Beautifying JSON in Burp

Most penetration testers know the pain of trying to view and modify an unparsed JSON string. For those that don’t, here’s a taste:
{"userId":1234,"username":"JakeReynolds","favorites":["Rubik's cubes","Doctor Who"],"dislikes":["Sushi","Vegetables"]}
When looking at thousands of these strings a day it is important for them to be well formatted and easily understandable. There currently exists a Burp Extension for beautifying JSON but it is written in Python, which requires Jython to be downloaded and added to Burp. There were also some issues with Jython and that extension not being as dependable as hoped. Due to those reasons we ported that functionality to Java which is run natively by Burp.
Java makes this extension one-click install, with support from Google’s GSON parser. The source code can be found on our Github as well as PortSwigger’s Github which includes updated build instructions.
To install, simply go to Burp > Extender > BApp Store and select “JSON Beautifier”. The next time there is a JSON request in any of the Burp tabs there will be the option of “JSON Beautifier”. Any content modified in this tab will also be modified in the “Raw” tab. An example is below:
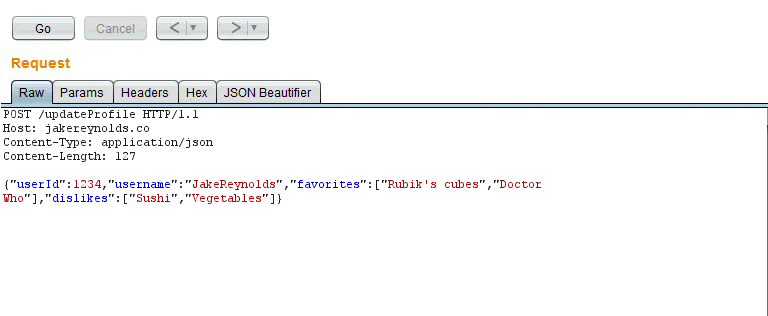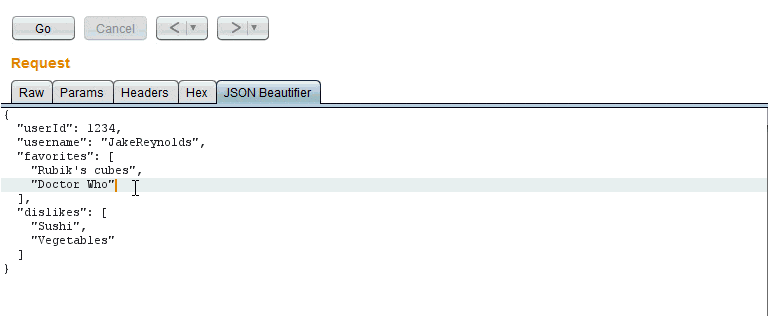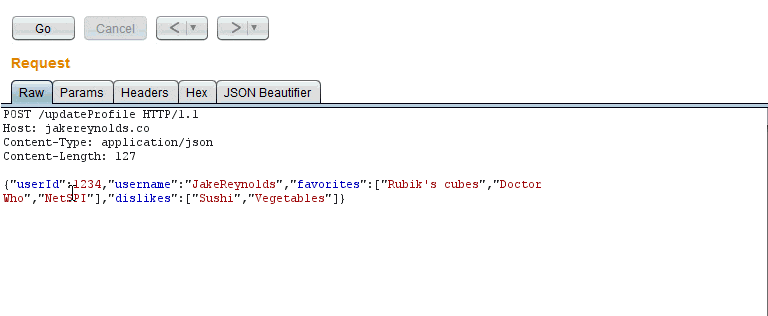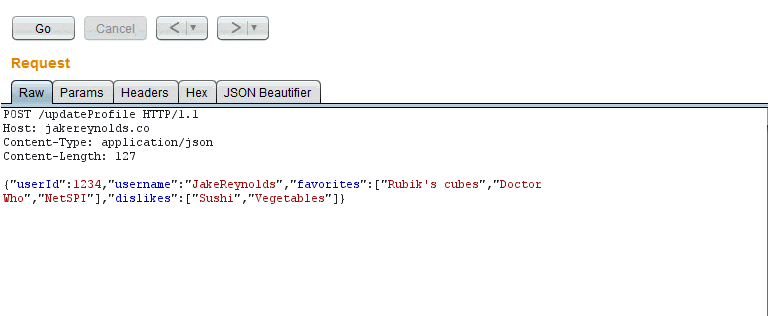
Thanks for checking out our Burp Extension! If you would like any features added feel free to create an issue on Github.
Explore More Blog Posts

CVE-2026-1731 – BeyondTrust RCE Overview and Takeaways
Learn about CVE-2026-1731, a critical RCE vulnerability in BeyondTrust RS & PRA products. Discover its impact, affected versions, and remediation steps.

Pipe Dreams: Remote Code Execution via Quest Desktop Authority Named Pipe
Discover the risks of the CVE-2025-67813 vulnerability in Quest Desktop Authority. Learn how this RCE flaw impacts your organization and how to mitigate it.

Ivanti Endpoint Manager Mobile (EPMM) [CVE-2026-1281 & CVE-2026-1340]: Overview & Takeaways
Ivanti has disclosed two critical zero‑day vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM), tracked as CVE‑2026‑1281 and CVE‑2026‑1340. Both vulnerabilities have been exploited in active attacks and allow unauthenticated remote threat actors to compromise EPMM appliances.