From Pentest Report to Boardroom Strategy in 5 Steps
How to Turn Technical Findings into Executive Action
To some organisations, penetration testing is just a checkbox on a list of compliance requirements. However, penetration testing is a powerful tool for every cybersecurity professional. In an industry dominated by theoretical risks, penetration testing is the route to real-world data that enables leaders and their teams to make informed decisions. It is a strategic instrument for validating defences, exposing blind spots, and prioritising investment.
The challenge for leaders is translation: taking highly technical observations (Common Vulnerability Scoring System (CVSS) scores, exploit chains, lateral movement paths) and recasting them into real business risks, with a clear plan of action. This article outlines a five‑step approach that leaders can use to maximise the value of pentesting for their organisation.
1) Scope Tests to Business Priorities, Collaboratively
Pentesting should begin with the business model, not just compliance requirements. Scope engagements around critical functions, crown‑jewel systems, sensitive data flows, and realistic threat actors. Regulatory drivers (e.g., PCI-DSS, DORA, NIST2 etc.) can then be overlayed as required. Well‑designed scopes ensure findings already map to business risk; accelerating decision‑making and making the value of the test easier to articulate.
Most importantly, involve stakeholders from applicable areas of the business in this process to understand what matters most to them. In some cases, security will be of direct interest to these stakeholders, facilitating productive conversations about potential attack vectors and how to conduct penetration testing efficiently. When stakeholders do not feel engaged, it is critical to adjust the framing used to communicate with them. For example:
- Software developers may perceive cybersecurity and penetration testing as a direct impediment to their work. However, presenting code security as an aspect of code quality, can often encourage development teams to treat security as a core part of their work.
- Teams that do not rely directly on IT systems to carry out their work may see cybersecurity as irrelevant to their role, or someone else’s responsibility. Helping these teams understand how cybersecurity failures will impact them is vital, as well as communicating how valuable their input is to undertake effective penetration testing and deliver positive outcomes for all teams in the business.
2) Convert Findings into Risk Stories
Once a penetration test report is delivered, the most common error teams make is treating the resulting findings as a checklist for remediation. In the real world, security must be balanced against the other needs of the organisation. While many teams know that fixing every finding in the report is very rarely necessary to reduce the identified risks to an acceptable level, many of these teams also make decisions about which findings to address based on limited context.
Instead, findings should form concise narratives of how an attacker could progress—from initial access, to privilege escalation and data exfiltration—and what that would mean for the business. Each story should identify impacted assets and functions, likely blast radius, ease of exploitation and an overall risk score aligned to the organisation’s tolerance.
Yes, this does require more time and effort than “fix all the High and Medium findings,” or “fix anything above a CVSS score of 6.0” – but investing time and effort in this step of the process will result in substantial savings at a later stage.
3) Extract Vulnerability Patterns
The real value emerges when patterns are analysed. Using the risk stories created in the previous step, answers can be provided to questions such as:
- Are the same issues repeating across systems?
- Are we lacking controls to prevent exploitation of these vulnerabilities?
- If we have controls, how confident are we in their efficacy?
- Did detection and response controls trigger when they should have?
This step usually highlights that many identified security weaknesses share a common root cause. A common example of this is a configuration weakness identified on multiple server systems in a network. Where these systems are managed by independent teams, entirely separate groups may plan and execute remediation work, without sharing any of the lessons learned during the process. Furthermore, the configuration weakness is likely to be reintroduced into the environment when new servers are deployed via the same process that did not correct it, resulting in repeated, inefficient remediation work.
Identifying this pattern makes it possible to take a better approach.
4) Define Actionable Recommendations
Translate these vulnerability patterns into a balanced plan:
- Rapid risk‑reduction actions should be used to address vulnerabilities that present an immediate risk to the organisation, such that delaying remediation to optimise efficiency cannot be considered. This should be based on the potential impact of exploitation that has previously been determined.
- Root-cause corrections should be added to prevent vulnerabilities being reintroduced via the same vector that initially resulted in them. Where possible, these should be implemented concurrently with, or shortly after, rapid risk-reduction actions. It is common for these changes to take longer, due to involvement of other teams and changes to critical business services.
- Structural security investments, such as the introduction of new controls and major process changes, should also be considered. For example, where a control gap has been identified, the evidence gathered in the previous steps should be used to create a clear business case for the investment required to close the gap.
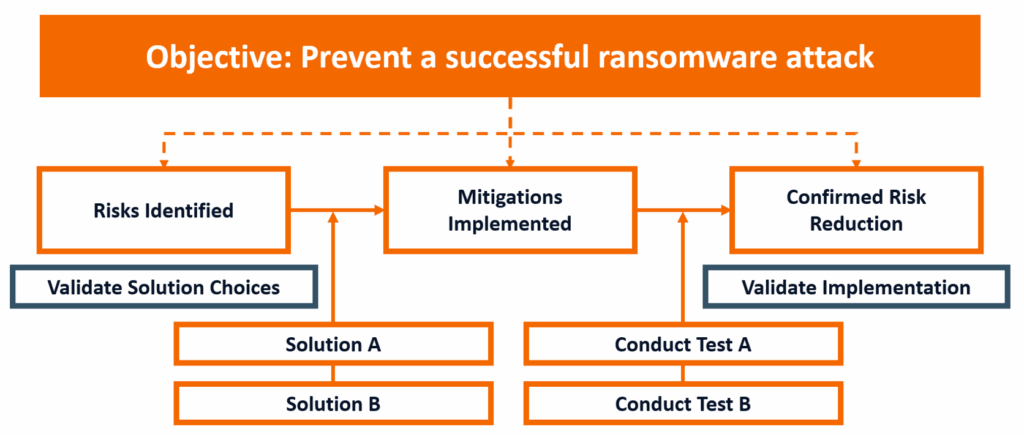
Most actions will require a series of steps to complete. When this is the case, it is important to work backwards from the desired outcome and define key milestones that can be used to verify that work is progressing effectively. A common mistake is to assume that a particular product or solution will address a control gap, with all efforts then focused on procurement, rather than the overarching risk reduction objective. The diagram below highlights the importance of focusing on risks and validating solutions, thus avoiding assumptions that can result in a false sense of security:
5) Report in All Directions, with Confidence
Communicating the value of penetration testing and the results of subsequent work is an important part of this process, but tailoring that communication to different audiences is critical. Exposure scores and coverage metrics are appropriate for technical stakeholders with a strong understanding of cybersecurity, but will mean little to colleagues in other areas of the business.
Data and numerical metrics should be used within technical teams, as well as to provide evidence more broadly where it is required, but the majority of communication should focus on the risk narrative that matters to the audience.
Describing a potential attack path and how the probability and/or impact of that attack has been reduced, in simple terms, provides important context that an audience can digest. However, the single most important message to answer when communicating with all stakeholders is: what does this mean for me? A good exercise to determine if a communication plan is sufficiently concise and clear is to ask “so what?” and “who cares?” until both questions can be answered with confidence.
The most successful cybersecurity teams treat penetration testing as a proactive security tool, a deliberate programme for simulating realistic threats and closing the gaps they reveal. Many of those teams consider working with NetSPI to achieve their penetration testing objectives, to be a core part of their success. Contact NetSPI to schedule your next penetration test and enhance the value of delivering pentest reports to leadership.
Explore More Blog Posts

Ready for Red Teaming? How to Design Realistic, Intelligence-Driven Scenarios
By adopting an adversarial mindset, you can uncover the blind spots that automated scans often miss, shifting from a reactive stance to a proactive, battle-tested defense.

CVE-2026-1731 – BeyondTrust RCE Overview and Takeaways
Learn about CVE-2026-1731, a critical RCE vulnerability in BeyondTrust RS & PRA products. Discover its impact, affected versions, and remediation steps.

Pipe Dreams: Remote Code Execution via Quest Desktop Authority Named Pipe
Discover the risks of the CVE-2025-67813 vulnerability in Quest Desktop Authority. Learn how this RCE flaw impacts your organization and how to mitigate it.


