Activate Proactive Security With The NetSPI Platform
The NetSPI Platform brings a proactive approach to tackling the most urgent cybersecurity challenges today: visibility and prioritization of assets, vulnerabilities, and exposures.
Take a Holistic Approach to Proactive Security

Discover
Gain a single source of truth for real-time visibility into your entire attack surface, both known and unknown, and internal and external assets.

Prioritize
Leverage NetSPI’s combination of security experts, intelligent process, and advanced technology to add business context and prioritize the most impactful findings.

Remediate
Trust in a proactive process that prioritizes the remediation of your team’s security vulnerabilities of the highest importance.
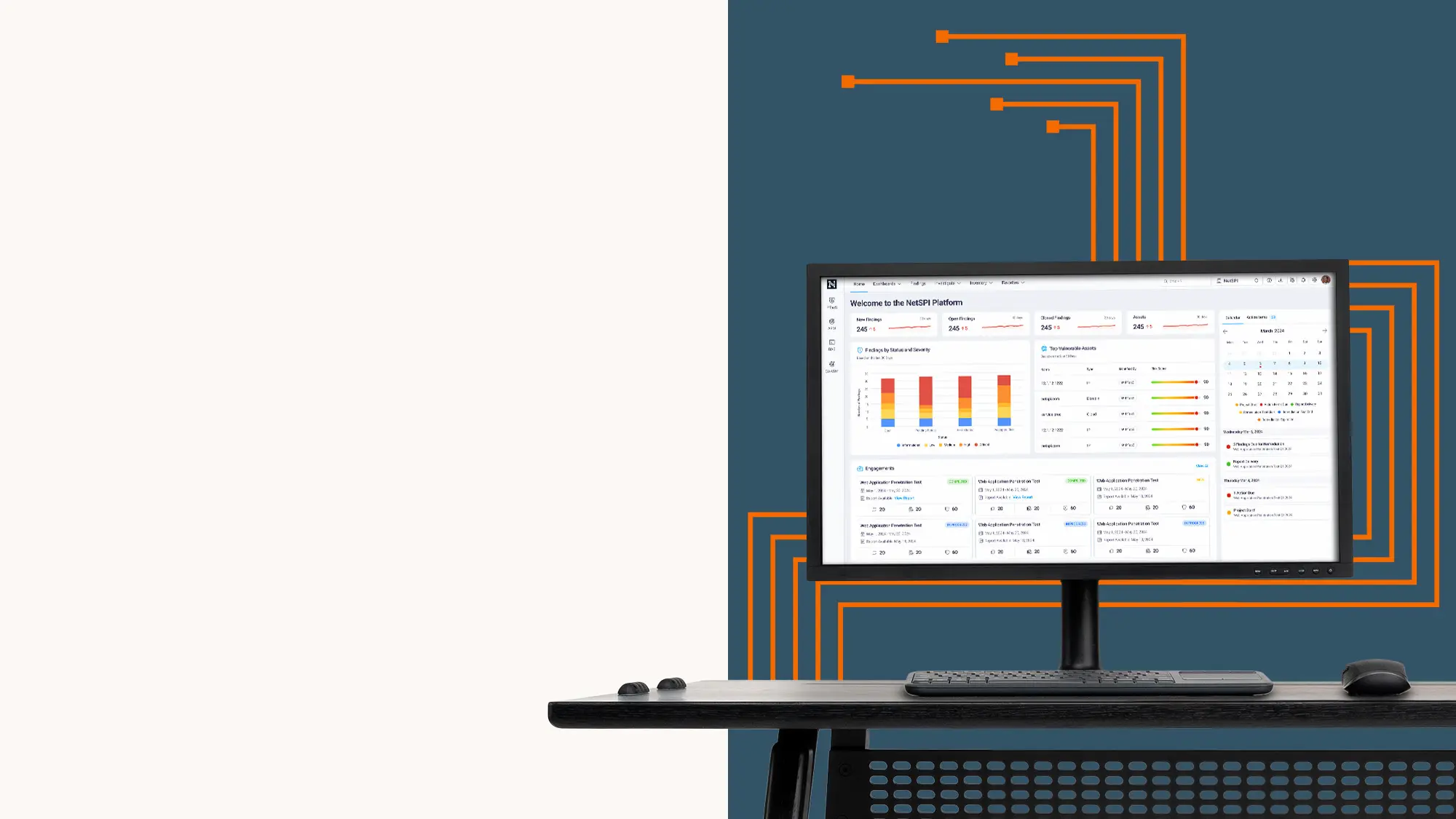
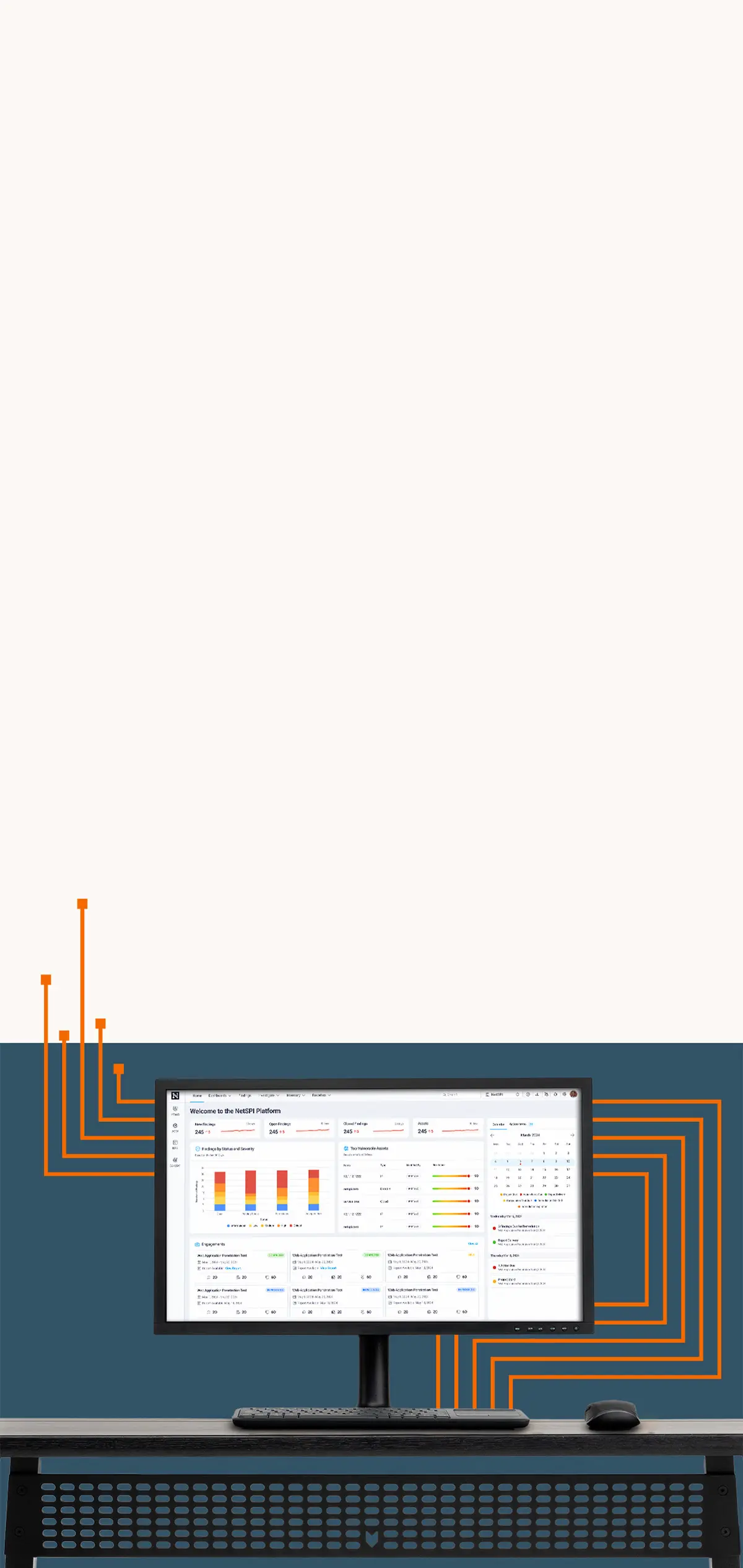
See The NetSPI Platform in Action
See how The NetSPI Platform delivers a dynamic asset inventory with improved asset and data fidelity, and how it reduces administrative tasks by integrating easily with existing workflows to accelerate time to remediation.

You Deserve The NetSPI Advantage

Security Experts
- 300+ pentesters
- Employed, not outsourced
- Domain expertise

Intelligent Processes
- Programmatic approach
- Strategic guidance
- Delivery management team

Advanced Technology
- Consistent quality
- Deep visibility
- Transparent results