Cracking Stats for Q2 2014

During many of our penetration tests, we gather domain password hashes (with permission of the client) for offline cracking and analysis. This blog is a quick summary of the hashes that we attempted to crack in the second quarter of 2014 (and so far for this year). The plan is to continue doing this each quarter for the rest of the year to see how we did overall for the year. Please keep in mind that this is not an all encompassing sample. We do not collect domain hashes during every single penetration test, as some clients do not want us to.
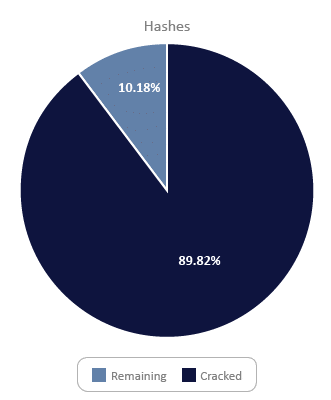
The sample for this quarter included three sets of domain hashes that added up to 23,898 hashes. All three sets had some LM hashes stored along with the NTLM hashes, but none of the LM stored passwords were that complicated, so it wasn’t a huge advantage. Of the hashes, 8,277 were duplicates, leaving 15,621 unique hashes. Of the 23,898 hashes, we were able to crack 21,465 (89.82%).
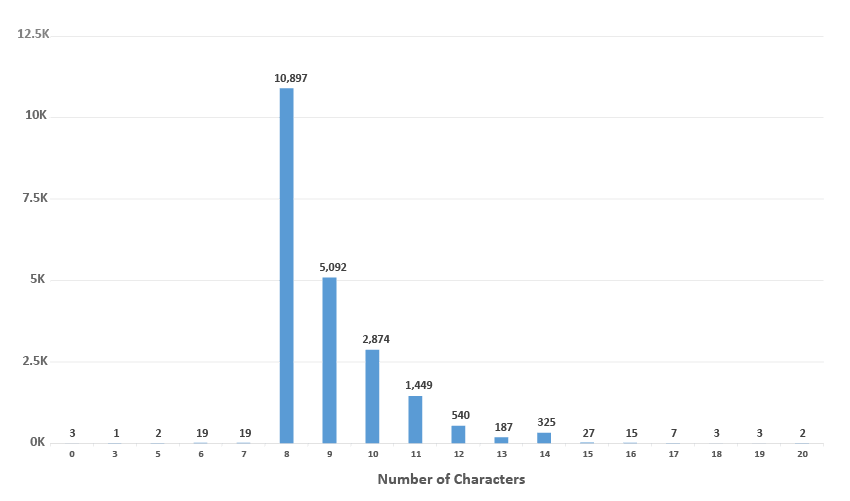
Cracked Password Length Breakdown:
As you can see, the cracked passwords peak at the eight character length. This is pretty common for a minimum password length, so it’s not a big surprise that this is the most common length cracked.
Some interesting finds:
- Most Common Password (820 instances): Changem3
- Longest Password: 20 characters
- Most Common Length (10,897 instances): 8 characters
- Instances of “password” (case-insensitive): 1,541
- Instances of “spring2014” (case-insensitive): 111
- Instances of “spring14” (case-insensitive): 93
- Instances of “summer2014” (case-insensitive): 84
- Instances of “summer14” (case-insensitive): 59
So far this year, we’ve collected 33,950 hashes to crack. Of those, we’ve been able to crack 29,077 (85.65%).
Some more interesting finds:
- Most Common Password (1274 instances): Password1
- Longest Passwords: 20 characters – Two passwords based off of the name of the business group using them
- Most Common Length (14,339 instances): 8 characters
- Instances of “password” (case-insensitive): 2,675
- Instances of “winter2014” (case-insensitive): 23
- Instances of “winter14” (case-insensitive): 18
- Instances of “spring2014” (case-insensitive): 102
- Instances of “spring14” (case-insensitive): 91
I put together an hcmask file (to use with oclHashcat ) of our top forty password patterns that were identified for this quarter. Additionally, I put together one for everything that we’ve cracked for the first half of the year. You can download the files here: Top40_Q2 and Top40 Q1 and Q2. I plan on keeping up with this each quarter, so check back in next quarter to see how this mask files have changed and to see how well we’ve done across the three quarters.
For more information on how we built our GPU-enhanced password cracking box, check out our slides
For a general outline of our password cracking methodology check out this post
Explore More Blog Posts
How Secure Are Your SaaS Applications? Pentesting for SaaS Providers
Proactive SaaS pentesting protects data, ensures compliance, and builds trust. Learn best practices for securing APIs and cloud apps.

NetSPI Celebrates Our 2025 Partners of the Year
Congratulations to NetSPI’s 2025 Partner of the Year Recipients Stratascale, Defy Security, VLCM, BlackLake Security, Consortium, Softcat, CDW UK, ConnexIT, and AWS.

When Your AI Provider Goes Bankrupt: 6 CISO Insights to Stay Ahead of AI Vendor Failure
AI vendor failure poses risks to data, security, and operations. Learn six CISO strategies to prepare for instability and protect your organisation effectively.