
UPEK + Lenovo = Insecure Password Storage
Recently Adam Caudill and ElcomSoft identified vulnerabilities in the way that UPEK fingerprint readers store Windows passwords in the registry. Adam has released a great proof-of-concept tool to decrypt these poorly encrypted passwords. I have access to a Lenovo T420 ThinkPad that features a UPEK fingerprint reader. The ThinkVantage Fingerprint Software is also vulnerable to this UPEK issue. The issue with the ThinkPad software affects credentials that are entered by the user in the ThinkVantage Fingerprint Software. Since I do not use the fingerprint reader for Active Directory authentication, I do not regularly update my password in the software. So when I initially ran the decryption tool, the tool came back with my password from several months ago. For users who regularily use the fingerprint reader for AD authentication, this could be a major issue. If you have this software on your machine and want to keep it on your machine, I would recommend the following:
- Set a disposable password for your Windows account
- Open up the “ThinkVantage Fingerprint Software” (Accessible from the ThinkVantage Client Security Solution menu)
- Enter your disposable password in the software and click “Submit”:
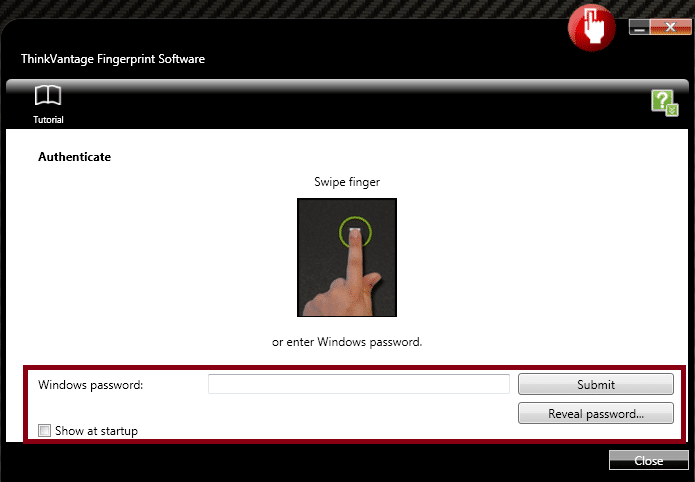
- Close out the software and only authenticate to the application with your fingerprint.
- Once your password has been updated, it may be worth compiling Adam Caudill’s tool to double check that the password has been changed: https://github.com/brandonlw/upek-ps-pass-decrypt
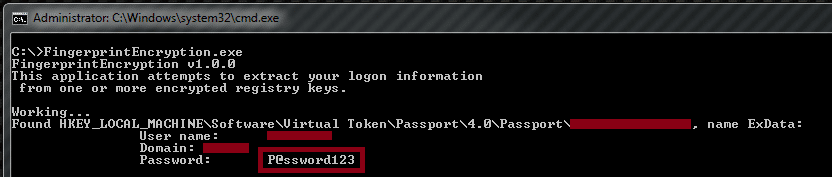
- Additionally, you can use the reveal password button to show the current password stored by the application.
- Finally, full disk encryption is a good idea, regardless of your use of a fingerprint reader. If someone steals your computer, full disk encryption will prevent them from recovering data (including registry keys) from the hard drive.
Explore More Blog Posts

Part 2: Ready for Red Teaming? Crafting Realistic Scenarios Reflecting Real-World Threats
Learn to craft realistic red team scenarios that reflect real-world threats. Gain actionable insights to strengthen detection and response capabilities.

Detecting Authorization Flaws in Java Spring via Source Code Review (SCR)
Discover how secure code review catches privilege escalation vulnerabilities in Java Spring apps that pentests miss - identify insecure patterns early.
Set Sail: Remote Code Execution in SailPoint IQService via Default Encryption Key
NetSPI discovered a remote code execution vulnerability in SailPoint IQService using default encryption keys. Exploit details, discovery methods, and remediation guidance included.