Pew Pew, Precisely: The Physics and Practices Behind RayV Lite

Whenever sophisticated hardware attacks such as laser fault injection are discussed, a common comment is that such techniques are only relevant to well-resourced adversaries — i.e., “nation-states”, if you will. This belief that only governments or large corporations — with multimillion-dollar labs and specialized equipment — can execute these attacks, can lead to dangerous oversight in silicon protections and supply chain security.
Given that by underestimating the real-world accessibility and impact these techniques can have; we recognized was an addressable concern, as very few people were testing for flaws, and fewer had the access to devices to learn how to. Thus, we decided to democratize this “advanced hardware security technique”, by creating the RayV Lite.
TL;DR
The RayV Lite is a low-cost laser fault injection platform built using open-source hardware and inexpensive IR-leaking lasers:
- Faults can be triggered with lower-power lasers by extending exposure time and aligning with clock cycles – a change from the norm of high-power lasers.
- The platform supports Infrared In-Situ Imaging to observe transistor-level activity and confirm glitching zones, allowing for chip targeting through the silicon using IR transparency.
Understand the physics, engineering, and real-world results behind how the RayV Lite is making light-based techniques and attacks, like laser fault injection, accessible.

When we set out to prove that laser fault injection wasn’t limited to nation-states, our biggest challenge was cost. Leveraging the OpenFlexure project helped us solve much of the hardware positioning problem, but that still left us without a laser. High-end lasers used in commercial setups are powerful and precise, but expensive. To reach our goals, we turned to something less conventional: a $9 green laser pointer from a big-box store.
Safety Note: Many consumer green lasers emit invisible infrared that poses a serious eye hazard.
Proper filtering, safety goggles, and lab practices are essential when replicating this setup.
Why an Inexpensive Laser Works
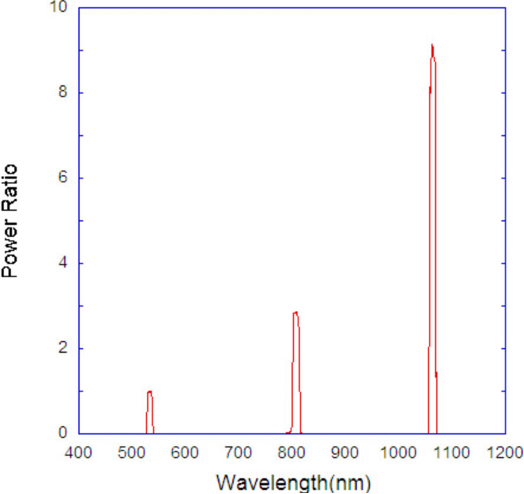
These off-the-shelf lasers are technically classified as Class III devices under the 5mW safety threshold. However, this designation relies on a technical sleight of hand. These aren’t native 532 nm (green) lasers, they’re 1064 nm infrared (IR) lasers, pumped by 808 nm diodes and passed through a frequency-doubling crystal to produce the green beam. That crystal is only about 5% efficient, meaning 95% of the laser’s actual output remains in the infrared.
This IR output, which is invisible to the human eye, happens to be ideal for penetrating silicon. IR photons at 1064 nm are just above silicon’s bandgap (1.12 eV), allowing them to reach transistors without being immediately absorbed, an ideal condition for inducing faults via the photoelectric effect.
Attacking Through the Backside
Silicon is opaque to visible light but becomes translucent at longer IR wavelengths. To make things simple for us when testing: Instead of removing epoxy and attacking chips from above, we flipped the problem and accessed chips through the underside.
- The backside contains no fragile bond wires.
- The die is usually thick enough to withstand minor abrasions.
- Most of the shielding is on the top, leaving the underside exposed.


Using the backside, we could exploit IR penetration to reach the active transistor layer even though it was buried beneath microns of silicon.
Packaging Note: Our test devices used standard DIP and SOIC packages. Decapsulation was performed mechanically using manual grinding techniques. Acid etching was employed, though manual methods for this research were preferred to prove possibility in RayV’s accessibility and safety for reproduction.
Energy Matters: Green vs IR
We calculated the photon energy for 532 nm (green) light using Planck’s equation:
Where:
- h is Planck’s constant (6.626×10−34 J⋅s)
- c is the speed of light in a vacuum (2.998×108 m/s)
- λ is the wavelength in meters (532 nm=532×10−9 m)
We can convert this to electron volts (eV) using:
This gives ~2.33 eV per photon, well above the silicon bandgap. These photons are quickly absorbed and thus can’t penetrate deeply.
However, let us consider the other 95% of the laser beam, the infrared( IR).
Conversely, 1064 nm IR light produces photons around 1.17 eV; just above the bandgap. These photons can travel much deeper into the substrate, thus allowing photons to penetrate the silicon die, reaching the transistors of the target (Handbook of Optical Constants of Solids).
Transistor Glitching with Light
Allow us to shine a little light on the subject: why does this matter? Because transistors are inherently photodiodes, just extremely inefficient ones.
In a semiconductor like silicon, electrons are not “free” as they are in metals. Instead, they occupy distinct energy bands: the valence band, where electrons are tightly bound to atoms, and the conduction band, where electrons are mobile and can conduct electricity.
For fault injection, we are specifically interested in the photoelectric effect as a large group of photons strike the p-n junctions and depletion regions within the transistor. Transistors, especially in their “OFF” state, often have reverse-biased p-n junctions that create a depletion region, an area largely devoid of free charge carriers, but with a strong internal electric field.
When exposed to light in the right wavelength range, they absorb photons and allow electrons to jump from the valence band to the conduction band, injecting charge into the depletion region. This disrupts the normal electrical potential of specific areas of transistors thus inducing bit flips, skipped instructions, or change logic states during memory or instruction processing. With sufficient photons, fault conditions can be introduced though outcomes may vary statistically depending on the circuit design.
But Do We Have Enough Power?
Traditional commercial systems use high-energy pulses in the millijoule range and fire them over nanoseconds. It was thought that low-power laser pointer like ours could not compete with that.
Recent research demonstrated that fault injection thresholds are significantly lower than once believed: in the 40–80 nJ range (Kelly, M. (2022). Fault Attack Resilience on Error-prone Devices). Furthermore, studies suggest that energy from longer, low-power pulses may still trigger faults under specific conditions, particularly when the transistor state is held stable over time.
This is due to the theory that the charge associated with the photoelectric effect was culminated within a clock cycle, the charge would build within the bands until the threshold to change the state was triggered.
Using:
Where the total green light (532 nm) output:
Then, solving for time:
We determined that a 95 mW IR beam (from the “hidden” component of our laser) could deliver 42 nJ in just 0.44 μs. To accommodate this, we modified the timing on our test device.
Clock Control and Precision Timing
Our initial target, the Arduino, runs at 16 MHz (62.5 ns per cycle). To deliver a 0.42 μs laser pulse effectively, we replaced the onboard crystal oscillator with a programmable FPGA-based clock. This allowed us to pause time just long enough for the laser to accumulate sufficient charge.
This approach isn’t universal. Results depend on the memory timing, latch refresh behavior, and logic architecture of the chip under test. But in controlled conditions, it allows a low-power, long-duration pulse to achieve meaningful disruption.
Optics and Beam Targeting: RayV Lite uses a low-cost, manually adjustable optical path, based on the OpenFlexure microscope, with spot size approximating 0.5–1 μm depending on focus. This offers sufficient resolution for targeting SRAM blocks, registers, and control logic under test.
IRIS Imaging and Chip Visualization
RayV Lite doesn’t just support fault injection, it also enables infrared-based visualization using IRIS (Infrared In-Situ Imaging), a technique rooted in near-IR reflectometry (IEEE IR backside imaging). This enables us to use infrared-based visualization. This technique allows researchers to observe activity within a silicon device by leveraging IR transparency. While it doesn’t offer the resolution of advanced microscopy tools like OBIC or TIVA, it provides meaningful insight into logic-level switching and confirms a glitch location under controlled experiments.

Target Device Context and Fault Effects
Our testing focused on legacy and mid-tier microcontrollers in standard DIP and SOIC packaging. These targets were selected not because modern secure SoCs are unreachable, but because they represent realistic and currently deployed systems where laser fault injection remains feasible without requiring extreme precision optics or decapsulation. While RayV Lite is technically capable of targeting smaller node processes, such as those in advanced SoCs, these targets are often impractical due to cost and the availability of simpler, more repeatable software-level attack surfaces.
Observed fault behaviors included bit-flips in control registers, skipped instructions in boot sequences, and changes in memory I/O during clocked operations. These effects were consistent with induced charge during instruction fetches and aligned with known fault injection models. Repeatability was statistically measurable when timing was controlled.
Process Node and Silicide Transparency: Tests were conducted on 180 nm microcontrollers with minimal top-layer silicide, simplifying IR penetration. Denser nodes or FinFET structures would likely require increased power or enhanced optics, which are areas of ongoing research given the cost prohibitions associated with each area. At present, the RayV setup is capable of going smaller with more expensive options given user preference.
Broader Reflections and Conclusion
We began with a simple question: could laser fault injection be democratized? Our answer is a resounding yes. With back-of-the-envelope physics, modest optics, and basic spare parts, we created a replicable, low-cost method for laser-based hardware attacks. While the methodology requires hands-on skill and hardware familiarity, it significantly lowers the barrier compared to traditional laser fault injection labs costing tens if not hundreds of thousands of dollars.
This isn’t theoretical. It’s real, testable, and accessible to anyone with the skills and curiosity to try. RayV Lite exists to empower researchers, train students, and bring physical-layer security into the hands of those ready to explore it.


Interested in learning more about NetSPI’s
Hardware & Embedded Security team?
Explore More Blog Posts
7 Ways to Execute Command on Azure Virtual Machine & Virtual Machine Scale Sets
Examples of different command execution paths for Azure Virtual Machines and Virtual Machine Scale Sets.

NetSPI Recognized for Second Consecutive Year by GigaOm
For the second consecutive year, NetSPI has been recognized in the GigaOm Radar Report for Attack Surface Management.

CVE-2026-20127 – Cisco Catalyst SD-WAN Controller and Manager Authentication Bypass Overview & Takeaways
A critical authentication bypass vulnerability (CVE-2026-20127) has been identified in Cisco Catalyst SD-WAN Controller and Manager. This flaw allows unauthenticated, remote attackers to gain administrative privileges on affected systems. Exploitation in the wild has been confirmed, and immediate action is required to mitigate risk.




