4 Risk-Based Vulnerability Management Realities Cybersecurity Leaders Must Face
Let’s start by defining the goal: a risk-based vulnerability management program. A risk-based vulnerability management program focuses on finding and fixing the vulnerabilities based on the damage it could cause if exploited and how likely exploitation is… in other words, the ones that pose the greatest risk to your business.
Even the majority of board members across the globe view cybersecurity as a business risk versus a technology risk, according to a survey from Gartner. It makes sense why most security leaders are working hard to shift to this model as organizations are swamped with vulnerabilities – notably, high-severity, business critical vulnerabilities.
Last year, a record number of critical vulnerabilities were disclosed to the National Institute of Standards and Technology (NIST): 10,342 (source: Security Magazine). A check-the-box, compliance-driven vulnerability management program will no longer cut it. As serious vulnerabilities are on the rise, it’s up to us to determine which are fixed first.
Before you can successfully implement a risk-based program, there are four realities you must face:
- You will have security vulnerabilities that you will never address
- CVSS scores do not represent business risk
- To have an effective risk-based program, we have to lessen the gap between IT and business
- We must adopt a “we’re all in this together” mentality to tackle cybersecurity risk
In this blog post, I’ll dig into each of these realities and the steps you can take to come to terms with and, in many cases, overcome them. First, a quick primer on risk scoring, a key component to risk-based vulnerability management.
An introduction to risk scoring
At NetSPI, one way we’re helping our clients address these challenges, or “realities” as I refer to in this article, is through risk scoring. In simple terms, a risk score quantifies risk for more accurate and efficient vulnerability remediation prioritization.
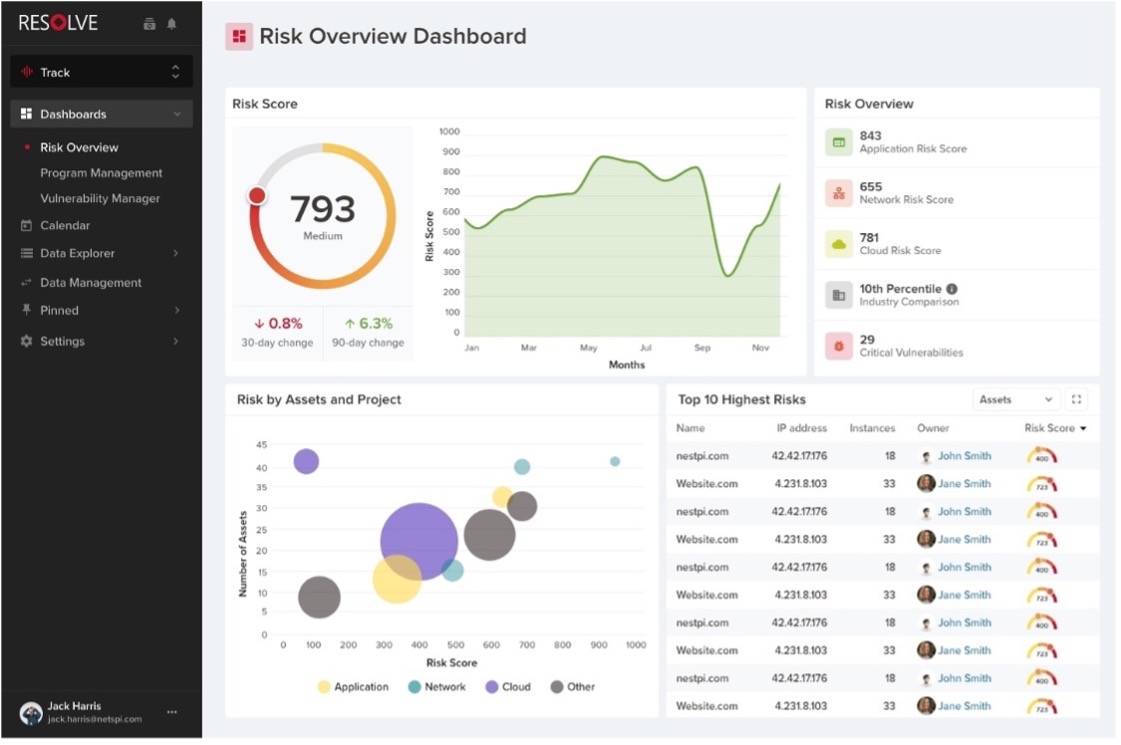
If you’re a NetSPI customer, you may have noticed the new Risk Overview Dashboard in Resolve™, our PTaaS platform. The dashboard features an aggregate risk score, composite risk scores for applications, networks, and cloud, an industry benchmark, the number of open critical vulnerabilities, the riskiest projects or assets, the top 10 highest risks, and more.
NetSPI’s Risk Score is calculated based on transparent methodology that considers vulnerability risk (impact, likelihood, environmental modifiers, and temporal modifiers), threat actor risk, remediation risk, and industry risk to quantify risk levels on any given asset, project, network, or an entire organization.
Risk scores can be used for remediation prioritization, resource allocation, cybersecurity spend validation, risk management tracking, industry benchmarking, and more. I like to think of it as a behind-the-scenes program manager for risk-based vulnerability management programs – continue reading to learn why.
You will have security vulnerabilities that you will never address
It is unrealistic to assume that any organization is vulnerability-free. Once you come to terms with this, risk’s role in vulnerability management becomes a lot clearer.
You can have the same vulnerability across 6 different assets, but is it wise to fix them all at once?
Traditionally, this is how many have approached vulnerability management, but the answer is, in most situations, no. It is important to focus on the system with the most risk versus solving the vulnerability across all systems. This holistic approach to vulnerability management is key as it allows you to incorporate business risk into your decisions.
When you start to factor business risk into the mix, you can identify which assets or systems are most likely to be taken advantage of AND create the most damage if exploited. Then, prioritize remediation, budget, and time accordingly.
Risk scoring can help expedite this decision-making process. The higher your risk score, the higher priority that system, asset, network, finding, project, etc. And some with very low risk may not warrant remediation at all.
CVSS scores do not represent business risk
A Common Vulnerability Scoring System (CVSS) score alone cannot provide a full picture of business risk, but it is a strong starting point for the basis of a risk score. CVSS scores are helpful for vulnerability-specific ratings, but they do not incorporate aggregate factors such as active threat intelligence or correlation to other penetration testing data points.
Additionally, CVSS scores follow a standard formula, regardless of the size, industry, or other business factors, leaving little to no room for customization. This results in organizations not getting the complete picture of a vulnerability’s potential impact.
CVSS scores are often used as a metric for return on security investments. I believe they should not be used as such. As an alternative, if you are utilizing a true risk program, risk scoring can be used as a quantitative metric to represent business risk across your organizations.
To have an effective risk-based program, we have to lessen the gap between IT and business
There’s a knowledge gap between IT and the business and we cannot achieve a risk-based vulnerability management program until that gap shrinks.
In the healthcare industry, risk alignment between IT and the business is critical. The business is patient health and safety and its up to security and IT leaders to help the business understand how it directly impacts and protects patient health and safety, whether that’s through protecting Personal Health Information (PHI) or saving lives through ransomware prevention activities.
This is the same with any business. You have to find common ground between what you’re doing from an IT perspective to show how you’re a part of the business and are critical in the day-to-day operations.
A simple shift in the way we talk about cybersecurity to business leaders could make a massive difference. A risk-forward approach is key. Here are two examples of this:
🚫 What does it cost us to protect the business
🚫 How do we secure our technical systems
✔️ What will it cost us if we don’t
✔️ How do we secure our business processes
We must adopt a “we’re all in this together” mentality to tackle cybersecurity risk
Industry benchmarking is an incredibly powerful tool to communicate your risk-based vulnerability management program successes and progress.
However, we must not fall into the pattern of comparing our programs against others in our industry. There is an analogy that we need to retire. It’s used so often that Red Bull even uses it as the premise for one of its most popular commercials. It’s the idea that, if you’re better than your industry peers, you’re less likely to fall victim to a cyberattack.
It is important to remember that we’re all fighting the same fight: to eliminate or alleviate the cybersecurity risks that lurk not only in specific industries but across all organizations. We need to work together, not against one another, for the greater good – and a risk-based vulnerability management program is a step in the right direction. Even auditors and cyber insurers are recognizing this shift towards risk-based programs to steer security programs towards maturity.
With these four realities addressed, there’s no better time to get started. Focus your attention on high-risk vulnerabilities, use risk scores to communicate business risk, shrink the gap between IT and business, and work together to make the shift to a risk-based vulnerability management program a reality for your organization.





