Our Technology
At its core, NetSPI is a technology-enabled cybersecurity firm. The technology we build and continuously innovate allows us to provide best-in-class enterprise penetration testing and attack surface management.
Resolve™
CISOs, infosec managers, vulnerability managers, and more use Resolve, NetSPI’s vulnerability management and orchestration platform, to make their jobs easier and improve their organization’s security posture.
-
Simplify Vulnerability ManagementResolve manages the lifecycle of vulnerabilities from discovery to remediation.
-
Pentest EfficienciesResolve’s Workbench cuts the time to complete an engagement by 40 percent.
-
Security AutomationAutomation enables manual pentesters to focus on discovering the hard-to-find vulnerabilities.
-
Test Continuously or At-ScaleResolve is flexible and can scale up or down to meet the testing requirements of any organization. The platform also supports continuous testing. Increase the frequency of your security testing to stay on top of new releases and incremental changes.
-
Attack Surface ManagementYour attack surface is constantly evolving and your security should too. NetSPI builds strong testing programs to ensure you understand your attack surface and potential risks.
Attack Surface Management (ASM)
NetSPI’s Attack Surface Management service is powered by an easy-to-use, cloud-based application: ASM. The technology enables the ASM Operations Team to find gaps in your security posture that tools miss. It provides an interactive interface for continuous pentesting and efficient attack surface management and features:
- Immediate and simple set up
- Tracking and trending data over time
- 24/7/365 internet-scale scan coverage
- Asset intelligence
- Slack and email integration
- Open source intelligence gathering
- Asset and exposure prioritization
- Port discovery
- And much more

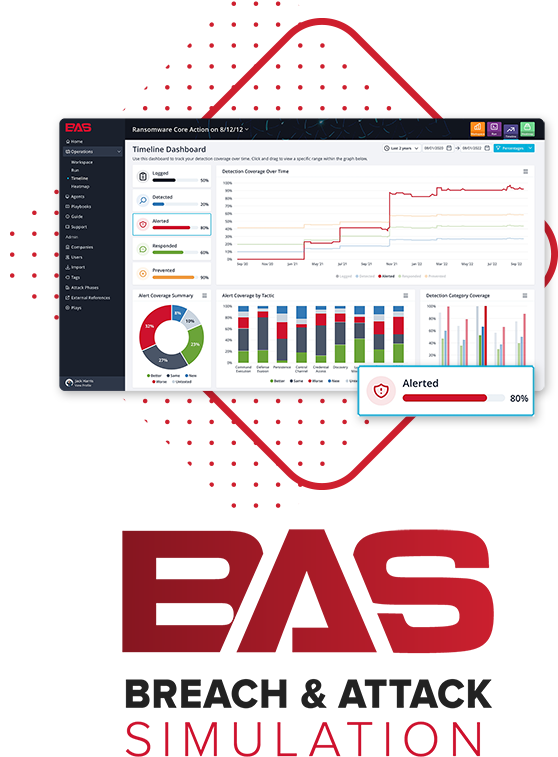
Breach and Attack Simulation
NetSPI’s Breach and Attack Simulation platform provides you with the tools you need to ensure the effectiveness of your defensive controls and measurably improve security maturity.
- Customize and automate MITRE ATT&CK frameworks
- Execute attack scenarios based on real-world attacker TTPs
- Simulate a single technique as a play or execute a full attack chain using one of the pre-built playbooks
- Gain remediation guidance for each attacker technique
- Test, measure, and track the maturity of detective and preventive controls against specific attacker techniques

 Resolve™
Resolve™