Why Your Security Program Needs Domain Monitoring

Most security professionals dedicate their efforts to protecting the assets they own, such as their websites, email servers, and digital infrastructure. They focus on hardening their legitimate domains, implementing SSL certificates, and ensuring their web properties follow security best practices. These defensive measures are undeniably important for protecting the assets you directly control.
But what about the look-alike domains that impersonate your organization, deceive your customers, and exploit your brand reputation?
This blind spot represents one of the most damaging yet overlooked threats facing modern enterprises. Research performed by CISA shows that phishing attacks (which often launch from look-alike domains) account for over 90% of successful data breaches. However, organizations routinely discover fraudulent domains impersonating their brand only after customers report suspicious activity or financial losses occur. By then, the damage to reputation and customer trust may already be irreversible.
The reality is that attackers don’t need to breach your defenses when they can simply impersonate your brand. Look-alike domains enable threat actors to create malicious websites that appear legitimate enough to deceive both employees and customers alike, adding risk outside what traditional security controls monitor. n this blog, we’ll discuss the risks of domain abuse and how NetSPI’s Domain Monitoring capabilities provide visibility into this critical threat vector.
The Expanding Attack Surface Challenge
As organizations expand their digital presence, their brand becomes increasingly valuable and targeted. Many companies focus on discovering and securing their owned assets, which is important and they should continue to do, however there are many assets such as look-alike domains and dark web data that a company may not own but are still related to and can affect the organization. As your attack surface continues to grow and change, it creates new opportunities for attackers to exploit the trust associated with your brand.
The sophistication of domain-based attacks has evolved dramatically. Attackers employ homograph attacks using visually identical characters from different alphabets, register domains with subtle hyphenations or character substitutions, and abuse legitimate-looking subdomains that can fool even security-aware users.
Let’s dig into look-alike domains more.
About Look-alike Domains
Look-alike domains (sometimes called “doppelganger domains” or “typosquatting domains”) represent an ecosystem where cybercriminals impersonate legitimate organizations. If your legitimate domain is company.com, attackers might register compny.com (missing an ‘a’), cοmpany.com (using a Greek omicron instead of ‘o’), company.security-update.com (subdomain abuse), or c0mpany.com (zero instead of ‘o’).
Look-alike domains affect virtually every organizational stakeholder through a range of attack methods:
- Customers face credential theft and financial fraud through phishing campaigns and fraudulent e-commerce sites.
- Employees become victims of business email compromise attacks that authorize fraudulent wire transfers or credential harvesting portals that capture sensitive information.
- IT and security teams must respond to incidents that bypass traditional defenses, including malware distribution disguised as legitimate updates and command-and-control infrastructure.
- Executive leadership faces regulatory scrutiny, legal liability, and reputational damage when these sophisticated social engineering campaigns successfully exploit organizational trust.
Once registered, these domains can remain dormant for months before being weaponized. They can be sold to other criminals, combined with other attack infrastructure, and repurposed for different campaigns. Early detection can mean the difference between preventing an attack and experiencing widespread customer fraud, regulatory violations, and lasting brand damage.
Registered Look-alike Domains: Active Threats in Motion
Registered look-alike domains represent immediate, active threats to your organization. These domains have been purchased by threat actors and may already be configured to impersonate your brand, host phishing pages, or serve as infrastructure for ongoing attacks.
The impact extends across your entire organization. Security operations teams must investigate each suspicious domain. Legal teams face the complex process of pursuing takedown requests through registrars and hosting providers. Marketing teams manage customer notifications and damage control. Executive leadership deals with regulatory reporting requirements and financial consequences.
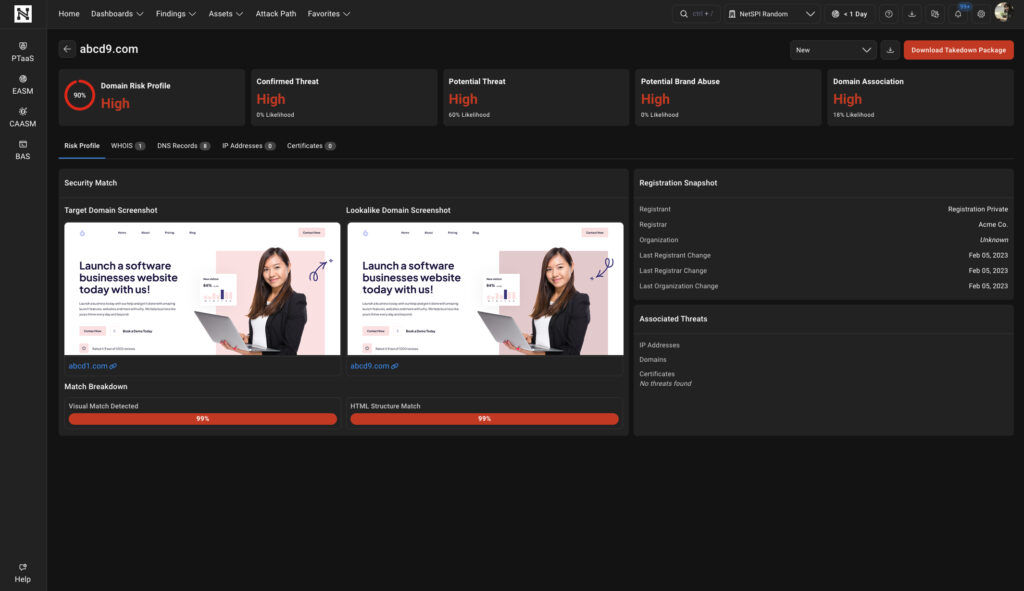
Comprehensive domain monitoring requires capabilities that go beyond simple registration alerts. Organizations need rich contextual intelligence including risk profiles, WHOIS records, IP address information, DNS records, and certificate data in order to prioritize response efforts and build evidence for takedown requests.
Response demands swift action with coordinated efforts across legal, technical, and communications functions. Organizations must generate comprehensive takedown packages, submit requests to domain registrars and hosting providers, notify affected customers, and implement enhanced monitoring. The faster you act, the less damage attackers can inflict.
Unregistered Look-alike Domains: Proactive Defense Opportunities
While registered look-alike domains represent active threats, unregistered look-alike domains present a unique opportunity for proactive defense. These are the domain variations that attackers haven’t yet purchased but could easily weaponize in future campaigns.
Identifying unregistered look-alike domains allows organizations to implement defensive registration strategies, purchasing high-risk variations before threat actors can acquire them. This proactive approach eliminates entire attack vectors by redirecting these domains to legitimate properties, improving the customer experience and reducing risk. Organizations can then monitor registration attempts, receive early warning of potential threats, and demonstrate comprehensive brand protection efforts to stakeholders and leadership.
The Path Forward: Continuous Registered and Unregistered Domain Monitoring
The modern threat landscape demands a fundamental shift from reactive incident detection and response to proactive threat identification and neutralization. Organizations can no longer afford to discover domain impersonation attacks only after customers report fraud.
This critical need is precisely why NetSPI has expanded our offerings to include comprehensive Domain Monitoring capabilities within our Penetration Testing as a Service (PTaaS) platform. Domain monitoring extends our modern PTaaS capabilities for proactive and continuous security, identifying threats that exist outside your direct control but directly target your organization. By integrating automated look-alike domain discovery within the platform, organizations can now maintain complete visibility across both registered and unregistered domains that could be used to impersonate their brand and extend their external threat landscape.
NetSPI Domain Monitoring continuously discovers and assesses look-alike domains related to your organization, providing deep contextual intelligence including risk profiles, WHOIS records, IP details, DNS records, and certificate data. The NetSPI Platform streamlines response by allowing users to generate pre-filled takedown reports with all relevant evidence and technical details in a single click, enabling rapid action against high-risk domains.
Our domain monitoring capabilities surface potential look-alike domains, categorizing each as a confirmed threat, potential threat, or potential brand abuse. This insight empowers security teams to prioritize their response efforts and allocate resources where they matter most.
The question facing security leaders isn’t whether attackers will attempt to impersonate their organization; it’s whether they’ll detect and neutralize these threats before customers and employees are defrauded and brand reputation is damaged.
Whether you are looking for continuous monitoring of your external attack surface and digital risks, or a point-in-time pentest, NetSPI is your trusted partner, extending your security by meeting your needs today and supporting you on your journey to comprehensive proactive security.
To learn more, contact us, or check out our announcement on Domain Monitoring.
Explore More Blog Posts

CVE-2026-1731 – BeyondTrust RCE Overview and Takeaways
Learn about CVE-2026-1731, a critical RCE vulnerability in BeyondTrust RS & PRA products. Discover its impact, affected versions, and remediation steps.

Pipe Dreams: Remote Code Execution via Quest Desktop Authority Named Pipe
Discover the risks of the CVE-2025-67813 vulnerability in Quest Desktop Authority. Learn how this RCE flaw impacts your organization and how to mitigate it.

Ivanti Endpoint Manager Mobile (EPMM) [CVE-2026-1281 & CVE-2026-1340]: Overview & Takeaways
Ivanti has disclosed two critical zero‑day vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM), tracked as CVE‑2026‑1281 and CVE‑2026‑1340. Both vulnerabilities have been exploited in active attacks and allow unauthenticated remote threat actors to compromise EPMM appliances.
