Sent email to Forescout to query the published CVE and fix
CVE-2025-4660: Forescout SecureConnector RCE

TL;DR
- Vulnerability ID: CVE-2025-4660
- Product Affected: Forescout SecureConnector (Windows only)
- Severity: High (CVSS 4.0 Score: 8.7)
- Versions: 11.1.02.1019 through 11.3.6
- Impact: Remote Code Execution (RCE)
- Attack Vector: Remote, low-privilege attacker can redirect the SecureConnector agent to a malicious server
- Fun Fact: The agent can then be used as a Command and Control (C2) channel. Yes, the security agent becomes the attacker’s minion
- Fix: Upgrade to version 11.3.7 or later
The Breakdown
Forescout SecureConnector is a security agent designed to enforce endpoint compliance and security posture. Ironically, in versions 11.1.02.1019 through 11.3.6 on Windows, it can be turned into a remote attacker’s best friend. IT personnel can use SecureConnector to access Windows, Linux and MacOS endpoints and make them manageable for deep inspection and remote tasking from the Forescout Platform.
What Went Wrong?
At the heart of CVE-2025-4660 is a named pipe, specifically _FS_SC_UNINSTALL_PIPE, used for inter-process communication. This pipe was configured to allow remote access by the Everyone group, meaning any user on the network could connect to it.

This allowed a low-privileged attacker to:
- Connect to the named pipe remotely.
- Send a redirect command to the SecureConnector agent.
- Point the agent to a rogue CounterACT server.
- Disable certificate pinning by using a thumbprint of all 00s.
- Issue commands to the agent as if they were the legitimate Forescout backend.
A Vulnerability Lost in the Shuffle
This issue was originally discovered and disclosed before I joined NetSPI during a CBEST Red Team engagement in 2023. However, due to the role change I had little visibility of the original reported issue. The fix appears to have been quietly released without a corresponding CVE or clear public disclosure. The patch notes were vague and assigned to a Feature/Enhancement category not a vulnerability which meant the issue flew under the radar.
Later, while working on a NetSPI client engagement, we encountered the same vulnerability again, still exploitable, still unpatched in the wild. That’s when it became clear: this wasn’t just a one-off oversight. The vulnerability was not widely known, and many environments were still at risk.
Technical Deep Dive
The SecureConnector agent communicates with a configured CounterACT server, either hardcoded or defined in a SecureConnector.ini file. The agent uses a binary command ID format over the named pipe, followed by structured data.
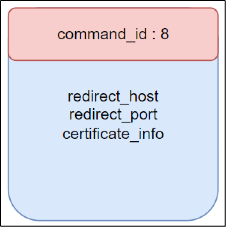
One such command allows redirection to a new server, including host, port, and certificate thumbprint. By sending a crafted redirect command, an attacker can:
- Redirect the agent to a malicious server.
- Use a thumbprint of all 00s to bypass certificate pinning.
- Establish a persistent connection with the rogue server.
Forescout SecureConnector C2
Once the redirection message has been submitted to the remote agent over the named pipe, it will connect to the rogue server and wait for instruction. The agent uses a length-prefixed, text-based XML protocol to communicate. The rogue server can issue commands such as:
- Process listing
- Directory listing
- File download
- Arbitrary command execution (as SYSTEM)
0088:<FSAGENT_REQ><COMMANDS><COMMAND id="1"><PROCESSES/></COMMAND></COMMANDS></FSAGENT_REQ>
A more complete POC can be found on our GitHub repository here.
Who’s Affected?
Only Windows-based deployments of SecureConnector are vulnerable. Linux and macOS agents are not impacted.
Mitigation
Forescout has released a patch in version 11.3.7. If you’re running anything earlier, especially in the affected range, upgrade immediately.
Final Thoughts
This vulnerability is a textbook example of how default permissions and trust assumptions can backfire. It also highlights the importance of hardening security agents themselves, as they often run with elevated privileges and deep network access.
And yes, while it’s a serious issue, there’s something darkly amusing about a security agent being flipped into a C2 node. Just don’t let it happen on your watch.
Disclosure Timeline
Circa 2023 – Initial disclosure
Was asked to submit a brand new report
Refusal from NetSPI to resubmit the same finding
Update from Forescout to indicate they had a KB article for it behind a customer support portal
Request latest agent to confirm the fix
Response from Forescout indicating that I would need to through customer portal
Requesting latest agent failed via the new partner portal as we were not a partner
Response from Forescout, CVE-2025-4660
Blog post published on NetSPI website
Interested in learning more about NetSPI’s Red Team Operations?
NetSPI’s Red Team Operations enhance your team’s safeguards against threats
Explore More Blog Posts

Pipe Dreams: Remote Code Execution via Quest Desktop Authority Named Pipe
Discover the risks of the CVE-2025-67813 vulnerability in Quest Desktop Authority. Learn how this RCE flaw impacts your organization and how to mitigate it.

Ivanti Endpoint Manager Mobile (EPMM) [CVE-2026-1281 & CVE-2026-1340]: Overview & Takeaways
Ivanti has disclosed two critical zero‑day vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM), tracked as CVE‑2026‑1281 and CVE‑2026‑1340. Both vulnerabilities have been exploited in active attacks and allow unauthenticated remote threat actors to compromise EPMM appliances.

Why Your Security Program Needs Domain Monitoring
NetSPI Domain Monitoring continuously discovers and assesses look-alike domains related to your organization, providing deep contextual intelligence including risk profiles, WHOIS records, IP details, DNS records, and certificate data. The NetSPI Platform streamlines response, enabling rapid action against high-risk domains.
