Ransomware Prevention, Detection, and Simulation
Table of Contents
- What is ransomware?
- Ransomware trends
- Ransomware prevention
- Ransomware detection
- Ransomware simulation
- Ransomware security terms
- How NetSPI can help
What is ransomware?
In this section, you learn what is ransomware, how it fuels criminal activity, how ransomware works, and how to stop ransomware.
Ransomware, a definition
Ransomware is a set of malware technologies, hacking techniques, and social engineering tactics that cybercriminals use to cause harm, breach data, and render data unusable. Ransomware adversaries hold the data hostage until a victim pays the ransom. Increasingly, they also threaten to leak stolen data.
Ransomware is a business model for cybercriminals. Victims pay ransomware adversaries for decryption keys through cryptocurrency, such as Bitcoin. Many victims pay a second ransom to get assurance that the threat actor won’t release stolen data.
How does ransomware fuel criminal activity?
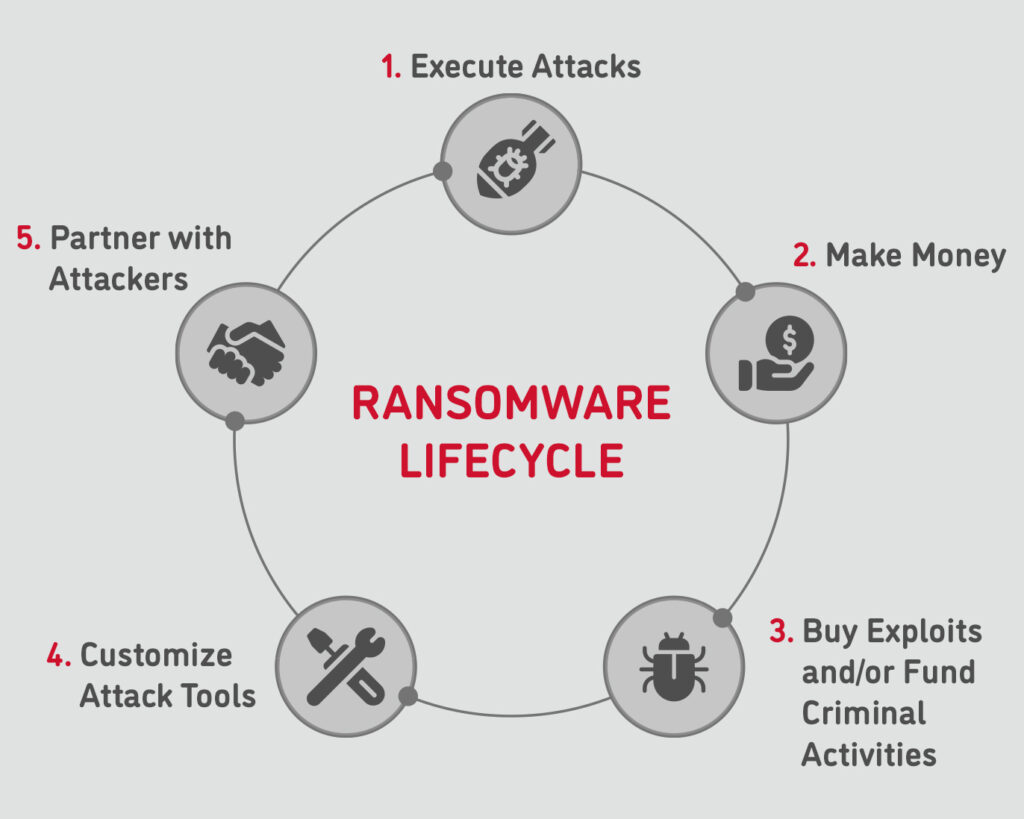
Figure 1: The ransomware economic lifecycle fuels more criminal activity.
Ransomware fuels a criminal economy through five steps:
Step 1: Cybercriminals execute ransomware attacks.
Step 2: Attackers make money when they collect a ransom.
Step 3: Ransoms fund the purchase of new exploits, lists of vulnerable networks, and ransomware-as-a-service toolkits.
Step 4: Attackers use malware and exploits off-the-shelf or customize the tools to create ransomware variants and new techniques.
Step 5: Ransomware developers engage with attack partners who use the tools and techniques to perform the attacks.
How does ransomware work?
A ransomware attack follows a series of steps called a kill chain. Most ransomware attacks follow a variation of this ransomware kill chain: gain access, escalate privileges, target data, exfiltrate data, remove recovery capabilities, deploy ransomware, and get paid.
Tip: Attackers have options, so every ransomware attack is different. Defenders must prepare to detect and block the many choices available to a ransomware attacker, not a single path.
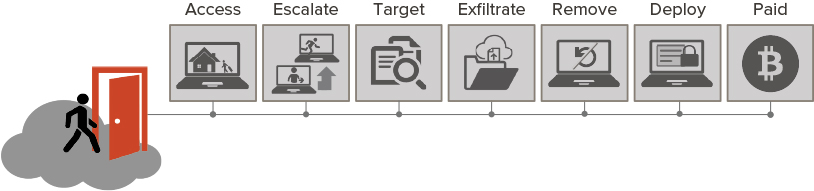
Figure 2: A ransomware kill chain traces the seven steps in a ransomware attack: access, escalate, target, exfiltrate, remove, deploy, and get paid.
Do antivirus and endpoint detection and response (EDR) tools stop ransomware?
Only about 20% of the ransomware tactics, techniques, and procedures (TTP) used by ransomware attackers are identified out-of-the-box by antivirus (AV), endpoint detection and response (EDR), and security information and event management (SIEM) tools. Given AV, EDR, and SIEM vendors choose to focus on limiting false positives, many true positives are missed in Windows, Linux, and mainframe environments.
How to stop ransomware
Every step in the ransomware kill chain is an opportunity for defenders to detect and stop a ransomware attack—but you don’t need to achieve 100% detection at every step. Instead, if you can detect one or more malicious events present in most kill chains before the attackers meet their objective, then you can prevent ransomware attacks.
Tip: Detecting a ransomware attack earlier in the kill chain delivers more value, so prioritize detective controls that enable detection when an attacker accesses systems, escalates privileges, or targets data.
Ransomware trends
In this section, learn how ransomware attackers gain access, escalate privileges, target data, steal data, and deploy ransomware as well as the average ransomware payment.

Source: IST Ransomware Task Force Report
How do ransomware attackers gain access?
Ransomware attackers get into a network in many ways:
- Social engineering. Users unintentionally download and execute ransom malware via malicious emails, PDFs, drive-by downloads, malvertising, forced download, and browser exploits.
- Unpatched exploits. Most ransomware attackers use exploits that have been around for years. An attacker can easily scan the internet for websites that haven’t patched a vulnerability for which the attacker has an exploit.
- Ransomware-as-a-Service (RaaS). Malicious software developers provide ready-made malware to criminal groups who already have access to environments or the ability break in.
- Logins without multi-factor authentication. Without MFA to stop them, attackers gain access to the same powerful tools used daily by IT administrators who manage corporate networks and IT resources. Administrators who access IT management interfaces—e.g., terminal services, virtual private networks (VPNs), and remote desktops—often use weak passwords and do not require MFA. Attackers guess the passwords easily, find them in open source code repositories, or collect them via phishing.
How do ransomware attackers escalate privileges?
Ransomware attackers work to exploit bugs, design flaws, and configuration oversights in an operating system or application to gain access to protected databases, file shares, and business sensitive data. They often use Server Message Block (SMB) exploits, weak passwords, and insecure Active Directory configurations to gain more privileges on systems and those of trusted partners.
Ransomware attackers may go after a subsidiary or service provider with weaker security controls and then ride the third-party trust relationship into your environment. Or vice versa: your organization may be used to spread ransomware to your customers and partners.
What data and resources do attackers want?
Ransomware attackers search the network and systems for valuable data and resources to target, such as:
- Non-public information
- Regulated data, such as personal healthcare data (HIPAA) and payment card information (PCI)
- Operational technologies in manufacturing, industrial control systems (ICS), and other critical infrastructure
- Hardware and software supply chains
- Cyber insurance policies that reveal the maximum payout
To find resources to target, ransomware attackers may follow a workflow like this:
- Perform Active Directory reconnaissance for all domain computers, SQL Server databases, and server message block shares.
- Attempt access to file and SQL servers with privileged accounts.
- Search for sensitive data patterns across file servers and SQL Server databases.
How and why do ransomware attackers exfiltrate data?
In addition to encrypting data and holding it hostage, ransomware attackers also upload valuable data to other systems on the internet. This enables the attacker to extort more money in exchange for a promise not to leak the exfiltrated data.
Rather than stealthily copying the data, ransomware attackers may upload the data quickly to a website via FTP using SSH encryption. They may exfiltrate the data in one large file or in parts using common protocols such as Secure Message Block (SMB), Secure Sockets Shell (SSH), File Transfer Protocol (FTP), and HTTP/HTTPS.
Tip: You may be able to detect ransomware exfiltration by monitoring for large file uploads, excess bandwidth usage, or data loss prevention (DLP) via alternate protocols.
How do attackers deploy ransomware?
Once they have encrypted and uploaded the data, many ransomware attackers remove the victim’s ability to recover independently. Often, ransomware families follow steps like this to deploy ransomware:
- Verify correct platform, language, and time zone.
- Disable or bypass detective security controls.
- Hunt and destroy or encrypt backups hosted in local and cloud networks as well as virtual machine snapshots.
- Target IT management systems that an administrator could use to recover from ransomware.
- Search for targeted file types, generate a unique set of encryption keys, and encrypt the target files, often with custom libraries.
- Remove system restore capabilities by killing processes and services, removing restore points, deleting volume shadow copies, and overwriting master boot records on local workstations and servers.
- Propagate the ransomware using worm-like self-propagation to network shares via server message block (SMB).
- Remove their own files, scripts, and tools.
- Leave payment instructions.
How much do ransomware victims pay?
Average ransomware payouts are on the rise as attackers target bigger companies, specific sectors, and markets with deeper pockets. About 1 in 4 victims pay the ransom. Some can’t afford not to pay, and some are covered by cyber insurance. To date, the largest known ransom payment is $70 million.
EBOOK
The Ultimate Guide to Ransomware Attacks
Learn about ransomware trends, how ransomware works, and how to prevent and detect a ransomware attack.
Get the Guide
Ransomware prevention
In this section, learn about ransomware preparedness resources and leverage our ransomware prevention checklist.
What ransomware preparedness resources are available?
Several toolkits provide guidance to help organizations prepare for and become more resilient to ransomware:
- Ransomware Response Checklist (CISA)
- Ransomware Guide, which includes ransomware prevention best practices (CISA)
- Ransomware Tips (CISA)
- Preparing for a Cyber Incident (US Secret Service)
- Ransomware Protection and Response (NIST)
Checklist: How to prevent ransomware attacks
The best ransomware protection is prevention. Invest in security and ransomware prevention to protect sensitive data and avoid paying a ransom and downtime. The following checklist of ransomware prevention best practices can help you to minimize the risk of ransomware:
Reduce the attack surface presented by internet-facing systems, applications, and clouds. This requires an asset inventory. In general, the fewer assets you have exposed to the internet the better, so if it doesn’t need to be out there, remove it, and bring it inside your virtual private network (VPN).
Enable multi-factor authentication. Inventory all management interfaces of internet-facing assets—e.g., email, remote desktops, and Citrix—and secure them with MFA.
Make your vulnerability management program a priority, including asset management, configuration management, patch management, application management, Active Directory management, and cloud management.
Segment and isolate sensitive systems, applications, data, and privilegesto slow down or block threat actors. Isolate privileges between user levels. Isolate administrative management platforms to prevent ransomware attackers from using these tools.
Protect your backup systems. Does backup protect against ransomware? In some cases, but ransomware can infect NAS (network attached storage). That’s why off-site backups are critically important for recovery. In some cases, cloud storage is safe from ransomware, but it needs to be isolated, too. Be sure to segment and isolate access to your backup management interfaces.
Protect and validate recovery capabilities. Test your ability to restore from backups. In addition to making sure they are functional, consider the costs and time required to restore from backups. Have an incident response plan in place.
Test all ransomware security controls regularly through security audits, penetration testing, detective control reviews, and security awareness training.
Tip: Replicated data will replicate ransomware. Immutable offsite backups are required to restore point-in-time systems.
Tip: Tabletop exercises are a good start but not enough. Don’t assume that technical security controls will work as expected. Test them.
Should I get a ransomware cyber insurance policy?
Many organizations have used cyber insurance to recover from ransomware attacks. Because ransomware insurance losses have increased, however, common ransomware scenarios may now be excluded. The insurance company may require you to manage your risk and follow ransomware prevention and mitigation best practices before they issue a cyber insurance policy. Read the fine print of any ransomware policy to understand your coverage.
Ransomware detection
Defenders only need to detect one malicious event to recognize a ransomware attack in progress, quarantine the attacker, and prevent damage. In this section, learn about the detective control lifecycle and how to detect ransomware.
Checklist: How to detect a ransomware attack
Successful ransomware detection requires research from which data is fed into a detective control lifecycle with the following phases:
- Measure and track key performance indicators (KPIs) for detective control baselines to identify gaps and improve performance in data source logging, detection, blocking, alerting, and response.
- Identify high-impact and common tactics, techniques, and procedures based on current ransomware trends and historical data. TTPs are found in corporate annual reports, CISA, threat intelligence feeds, user groups such as Financial Services Information Sharing and Analysis Center (FS-ISAC), offensive security trends, and MITRE ATT&CK groups and software.
- Understand trending ransomware families to identify data sources and artifacts associated with the TTPs in your environment. Maintain this list over time. Know what artifacts are left behind by each ransomware family and its known bad behavior. At a minimum, learn about the following ransomware families:
| MAZE | Sodinokibi | Ryuk | Netwalker | SamSam |
| Related to ChaCha | Related to REvil and Sodin | Related to Hermes | A fileless ransomware | Related to Samas and SamsamCrypt |
- Map your current detective controls coverage of the identified ransomware behaviors. Ensure data sources are available to provide your security operations teams and partners with enough information to develop detections for common malicious behavior, such as file modification events, registry modification events, process creation events, image load events, network connection events, Windows endpoint security event logs, command line event logs, PowerShell event logs, NetFlow/PCAP (packet capture) data, and security event data from third-party software and devices.
- Develop new detections that work for your environment, based on data sources and the known bad behavior of ransomware families, while excluding the known good behavior of your users. Ensure detections cover common defensive evasion techniques.
- Test new detections to determine fidelity, block, alert, and response levels. Ensure that alert levels trigger an effective response for high-risk behavior associated with high-fidelity detections.
- Deploy new detections with a rollback plan.
- Monitor, monitor, monitor. Deploy or configure monitoring for high-risk command execution related to scheduled tasks, service manipulation, and living off the land binaries (lolbins). Monitor for the deletion of shadow copies and modifications to SafeBoot.sys (SafeBoot) and similar restore capabilities. Monitor for high CPU utilization on individual systems and across the network. Ensure security tool tampering logs are enabled and forwarded to the SIEM.
- Repeat, because trending ransomware families and your environment will change.
- Continuously evolve and grow your detective control capabilities.
WEBINAR
How to Build and Validate Ransomware Attack Detections
Learn tips to make your organization more resilient to ransomware attacks.
Watch the Webinar
Ransomware simulation
In this section, learn about ransomware attack simulation.
What is ransomware attack simulation?
Ransomware attack simulation is a collaborative, live test with a ransomware simulation tech-enabled service like NetSPI’s and your security operation center (SOC) team. During a ransomware simulation, we test your team’s visibility into your security controls and ability to detect each phase of real ransomware attack TTPs used by threat actors and malware.
Deliverables include a baseline report of your detective controls, a robust inventory of your security controls, custom recommendations to improve your security posture, as well as access to NetSPI’s continuous Breach and Attack Simulation platform to track your progress over time.
Tip: A ransomware simulation may identify an opportunity to stop paying for a software tool, such as a redundant endpoint detection and response tool, and free up budget for more valuable security efforts.
What is Breach and Attack Simulation?
Many companies spend millions of dollars on security controls and processes for ransomware prevention and detection, however, very few companies test if they really work. Would you know if an adversary was in your environment planning a ransomware attack? Breach and Attack Simulation (BAS) allows you to confidently answer this question.
Some key breach and attack simulation terms to understand first:
-
ProcedureA procedure is a description, recommendations, step-by-step attack instructions, and other educational content related to an attack behavior.
-
PlayA play is the automation of a specific manual procedure.
-
PlaybookA collection of plays that can be automated, ordered, and executed to simulate real-world threats.
-
OperationOperations define the scope of plays, playbooks, and the agents they run on, as well as the scope of detective control coverage tracking.
-
AgentThe software users download which runs the plays and playbooks.
-
TTPsTactic, techniques, and procedures
- Tactic: Tactics equate to the threat actor’s intended goal and reason for performing an action. This is the “WHY”.
- Technique: A technique is the broad description of how a threat actor accomplishes their goal. This is general “HOW”.
- Procedure: A Procedure is the specific action taken to accomplish the goal. This is specific click-by-click “HOW”.
NetSPI’s Breach and Attack Simulation (BAS) platform leverages a collection of pre-built procedures to simulate common attack TTPs. This helps clients determine if they can detect and respond to specific breach scenarios, including ransomware attacks, as well as other common attack types such as denial of service, data loss, fraud, information leaks and more.
Through BAS, NetSPI delivers a centralized detective control platform that gives companies the ability to create, execute, and automate pre-loaded and customized procedures. Utilizing purpose-built technology and professional human penetration testers, NetSPI can simulate real-world ransomware attack behaviors, not just IOC’s, to put your detective controls to the test in a way no other organization can and validate detection and response throughout the cyber kill chain.
Ransomware security terms
In this section are security acronyms that you may encounter as you learn about ransomware.
- AC: Access Control
- APT: Advanced Persistent Threat
- ASR: Attack Surface Reduction
- AV: Antivirus
- C2: Command and Control
- CIA: Confidentiality, Integrity, and Availability
- CIRT: Computer Incident Response Team
- CISA: Cybersecurity and Infrastructure Security Agency
- CMDB: Configuration Management Database
- CSF: Cybersecurity Framework
- CSIR: Computer Security Incident Response
- CSP: Cloud Service Provider
- CVE: Common Vulnerabilities and Exposures
- DAST: Dynamic Application Security Testing
- EDR: Endpoint Detection and Response
- FSISAC: Financial Services Information Sharing and Analysis Center
- GRC: Governance, Risk, and Compliance
- HIDS: Host-based Intrusion Detection System
- IAM: Identity and Access Management
- ICS: Industrial Control Systems
- IDS: Intrusion Detection System
- IOC: Indicators of Compromise
- IOT: Internet of Things
- IPS: Intrusion Prevention System
- IT: Information Technology
- ITAM: Information Technology Asset Management
- ITSM: Information Technology Service Management
- MFA: Multi-Factor Authentication
- MSP: Managed Service Provider
- MTD: Maximum Tolerable Downtime
- NAC: Network Access Control
- NAS: Network Attached Storage
- NDR: Network Detection and Response
- NVD: National Vulnerability Database
- OSINT: Open-Source Intelligence
- OT: Operational Technology
- RaaS: Ransomware as a Service
- RBAC: Role-based Access Control
- RCE: Remote Code Execution
- RPO: Recovery Point Objective
- RTF: Ransomware Task Force
- RTO: Recovery Time Objective
- SAR: Suspicious Activity Report
- SAST: Static Application Security Testing
- SCA: Software Composition Analysis
- SEIM: Security Information and Event Management
- SEM: Security Event Management
- SI: System and Information Integrity
- SOAR: Security Orchestration, Automation, and Response
- TIP: Threat Intelligence Platform
- TTP: Tactics, Techniques, and Procedures
- TVM: Threat and Vulnerability Management
- VM: Vulnerability Management
- VPN: Virtual Private Network
- WAF: Web Application Firewall
How NetSPI can help
Reduce risk with ransomware attack simulation services
NetSPI’s ransomware attack simulation service raises the ransomware security awareness in your organization, measures ransomware prevention and detection controls, and provides prescriptive guidance to improve your ransomware security posture. NetSPI’s cybersecurity experts work with your team to evaluate your security controls against the tactics, techniques, and procedures (TTPs) used by real-world ransomware families. You can continue to use our Breach and Attack Simulation platform after the engagement to run custom ransomware exercises and develop and test your ransomware playbooks.
Contact us to learn more and get a quote.
