Get the Report: 2024 GigaOm Radar Report for Attack Surface Management

Better attack surface visibility starts here
Access the 2024 GigaOm Radar Report for Attack Surface Management (ASM) to help select the best Attack Surface Management solution to advance your security posture. Learn about the top 22 global vendors in the space, including NetSPI ASM, which is positioned as a Fast Mover and Leader in the GigaOm ASM Radar Report.
“NetSPI demonstrates exceptional capabilities in asset discovery and vulnerability assessment. Its discovery capability is class-leading, offering granular findings and comprehensive results that surpass most competitors. The platform’s active assessment of vulnerabilities is bolstered by powerful automations, complemented by the human creativity of consultants, resulting in a nuanced identification of true risk.”
– 2024 GigaOm Radar for Attack Surface Management (ASM)
Access the GigaOm ASM Radar Report to learn
- The latest security outlook for ASM
- An assessment of 22 of the top ASM solutions
- How ASM helps manage the rapidly expanding attack surface
We’re honored that NetSPI ASM is recognized as one of 22 ASM solutions in the GigaOm ASM Radar Report. See what sets us apart and learn about the ASM landscape by accessing the report.
Access the Report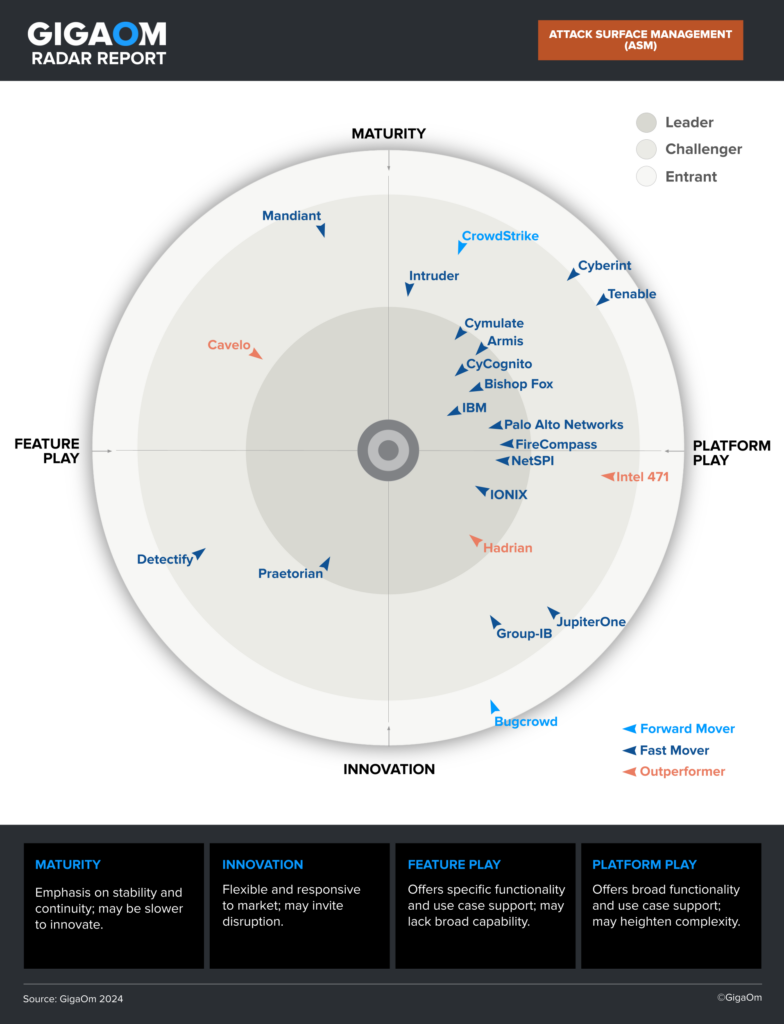
The challenge with attack surface visibility
Today’s attack surface is continuously expanding with many organizations having thousands of internet-facing assets with potential exposures. The ability to find, manage, and protect these assets presents a challenging but critical task that has the potential to leave organizations vulnerable to cyberattacks.
The solution that saves your team time
NetSPI ASM combines advanced technology to continuously scan your external perimeter with human intelligence to deliver results tailored to your environment. Our technology, process, and security experts save your team time, allowing them to focus on the exposures and vulnerabilities that matter most.
Learn the latest about ASM by accessing the GigaOm ASM Radar Report.
Access the Report