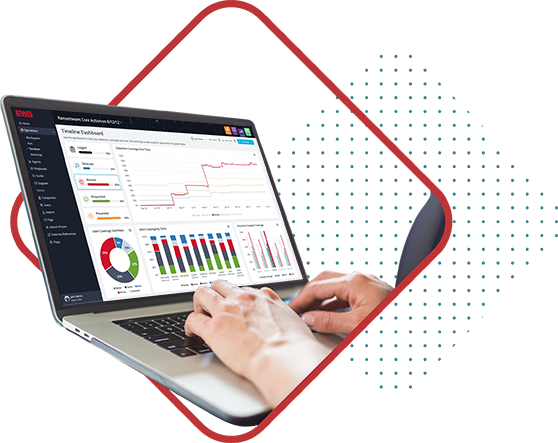
Breach and Attack Simulation
It takes one click to give an adversary everything they need to access your global environment. Our proven technology and expert teams will evaluate your detective controls to prepare you for real-world threats throughout the cyber kill chain.

Only 20 percent of common attack behaviors are caught by EDR, SIEM, and MSSP out-of-the-box solutions.
Contrary to what many BAS vendors and technology providers claim, 100% detection does not exist. So, how can we improve our security controls to better detect attacks across the kill chain? With breach and cyber attack simulation.
NetSPI’s Award-Winning Breach and Attack Simulation
Recognized as “BAS Solution of the Year” in the CyberSecurity Breakthrough Awards, we deliver a centralized detective control platform that gives organizations the ability to create and execute customized procedures utilizing purpose-built technology and professional human pentesters. Simulate real-world attack behaviors, not just IOC’s, and put your detective controls to the test in a way no other organization can.
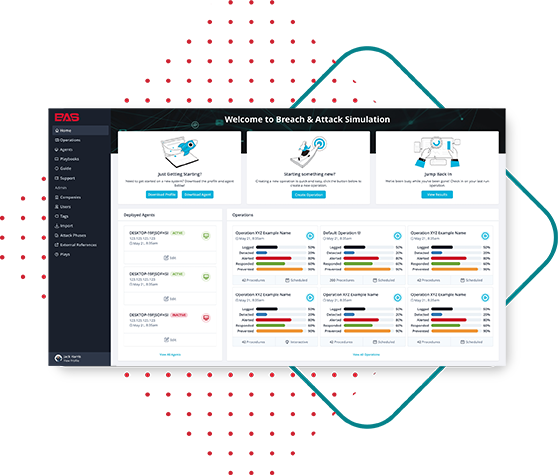
Build Resiliency To:
- Ransomware
- Denial of Service
- Data Loss
- Fraud
- Information Leaks
- And More!
Validate Controls:
- Endpoint Controls
- Network Controls
- Active Directory Controls
- SIEM Capabilities
- MSSP Capabilities
Identify Detection Gaps:
- Missing Data Sources
- Disabled Controls
- Misconfigured Controls
- Broken Telemetry Flows
- Missing Detections
- Incomplete Coverage
- Kill Chain Gaps
Evaluate Detective Controls
Measure the effectiveness of your security controls and identify gaps with customizable procedures run by our manual pentesting teams. NetSPI delivers a true white-glove service throughout operations, performing top quality testing with streamlined communication from beginning to end of each engagement.
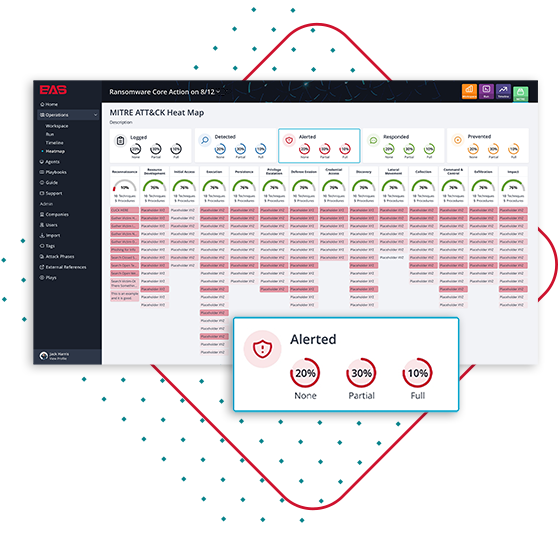
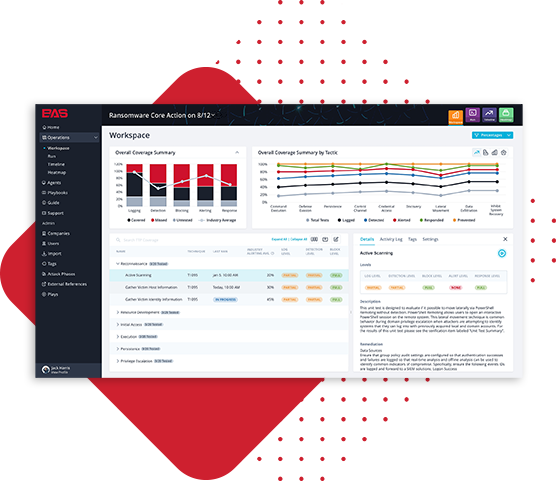
Educate Security Operations Teams
Findings are delivered with descriptions, recommendations, procedures, and resource links, allowing procedures to be easily understood and replicated. Comprehensive dashboards update in real-time allowing you to easily track and trend your security posture, benchmark against industry competitors, and visualize your ROI.
Execute With Confidence
Utilize our centralized platform, expert testing teams, and proven testing methodology to enable security operation teams and implement fact-based decision making to improve resilience from adversarial attacks where it is needed most.