Ken Johnson
More by Ken Johnson
WP_Query Object
(
[query] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "33"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "33"
[compare] => LIKE
)
)
)
[query_vars] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "33"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "33"
[compare] => LIKE
)
)
[error] =>
[m] =>
[p] => 0
[post_parent] =>
[subpost] =>
[subpost_id] =>
[attachment] =>
[attachment_id] => 0
[name] =>
[pagename] =>
[page_id] => 0
[second] =>
[minute] =>
[hour] =>
[day] => 0
[monthnum] => 0
[year] => 0
[w] => 0
[category_name] =>
[tag] =>
[cat] =>
[tag_id] =>
[author] =>
[author_name] =>
[feed] =>
[tb] =>
[paged] => 0
[meta_key] =>
[meta_value] =>
[preview] =>
[s] =>
[sentence] =>
[title] =>
[fields] =>
[menu_order] =>
[embed] =>
[category__in] => Array
(
)
[category__not_in] => Array
(
)
[category__and] => Array
(
)
[post__in] => Array
(
)
[post__not_in] => Array
(
)
[post_name__in] => Array
(
)
[tag__in] => Array
(
)
[tag__not_in] => Array
(
)
[tag__and] => Array
(
)
[tag_slug__in] => Array
(
)
[tag_slug__and] => Array
(
)
[post_parent__in] => Array
(
)
[post_parent__not_in] => Array
(
)
[author__in] => Array
(
)
[author__not_in] => Array
(
)
[search_columns] => Array
(
)
[ignore_sticky_posts] =>
[suppress_filters] =>
[cache_results] => 1
[update_post_term_cache] => 1
[update_menu_item_cache] =>
[lazy_load_term_meta] => 1
[update_post_meta_cache] => 1
[nopaging] => 1
[comments_per_page] => 50
[no_found_rows] =>
[order] => DESC
)
[tax_query] => WP_Tax_Query Object
(
[queries] => Array
(
)
[relation] => AND
[table_aliases:protected] => Array
(
)
[queried_terms] => Array
(
)
[primary_table] => wp_posts
[primary_id_column] => ID
)
[meta_query] => WP_Meta_Query Object
(
[queries] => Array
(
[0] => Array
(
[key] => new_authors
[value] => "33"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "33"
[compare] => LIKE
)
[relation] => OR
)
[relation] => OR
[meta_table] => wp_postmeta
[meta_id_column] => post_id
[primary_table] => wp_posts
[primary_id_column] => ID
[table_aliases:protected] => Array
(
[0] => wp_postmeta
)
[clauses:protected] => Array
(
[wp_postmeta] => Array
(
[key] => new_authors
[value] => "33"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
[wp_postmeta-1] => Array
(
[key] => new_presenters
[value] => "33"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
)
[has_or_relation:protected] => 1
)
[date_query] =>
[request] => SELECT wp_posts.ID
FROM wp_posts INNER JOIN wp_postmeta ON ( wp_posts.ID = wp_postmeta.post_id )
WHERE 1=1 AND (
( wp_postmeta.meta_key = 'new_authors' AND wp_postmeta.meta_value LIKE '{49f583f6e82e73dcfbbb8593876dd64476268f43849de12e6d0f9132c36a8c57}\"33\"{49f583f6e82e73dcfbbb8593876dd64476268f43849de12e6d0f9132c36a8c57}' )
OR
( wp_postmeta.meta_key = 'new_presenters' AND wp_postmeta.meta_value LIKE '{49f583f6e82e73dcfbbb8593876dd64476268f43849de12e6d0f9132c36a8c57}\"33\"{49f583f6e82e73dcfbbb8593876dd64476268f43849de12e6d0f9132c36a8c57}' )
) AND wp_posts.post_type IN ('post', 'webinars') AND ((wp_posts.post_status = 'publish'))
GROUP BY wp_posts.ID
ORDER BY wp_posts.post_date DESC
[posts] => Array
(
[0] => WP_Post Object
(
[ID] => 6836
[post_author] => 33
[post_date] => 2017-02-28 07:00:47
[post_date_gmt] => 2017-02-28 07:00:47
[post_content] => Remote Code Execution on Cisco ASA
A year ago ExodusIntel disclosed a vulnerability affecting the IKE implementation in Cisco's ASA products. The error is due to an overflow in the checking of reassembled IKE fragments, and allows remote code execution from an unauthenticated attacker. More information on the technical aspects of this can be found at ExodusIntel's blog here. As Cisco ASAs are widely used in the industry, we started to see this vulnerability come up in many penetration tests, but it was hard to verify beyond the fact that a scanner found this issue. The consulting team here at NetSPI, as well as our clients, wanted a more verbose verification that this vulnerability was present.
Creating the Verification Tool
In order to get a concrete verification for this, I first read through all the write-ups on the vulnerability. After I had a solid foundation of the flaw itself, I used vulnerability scanners to test a vulnerable ASA in our lab environment and did a packet capture. With this packet capture, and the scanner plugins I was able to figure out a good way to verify the presence of the vulnerability. I implemented a similar verification in Python which included output showing where the fragmentation reassembly fails. The ASA will either respond with an incomplete IKE notify packet, indicating the ASA is vulnerable, or it will drop the invalid fragments and it will not respond, demonstrating that the patch has been applied. Examples of both of these scenarios can be seen below, note that these would typically be externally facing IP addresses, but as they were in a testing lab the WAN interface was on an internal network.
Vulnerable ASA
pentest ~ $ python3 cisco_asa.py 10.10.1.100:500
This tool is used to verify the presence of CVE-2016-1287, an unauthenticated remote code execution vulnerability affecting Cisco's ASA products.
No attempt will be made to execute code, this simply observes behavior of affected versions when malformed fragments are sent to the ASA.
Continue? [y/N]
y
[*] Sending Initiator Request
[*] Received Response
[+] Valid SA found. Moving on
[*] Sending first fragment
[*] Sending second fragment
[*] Notify Payload found. Printing Notify payload data.
Next payload: NONE
Critical bit Not Critical
Payload length: 8
Protocol ID: IKE
SPI Size: 0
Notify Message Type: Invalid Syntax
Notification DATA: missing
[+] Notification data is missing. ASA is vulnerable.
00000000: 66 53 54 71 45 49 58 64 75 6A FD C0 52 32 52 96 fSTqEIXduj..R2R.
00000010: 29 20 22 20 00 00 00 00 00 00 00 24 00 00 00 08 ) " .......$....
00000020: 01 00 00 07 ....
Patched ASA
pentest ~ $ python3 cisco_asa.py 10.10.1.100:500
This tool is used to verify the presence of CVE-2016-1287, an unauthenticated remote code execution vulnerability affecting Cisco's ASA products.
No attempt will be made to execute code, this simply observes behavior of affected versions when malformed fragments are sent to the ASA.
Continue? [y/N]
y
[*] Sending Initiator Request
[*] Received Response
[+] Valid SA found. Moving on
[*] Sending first fragment
[*] Sending second fragment
[*] IKE Fragment was dropped indicating the ASA is not vulnerable.
The code can be found on NetSPI's GitHub here.
[post_title] => Cisco ASA Remote Code Execution - Verifying CVE-2016-1287
[post_excerpt] =>
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => cisco-asa-remote-code-execution-verifying-cve-2016-1287
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-13 00:05:37
[post_modified_gmt] => 2021-04-13 00:05:37
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://netspiblogdev.wpengine.com/?p=6836
[menu_order] => 644
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[1] => WP_Post Object
(
[ID] => 6814
[post_author] => 33
[post_date] => 2017-02-14 07:00:21
[post_date_gmt] => 2017-02-14 07:00:21
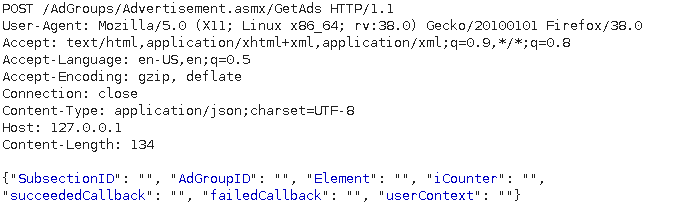
[post_content] => JavaScript Web Service Proxies are an alternative to WSDL (Web Services Description Language) files for interacting with WCF Web Services. The proxy files function as a description of the web service methods, exposing the available service methods as well as their parameters. JavaScript Service Proxies, or JSWS (JavaScript Web Services) as I will be calling them for brevity’s sake, are a component of an AJAX framework and can typically be used in place of WSDLs for the same web services. JSWS uses JavaScript to model the descriptor file, and JSON in transit making it a good alternative to WSDL’s XML as JavaScript and JSON are heavily integrated into all browsers. The client side application will either load the JSWS upon need, or it may be embedded into the page. The JSWS contains JavaScript code that will instruct the browser in the creation of the JSON request. An example of one of these files can be seen below.
Type.registerNamespace('NewsSite.AdGroups');
NewsSite.AdGroups.Advertisement=function() {
NewsSite.AdGroups.Advertisement.initializeBase(this);
this._timeout = 0;
this._userContext = null;
this._succeeded = null;
this._failed = null;
}
NewsSite.AdGroups.Advertisement.prototype={
_get_path:function() {
var p = this.get_path();
if (p) return p;
else return NewsSite.AdGroups.Advertisement._staticInstance.get_path();},
GetAds:function(SubsectionID,AdGroupID,Element,iCounter,succeededCallback, failedCallback, userContext) {
return this._invoke(this._get_path(), 'GetAds',false,{SubsectionID:SubsectionID,AdGroupID:AdGroupID,Element:Element,iCounter:iCounter},succeededCallback,failedCallback,userContext); }}
NewsSite.AdGroups.Advertisement.registerClass('NewsSite.AdGroups.Advertisement',Sys.Net.WebServiceProxy);
NewsSite.AdGroups.Advertisement._staticInstance = new NewsSite.AdGroups.Advertisement();
NewsSite.AdGroups.Advertisement.set_path = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_path(value); }
NewsSite.AdGroups.Advertisement.get_path = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_path(); }
NewsSite.AdGroups.Advertisement.set_timeout = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_timeout(value); }
NewsSite.AdGroups.Advertisement.get_timeout = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_timeout(); }
NewsSite.AdGroups.Advertisement.set_defaultUserContext = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_defaultUserContext(value); }
NewsSite.AdGroups.Advertisement.get_defaultUserContext = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_defaultUserContext(); }
NewsSite.AdGroups.Advertisement.set_defaultSucceededCallback = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_defaultSucceededCallback(value); }
NewsSite.AdGroups.Advertisement.get_defaultSucceededCallback = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_defaultSucceededCallback(); }
NewsSite.AdGroups.Advertisement.set_defaultFailedCallback = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_defaultFailedCallback(value); }
NewsSite.AdGroups.Advertisement.get_defaultFailedCallback = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_defaultFailedCallback(); }
NewsSite.AdGroups.Advertisement.set_enableJsonp = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_enableJsonp(value); }
NewsSite.AdGroups.Advertisement.get_enableJsonp = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_enableJsonp(); }
NewsSite.AdGroups.Advertisement.set_jsonpCallbackParameter = function(value) { NewsSite.AdGroups.Advertisement._staticInstance.set_jsonpCallbackParameter(value); }
NewsSite.AdGroups.Advertisement.get_jsonpCallbackParameter = function() { return NewsSite.AdGroups.Advertisement._staticInstance.get_jsonpCallbackParameter(); }
NewsSite.AdGroups.Advertisement.set_path("/AdGroups/Advertisement.asmx");
NewsSite.AdGroups.Advertisement.GetAds= function(SubsectionID,AdGroupID,Element,iCounter,onSuccess,onFailed,userContext) {NewsSite.AdGroups.Advertisement._staticInstance.GetAds(SubsectionID,AdGroupID,Element,iCounter,onSuccess,onFailed,userContext); }
var gtc = Sys.Net.WebServiceProxy._generateTypedConstructor;
if (typeof(NewsSite.AdGroups.AdGroupInfo) === 'undefined') {
NewsSite.AdGroups.AdGroupInfo=gtc("NewsSite.AdGroups.AdGroupInfo");
NewsSite.AdGroups.AdGroupInfo.registerClass('NewsSite.AdGroups.AdGroupInfo');
}
After the file is loaded the subsequent request will be formatted in the following way.
 A side effect of this file instructing the browser in how the requests must be formatted is that it can also aid an attacker in enumerating web service methods and potential injection points. Before these can be used, it is important to understand when JSWS is in use, and how to identify it.
A side effect of this file instructing the browser in how the requests must be formatted is that it can also aid an attacker in enumerating web service methods and potential injection points. Before these can be used, it is important to understand when JSWS is in use, and how to identify it.
Identifying JSWS
There are multiple different ways to identify when these services are being used in an application. The application may request a JSWS file allowing it to be identified through proxy logs by looking for https://some.domaim.com/WebService.asmx/js. The application may also request the same file with the debug information, https://some.domain.com/WebService.asmx/jsdebug. The jsdebug file will contain additional information about the datatypes of the parameters needed, and which parameters are required. Even if the application is not requesting the jsdebug file it is likely still available.
Alternatively, the application may be using the PageMethods technique, which means the JSWS will be embedded directly into the page.
This will typically be on an aspx page rather than asmx, but it could be present with any extension. This method can be identified by searching server responses for the ‘PageMethods’ string, or by inspecting proxy logs for the method calls (e.g. https://some.domain.com/WebService.aspx/GetInformation)
The JSWS Extension
After identifying that this technology is being used an attacker is able craft all the request variations the web service will accept, but this takes time and can be quite tedious. After starting to see JSWS in assessments more often, I decided to create a Burp extension that would automate this process. The tool is modeled after Eric Gruber’s Wsdler, and functions in the same way. The JSWS extension can be downloaded from https://github.com/NetSPI/JSWS, and is available in the BApp store.
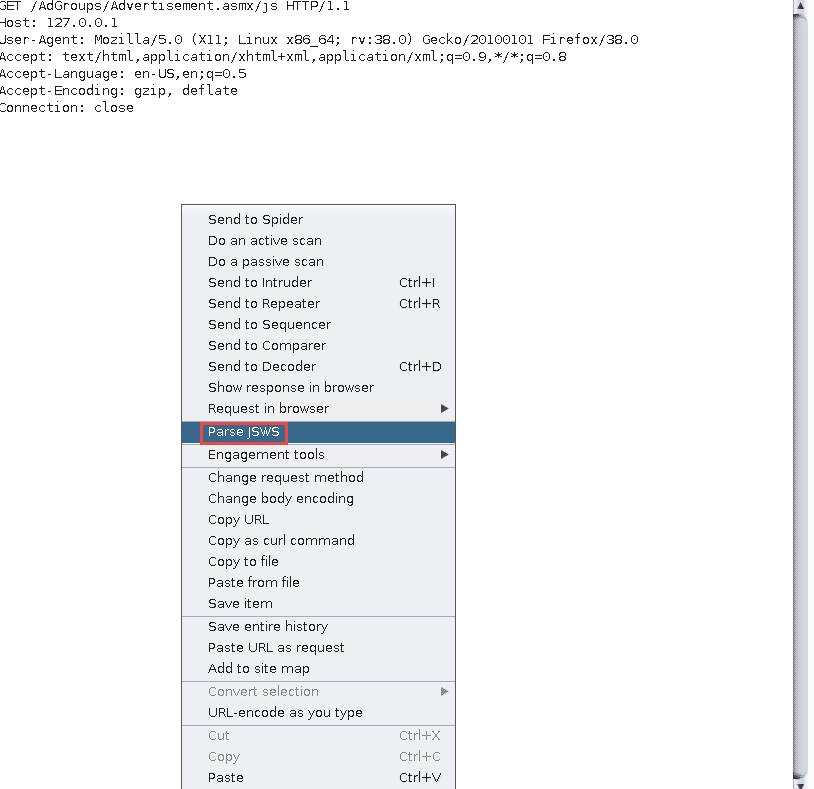
To use this tool, simply right click on the request or response containing the JSWS and click Parse JSWS. If the application is loading the JSWS file, the file should already be in the proxy logs.
 It is recommended to parse the jsdebug file rather than the js file, as it will give the user more information about which types of parameters to tamper with.
If the application uses the PageMethods representation of JSWS, right click on the request or response containing the PageMethods code and click Parse JSWS.
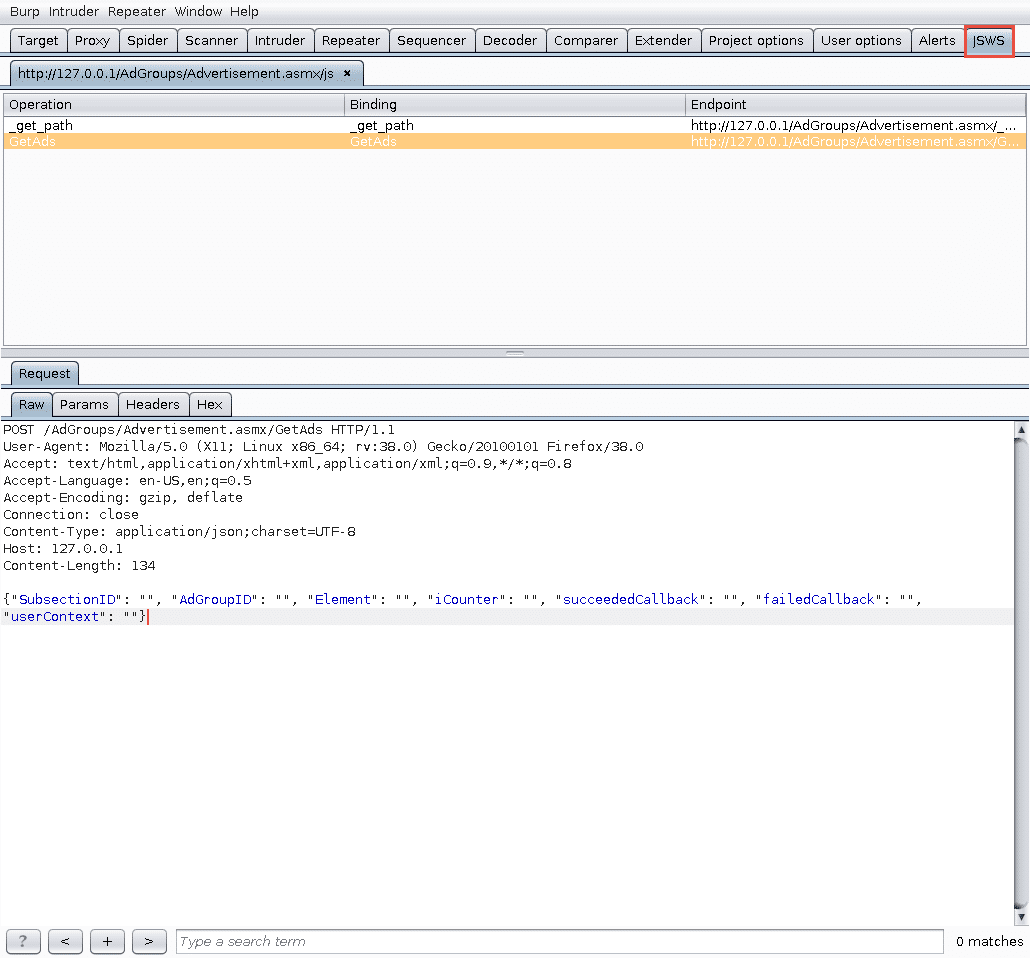
The JSWS extension will then open a JSWS tab, as well as a subtab for the service just parsed. Under this tab are two panes, the top containing all available methods, and the bottom containing the JSON template.
It is recommended to parse the jsdebug file rather than the js file, as it will give the user more information about which types of parameters to tamper with.
If the application uses the PageMethods representation of JSWS, right click on the request or response containing the PageMethods code and click Parse JSWS.
The JSWS extension will then open a JSWS tab, as well as a subtab for the service just parsed. Under this tab are two panes, the top containing all available methods, and the bottom containing the JSON template.
 From here the request can be handled as any JSON request, and can be sent to Repeater for manual testing, or Intruder and Scanner for automated testing.
From here the request can be handled as any JSON request, and can be sent to Repeater for manual testing, or Intruder and Scanner for automated testing.
Conclusion
The extension does not currently detect the presence of JSWS through passive scanning. This is being implemented and will be released in a future build. For any feature requests or bugs you may find please email me or create a ticket on Github.
[post_title] => Attacking JavaScript Web Service Proxies with Burp
[post_excerpt] =>
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => attacking-javascript-web-service-proxies-burp
[to_ping] =>
[pinged] =>
[post_modified] => 2021-06-08 21:47:45
[post_modified_gmt] => 2021-06-08 21:47:45
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://netspiblogdev.wpengine.com/?p=6814
[menu_order] => 646
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
)
[post_count] => 2
[current_post] => -1
[before_loop] => 1
[in_the_loop] =>
[post] => WP_Post Object
(
[ID] => 6836
[post_author] => 33
[post_date] => 2017-02-28 07:00:47
[post_date_gmt] => 2017-02-28 07:00:47
[post_content] => Remote Code Execution on Cisco ASA
A year ago ExodusIntel disclosed a vulnerability affecting the IKE implementation in Cisco's ASA products. The error is due to an overflow in the checking of reassembled IKE fragments, and allows remote code execution from an unauthenticated attacker. More information on the technical aspects of this can be found at ExodusIntel's blog here. As Cisco ASAs are widely used in the industry, we started to see this vulnerability come up in many penetration tests, but it was hard to verify beyond the fact that a scanner found this issue. The consulting team here at NetSPI, as well as our clients, wanted a more verbose verification that this vulnerability was present.
Creating the Verification Tool
In order to get a concrete verification for this, I first read through all the write-ups on the vulnerability. After I had a solid foundation of the flaw itself, I used vulnerability scanners to test a vulnerable ASA in our lab environment and did a packet capture. With this packet capture, and the scanner plugins I was able to figure out a good way to verify the presence of the vulnerability. I implemented a similar verification in Python which included output showing where the fragmentation reassembly fails. The ASA will either respond with an incomplete IKE notify packet, indicating the ASA is vulnerable, or it will drop the invalid fragments and it will not respond, demonstrating that the patch has been applied. Examples of both of these scenarios can be seen below, note that these would typically be externally facing IP addresses, but as they were in a testing lab the WAN interface was on an internal network.
Vulnerable ASA
pentest ~ $ python3 cisco_asa.py 10.10.1.100:500
This tool is used to verify the presence of CVE-2016-1287, an unauthenticated remote code execution vulnerability affecting Cisco's ASA products.
No attempt will be made to execute code, this simply observes behavior of affected versions when malformed fragments are sent to the ASA.
Continue? [y/N]
y
[*] Sending Initiator Request
[*] Received Response
[+] Valid SA found. Moving on
[*] Sending first fragment
[*] Sending second fragment
[*] Notify Payload found. Printing Notify payload data.
Next payload: NONE
Critical bit Not Critical
Payload length: 8
Protocol ID: IKE
SPI Size: 0
Notify Message Type: Invalid Syntax
Notification DATA: missing
[+] Notification data is missing. ASA is vulnerable.
00000000: 66 53 54 71 45 49 58 64 75 6A FD C0 52 32 52 96 fSTqEIXduj..R2R.
00000010: 29 20 22 20 00 00 00 00 00 00 00 24 00 00 00 08 ) " .......$....
00000020: 01 00 00 07 ....
Patched ASA
pentest ~ $ python3 cisco_asa.py 10.10.1.100:500
This tool is used to verify the presence of CVE-2016-1287, an unauthenticated remote code execution vulnerability affecting Cisco's ASA products.
No attempt will be made to execute code, this simply observes behavior of affected versions when malformed fragments are sent to the ASA.
Continue? [y/N]
y
[*] Sending Initiator Request
[*] Received Response
[+] Valid SA found. Moving on
[*] Sending first fragment
[*] Sending second fragment
[*] IKE Fragment was dropped indicating the ASA is not vulnerable.
The code can be found on NetSPI's GitHub here.
[post_title] => Cisco ASA Remote Code Execution - Verifying CVE-2016-1287
[post_excerpt] =>
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => cisco-asa-remote-code-execution-verifying-cve-2016-1287
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-13 00:05:37
[post_modified_gmt] => 2021-04-13 00:05:37
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://netspiblogdev.wpengine.com/?p=6836
[menu_order] => 644
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[comment_count] => 0
[current_comment] => -1
[found_posts] => 2
[max_num_pages] => 0
[max_num_comment_pages] => 0
[is_single] =>
[is_preview] =>
[is_page] =>
[is_archive] =>
[is_date] =>
[is_year] =>
[is_month] =>
[is_day] =>
[is_time] =>
[is_author] =>
[is_category] =>
[is_tag] =>
[is_tax] =>
[is_search] =>
[is_feed] =>
[is_comment_feed] =>
[is_trackback] =>
[is_home] => 1
[is_privacy_policy] =>
[is_404] =>
[is_embed] =>
[is_paged] =>
[is_admin] =>
[is_attachment] =>
[is_singular] =>
[is_robots] =>
[is_favicon] =>
[is_posts_page] =>
[is_post_type_archive] =>
[query_vars_hash:WP_Query:private] => 0a0c0c6fcc4a491e207150940ba50695
[query_vars_changed:WP_Query:private] =>
[thumbnails_cached] =>
[allow_query_attachment_by_filename:protected] =>
[stopwords:WP_Query:private] =>
[compat_fields:WP_Query:private] => Array
(
[0] => query_vars_hash
[1] => query_vars_changed
)
[compat_methods:WP_Query:private] => Array
(
[0] => init_query_flags
[1] => parse_tax_query
)
)

 It is recommended to parse the jsdebug file rather than the js file, as it will give the user more information about which types of parameters to tamper with.
If the application uses the PageMethods representation of JSWS, right click on the request or response containing the PageMethods code and click Parse JSWS.
The JSWS extension will then open a JSWS tab, as well as a subtab for the service just parsed. Under this tab are two panes, the top containing all available methods, and the bottom containing the JSON template.
It is recommended to parse the jsdebug file rather than the js file, as it will give the user more information about which types of parameters to tamper with.
If the application uses the PageMethods representation of JSWS, right click on the request or response containing the PageMethods code and click Parse JSWS.
The JSWS extension will then open a JSWS tab, as well as a subtab for the service just parsed. Under this tab are two panes, the top containing all available methods, and the bottom containing the JSON template.
 From here the request can be handled as any JSON request, and can be sent to Repeater for manual testing, or Intruder and Scanner for automated testing.
From here the request can be handled as any JSON request, and can be sent to Repeater for manual testing, or Intruder and Scanner for automated testing.