
CTEM Defined: The Fundamentals of Continuous Threat Exposure Management
Cybersecurity challenges evolve daily, and organizations recognize the need to enhance their strategies to stay ahead of potential threats. Traditional vulnerability management frameworks are no longer enough to address the complex and expanding attack surface that enterprises face today. This is where continuous threat exposure management (CTEM) emerges as a powerful process for cybersecurity programs.
CTEM Definition: What is Continuous Threat Exposure Management?
CTEM is more than just a buzzword — it’s a vital shift in how organizations view and manage their security posture. A recent article in BizTech Magazine highlights experts’ insights on CTEM. In the article, Erik Nost of Forrester describes CTEM as “a new approach that unifies various proactive security solutions, offering a comprehensive view of vulnerabilities, visibility, and response orchestration.” By enabling continuous assessment of digital and physical assets for exposure, accessibility, and exploitability, CTEM provides a proactive approach to identifying and addressing modern threats. Now more than ever, proactive security strategies are critical in mitigating risks before they become full-blown security incidents, and in ensuring organizations stay cyber resilient.
According to Gartner, “What’s needed is a continuous threat exposure management (CTEM) program that surfaces and actively prioritizes whatever most threatens your business. Creating any such program requires a five-step process.”
According to Gartner, “What’s needed is a continuous threat exposure management (CTEM) program that surfaces and actively prioritizes whatever most threatens your business. Creating any such program requires a five-step process.” It allows organizations to continuously assess the accessibility, visibility, and exploitability of their digital environments. Unlike traditional risk-based vulnerability management (RBVM), CTEM expands beyond identifying vulnerabilities. It includes governance, process optimization, and long-term improvements to ensure vulnerabilities are remediated.
At its core, CTEM serves as a broader exposure management process that proactively minimizes risks while optimizing how organizations address and resolve security gaps. By integrating process improvement with technical threat assessments, CTEM shifts organizations from reactive to proactive security operations.
5 Steps to Implement a CTEM Program
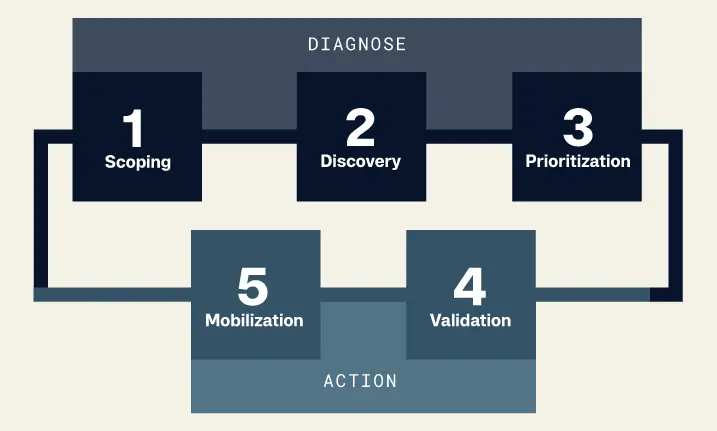
1. Scoping Process
Start by defining the scope of objectives and aligning them with your business priorities. During this process, you want to identify sensitive assets, evaluate potential impacts, and foster collaboration across your organization to establish a focused, business-aligned scope for managing threats.
2. Discovery Process
Consider using a combination of penetration tests and an attack surface management solution to gain visibility of all known and hidden assets. Penetration testing is an effective point-in-time test that provides a snapshot of how vulnerable your critical assets are, so you can prioritize what matters most in the next step of CTEM. Using an attack surface management solution will give you continuous visibility into all hidden and known assets and manage the attack surface. These insights help you establish a clear understanding of your threat landscape.
3. Prioritization Process
Not every risk can be remediated immediately, so focus your resources on those with the highest potential impact. Balance technical severity with business relevance to ensure that you’re addressing the most critical vulnerabilities first, particularly those most likely to be exploited.
4. Validation Process
Test and retest your vulnerabilities to verify if they can be exploited, and ensure that mitigation efforts are effective. This is where breach and attack simulation, red teaming exercises, and additional penetration tests can validate the efficacy of your security program and remediation efforts.
5. Mobilization Process
Remediate high-risk vulnerabilities, track progress, and develop ongoing strategic plans for threat management. Mobilization also requires communication and training across your organization to ensure adoption and incremental improvement in CTEM practices.
What Are the Benefits of Adopting CTEM?
Adopting CTEM provides multiple advantages for enterprises aiming to stay ahead of the evolving landscape and improving cyber resiliency.
Maximize Security Resources
By prioritizing vulnerabilities and addressing critical threats early, CTEM allows for more efficient allocation of security resources. According to Gartner, “By 2026, Gartner predicts that organizations prioritizing their security investments based on a CTEM program will realize a two-thirds reduction in breaches.” This shift to proactive security preventing breaches will allow security teams to maximize their resources.
By prioritizing vulnerabilities and addressing critical threats early, CTEM allows for more efficient allocation of security resources.
Stay Ahead of Bad Actors
Cyberthreats evolve at an alarming pace, and CTEM empowers security teams to adapt just as quickly. Continuous exposure assessment and remediation equips security teams to address vulnerabilities before bad actors exploit them, minimizing risks and response times.
Build Long-Term Cyber Resilience
Beyond addressing immediate threats, CTEM emphasizes continuous improvement in both processes and governance. This holistic approach doesn’t just repair security gaps — it helps prevent similar vulnerabilities from emerging again. Over time, this drives long-term risk reduction.
How Does NetSPI Align with a CTEM Program?
NetSPI takes a proactive approach to cybersecurity programs by embedding CTEM principles directly into The NetSPI Platform, enabling you to align your security efforts with the CTEM process: scoping, discovery, prioritization, validation, and mobilization. The Platform includes Attack Surface Management, Penetration Testing as a Service, and Breach and Attack Simulation solutions, which all work together to support your alignment with CTEM and achieve consistent threat exposure management outcomes.
Penetration Testing as a Service (PTaaS)
NetSPI PTaaS delivers a robust pentesting program that includes more than 50 types of pentests that uncover vulnerabilities, exposures, and misconfigurations to help you through the initial processes of CTEM. The NetSPI Platform contextualizes outcomes in real-time, while our experts provide detailed guidance on prioritization and classification of risk. The Platform integrates with many common security tools, so you can accelerate your remediation and quickly close gaps. PTaaS provides additional support through the validation process by retesting to verify remediation effectiveness, and it addresses new threats as they arise. NetSPI PTaaS supports you through all processes of CTEM, so you can proactively reduce risk.
Attack Surface Management (ASM)
NetSPI ASM encompasses External Attack Surface Management (EASM) and Cyber Asset Attack Surface Management (CAASM) to deliver complete visibility into your attack surface, always-on coverage, and deep data context. This can significantly support scoping, discovery, and prioritization processes by identifying and inventorying visible and hidden assets and vulnerabilities, mapping attack paths, and providing deep contextual insights for streamlined remediation. With always-on monitoring and real-time asset and vulnerability updates, you can proactively inventory assets and tackle vulnerabilities as they arise in the evolving threat landscape.

Breach and Attack Simulation (BAS)
NetSPI BAS supports your CTEM program in the discovery, validation, and mobilization processes by testing your security controls to uncover vulnerabilities and misconfigurations against specific threat actors and malware techniques across your environment.
Our security experts will work alongside you to provide deep context of your vulnerabilities and help prioritize risk. The Platform also helps prioritize, validate, and mobilize threats by providing step-by-step instructions to test, retest, and remediate threats, and by illustrating areas of high risk in a MITRE ATT&CK matrix. With BAS, you can optimize security controls, enhance detection, and track progress over time.
Ready to Bolster Your Proactive Security Journey?
The evolving threat landscape requires a proactive and adaptive approach. Aligning your security operations and processes with CTEM ensures you’re not just reacting to threats, but actively staying ahead of them. Let us help you accelerate your proactive security journey with The NetSPI Platform and our security experts by your side.
Learn more about NetSPI’s solutions by reading our Proactive Security solution brief.
Explore More Blog Posts

Extracting Sensitive Information from Azure Load Testing
Learn how Azure Load Testing's JMeter JMX and Locust support enables code execution, metadata queries, reverse shells, and Key Vault secret extraction vulnerabilities.

3 Key Takeaways from Continuous Threat Exposure Management (CTEM) For Dummies, NetSPI Special Edition
Discover continuous threat exposure management (CTEM) to learn how to bring a proactive approach to cybersecurity and prioritize the most important risks to your business.

How Often Should Organizations Conduct Penetration Tests?
Learn how often organizations should conduct penetration tests. Discover industry best practices, key factors influencing testing frequency, and why regular pentesting is essential for business security.

