During phishing engagements, one of the key steps is to ensure that targeted users can access your phishing website. Many companies have web content filtering services or solutions in place at their outbound gateway, ensuring their users can’t access things they shouldn’t. These filtering services can often cause problems during phishing attacks by preventing target users from accessing the phishing site.
Websites are categorized using multiple methods and techniques. URL structure and content, specific keywords, IP address, and file types can all be considered by web filters when determining a site’s category. Most still populate a vast majority of well-known sites using a subscription service to database(s) to automate web categorization such as Cyberoam’s WebCat. In this case, subscribers get an updated list of URLs and categories multiple times a week, which attempts to stay on top of emerging threats and potentially malicious sites that are discovered or reported. Other products and services use their own custom web crawlers to determine proper categories.
In multiple corporate environments I have encountered, web filters run in a “fail-closed” configuration, meaning that if a website has not been seen by the web filter before, it will be automatically blocked. Thankfully for pentesters , many of these web content filters allow anyone to submit a categorization for a new URL via easy to use support websites. Once the website has been reviewed, which can take anywhere from thirty minutes to multiple days, the content filter either places the URL into the user suggested category or into a category deemed more appropriate. These updates are then pushed down to the associated appliances, ensuring your website categorization is in place during any phishing attempt. It is important to note that customers of some web content filters can choose how often they update the databases, which may delay the new categorization from being recognized. More so, I couldn’t find specific language on any of the web content filters stating how often they re-check that the categorization is appropriate. Because of this, a malicious website owner could run a stand-in website while the web content filter checks the URL for an appropriate categorization, and then modify the site to something else entirely after receiving a category.
Below is a quick, non-exhaustive list of some of the more popular web filters for submitting site categorization:
Submitting the URL categorization requests for these sites is trivial, but I’ll step through the process. The sites generally prompt for a URL first so it can attempt to look it up in their database.
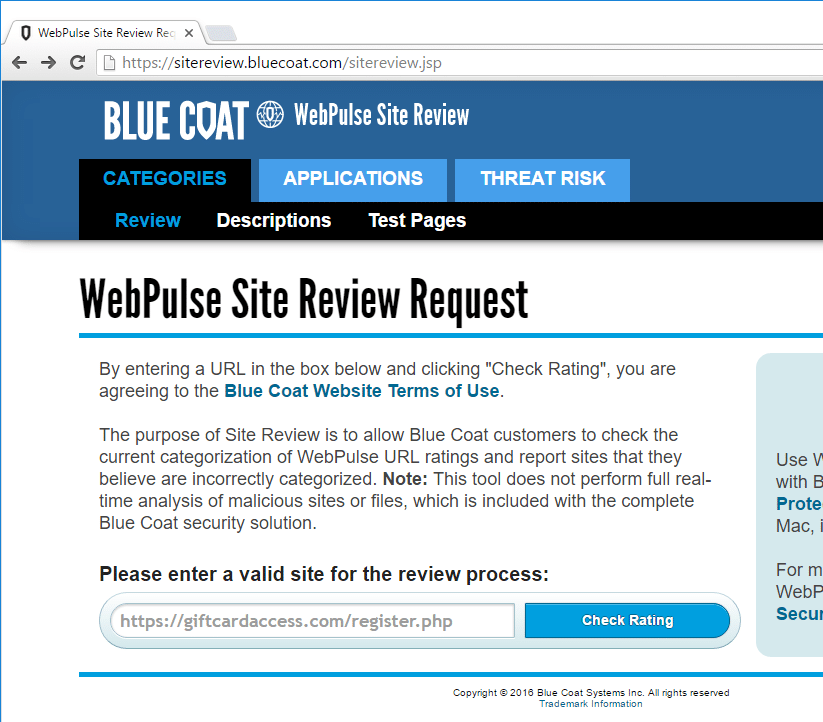
After a quick lookup, the site should report back the current status of the URL; if it is categorized already or not. These sites should allow you to submit a new categorization for the URL even if the site already has one.
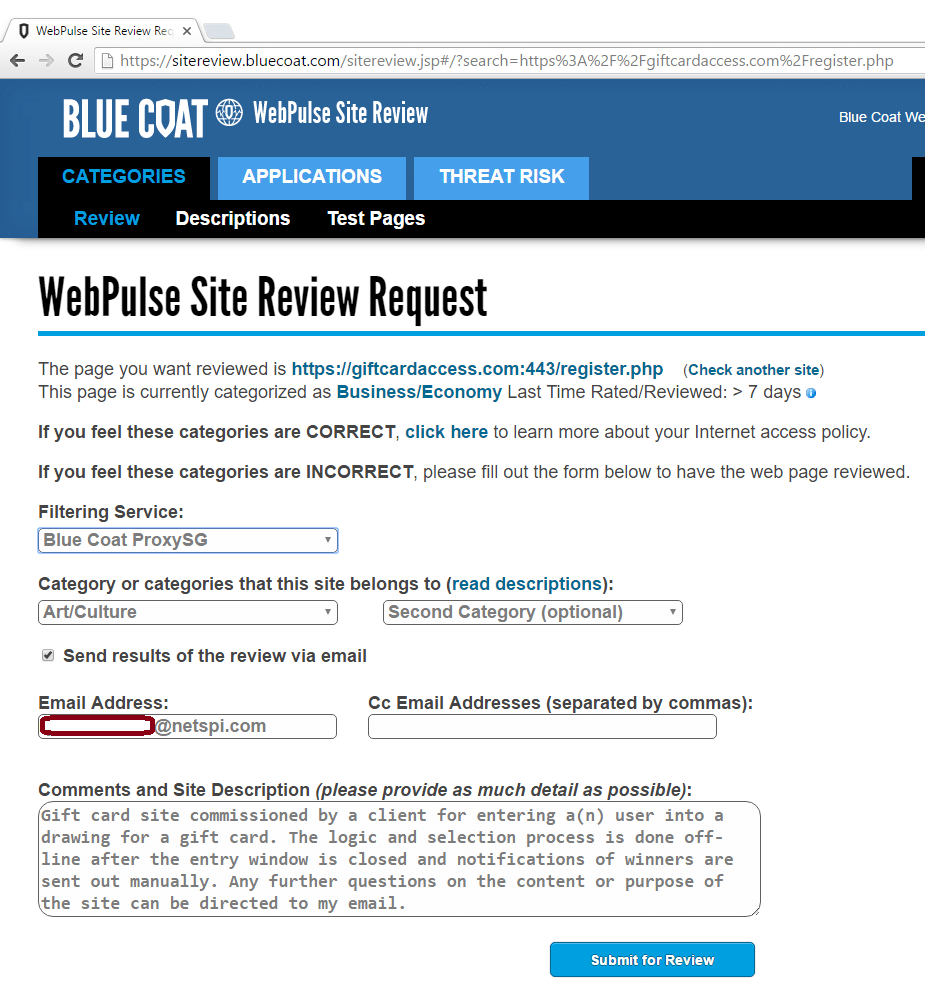
Once the URL is submitted, it’s put into the queue to review. This step can be automated or performed manually, depending on the company. After the URL has been categorized, an email is sent out to the provided address informing that user of the change.
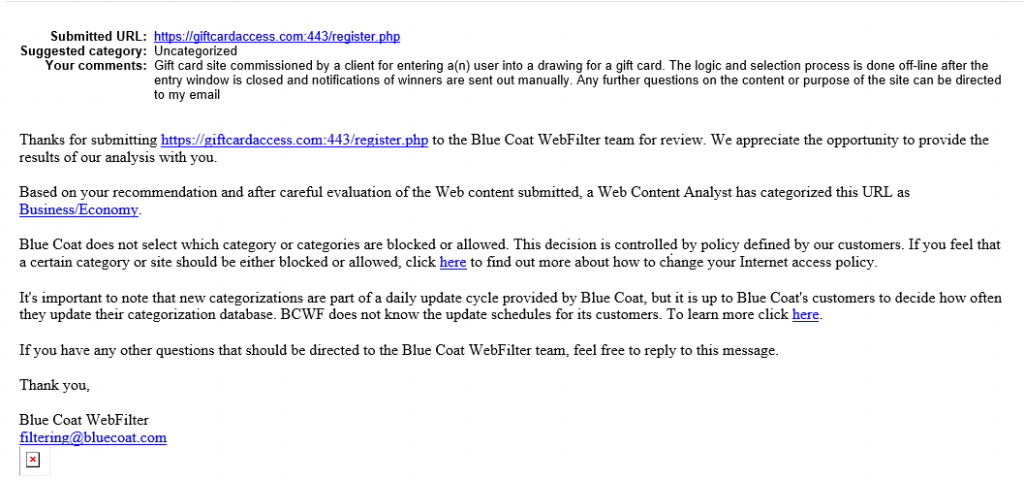
After the site has been categorized and the new policy has been pushed to the product(s) onsite, users should be able to now access the site. It is important to note that even if a site has been categorized, the client needs to allow users to access that specific category. If your site is categorized as one that is not allowed through the web filter, the end result will a failed phishing campaign.
Happy phishing!