
5 Criteria for Evaluating External Attack Surface Management Vendors
As your company’s external attack surface expands and threat actors remain relentless, Attack Surface Management (ASM) solutions can help level up your proactive security measures by enabling continuous pentesting. Thoroughly vetting and comparing different ASM providers is essential to selecting one that best aligns with your business needs and overarching security goals.
What to Look for When Evaluating External Attack Surface Management Providers
To simplify the process of evaluating attack surface management vendors, we’ve identified five important criteria to look for when comparing different companies.

1. Proven Reputation and Third-Party Validation
Vendors new to the attack surface management space may not have enough experience tailoring their platform for greater business needs. Selecting a tenured vendor with a history in ASM can offer benefits such as streamlined processes, quick access to support teams, and proven methods to improve security.
Look for attack surface management providers that have received recognition from trusted third parties such as Gartner® or Forrester. Expert analysts at these and other research and advisory firms perform a factual review of information from technology providers to recognize solutions that demonstrate innovation.
As part of this research, Forrester included NetSPI in its External Attack Surface Management Landscape Report featuring top EASM vendors, and Gartner featured NetSPI in its EASM Competitive Landscape Report.
Gartner shared the following about NetSPI in the report:
NetSPI differentiates by combining its ASM capability with its human pentesting expertise. This is achieved via the attack surface operations team, who manually test and validate the exposures found. As a result, it reduces alert fatigue and false positives, while providing customers only the critical and high exposures relative to their organization, as well as the support on how to remediate said exposures.
2. Critical Functionality
Depending on your business needs and use cases for choosing an ASM platform, some functionalities may be more important than others.
In The External Attack Surface Management Landscape, Q1 2023, Forrester listed several core functionalities to look for in attack surface management platforms, including:
- External/internet-facing asset discovery
- Asset identification
- Asset and business relationship mapping
- Active and passive vulnerability scanning
- Open ports and services monitoring
- URL and IP range tracking
- Certificate monitoring
- Exposure/risk prioritization
- Custom dashboarding and reporting
3. Screenshots and Software Demos of the Platform
Trusted attack surface management providers have screenshots of the platform readily available so prospective customers can see what the platform and key functionalities look like firsthand.
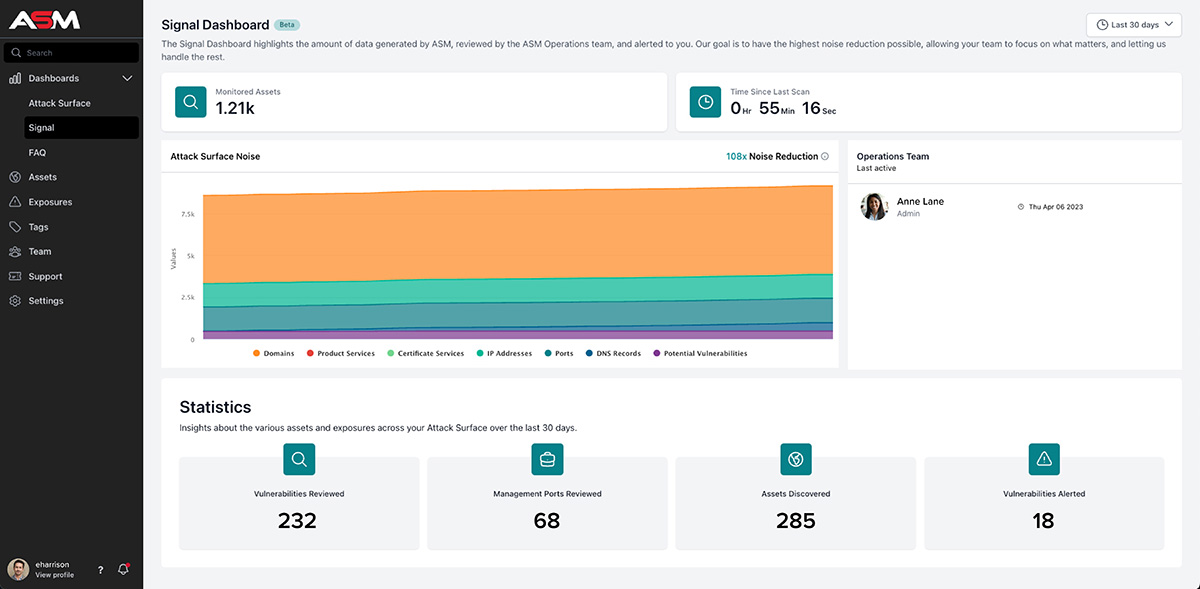
In addition to screenshots, having the option to take an ASM platform for a test drive through a guided demo or webinar is an important step before selecting an ASM vendor. This option can enable your team to experience the platform, ask specific questions about capabilities, and better understand feature differentiators between tools.
4. Human Analysis and Guidance
In addition to advanced functionality, human analysis and expertise is essential to take into consideration when evaluating attack surface management companies. With human analysis, the vendor’s ASM operations team manually reviews and validates findings to reduce false positive alerts and minimize disruptions to business operations as a result. The team also helps by answering any questions that come up related to findings and providing guidance for remediation.
One challenge businesses often face is that security or IT teams need to hire a dedicated employee to manage an ASM solution on top of investing in the solution itself, which drives up costs including hiring, training, and salary. In fact, our 2023 Offensive Security Vision Report found that one of the greatest barriers to improved offensive security is a lack of resources.
With a user-friendly ASM platform powered by human expertise, an entire team is available to triage alerts, so you don’t need to add additional responsibilities or headcount to your team.
5. Simple Onboarding
Some attack surface management companies require time-intensive setup and onboarding, which can take several hours of your team’s time and can push back the timeline of full platform implementation by weeks.
As you consider different ASM platforms, look for one with a streamlined or automated onboarding process, on-demand training materials, a user-friendly design, easy to digest dashboards, and human support as-needed during the onboarding process. Seamless onboarding can help ensure you start off on the right foot with an ASM vendor and accelerate time to value.
Types of Attack Surface Management Vendors
A few different types of ASM vendors are available:
Human-Based
With this type of ASM vendor, expert human pentesters conduct penetration testing and vulnerability assessments to test the external network, typically on a quarterly basis.
Pure Technology-Driven
Technology-driven ASM solutions involve tools or scanners that review the full attack surface (aka the assets a business has on the Internet) and use scores to prioritize and remediate impactful findings.
Hybrid
A hybrid approach involves combining both human intuition and analysis with advanced, automated technology to more effectively identify vulnerabilities and filter prioritized alerts.
Partnering with a hybrid ASM vendor is the most impactful option because it enables verified prioritization of results to ensure only the most relevant alerts are delivered, resulting in the best ROI on your cybersecurity investment.
Questions to Ask Attack Surface Management Vendors
To effectively evaluate an ASM solution and select the right partner that aligns with your business requirements, develop a standardized list of questions to ask each vendor before making a decision.
Questions to consider asking include:
- Do you offer a human-based, technology-driven, or hybrid approach to attack surface management?
- How often are tests conducted?
- Do you offer continuous pentesting? If so, how do you approach it?
- How broad and up-to-date is the data?
- How soon do new assets appear and get recognized by the ASM tool?
- Do you support exposure remediation once vulnerabilities are discovered? How?
- Do I have access to all of my scan data if needed?
- What does the onboarding process look like? How much time is required of my team?
- What’s your process for managing and prioritizing alerts?
- How will you help me understand the most critical assets or vulnerabilities on my attack surface?
- What are the critical risk factors most likely to impact the business?
- Who are the potential attackers threatening my business?
- Which vulnerabilities are the most important to prioritize with remediation?
- Which exposures are threat actors most likely to exploit?
Partner with NetSPI for the Most Comprehensive ASM Capabilities
The right attack surface management provider can help your organization more effectively manage your attack surfaces and quickly identify and remediate vulnerabilities.
If you’re looking for an ASM platform that includes all the criteria listed above – and more – NetSPI has you covered. We created our attack surface management platform based on three essential pillars of ASM—human expertise, always-on, continuous pentesting, and risk prioritization.
Some of the benefits of selecting NetSPI as your attack surface management provider include:
- Simple setup and onboarding
- Comprehensive asset discovery
- Manual triaging of exposures
- Prioritized alerts
Learn more about how we can improve your offensive security together by watching a demo of our ASM platform. Also take our free attack surface management tool for a test drive and search more than 800 million public records for potential attack surface exposures.
Explore more blog posts

The Strategic Value of Platformization for Proactive Security
Read about NetSPI’s latest Platform milestone, enabling continuous threat exposure management (CTEM) with consolidated proactive security solutions.
Backdooring Azure Automation Account Packages and Runtime Environments
Azure Automation Accounts can allow an attacker to persist in the associated packages that support runbooks. Learn how attackers can maintain access to an Automation Account.
The Rapid Evolution of AI Voice Cloning and its Implications for Cybersecurity
Learn about the rise of AI voice cloning, its cybersecurity challenges, and necessary measures for IT and InfoSec leaders to stay protected.

