
Directory Traversal, File Inclusion, and The Proc File System
Directory traversal and local file inclusion bugs are frequently seen in web applications. Directory traversal is when a server allows an attacker to read a file or directories outside of the normal web server directory. Local file inclusion allows an attacker the ability to include an arbitrary local file (from the web server) in the web server’s response. Both of these bugs can be used to read arbitrary files from the server.
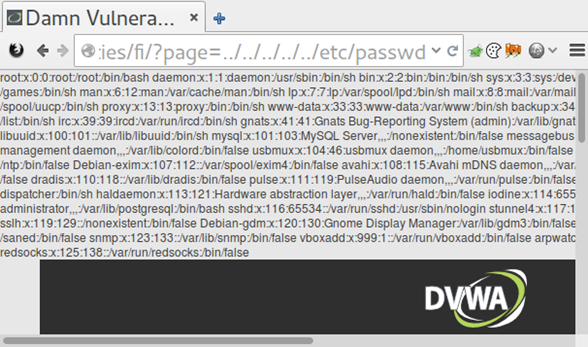
In most cases, this means that an attacker can read the /etc/passwd file and the shell history files in order to find information leaks. However, an attacker can also use this to read the proc file system. This can provide some interesting insights into what’s running on the server.
A few of the more interesting proc entries include:
| Directory | Description |
|---|---|
| /proc/sched_debug | This is usually enabled on newer systems, such as RHEL 6. It provides information as to what process is running on which cpu. This can be handy to get a list of processes and their PID number. |
| /proc/mounts | Provides a list of mounted file systems. Can be used to determine where other interesting files might be located |
| /proc/net/arp | Shows the ARP table. This is one way to find out IP addresses for other internal servers. |
| /proc/net/route | Shows the routing table information. |
| /proc/net/tcp and /proc/net/udp | Provides a list of active connections. Can be used to determine what ports are listening on the server |
| /proc/net/fib_trie | This is used for route caching. This can also be used to determine local IPs, as well as gain a better understanding of the target’s networking structure |
| /proc/version | Shows the kernel version. This can be used to help determine the OS running and the last time it’s been fully updated. |
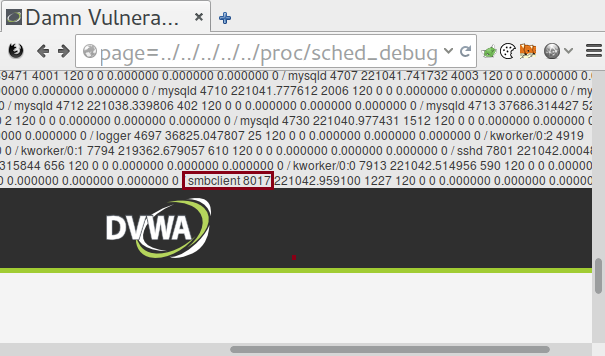
Each process also has its own set of attributes. If you have the PID number and access to that process, then you can obtain some useful information about it, such as its environmental variables and any command line options that were run. Sometimes these include passwords. Linux also has a special proc directory called self which can be used to query information about the current process without having to know it’s PID. In the following examples you can replace [PID] with either self or the PID of the process you wish to examine.
| Directory | Description |
|---|---|
| /proc/[PID]/cmdline | Lists everything that was used to invoke the process. This sometimes contains useful paths to configuration files as well as usernames and passwords. |
| /proc/[PID]/environ | Lists all the environment variables that were set when the process was invoked. This also sometimes contains useful paths to configuration files as well as usernames and passwords. |
| /proc/[PID]/cwd | Points to the current working directory of the process. This may be useful if you don’t know the absolute path to a configuration file. |
| /proc/[PID]/fd/[#] | Provides access to the file descriptors being used. In some cases this can be used to read files that are opened by a process. |
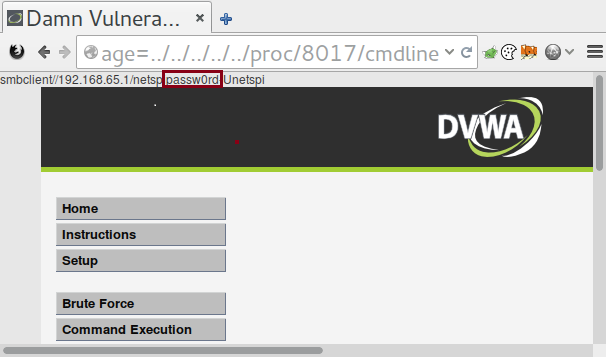
Combining directory traversal and file inclusion vulnerabilities with the proc file system ends up being a great way to gain access to information relating to the running processes on a Linux system. For instance, it’s possible to locate database servers by looking at the current connections the machine has. It also makes it easier to fingerprint what software is running on the machines in order to help determine if they are vulnerable to version-specific issues. It’s important not to overlook the proc file system when one of these vulnerabilities are found during a penetration test.
Explore More Blog Posts

Extracting Sensitive Information from Azure Load Testing
Learn how Azure Load Testing's JMeter JMX and Locust support enables code execution, metadata queries, reverse shells, and Key Vault secret extraction vulnerabilities.

3 Key Takeaways from Continuous Threat Exposure Management (CTEM) For Dummies, NetSPI Special Edition
Discover continuous threat exposure management (CTEM) to learn how to bring a proactive approach to cybersecurity and prioritize the most important risks to your business.

How Often Should Organizations Conduct Penetration Tests?
Learn how often organizations should conduct penetration tests. Discover industry best practices, key factors influencing testing frequency, and why regular pentesting is essential for business security.