NetSPI Penetration Testing as a Service (PTaaS)
The NetSPI approach to Penetration Testing as a Service makes our expert penetration testing team available for you when you need it.
When You Pentest With Us, You Get the Value of The NetSPI Platform
NetSPI PTaaS delivers a robust pentesting program that enables you to:
Gain Guidance From Security Experts
Collaborate in real time with our security experts. NetSPI employs more than 300 in-house pentesters that you can trust to deliver consistent, quality manual pentesting results.
Accelerate Time to Remediation
Live, interactive vulnerability reports make the path to remediation clear and easy. Integrate with your ticketing systems and tools to streamline the remediation process.
Reduce Administrative Tasks
Spend more time delivering value to your business and less time managing security testing projects. From scoping to remediation, Penetration Testing as a Service removes administrative hassles and makes sure your penetration tests start and end on time.
Improve Asset and Data Fidelity
Contextualize your pentesting data in a single platform with an easy to use and manage asset inventory and get a high-quality inventory of your assets, with high fidelity, manually validated findings so you can have confidence in the results.
Deliver Detailed Reports
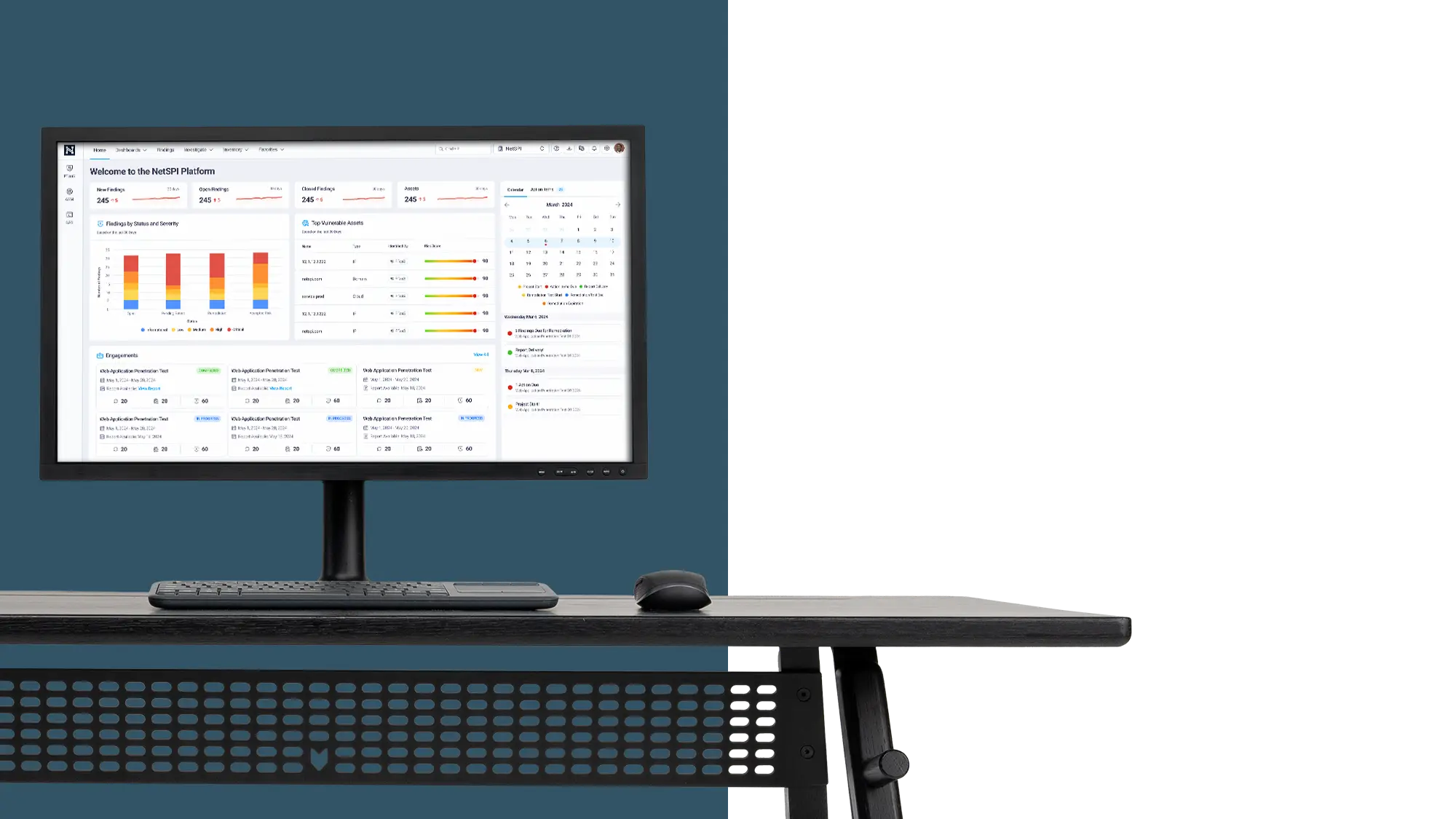
Access fully detailed vulnerability reports as well as executive summaries with high-level results of the engagement. With the NetSPI PtaaS you gain year-round trend analysis and access to dashboards tracking the state of your remediation efforts for all vulnerabilities.

Ebenezer Frimpong
Information Security Analyst at Trella Health

Compare NetSPI PTaaS Features
Pentesting Features
Usage
Traditional Pentesting Companies
Usage
Unlimited
Usage
Unlimited
Vulnerabilities
Infinite
Vulnerabilities
Infinite
Integrations
Open API and more than 1,000 integrations including:
- Jira
- Service Now
- Asana
- Microsoft Teams
- Azure Sentinel
- GitHub
- Hubspot
- Amazon SQS
- and more
Integrations
Open API and more than 1,000 integrations including:
- Jira
- Service Now
- Asana
- Microsoft Teams
- Azure Sentinel
- GitHub
- Hubspot
- Amazon SQS
- and more
Vulnerability Management
Traditional Pentesting Companies
Real-time vulnerability reporting

Real-time vulnerability reporting

Unlimited vulnerability hosting

Unlimited vulnerability hosting

Vulnerability deduplication

Vulnerability deduplication

Risk scoring

Risk scoring

Custom severities

Custom severities

Attack paths

Attack paths

Global tagging

Global tagging

User assignments

User assignments

Custom remediation SLAs

Custom remediation SLAs

Program Management
Traditional Pentesting Companies
Dedicated project manager


Dedicated project manager


Client relationship management


Client relationship management


Program management dashboard

Program management dashboard

Security Testing
Traditional Pentesting Companies
Manual verification of findings


Manual verification of findings


Asset discovery


Asset discovery


Direct access to in-house security experts

Direct access to in-house security experts

Obtain findings and results in real-time

Obtain findings and results in real-time

Delivery & Remediation
Traditional Pentesting Companies
PDF / CSV report


PDF / CSV report


Annual NetSPI Platform access

Annual NetSPI Platform access

Integrate Seamlessly
NetSPI PTaaS includes 1000+ integrations and an open API to integrate with your existing workflows and save countless hours of manual effort.
- Jira
- Service Now
- Asana
- Microsoft Teams
- and more

Work With the A Team Every Time
With 300+ in-house security experts, NetSPI operates as a true extension of your team. Our proven methodology and consistent processes ensure you get the A Team, every time. Get the opportunity to work directly with the foremost experts across domains, spanning from mainframes to AI.
You Deserve The NetSPI Advantage

Security Experts
- 300+ pentesters
- Employed, not outsourced
- Domain expertise

Intelligent Processes
- Programmatic approach
- Strategic guidance
- Delivery management team

Advanced Technology
- Consistent quality
- Deep visibility
- Transparent results




