How to Select the Best Attack Surface Management Platform
As companies’ attack surfaces continue to expand and threat actors remain relentless, attack surface management (ASM) has grown to a rapidly emerging category in the cybersecurity space. Rather than organizations manually inventorying and protecting critical assets on their own, attack surface management tools provide continuous visibility and risk assessment of a company’s entire attack surface.
Teams looking to improve their offensive security efforts have many attack surface management tools to choose from, but most only provide standard asset discovery – such as the use of off-the-shelf scanners – and lack prioritization of actionable remediation efforts, resulting in alert overload.
We asked our team of attack surface management experts for their thoughts on which features security leaders should look for in ASM platforms to ensure they’re getting the best value and highest level of protection. The most effective attack surface management tools go beyond asset discovery by adding expert human analysis to prioritize alerts and remediation.
6 Must-Have Features in an Attack Surface Management Platform
As you weigh the pros and cons of various attack surface management platforms and tools, consider the following must-have features.
1. Ability to Comprehensively Discover the Unknown
Many attack surface management tools may only have the capabilities to discover known assets, such as IP addresses, domains, software, and other assets that the security team actively manages. However, finding and securing both known and unknown internet-facing assets is an essential capability for attack surface management tools.
Unknown assets may include those that lack awareness from the IT security team, unauthorized and unmanaged assets. There are a variety of causes for these gaps in known assets including shadow IT, misconfigurations, failed decommissions, and more. These gaps ultimately result in ineffective scan coverage and scopes for pentests, thus leaving your attack surface unmonitored and presenting a risk to your organization.
When you leverage an attack surface management platform like NetSPI, ASM engagements start with a list of known domains and IPs. Next, the search expands to related entities to uncover all assets tied to a company – including unknown assets. The Dynamic FAQs feature in NetSPI’s attack surface management platform shows how many IPs were initially provided, compared to how many public-facing assets were found.
2. Inclusion of Human Analysis to Prioritize Alerts
Our 2023 Offensive Security Vision Report showed that a lack of resources and prioritization are two of the top barriers to greater offensive security. Helping security teams with data-driven prioritization of remediation efforts eases the burden of decision-making.
Expert human analysis delivers the strongest cybersecurity results because pentesters provide context into alerts, which results in only alerting on high-impact vulnerabilities. Attack surface management tools that incorporate human analysis can leverage the team’s expertise to vet vulnerabilities before they’re added as alerts.
Manual pentesters review every exposure to contextualize it and determine whether they’re exploitable. This helps eliminate alert fatigue, drastically reduces the amount of work teams need to do, and enables teams to focus on meaningful remediation efforts.
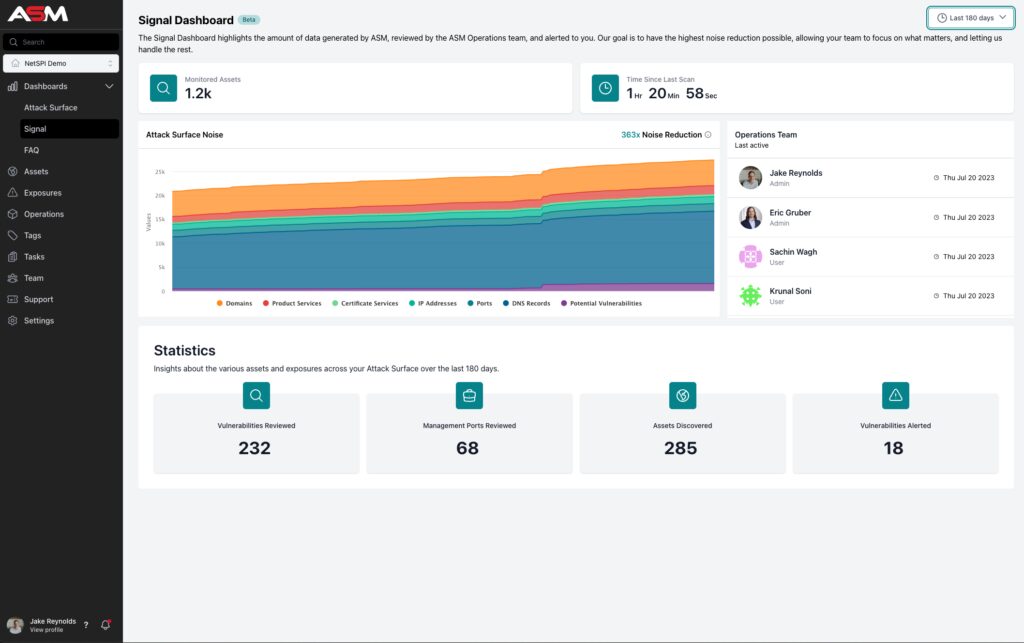
As an example of this approach in practice, NetSPI addresses this with a Signal Dashboard to distill signal from noise. This dashboard highlights all the activities of the ASM Operations Team, so clients can understand what’s happening behind the scenes even if they haven’t been alerted to new vulnerabilities in a while.
3. Ability to Track Attack Surface Changes Over Time
A key benefit of attack surface management is discovering attack surfaces that were previously unknown. A traditional approach to tracking attack surfaces has been manually tracking externally facing assets. However, because attack surfaces and threats can evolve and expand overnight, this approach isn’t enough to track changes and secure new attack surfaces that emerge throughout the year.
Rather than only performing annual pentesting, relying on a combination of external network penetration testing and comprehensive, continuous attack surface management enables organizations to track expanding attack surfaces and find vulnerabilities as they arise.
With the right attack surface management platform, once the initial report is complete and critical vulnerabilities have been addressed, the attack surface management platform performs regular evaluations of a company’s entire attack surface on an ongoing basis.
This inventories new attack surfaces as they arise and shows all data in one user-friendly platform.
4. Expertise to Develop New Features In-House Based on Customer Priorities
As cyber threats evolve and persist, security solutions also need to adapt to protect against the latest attacks and align with customers’ business needs. Working with customers is a two-way street for ASM vendors to advance technology capabilities.
The best attack surface management platform provider will listen to customers to help drive feature development and platform enhancements. Based on input from customers, a team of software engineers has the capability to update and build new features in-house.
When you work with NetSPI, you get incredible value through our technology and expert team, but one of the greatest benefits is that we are continually improving our platform to add more value every time you log in. Interested in learning more about our latest updates? Read our release notes.
5. A Clean, Easy-to-Use UX
As is the case with any product, software, or platform, attack surface management end users won’t settle for poor user experience (UX) or a clunky product with too many clicks to get to a destination. User-friendly design, easy to digest dashboards, and training materials at the ready are essential for the best attack surface management tools. Some platforms even have dark mode to meet anyone’s preferences.
6. Capabilities Beyond ASM into Related Market Categories
Features and capabilities that go beyond attack surface management and into related market categories are beneficial for organizations to continue evolving and advancing their offensive security strategies.
Additional capabilities to look for in an attack surface management platform include but aren’t limited to:
Partnering with a vendor like NetSPI that offers services such as these can help ensure you’re backed with the right mix of offensive security methods for your business.
Access the Most Important Attack Surface Management Features with NetSPI
Asset discovery with attack surface management is table stakes and the right vendors go far beyond this approach to provide the best possible offensive security solutions.
NetSPI’s attack surface management platform and solutions include human analysis to prioritize alerts, the ability to discover the unknown and track attack surfaces changes over time, capabilities to develop new features in-house, a user-friendly experience, and additional security services that go beyond ASM.
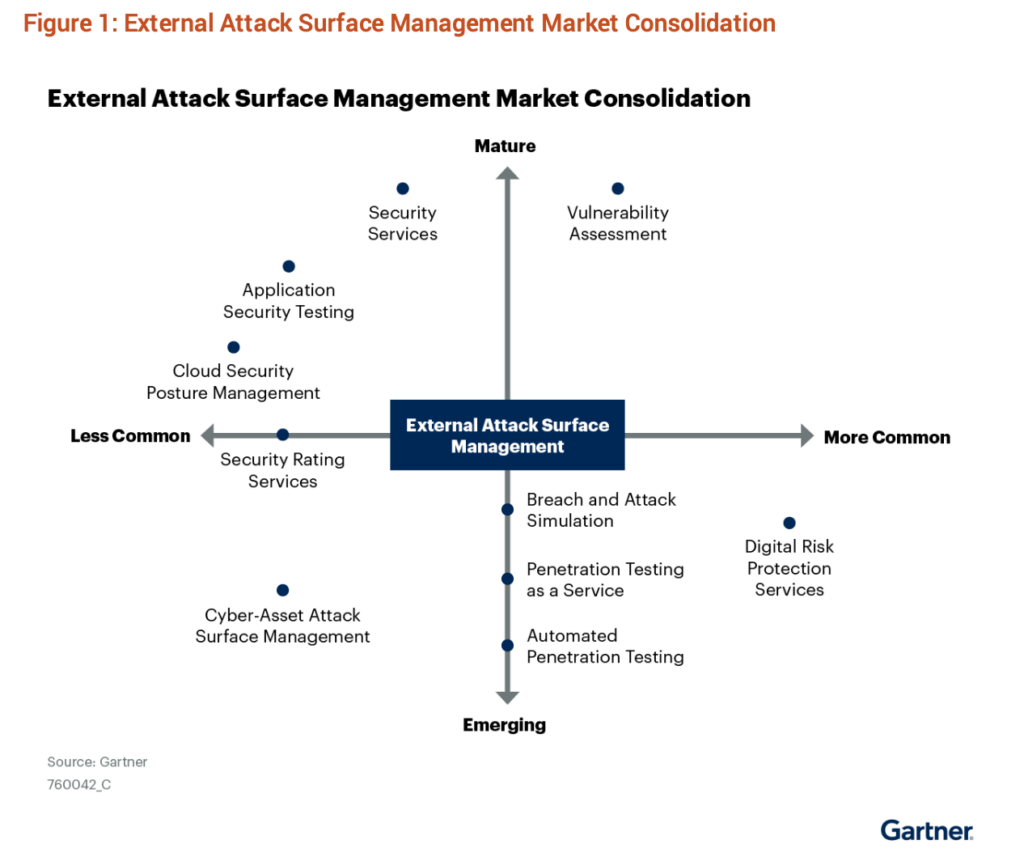
Want to hear about ASM from a third party? Gartner® provides recommendations on vendor capabilities in the report, Competitive Landscape: External Attack Surface Management. Take a look and then try our free Attack Surface Management Tool to search more than 800 million public records for potential attack surface exposures.






