Resource Types
eBooks & Whitepapers
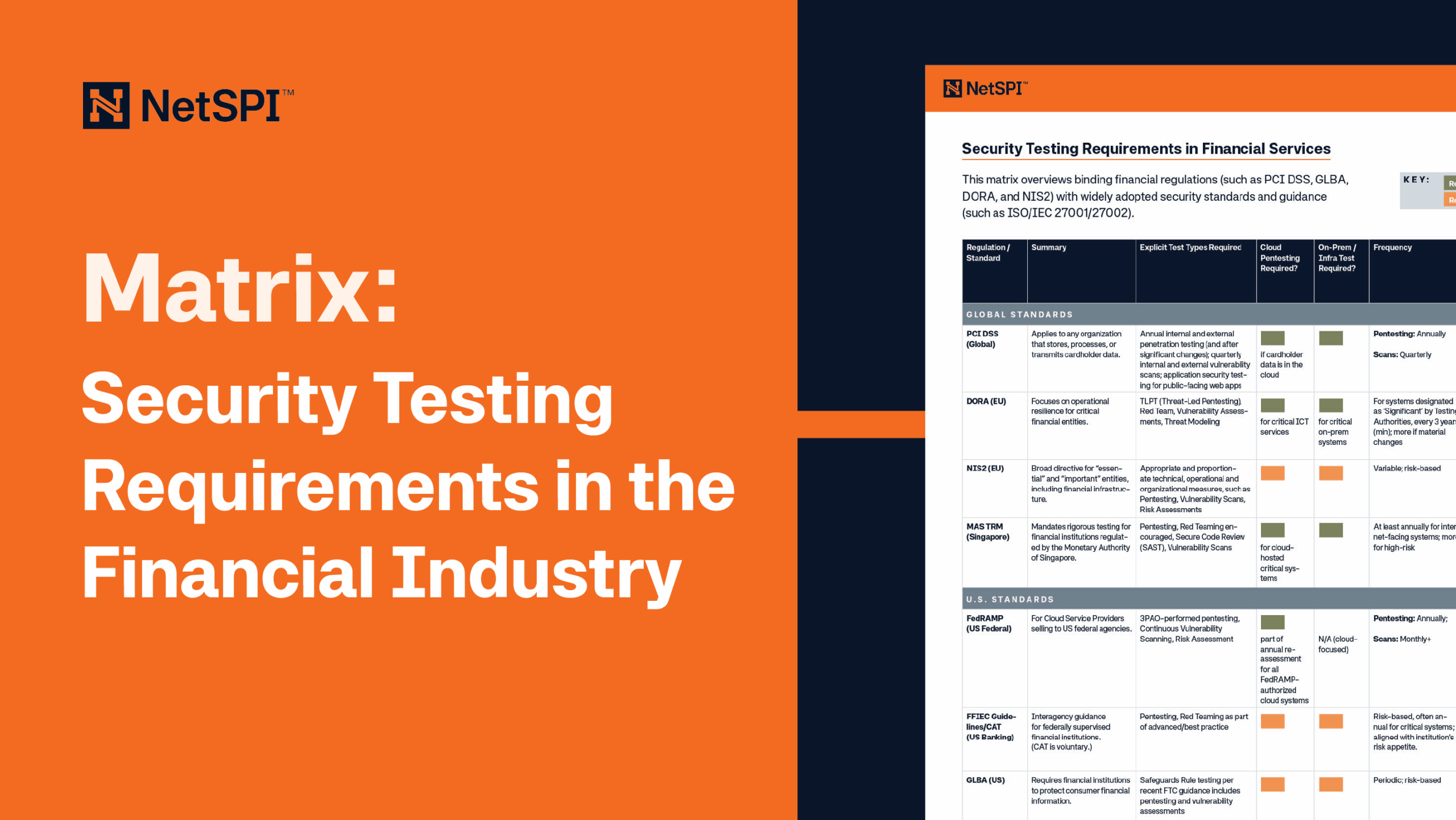
Financial Industry Security Testing Requirements Matrix
This comprehensive matrix breaks down financial industry security testing regulations (such as PCI DSS, GLBA, DORA, NIS2, and ISO/IEC 27001/27002)

2026 Cybersecurity Trends
Dive into the top cybersecurity trends that are shaping the industry in 2026 and beyond directly from NetSPI's leading security experts.

API Security Best Practices
APIs are central to digital business operations, and their rapid adoption expands the attack surface, making these targeted API security testing best practices essential.

Proactive Security Testing for Financial Institutions
With 54% of financial institutions experiencing attacks in 2025, it's imperative for this industry to adapt modern proactive testing strategies to stay a step ahead.

10 Commandments of Red Teaming
A red-teamer's dos and don'ts for effective and ethical security scenarios.

The Subtle Art of Successful Red Teaming
Answer the critical business question: “How resilient are our people, processes, and technology when faced with a skilled attacker?”

Decoding DORA for Operational Resilience
A practical guide to prepare security leaders for their upcoming DORA testing engagements.

The Ultimate Guide to Modern Penetration Testing as a Service (PTaaS)
Discover how to proactively secure your organization with our Ultimate Guide to Modern Penetration Testing as a Service. Learn to hunt vulnerabilities and build a resilient defense.

Continuous Threat Exposure Management (CTEM) For Dummies
Discover how to advance your team's approach to CTEM with Continuous Threat Exposure Management For Dummies.
5 Blockchain Security Fundamentals Every C-Suite Needs to Know
Learn why blockchain optimization and security go hand-in-hand. The emerging use of blockchain makes cybersecurity a priority for secure deployments.

The Ultimate Guide to Ransomware Attacks
Learn best practices and tools for your vulnerability management tracking system Find out what does not work – and what does!

Rein in Attack Surface Sprawl with Cyber Asset Attack Surface Management (CAASM)
See how CAASM brings peace of mind with comprehensive visibility into your attack surface. Access our Cyber Asset Attack Surface Management eBook.

The Complete Guide to Healthcare Ransomware Attacks
This complete guide to healthcare ransomware attacks explores how ransomware attacks affect healthcare and how to get ahead of it.
The CISO’s Guide to Securing AI/ML Models
Empower your AI journey with security from the start. Learn how to navigate the nuances of Adversarial Machine Learning (AML) and safeguard your LLMs.

NetSPI Attack Surface Management Case Studies
These Attack Surface Management (ASM) case studies demonstrate its ability to advance offensive security and protect the perimeter.

Proactive Security Stories
Explore the world of NetSPI's penetration testing experts, with six real stories featuring our critical discoveries, unique approaches, and the impact we’ve made on some of the world’s most prominent organizations.

Azure Cloud Penetration Testing Stories
Explore critical discoveries and unique approaches from NetSPI's top cloud penetration testers in our ebook. Learn how to improve Microsoft Azure Cloud security.

How Much Does Penetration Testing Cost?
Explore the six core components that impact the average cost of a penetration test.

How to Choose a Penetration Testing Company
Learn questions to ask penetration testing providers and how to select the best penetration testing service for your organization.