
ITPro Today: CISOs Take Note: Is Needless Cybersecurity Strangling Your Business?
While it may seem like adding more tools to your enterprise’s security stack inherently strengthens protection, that’s not always necessarily the case.
ITPro Today featured insights from NetSPI CEO Aaron Shilts in an article that challenges this assumption. The piece explores how outdated and redundant cybersecurity tools can actually create operational headaches – leading to alert fatigue, delayed incident response, and even dangerous blind spots in threat detection. In today’s fast-evolving threat landscape, it’s crucial that companies regularly audit their security stack to ensure tools are complementary, current, and truly effective. Read the preview below or view the full article online that addresses how – when done right – less can be more.
+ + +
There can never be too much cybersecurity, right? Wrong, says Jason Keirstead, vice president of security strategy at AI security developer Simbian. “Cybersecurity is not always a place where more is better,” he observes in an online interview. “Having redundant tools in your security stack, duplicating functions, can create increased churn and workloads, causing security operations center analysts to deal with superfluous, unnecessary alerts and information.”
The problem can grow even more serious if a tool is redundant because it’s outdated . . . Additionally, outdated tools can directly affect employees, hampering organizational productivity.
Aaron Shilts, president and CEO of security technology firm NetSPI, agrees. “For IT and security teams, redundant and obsolete security tools or measures increase workflows, hurt efficiency, and extend incident response and patch time,” he explains via email.
You can read the full story here.
Authors:
Explore More News

ChannelLife: Australian Retailers Face Holiday Surge in Cyber Scams & Threats
As retailers enter peak holiday shopping season, cybersecurity experts warn of escalating threats targeting retailers and consumers. Learn about common risks and ways to avoid them this holiday season.
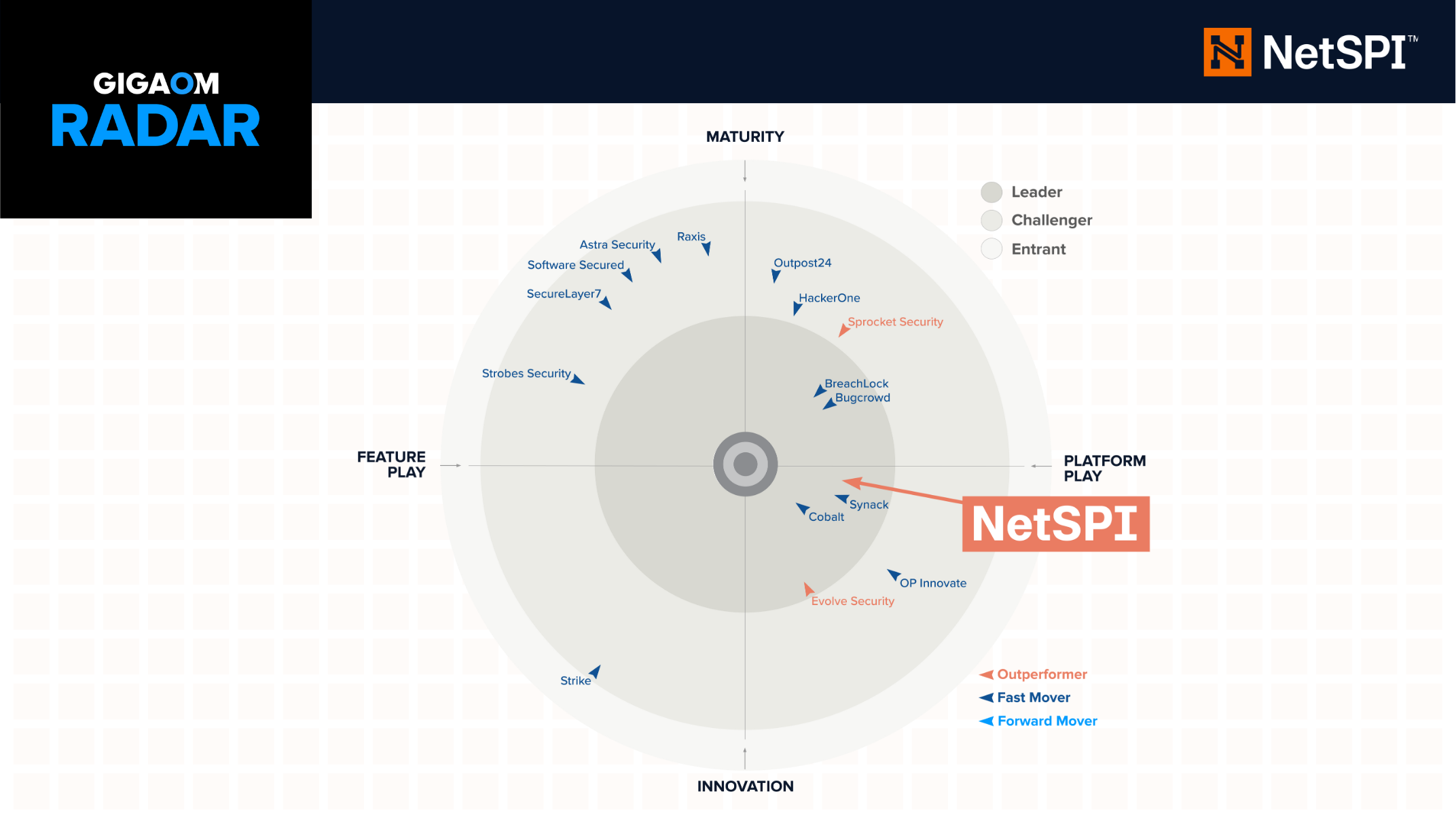
NetSPI Named a Leader and Outperformer in the 2025 GigaOm Radar for Penetration Testing as a Service (PTaaS)
NetSPI named Leader and Outperformer in 2025 GigaOm Radar for PTaaS, recognized for innovation, growth, and platform excellence.

TechChannel: Why Mainframe Security Postures Vary So Widely
Why does the state of mainframe security vary so widely? NetSPI’s Phil Young reveals common gaps, from FTP and weak MFA to lax data access.


