
Important Trends Among Masked Identities
This year, the VPN industry alone is expected to grow beyond $31 billion. And among the 4.33 billion active Internet users around the world, over 31 percent have used a VPN.
As popular as VPNs are, they only represent a small percentage of IP masking methods. Others include proxies, tor, relay usage, or a connection via a hosting provider, which can potentially be used to tunnel traffic.
And while some masked IPs are simply trying to protect their online personal information, many others hide their identity for malicious purposes such as exploiting server vulnerabilities, executing MITM attacks, stealing sensitive data, and more.
A recent study by IPinfo identified some interesting trends among masked IP addresses. Among these findings are some important takeaways for high-risk IP ranges, allowlisting/denylisting IPs, preventing IP spoofing, and ultimately securing cloud infrastructure by reducing your attack surface.
Here are the important metrics we’ll consider, from which we’ll draw applications for infrastructure security.
- IPv4 versus IPv6 usage among masked identities
- Comparison of most common IP masking methods
- Deep dive into the most-widely-used VPN services
IPv4 versus IPv6 Usage Among Masked Identities
The team at IPinfo tracked IP masking on IPv4 and IPv6 addresses separately by running two separate queries in the database. For IPv4:
select SUM(func.f_rough_range_size(`range`))
from ipinfo.privacy
where func.f_ip_family(`range`) = 4;
We then ran a similar query on all IPv6 addresses.
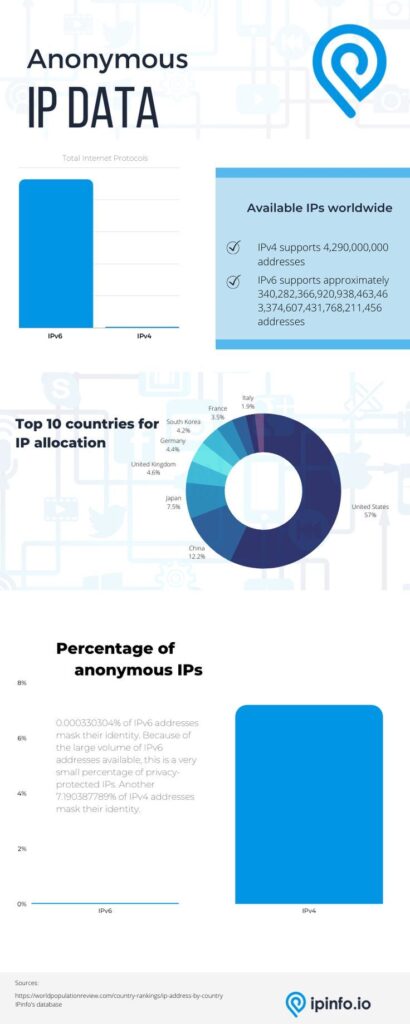
Of IPv4 addresses, around 308,824,804 users hide their identities. Approximately 1.1239648737961904 x 10-33 IPv6 addresses mask their IP address.
As you may have expected, the difference in these numbers is due largely to the massive pool of IPv6 addresses available. But as IPv6 adoption continues to grow, we expect to see even more masked IPs using IPv6. Here’s how IPv6 has grown over the past few years.
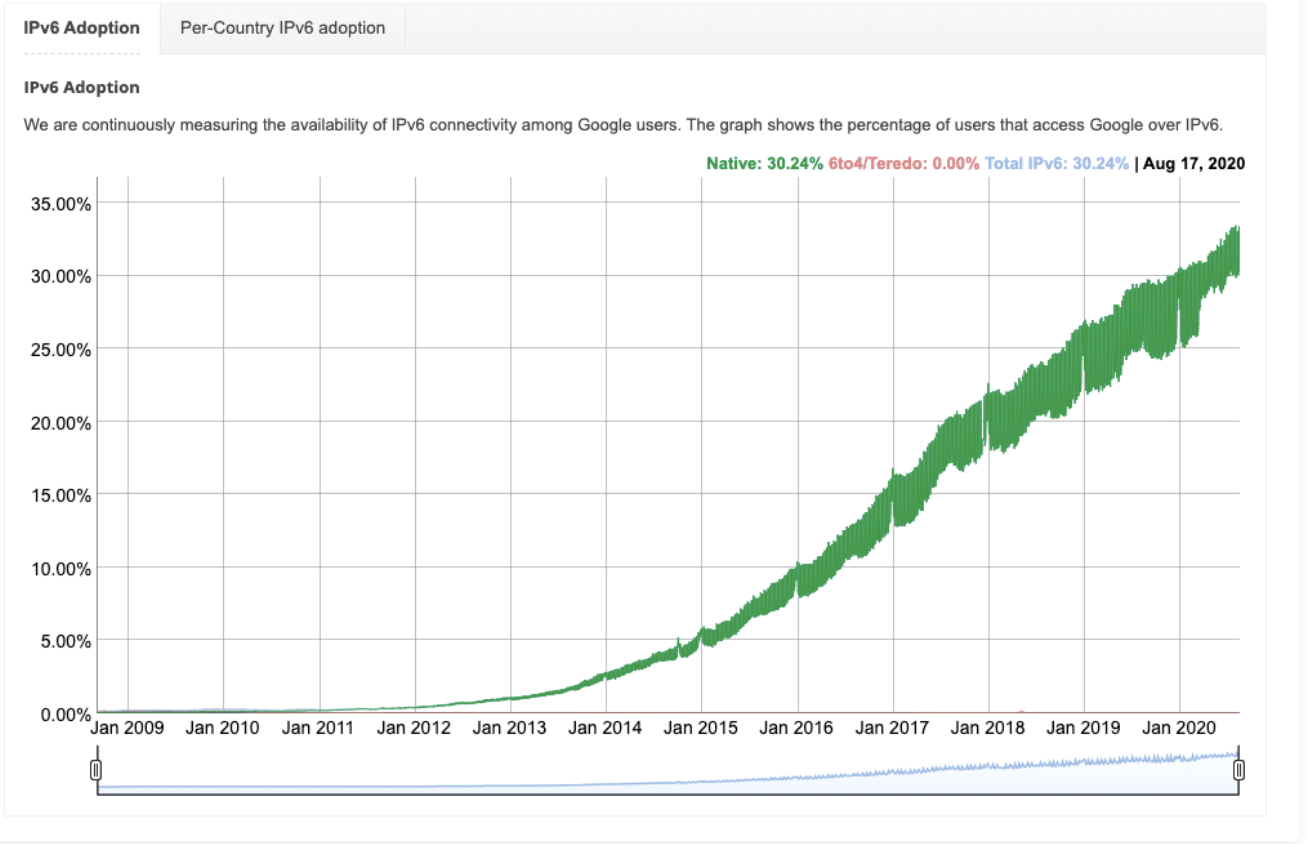
Percentage-wise, 0.000330304% of all IPv6 addresses hide their identity, and approximately 7.190387789% of all IPv4 addresses hide their identity.
It’s important to remember that IPv6 addresses have some added layers of security. Built into IPv6 are IPSec – IETF security protocols that promote authentication, security, and data integrity. While IPSec can be added to sites, servers, and routers using IPv4 addresses, the implementation is more expensive and therefore not widely used.
That being said, IPv4 addresses have a higher risk from malicious bots and spammers. But IPv6 security protocols don’t necessarily insulate these IPs from masked identities either.
When it comes to cloud penetration testing, identifying and tracking IPs is a very important component.
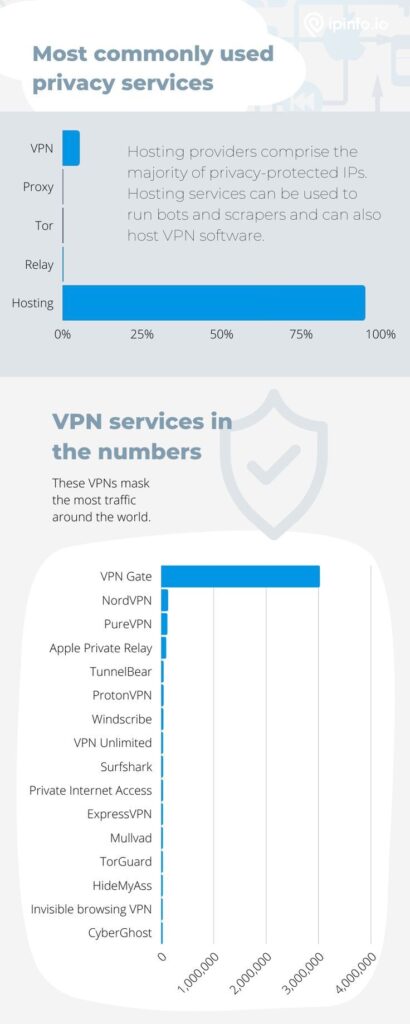
Comparison of Most Common IP Masking Methods
Among the many methods that exist for masking IPs, we found that the most common is hosting services – over 95 percent in fact. VPNs come in second place with around 5.24 percent.
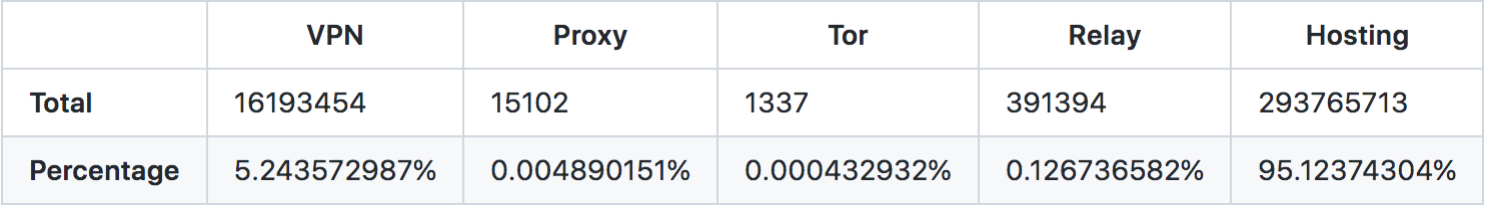
Hosting providers often help bots and spammers hide their IPs. Plus, VPNs can also be operated through hosting services. This contributes to the large number of masked IPs attributed to hosting providers.
Another interesting stat is that Apple Private Relay (APR) is currently the third most popular method for masking IPs. While it only consumes 0.12 percent of all anonymous IPs, its ranking has significantly grown since APR’s release in 2021.
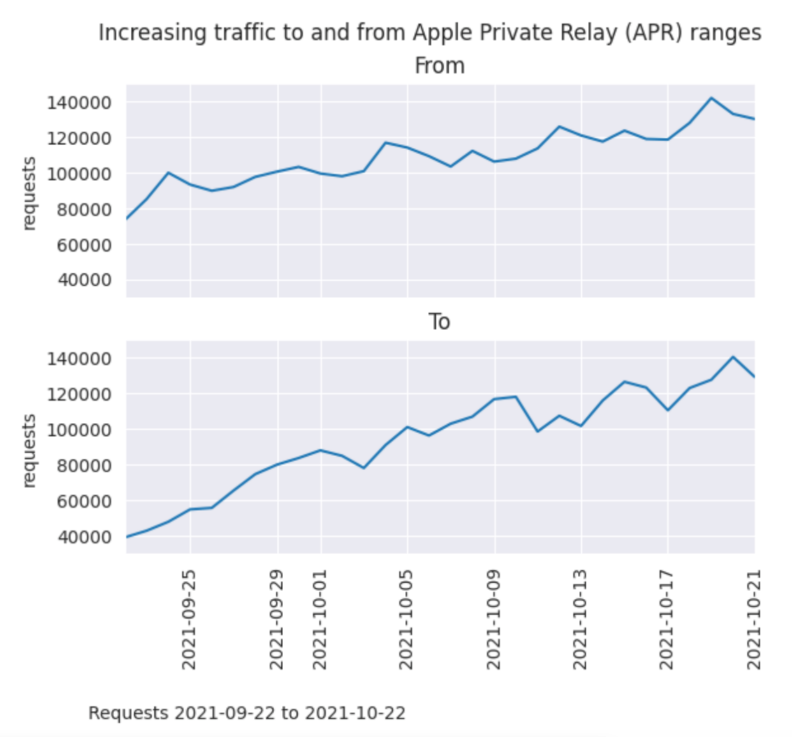
APR traffic growth is also important because it’s geo-aware. Users can’t tunnel their IP to a different location using APR. While APR protects personal identifiers such as IP addresses, it still provides accurate, generalized location data. Ultimately this led to IPinfo working with Apple to create a geo-aware feature within our Privacy Detection dataset.
Deep Dive into the Most Common VPN Services
All of these other metrics led our team to wonder what VPNs are used the most. We found that VPN Gate outranks all other services. There are several probable reasons for this ranking. Most importantly, VPN Gate is free, and it’s open-source.
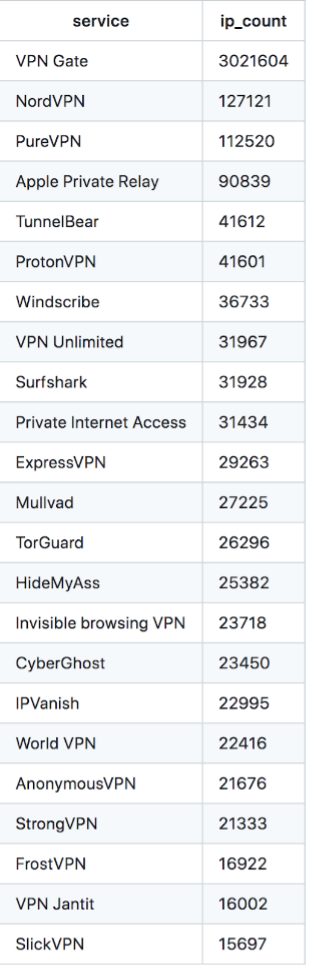
For VPN users these seem like upsides, but on the penetration testing side, VPN Gate’s free, open-source infrastructure may be vulnerable to MITM attacks due to misuse of the SSL certificate. Because VPN Gate lacks SSL certificate verification at the client site, a MITM attacker can hijack an IP by modifying the IP destination address and then implementing a TLS MITM attack.
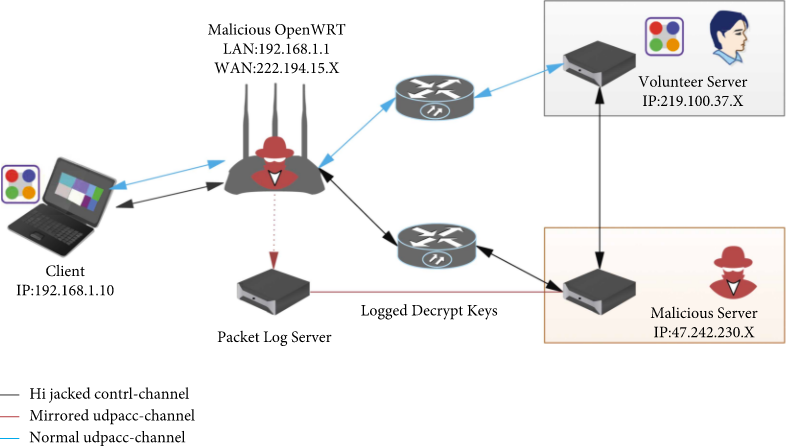
Needless to say, this introduces vulnerabilities to both the VPN user and the sites, servers, and other infrastructure they access, leading to information theft, data breaches, compromised infrastructure security, and more.
For instance in 2013, Apple’s Fairplay – a digital rights management system – was attacked by a MITM attack, leading to pirated distribution of proprietary content. Since then, Fairplay MITM attacks have been used by other malicious entities to steal Apple IDs and passwords.
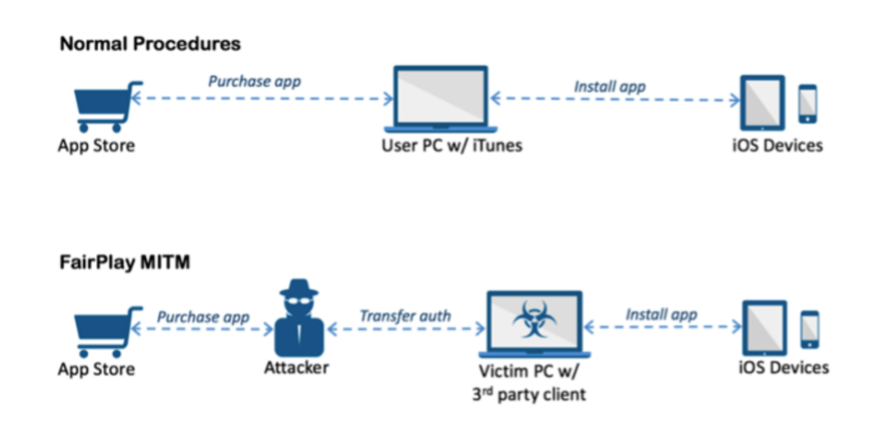
What You Should Know About Geo-aware Services
As was mentioned in the previous section, APR is gaining traction among VPNs. Currently, it ranks fourth in our IP count below NordVPN and PureVPN.
| Service | Number of IPs |
| VPN Gate | 3021604 |
| NordVPN | 127121 |
| PureVPN | 112520 |
| Apple Private Relay | 90839 |
Separating APR traffic from other VPN users can be useful. APR users differ from VPNs because they seem to be more concerned about protecting their personal information than hiding their general location.
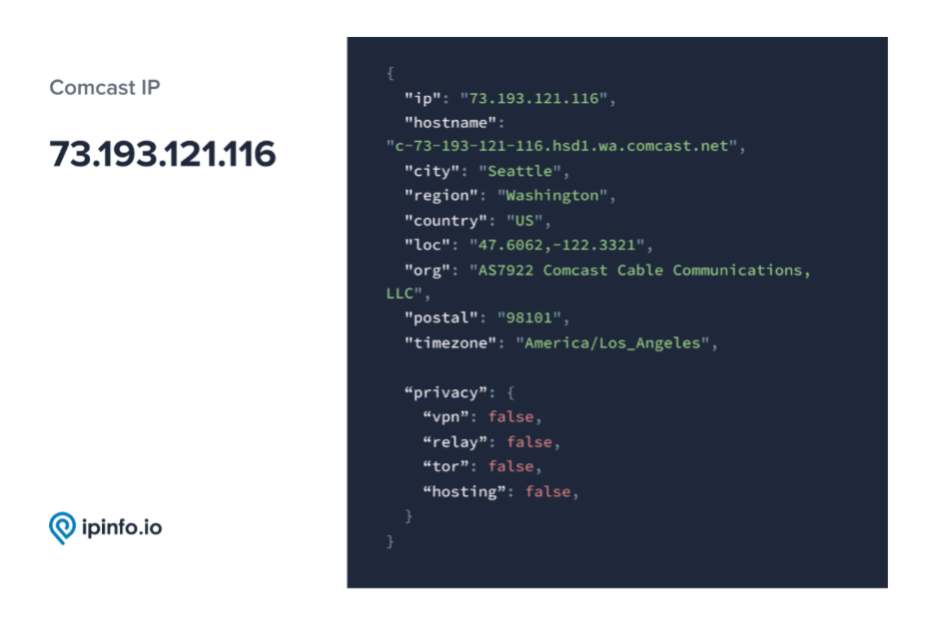
For instance, here’s a comparison of responses from IPinfo’s Privacy Detection database. The first is a typical response for IPs that aren’t masked by VPNs, tor usage, or hosting providers.
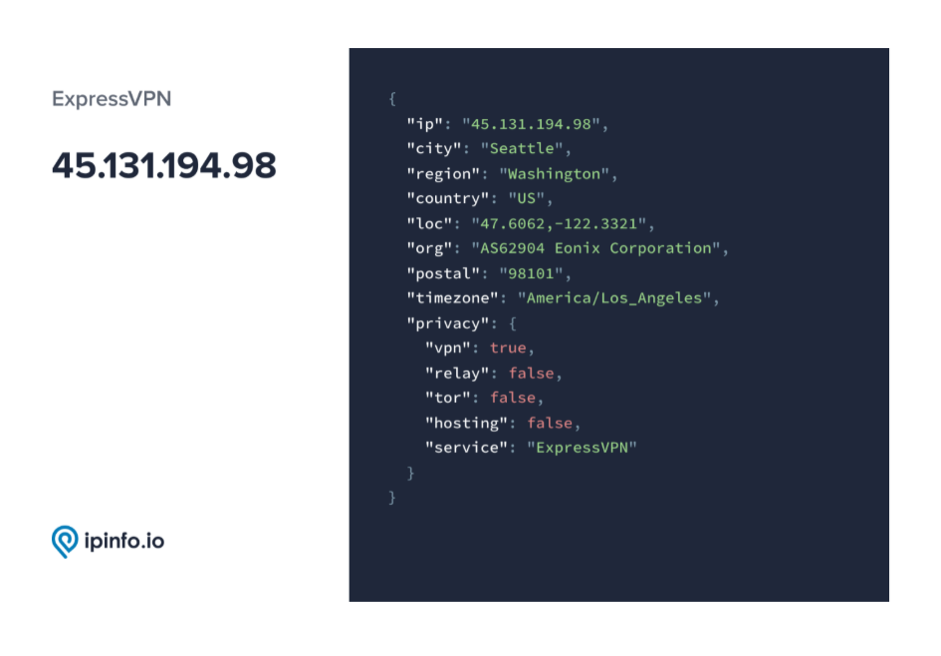
Shown below is what a typical Privacy Detection response reveals about masked IPs:
And finally, here’s what Privacy Detection queries show for APR users.
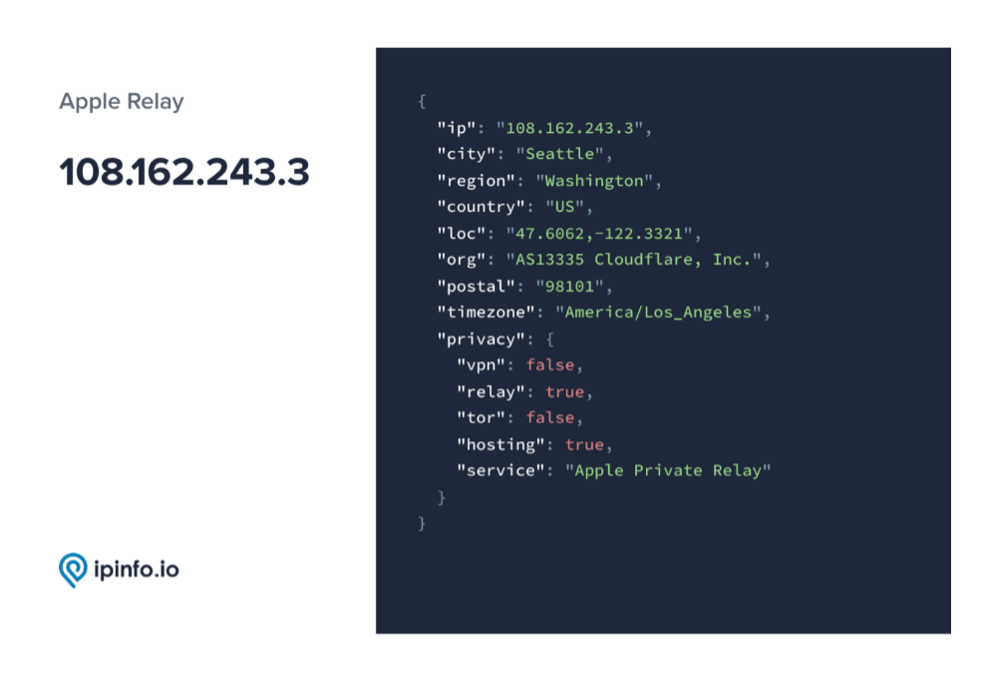
In contrast to the masked identity example, the APR response shows that this IP is located near Seattle, Washington. APR data, even though it’s masked, still contains useful information for penetration testing.
The fact that APR is one of the most-used privacy services means that there’s more threat intelligence to be gained from this somewhat anonymous data. As more geo-aware services come onto the market, IPinfo is ready to implement them into our Privacy Detection datasets.
For industries with high stakes – such as Fintech, Cybersecurity, Healthcare, and others – security issues from VPNs can introduce additional vulnerabilities. Privacy Detection data is one tool that can help digital rights management and digital infrastructure security develop mature application security programs, reduce attack surfaces, secure your networks, and more.
Try IPinfo’s Privacy Detection data for free. Sign up for a weeklong free trial of all our APIs.
NetSPI leverages IPInfo’s geolocation data set to identify new and changing IP addresses in our Attack Surface Management platform. Learn more about the platform capabilities: https://www.netspi.com/attack-surface-management/asm/.
Explore More Blog Posts

Extracting Sensitive Information from Azure Load Testing
Learn how Azure Load Testing's JMeter JMX and Locust support enables code execution, metadata queries, reverse shells, and Key Vault secret extraction vulnerabilities.

3 Key Takeaways from Continuous Threat Exposure Management (CTEM) For Dummies, NetSPI Special Edition
Discover continuous threat exposure management (CTEM) to learn how to bring a proactive approach to cybersecurity and prioritize the most important risks to your business.

How Often Should Organizations Conduct Penetration Tests?
Learn how often organizations should conduct penetration tests. Discover industry best practices, key factors influencing testing frequency, and why regular pentesting is essential for business security.