
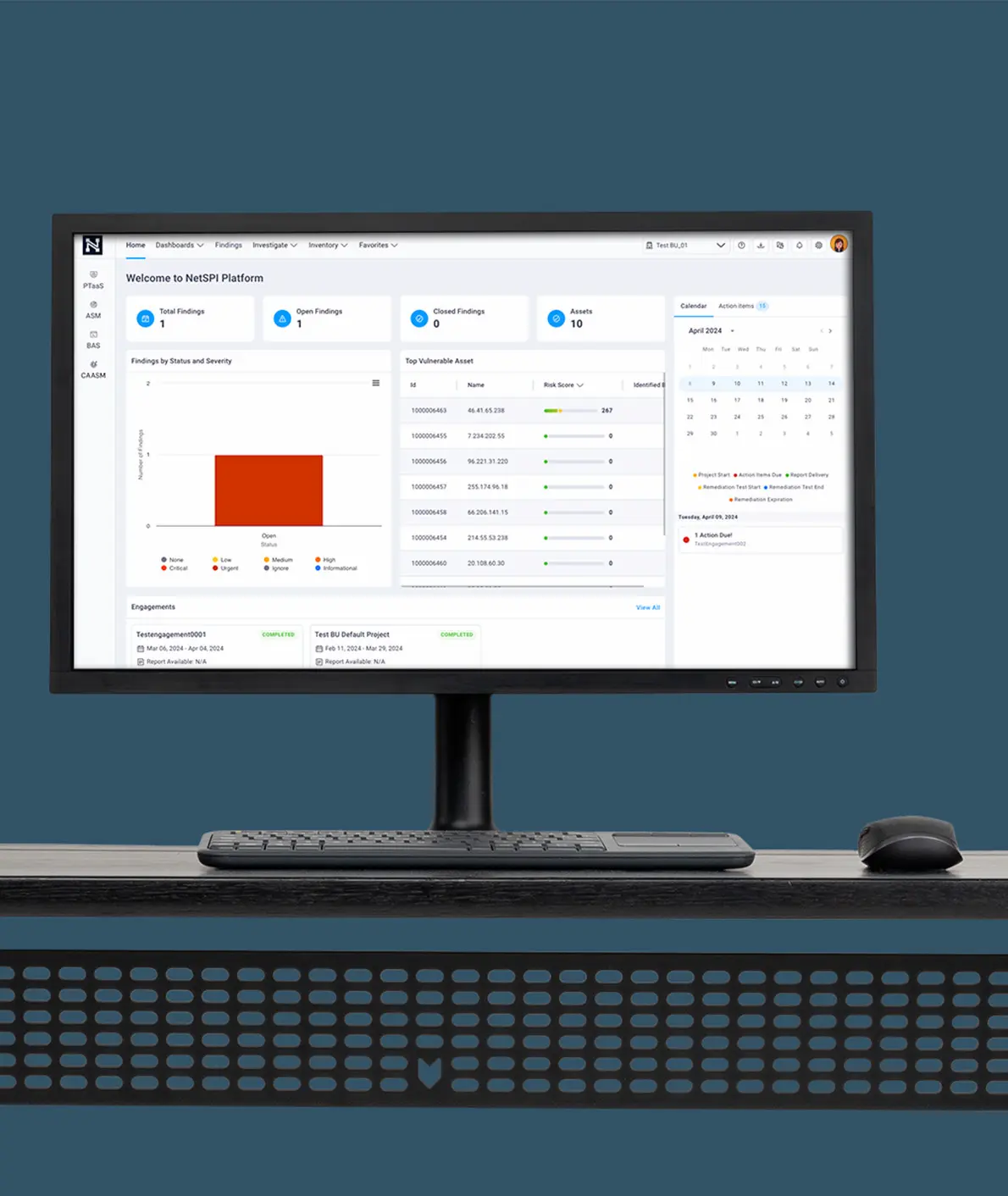
Azure Penetration Testing
NetSPI’s Azure penetration testing identifies cloud configuration and other security issues on your Azure infrastructure and provides actionable recommendations to improve your Azure cloud security posture.
Azure Penetration Testing Benefits
Whether you are migrating to Azure, developing cloud-native applications in Azure, using Azure Kubernetes Service (AKS), or pentesting Azure annually for compliance, partnering with NetSPI to penetration test your Microsoft Azure infrastructure helps ensure a secure cloud instance. Security issues can lead to the compromise of your Azure infrastructure and enable an attacker to expose sensitive data, take over Azure resources, or pivot to attack your internal network.
Azure Pentesting Methodology
During Azure penetration testing, NetSPI identifies high-impact vulnerabilities in your Azure services, including applications exposed to the internet. Identify exposed credentials, excess privileges, and security misconfigurations in your Azure Active Directory integration. Deliverables include an Azure penetration testing report with prioritized vulnerabilities and actionable guidance to help you reduce risk and secure your Azure attack surface.
Azure Penetration Testing Solutions
Our Azure security experts follow manual and automated penetration testing processes that use commercial, open source, and proprietary Azure penetration testing tools to evaluate your Azure cloud infrastructure from the perspective of anonymous and authenticated users.

Configuration Review
Our expert Azure penetration testers evaluate the configurations of your Azure services, and the Identity and Access Management (IAM) policies applied to those services. Misconfigurations can lead to significant security gaps in Azure environments.

External Azure Pentesting
External Azure vulnerability scanning tools and manual security testing probes your Azure infrastructure to uncover security issues in public-facing services. These issues include web and network-related security.

Internal Network Pentesting
Internal network layer penetration testing of virtual machines and services enables NetSPI to emulate an attacker that has gained a foothold on your Azure virtual network.
What Does NetSPI Test For?
Our Azure penetration testing includes a cloud services configuration review and external and internal penetration testing techniques, such as:
- System and services discovery
- Automated vulnerability scanning
- Manual verification of vulnerabilities
- Manual web application pentesting
- Manual network protocol attacks
- Manual dictionary attacks
- Network pivoting
- Domain privilege escalation
- Access sensitive data and critical systems
Featured Resources

Adventures in Azure Privilege Escalation Webinar
Explore Azure escalation paths in our webinar. Learn about common access vectors and privileged access maintenance techniques with Karl Fosaaen.
Azure Cloud Penetration Testing Stories
Explore critical discoveries and unique approaches from NetSPI’s top cloud penetration testers in our ebook. Learn how to improve Microsoft Azure Cloud security.

A Beginners Guide to Gathering Azure Passwords
Get started with Azure password gathering using Get-AzPasswords with this easy-to-follow guide for beginners. Find out about Contributor IAM rights and more.
You Deserve The NetSPI Advantage

Security Experts
- 300+ pentesters
- Employed, not outsourced
- Domain expertise

Intelligent Processes
- Programmatic approach
- Strategic guidance
- Delivery management team

Advanced Technology
- Consistent quality
- Deep visibility
- Transparent results

