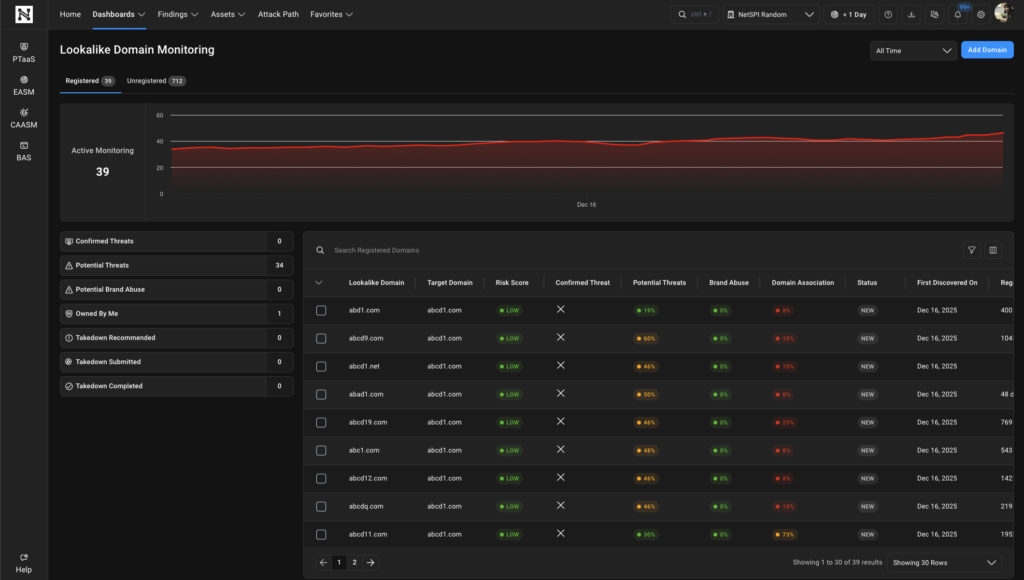
Domain Monitoring
NetSPI’s Domain Monitoring helps organizations identify look-alike domains that resemble their legitimate domains but are be used by attackers for brand impersonation, fraud, phishing, or malware campaigns. This is available for free with your pentesting services.
Monitor Fraudulent Domain Activity
Domain Monitoring Services help organizations detect registered and unregistered look-alike domains, web addresses that resemble a company’s legitimate domain and are often used in brand impersonation, fraud, phishing, or malware campaigns. Attackers create these domains by making subtle modifications to real domain names that are difficult to spot at first glance. Common use cases for attackers deploying look-alike domains include:
-
Phishing Campaigns
-
Credential Harvesting
-
Malware Distribution
-
Brand Impersonation
-
Command & Control (C2)
-
Social Engineering
“”
Executive Blog
“The question facing security leaders isn’t whether attackers will attempt to impersonate their organization, it’s whether they can detect and neutralize these threats before customers are defrauded and brand reputation is damaged.”
Key Features
-
Potential Threat Score
-
Confirmed Threat Score
-
Brand Abuse Score
-
Domain Association
-
Takedown Reports
-
Proactive Acquisition
” ”