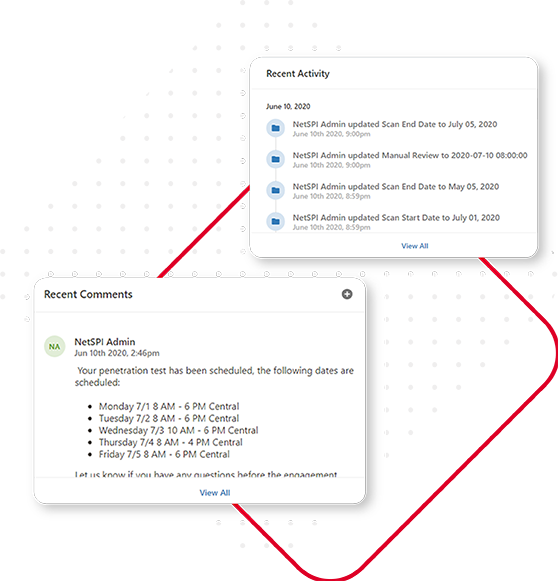
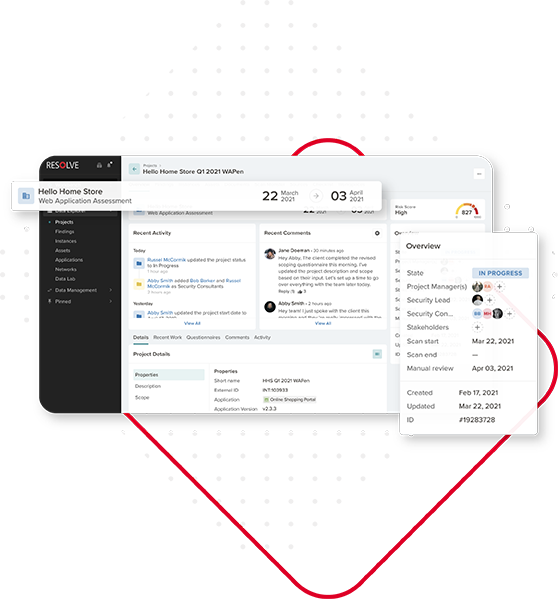
Powered by Resolve™
Virtual application pentest engagements are managed and delivered through Resolve, NetSPI’s vulnerability management and orchestration platform. Resolve elevates your vulnerability management and pentesting program.

Pentesting Research and Tools
Learn about penetration testing on our blog, our open source penetration testing toolsets for the infosec community, and our SQL injection wiki.
