Action Message Format (AMF) is one of the communication protocols used to exchange messages between Flash client and server; the others are RTMP and XML. BurpAMFDSer is another Burp plugin that will deserialize/serialize AMF request and response to and from XML with the use of Xtream library (https://xstream.codehaus.org/). BurpAMFDSer also utilizes part of Kenneth Hill’s Jmeter source code for custom AMF deserialization (https://github.com/steeltomato/jmeter-amf).
How to run:
java -classpath burp.jar;burpAMFDser.jar;xstream-1.4.2.jar burp.StartBurp
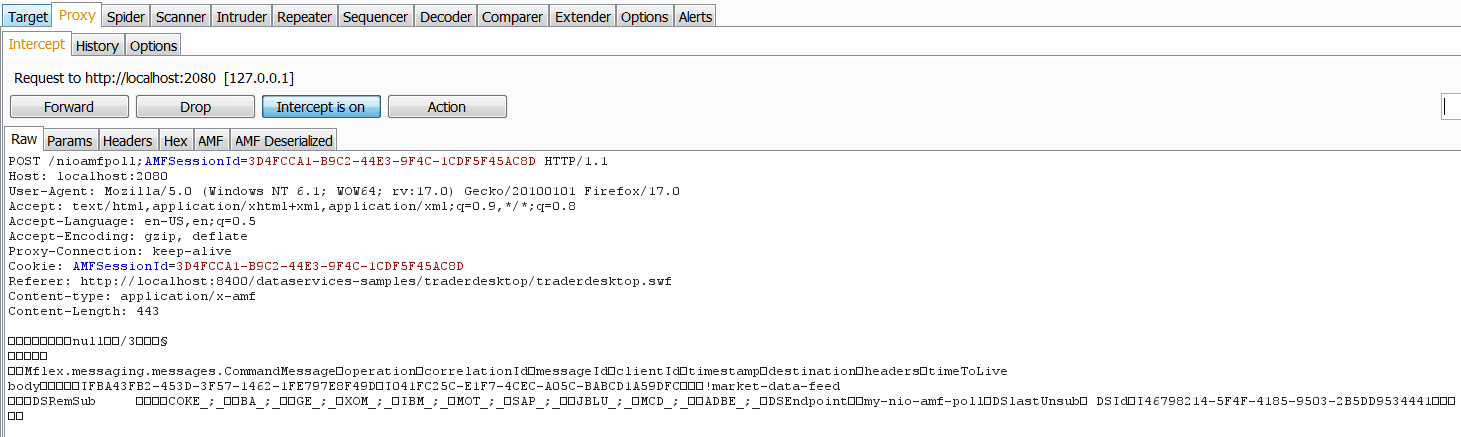
Sample serialized Request:
Sample deserialized Request:
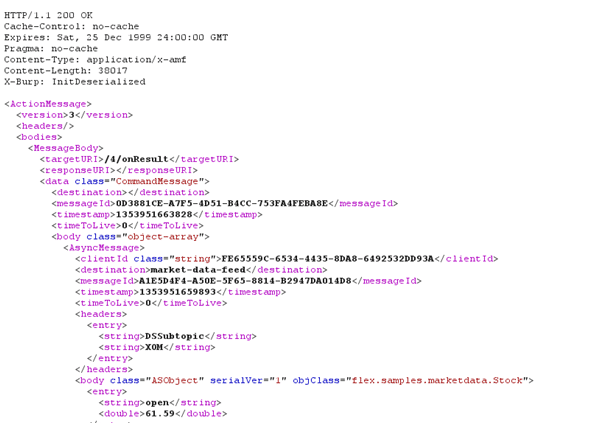
Sample deserialized Response:
Source code and executables are available at:
https://github.com/NetSPI/burp-plugins/tree/master/BurpAMFDSer/Old_APIs
The sample application in the screenshot is TraderDesktop, provided as part of ADEP Data Services for Java EE 4.6 and could be downloaded at: https://www.adobe.com/cfusion/tdrc/index.cfm?product=livecycle_dataservices
I’ve also developed a newer version of this plugin to be compatible with the new Burp Extender APIs (https://blog.portswigger.net/2012/12/draft-new-extensibility-api.html). Now you can modify AMF requests and responses in a separate tab.
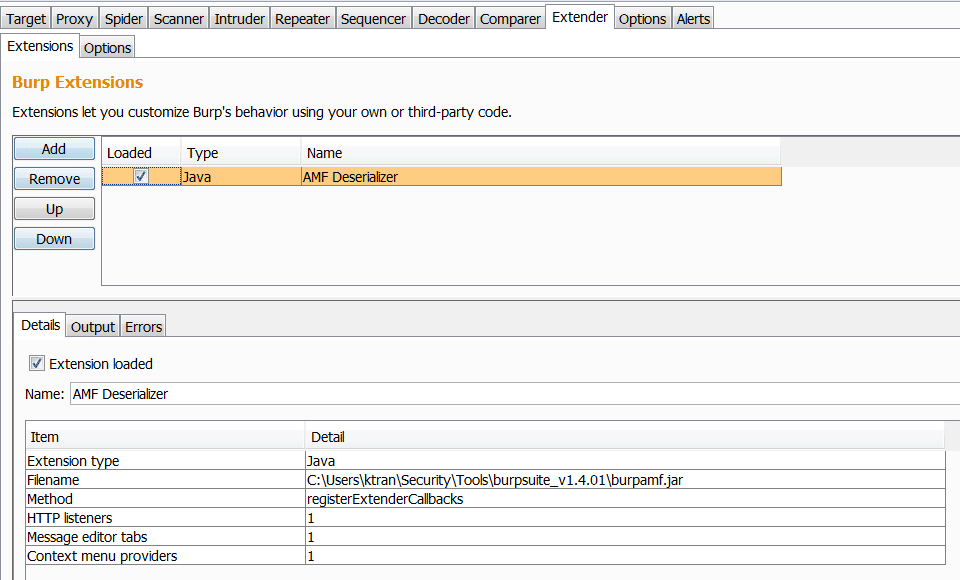
The new plugin can be loaded dynamically via Burp Extender:
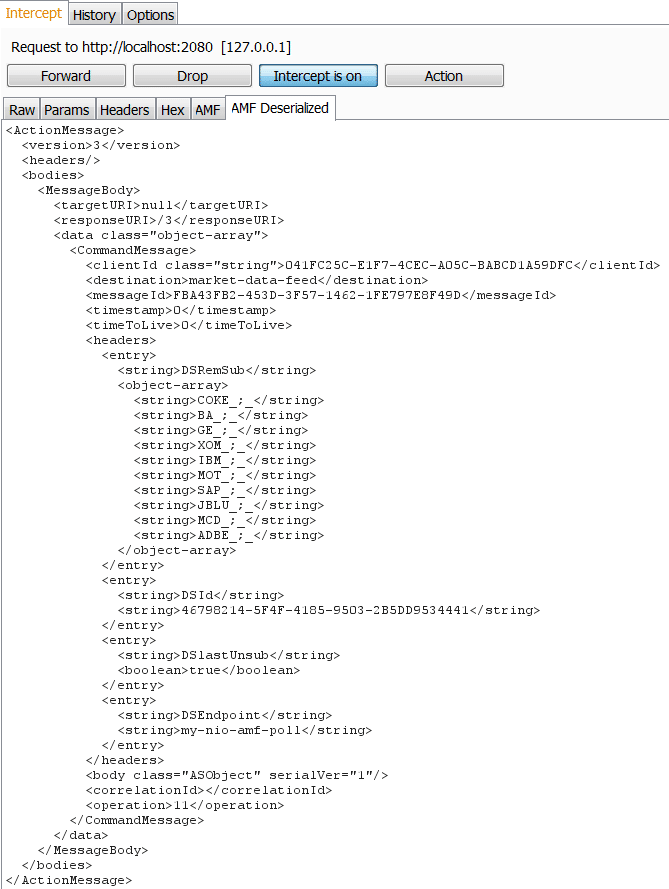
Sample Request:
I also added 2 new menus to work with Intruder and Scanner (pro version only)
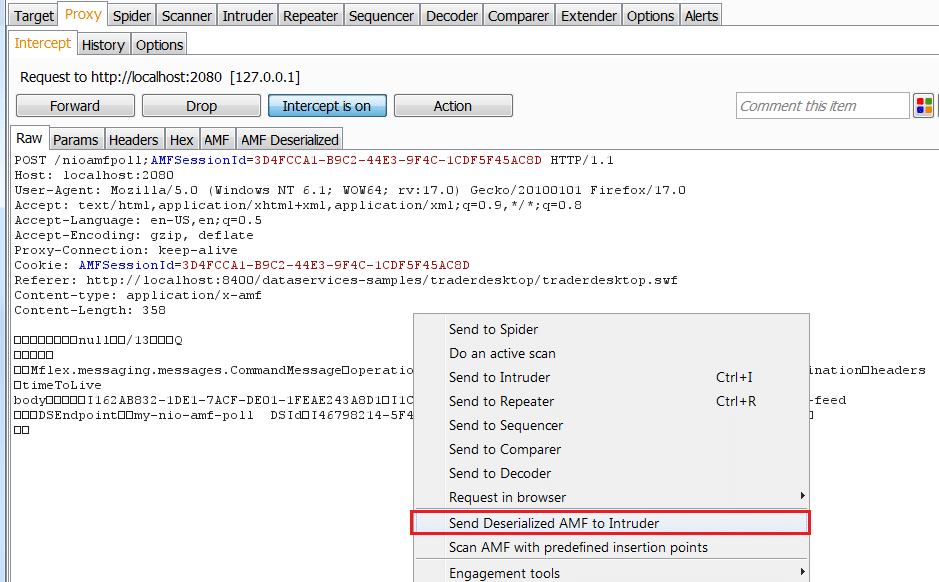
Send deserialized request to Intruder
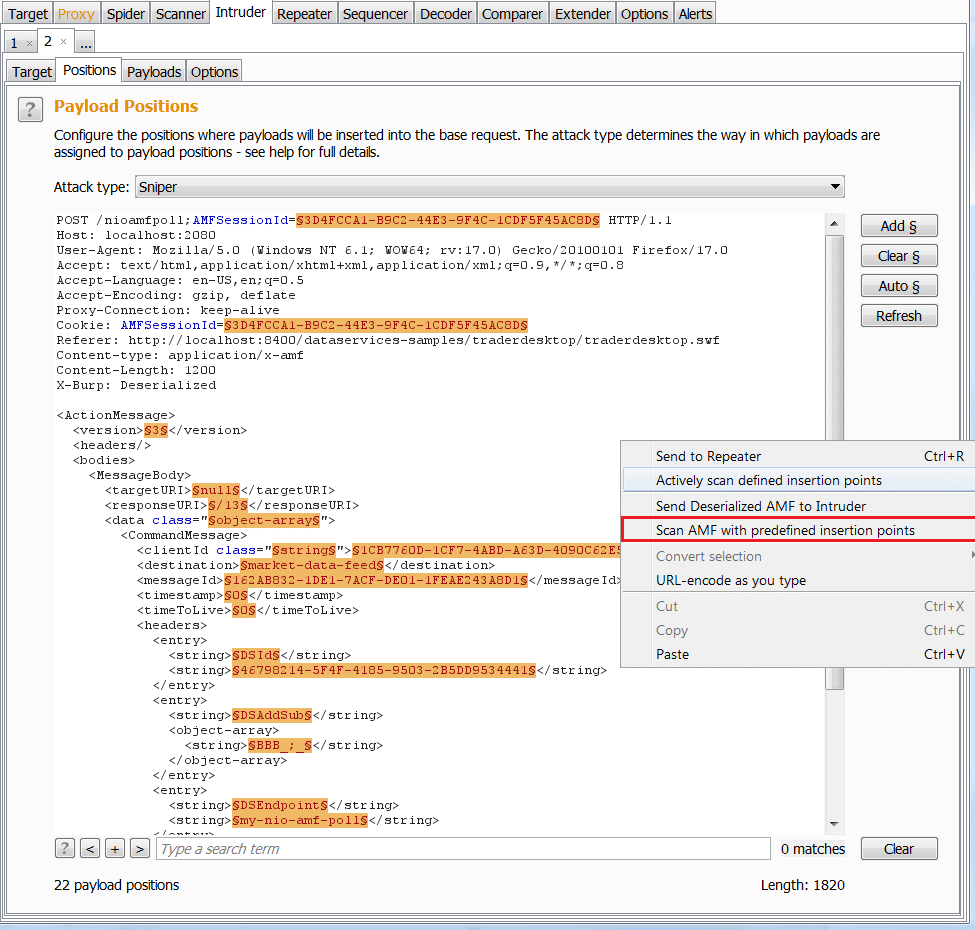
Scan AMF (Pro version only)
Unfortunately, the new APIs are only available for Burp Suite Pro version 1.5.01 and later. Hopefully the author will update the free version soon.
If you are interested, source code and executable are available at: https://github.com/NetSPI/burp-plugins/tree/master/BurpAMFDSer/New_APIs
Explore More Blog Posts

Pipe Dreams: Remote Code Execution via Quest Desktop Authority Named Pipe
Discover the risks of the CVE-2025-67813 vulnerability in Quest Desktop Authority. Learn how this RCE flaw impacts your organization and how to mitigate it.

Ivanti Endpoint Manager Mobile (EPMM) [CVE-2026-1281 & CVE-2026-1340]: Overview & Takeaways
Ivanti has disclosed two critical zero‑day vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM), tracked as CVE‑2026‑1281 and CVE‑2026‑1340. Both vulnerabilities have been exploited in active attacks and allow unauthenticated remote threat actors to compromise EPMM appliances.

Why Your Security Program Needs Domain Monitoring
NetSPI Domain Monitoring continuously discovers and assesses look-alike domains related to your organization, providing deep contextual intelligence including risk profiles, WHOIS records, IP details, DNS records, and certificate data. The NetSPI Platform streamlines response, enabling rapid action against high-risk domains.