Florindo Gallicchio
WP_Query Object
(
[query] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "71"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "71"
[compare] => LIKE
)
)
)
[query_vars] => Array
(
[post_type] => Array
(
[0] => post
[1] => webinars
)
[posts_per_page] => -1
[post_status] => publish
[meta_query] => Array
(
[relation] => OR
[0] => Array
(
[key] => new_authors
[value] => "71"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "71"
[compare] => LIKE
)
)
[error] =>
[m] =>
[p] => 0
[post_parent] =>
[subpost] =>
[subpost_id] =>
[attachment] =>
[attachment_id] => 0
[name] =>
[pagename] =>
[page_id] => 0
[second] =>
[minute] =>
[hour] =>
[day] => 0
[monthnum] => 0
[year] => 0
[w] => 0
[category_name] =>
[tag] =>
[cat] =>
[tag_id] =>
[author] =>
[author_name] =>
[feed] =>
[tb] =>
[paged] => 0
[meta_key] =>
[meta_value] =>
[preview] =>
[s] =>
[sentence] =>
[title] =>
[fields] =>
[menu_order] =>
[embed] =>
[category__in] => Array
(
)
[category__not_in] => Array
(
)
[category__and] => Array
(
)
[post__in] => Array
(
)
[post__not_in] => Array
(
)
[post_name__in] => Array
(
)
[tag__in] => Array
(
)
[tag__not_in] => Array
(
)
[tag__and] => Array
(
)
[tag_slug__in] => Array
(
)
[tag_slug__and] => Array
(
)
[post_parent__in] => Array
(
)
[post_parent__not_in] => Array
(
)
[author__in] => Array
(
)
[author__not_in] => Array
(
)
[search_columns] => Array
(
)
[ignore_sticky_posts] =>
[suppress_filters] =>
[cache_results] => 1
[update_post_term_cache] => 1
[update_menu_item_cache] =>
[lazy_load_term_meta] => 1
[update_post_meta_cache] => 1
[nopaging] => 1
[comments_per_page] => 50
[no_found_rows] =>
[order] => DESC
)
[tax_query] => WP_Tax_Query Object
(
[queries] => Array
(
)
[relation] => AND
[table_aliases:protected] => Array
(
)
[queried_terms] => Array
(
)
[primary_table] => wp_posts
[primary_id_column] => ID
)
[meta_query] => WP_Meta_Query Object
(
[queries] => Array
(
[0] => Array
(
[key] => new_authors
[value] => "71"
[compare] => LIKE
)
[1] => Array
(
[key] => new_presenters
[value] => "71"
[compare] => LIKE
)
[relation] => OR
)
[relation] => OR
[meta_table] => wp_postmeta
[meta_id_column] => post_id
[primary_table] => wp_posts
[primary_id_column] => ID
[table_aliases:protected] => Array
(
[0] => wp_postmeta
)
[clauses:protected] => Array
(
[wp_postmeta] => Array
(
[key] => new_authors
[value] => "71"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
[wp_postmeta-1] => Array
(
[key] => new_presenters
[value] => "71"
[compare] => LIKE
[compare_key] => =
[alias] => wp_postmeta
[cast] => CHAR
)
)
[has_or_relation:protected] => 1
)
[date_query] =>
[request] => SELECT wp_posts.ID
FROM wp_posts INNER JOIN wp_postmeta ON ( wp_posts.ID = wp_postmeta.post_id )
WHERE 1=1 AND (
( wp_postmeta.meta_key = 'new_authors' AND wp_postmeta.meta_value LIKE '{d0be621f6f8b0fee0baab71bbb7620235c7e2b4f433ff90e342cf813a65fa82f}\"71\"{d0be621f6f8b0fee0baab71bbb7620235c7e2b4f433ff90e342cf813a65fa82f}' )
OR
( wp_postmeta.meta_key = 'new_presenters' AND wp_postmeta.meta_value LIKE '{d0be621f6f8b0fee0baab71bbb7620235c7e2b4f433ff90e342cf813a65fa82f}\"71\"{d0be621f6f8b0fee0baab71bbb7620235c7e2b4f433ff90e342cf813a65fa82f}' )
) AND wp_posts.post_type IN ('post', 'webinars') AND ((wp_posts.post_status = 'publish'))
GROUP BY wp_posts.ID
ORDER BY wp_posts.post_date DESC
[posts] => Array
(
[0] => WP_Post Object
(
[ID] => 27771
[post_author] => 71
[post_date] => 2022-05-14 10:41:00
[post_date_gmt] => 2022-05-14 15:41:00
[post_content] =>
On May 14, 2022, NetSPI's VP of Strategic Solutions, Florindo Gallicchio, was featured in the Digital Journal article called Safeguarding Data from Dangerous Threats like Ryuk. Preview the article below, or read the full article online.
To maintain business continuity, each organization should develop a data protection and back-up strategy. To reduce the risk of data loss, firms need to back up files and databases. Firms will also want to back up their operating systems, applications, configuration. This ensures the protection of data from unauthorized access and data corruption throughout its lifecycle.
According to Florindo Gallicchio, Managing Director, Head of Strategic Solutions at NetSPI: “It’s time to acknowledge how critical data backup has become, especially since many ransomware strains attempt to delete backup files, as we witnessed with Ryuk.”
Ryuk is a type of ransomware known for targeting large, public-entity Microsoft Windows cybersystems. Here, the threat actors make sure that essential files are encrypted so they can ask for large ransom.
Expanding on the risks faced by the corporate sector, Gallicchio says: “Most businesses are faced with two significant risks when it comes to backups: the theft and public disclosure of sensitive data, and the disruption of critical business functions.”
In terms of the consequences, Gallicchio says: “If either of these risks occur, organizations could endure devastating consequences. To make sure that doesn’t happen, organizations need to proactively put strategies in place to bolster protection against these threat actors.”
Read the full article online.
[post_title] => Digital Journal: Safeguarding Data from Dangerous Threats like Ryuk
[post_excerpt] => On May 14, 2022, NetSPI's VP of Strategic Solutions, Florindo Gallicchio, was featured in the Digital Journal article called Safeguarding Data from Dangerous Threats like Ryuk.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => digital-journal-safeguarding-data-from-dangerous-threats-like-ryuk
[to_ping] =>
[pinged] =>
[post_modified] => 2023-01-23 15:10:38
[post_modified_gmt] => 2023-01-23 21:10:38
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=27771
[menu_order] => 270
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[1] => WP_Post Object
(
[ID] => 27588
[post_author] => 71
[post_date] => 2022-03-31 13:57:38
[post_date_gmt] => 2022-03-31 18:57:38
[post_content] =>
On March 31, 2022, Florindo Gallicchio was featured in the VMblog article, Don't Forget to Celebrate World Backup Day 2022 - Hear From Industry Experts. Preview the article below, or read the full article online.
+ + +
What is World Backup Day?
World Backup Day is celebrated on March 31st – and it is a yearly reminder for both organizations and individuals to secure their files via backups and how to improve the security per device and solution. It’s the day to prevent data loss.
Even though backing up data should be common knowledge:
- 21% of people have never made a backup
- 113 phones are lost or stolen every minute
- 29% of data loss cases are caused by accident
- 30% of all computers are already infected by malware
Hopefully this day will make everyone think twice about their situation, and educate themselves on the various options available to them so that they can get things backed up. A backup is only as good as your ability to recover the data. As part of your backup strategy, make sure to have a recovery plan. Be prepared to recover an entire system, a folder or collection of folders, and a single file. World Backup Day should bring about awareness and create a reminder for all of us to backup things up. No matter how secure or safe you feel about your data, know that it's important to backup your files.
Don't take my word for it. Hear from some of the leading industry experts in the backup and disaster recovery industry for more commentary and expertise:
Florindo Gallicchio, Managing Director, Head of Strategic Solutions at NetSPI
"This World Backup Day, it’s time to acknowledge how critical data backup has become, especially since many ransomware strains attempt to delete backup files, as we witnessed with Ryuk. Most businesses are faced with two significant risks when it comes to backups: the theft and public disclosure of sensitive data, and the disruption of critical business functions. If either of these risks occur, organizations could endure devastating consequences. To make sure that doesn’t happen, organizations need to proactively put strategies in place to bolster protection against these threat actors.
One way to do this is by ensuring that backups with all of the organization’s critical data are routinely, completely, and securely assessed – as this is a necessary step in recovering from a possible ransomware attack. These backups should be encrypted so that sensitive data is not disclosed and stored in such a way that an organization can recover its data in a timely manner, as this is necessary to minimize disruption to business operations. Additionally, organizations should regularly revisit and test disaster recovery and business continuity plans to validate that ransomware and other threats won't impact the integrity of any backups.
Finally, any highly important, sensitive data should be stored on an entirely separate network from the internal network. That way, if ransomware targets the desktop network, it cannot spread to the critical systems and cause complete chaos. While this is a long-term, and challenging strategy, it’s well worth the time and investment for organizations to counter the continuous risk of critical data loss."
[post_title] => VMblog: Don't Forget to Celebrate World Backup Day 2022 - Hear From Industry Experts [post_excerpt] => On March 31, 2022, Florindo Gallicchio was featured in the VMblog article, Don't Forget to Celebrate World Backup Day 2022 - Hear From Industry Experts. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => vmblog-dont-forget-to-celebrate-world-backup-day-2022-hear-from-industry-experts [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:45 [post_modified_gmt] => 2023-01-23 21:10:45 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27588 [menu_order] => 288 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [2] => WP_Post Object ( [ID] => 27587 [post_author] => 71 [post_date] => 2022-03-31 13:54:03 [post_date_gmt] => 2022-03-31 18:54:03 [post_content] =>On March 31, 2022, Florindo Gallicchio was featured in the Security Magazine article, Reduce Data Breach Risk on World Backup Day 2022. Preview the article below, or read the full article online.
+ + +
Backing up enterprise data can reduce the effects of ransomware or a data breach. After experiencing a ransomware attack, 83% of victims paid to restore their data — preparing for cyberattacks in advance by conducting frequent data backups may help reduce these costs.
Spreading awareness about data backups is the mission of World Backup Day, which began in 2011. For World Backup Day 2022, Security magazine spoke with security leaders about the importance of enterprise cybersecurity.
Florindo Gallicchio, Managing Director, Head of Strategic Solutions at NetSPI:
This World Backup Day, it’s time to acknowledge how critical data backup has become, especially since many ransomware strains attempt to delete backup files, as we witnessed with Ryuk. Most businesses are faced with two significant risks when it comes to backups: the theft and public disclosure of sensitive data, and the disruption of critical business functions. If either of these risks occur, organizations could endure devastating consequences. To make sure that doesn’t happen, organizations need to proactively put strategies in place to bolster protection against these threat actors.
One way to do this is by ensuring that backups with all of the organization’s critical data are routinely, completely, and securely assessed –– as this is a necessary step in recovering from a possible ransomware attack. These backups should be encrypted so that sensitive data is not disclosed and stored in such a way that an organization can recover its data in a timely manner, as this is necessary to minimize disruption to business operations. Additionally, organizations should regularly revisit and test disaster recovery and business continuity plans to validate that ransomware and other threats won't impact the integrity of any backups.
Finally, any highly important, sensitive data should be stored on an entirely separate network from the internal network. That way, if ransomware targets the desktop network, it cannot spread to the critical systems and cause complete chaos. While this is a long-term and challenging strategy, it’s well worth the time and investment for organizations to counter the continuous risk of critical data loss.
[post_title] => Security Magazine: Reduce Data Breach Risk on World Backup Day 2022 [post_excerpt] => On March 31, 2022, Florindo Gallicchio was featured in the Security Magazine article, Reduce Data Breach Risk on World Backup Day 2022. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => security-magazine-reduce-data-breach-risk-on-world-backup-day-2022 [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:45 [post_modified_gmt] => 2023-01-23 21:10:45 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27587 [menu_order] => 289 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [3] => WP_Post Object ( [ID] => 27578 [post_author] => 71 [post_date] => 2022-03-31 11:10:21 [post_date_gmt] => 2022-03-31 16:10:21 [post_content] =>On March 31, 2022, Florindo Gallicchio was featured in the BetaNews article, World Backup Day Highlights the Importance of Keeping Your Data Safe. Preview the article below, or read the full article online.
+ + +
Today is World Backup Day, which is a good opportunity to remind you that you only have a couple of days left to get your hands on some free backup software courtesy of our AOMEI giveaway.
It's also an opportunity to look at the continued importance of backups even in the modern world of clouds and SaaS applications. A new report from Crucial highlights the ongoing cost of data breaches which has risen 9.8 percent from 2020 to 2021.
There are also plenty of hints and tips on offer to help you make your backups effective and painless to carry out.
It's important to regularly review your backup strategy says Florindo Gallicchio, managing director and head of strategic solutions at NetSPI, "One way to do this is by ensuring that backups with all of the organization's critical data are routinely, completely, and securely assessed -- as this is a necessary step in recovering from a possible ransomware attack. These backups should be encrypted so that sensitive data is not disclosed and stored in such a way that an organization can recover its data in a timely manner, as this is necessary to minimize disruption to business operations. Additionally, organizations should regularly revisit and test disaster recovery and business continuity plans to validate that ransomware and other threats won't impact the integrity of any backups."
[post_title] => BetaNews: World Backup Day Highlights the Importance of Keeping Your Data Safe [post_excerpt] => On March 31, 2022, Florindo Gallicchio was featured in the BetaNews article, World Backup Day Highlights the Importance of Keeping Your Data Safe. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => betanews-world-backup-day-highlights-keeping-your-data-safe [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:46 [post_modified_gmt] => 2023-01-23 21:10:46 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27578 [menu_order] => 290 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [4] => WP_Post Object ( [ID] => 27579 [post_author] => 71 [post_date] => 2022-03-31 11:05:59 [post_date_gmt] => 2022-03-31 16:05:59 [post_content] =>On March 31, 2022, Florindo Gallicchio was featured in the Infosecurity article, #WorldBackupDay: 5 Backup Tips to Retain Critical Data Following a Ransomware Attack. Preview the article below, or read the full article online.
+ + +
The phrase “data is the new oil” offers a dramatic yet apt description of the importance of information flows to modern businesses in an increasingly digitized world. Sadly, cyber-criminals are highly aware of this fact, leading to surging cases of data breaches in the past few years.
This is why the annual World Backup Day campaign on March 31 is taking on increasing relevance, sending a timely reminder of the need for backups and best practices surrounding implementation. ExtraHop’s Costlow added: “This World Backup Day should be a call for all organizations to examine how their backup and recovery plan weaves into their overall security strategy to ensure they are protected in the event of a ransomware attack.”
Another important approach is to encrypt data stored in backups. Florindo Gallicchio, managing director, head of strategic solutions at NetSPI, elucidated this approach: “These backups should be encrypted so that sensitive data is not disclosed and stored in such a way that an organization can recover its data in a timely manner, as this is necessary to minimize disruption to business operations. Additionally, organizations should regularly revisit and test disaster recovery and business continuity plans to validate that ransomware and other threats won’t impact the integrity of any backups.”
[post_title] => Infosecurity Magazine: #WorldBackupDay: 5 Backup Tips to Retain Critical Data Following a Ransomware Attack [post_excerpt] => On March 31, 2022, Florindo Gallicchio was featured in the Info Security article, #WorldBackupDay: 5 Backup Tips to Retain Critical Data Following a Ransomware Attack. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => infosecurity-magazine-worldbackupday-5-backup-tips-to-retain-critical-data-following-a-ransomware-attack [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:46 [post_modified_gmt] => 2023-01-23 21:10:46 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27579 [menu_order] => 291 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [5] => WP_Post Object ( [ID] => 27239 [post_author] => 91 [post_date] => 2022-01-25 12:09:02 [post_date_gmt] => 2022-01-25 18:09:02 [post_content] =>On January 25, 2022, Travis Hoyt, Florindo Gallicchio, Charles Horton, and Nabil Hannan were featured in TechRound's 2022 Cybersecurity Predictions round up. Preview the article below, or read the full article online here.
- Explore industry expert predictions on what’s in store for cybersecurity in 2022.
- Cyber-attacks have remained a key concern throughout the COVID-19 pandemic. With 2021 now over, what does the new year have in store for cybersecurity?
- We’ve collected predictions from industry experts, including HelpSystems’s Joe Vest, Gemserv’s Andy Green and more.
With many businesses continuing to work from home where possible and settling into a more hybrid style of work, cybersecurity has been a key concern across a range of industries.
Here, we’ve collected opinions from industry experts on what they predict 2022 has in store for cybersecurity.
Travis Hoyt, CTO at NetSPI
Attack surface management: “As organisations continue to become more reliant on SaaS technologies to enable digital transformation efforts, the security perimeter has expanded. Organisations now face a new source of cybersecurity risk as cybercriminals look to exploit misconfigurations or vulnerabilities in these SaaS technologies to wage costly attacks. In 2022, we can expect that organisations will become more focused on SaaS posture management and ensuring that their SaaS footprint is not left open as a vector for cyberattacks. This trend will be further accelerated by the insistence of insurance providers that organisations have a detailed understanding of their SaaS deployments and configurations, or face higher premiums or even a refusal of insurance altogether.”
Next generation architectures open new doors for security teams: “Interest in distributed ledger technology, or blockchain, are beginning to evolve beyond the cryptocurrency space. In 2022, we’ll begin to see the conversation shift from bitcoin to discuss the power blockchain can have within the security industry. Companies have already started using this next generation architecture, to better communicate in a secure environment within their organisations and among peers and partners. And I expect we’ll continue to see this strategy unfold as the industry grows.”
CFOs will make or break ransomware mitigation: “For too long, companies have taken a reactionary approach to ransomware attacks – opting to pay, or not pay, after the damage has already been caused. I expect to see CFOs prioritising conversations surrounding ransomware and cyber insurance within 2022 planning and budgetary meetings to develop a playbook that overalls all potential ransomware situations and a corresponding strategy to mitigate both damage and corporate spend. If they don’t lead with proactivity and continue to take a laggard approach to ransomware and cyber insurance, they are leaving their companies at risk for both a serious attack and lost corporate funds.”
Florindo Gallicchio, Managing Director and Head of Strategic Solutions at NetSPI
Cybersecurity budgets will rebound significantly from lower spend levels during the pandemic: “As we look to 2022, cybersecurity budgets will rebound significantly after a stark decrease in spending spurred by the pandemic. Ironically, while COVID-19 drove budget cuts initially, it also accelerated digital transformation efforts across industries – including automation and work-from-home infrastructure, which have both opened companies up to new security risks, leading to higher cybersecurity budget allocation in the new year. Decisions are being made in Fortune 500+ companies with CFOs on the ground, as these risk-focused enterprises understand the need for larger budgets, as well as thorough budgeted risk and compliance strategies. Smaller corporations that do not currently operate under this mindset should follow the lead of larger industry leaders to stay ahead of potential threats that emerge throughout the year.”
Charles Horton, Chief Operations Officer at NetSPI
Company culture could solve the cybersecurity hiring crisis: “It’s no secret that cybersecurity, like many industries, is facing a hiring crisis. The Great Resignation we’re seeing across the country has underscored a growing trend spurred by the COVID-19 pandemic: employees will leave their company if it cannot effectively meet their needs or fit into their lifestyle. From a retention perspective, I expect to see department heads fostering a culture that’s built on principles like performance, accountability, caring, communication, and collaboration. Once this team-based viewpoint is established, employees will take greater pride in their work, producing positive results for their teams, the company and themselves – ultimately driving positive retention rates across the organisation.”
Nabil Hannan, Managing Director at NetSPI
2022 is the year for API security: “In 2022, we will see organisations turn their attention to API security risks, deploying security solutions and conducting internal audits aimed at understanding and reducing the level of risk their current API configurations and deployments create. Over the past few years, APIs have become the cornerstone of modern software development. Organisations often leverage hundreds, and even thousands, of APIs, and ensuring they are properly configured and secured is a significant and growing challenge. Compounding this issue, cyberattackers have increasingly turned to APIs as their preferred attack vector when seeking to breach an organisation, looking for vulnerable connection points within API deployments where they can gain access to an application or network. For these reasons, securing APIs will be a top priority throughout 2022.”
The Skills Shortage Will Continue Until Hiring Practices Change: “In 2022 the cybersecurity skills gap will persist, but organisations that take a realistic approach to cybersecurity hiring and make a commitment to building cybersecurity talent from the ground up will find the most success in addressing it. The focus in closing the skills gap often relies on educating a new generation of cybersecurity professionals through universities and trade programs, and generally encouraging more interest in young professionals joining the field. In reality, though, these programs will only have limited success. The real culprit behind the skills gap is that organisations often maintain unrealistic hiring practices, with cybersecurity degrees and certification holders often finding untenable job requirements such as 3+ years of experience for an entry level job.”
[post_title] => TechRound: Cybersecurity Predictions for 2022 [post_excerpt] => On January 25, 2022, Travis Hoyt, Florindo Gallicchio, Charles Horton, and Nabil Hannan were featured in TechRound's 2022 Cybersecurity Predictions round up. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => techround-cybersecurity-predictions-for-2022 [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:56 [post_modified_gmt] => 2023-01-23 21:10:56 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27239 [menu_order] => 315 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [6] => WP_Post Object ( [ID] => 26804 [post_author] => 71 [post_date] => 2021-12-02 09:15:00 [post_date_gmt] => 2021-12-02 15:15:00 [post_content] =>On December 2, 2021, NetSPI Managing Director Florindo Gallicchio was featured in an article written by David Marshall for VMBlog.com. Read the full article below or online here.
Wondering where cybersecurity is headed as we enter 2022? Read these predictions from 15 security industry experts as they weigh in and offer up their thoughts on the coming year.
++
Kevin Breen, Director of Cyber Threat Research, Immersive Labs
"We've seen an unfortunate increase in ransomware attacks, data leaks, and the sophistication of overall attack methods in the past year. While government-issued mandates have driven a positive increase in information sharing and disclosing rich technical details shortly after vulnerabilities are identified, we are still lacking critical workforce-wide cyber education.
In 2022 there's a lot more we can do to educate the entire workforce on how they can best identify and be prepared for cyber risks - and empower them to be defensive assets to their organizations. This now lies beyond security teams; it's everyone's responsibility and remit, from legal to sales to technical teams. Organizations need to ensure there is a fundamental understanding of security and cyber crisis preparedness workforce-wide, and I expect we'll see businesses make more deliberate efforts and investments to address this gap.
Unfortunately, ransomware is likely not going anywhere in 2022, but we will see attackers evolve their strategies in light of heavy crackdowns and supply chain insecurities. The attack surface will likely reduce as larger groups dissolve, and in turn we'll see affiliates move between RaaS operators as they rise and fall like REvil and BlackMatter. The attackers will always have the first-move advantage, but that's why it's crucial that we exercise the wider organization's cyber crisis response to ensure everyone is prepared when the worst case scenario strikes."
+++
James Christiansen, VP and CSO Cloud Strategy, Netskope
"In 2021 we've seen a rise of the "Great Resignation" and the utilization of gig workers. Specifically, with gig workers, the rapid churn of short-term projects and the widespread set of skills in demand means that background checks may be overlooked and the security of their own computers isn't up to corporate standards. At the same time, in 2021 Netskope Threat Labs found that departing employees upload 3X more data to personal apps in their final month of employment. Taken together, both of these developments point to a need for corporations to rethink their insider threat strategy."
Ray Canzanese, Director, Netskope Threat Labs
"By the end of 2022 malicious Office documents will account for more than 50% of all malware downloads as attackers continue to find new ways to abuse the file format and evade detection. At the beginning of 2020, Office documents accounted for only 20% of all malware downloads and have increased to 40% in 2021. This trend will continue due to the pervasive nature of Office documents in the enterprise and the many different ways they can be abused, making them an ideal malware delivery vector."
+++
Theresa Lanowitz, Head of Cybersecurity Evangelism, AT&T Business
Further acceleration to 5G networks
"While 5G adoption accelerated in 2021, in 2022, we will see 5G go from a new technology to a business enabler. While the impact of 5G on new ecosystems, devices, applications, and use cases ranging from automatic mobile device charging to streaming, 5G will also benefit from the adoption of edge computing due to the convenience it brings. We're moving away from the traditional infosecurity approach to securing edge computing. With this shift to the edge, we will see more data from more devices, which will lead to the need for stronger data security.
Ransomware will be the most feared adversary
The year 2021 was the year the adversary refined their business model. With the shift to hybrid work, we have witnessed an increase in security vulnerabilities leading to unique attacks on networks and applications. In 2022, ransomware will continue to be a significant threat. Ransomware attacks are more understood and more real as a result of the attacks executed in 2021. Ransomware gangs have refined their business models through the use of Ransomware-as-a-Service and are more aggressive in negotiations by doubling down with DDoS attacks. The further convergence of IT and OT may cause more security issues and lead to a rise in ransomware attacks if proper cybersecurity hygiene isn't followed.
While many employees are bringing their cyber skills and learnings from the workplace into their home environment, in 2022, we will see more cyber hygiene education. This awareness and education will help instill good habits and generate further awareness of what people should and shouldn't click on, download, or explore."
Bindu Sundareason, Director at AT&T Cybersecurity
Zero Trust will be the security model of choice
"Traditional cybersecurity practices focus on a ‘castle and moat' model, where security protocols concentrate on keeping threats out. This approach assumes that any user with the right credentials to access a network has done so legitimately and can be trusted to move freely through the system. However, as more organizations move their data and operations to the cloud more rapidly, the concept of a security perimeter as we know it is becoming obsolete. As a result, organizations will continue to focus on adopting a Zero Trust security model which restricts network access to only those individuals who need it.
Securing data with third-party vendors in mind will be critical
Attacks via third parties are increasing every year as reliance on third-party vendors continues to grow. Organizations must prioritize the assessment of top-tier vendors, evaluating their network access, security procedures, and interactions with the business. Unfortunately, there are many operational obstacles that will make this assessment difficult, including a lack of resources, increased organizational costs, and insufficient processes. The lack of up-to-date risk visibility on current third-party ecosystems will lead to loss of productivity, monetary damages, and damage to brand reputation."
+++
Jason Rebholz, CISO, Corvus Insurance
Ransomware + Impacts on Cyber Insurance
"Ransomware is the defining force in cyber risk in 2021 and will likely continue to be in 2022. While ransomware has gained traction over the years, it jumped to the forefront of the news this year with high profile attacks that had impacts on the day to day lives of millions of people. The increased visibility brought a positive shift in the security posture of businesses looking to avoid being the next news headline. We're starting to see the proactive efforts of shoring up IT resilience and security defenses pay off, and my hope is that this positive trend will continue. When comparing Q3 2020 to Q3 2021, the ratio of ransoms demanded to ransoms paid is steadily declining, as payments shrank from 44% to 12% respectively, due to improved backup processes and greater preparedness. Decreasing the need to pay a ransom to restore data is the first step in disrupting the cash machine that is ransomware.
Although we cannot say for certain, in 2022 we can likely expect to see threat actors pivot their ransomware strategies. Attackers are nimble - and although they've had a "playbook" over the past couple years, thanks to widespread crackdowns on their current strategies, we expect things to shift. We have already seen the opening moves from threat actors. In a shift from a single group managing the full attack life cycle, specialized groups have formed to gain access into companies who then sell that access to ransomware operators. As threat actors specialize on access into environments, it opens the opportunity for other extortion based attacks such as data theft or account lockouts - all of which don't require the encryption of data. The potential for these shifts will call for a great need in heavier investments in emerging tactics and trends to remove that volatility."
+++
Brian Murphy, CEO and Founder, ReliaQuest
Tackling the skills transfer issue to finally make progress in addressing the gap
"If this past year taught us anything, it's that cyber attacks are only increasing, so it's paramount that organizations have the best talent to prevent and address these breaches when they occur. In 2022, the industry will need to make substantial progress in addressing the cybersecurity skills gap as efforts thus far haven't shown the progress we need to properly address increasing threats. (ISC)2's recent report made it clear - there aren't yet enough cyber pros to build secure tech, implement protections or respond to breaches.
While it's great to see the efforts of the private sector prioritize training in cyber skills, and making cyber awareness training accessible to everyone, I hope, and expect, the industry will direct more of its efforts into tackling the broader skills transfer issue. There are plenty of people ready to raise their hand and help with this ongoing problem, but we need to better equip them with the right skills. I hope to see more companies in the new year investing in meaningful skills initiatives, like Microsoft's work with community colleges and ReliaQuest's work with 3DE high schoolers. These education-based efforts aim to encourage the next generation of the workforce to take interest and gain critical skills to shape the future cyber workforce."
Marcus Carey, Enterprise Architect, ReliaQuest
"2022 will be the year cryptocurrencies go mainstream. Already, big players are making moves into this space and NFTs are becoming increasingly popular among celebrities. We've unfortunately seen businesses use cryptocurrencies to make ransomware payments, but in 2022, they will become a more widely utilized method for companies to do things like compensate employees and take payments from customers. This will open up a whole new paradigm for security teams and CISOs, as there will be an increased emphasis on the security aspects of these new technologies.
CISOs and security teams will need to have an understanding of all of the facets of cryptocurrencies, including different blockchains like Ethereum and Solana, smart contracts, and hot and cold storage. Just as cybersecurity teams audit code now, they will have to audit smart contracts - which are automated agreements written in code and incorporated into the blockchain. Cybersecurity teams and IT teams will need to manage hot wallets, which are used for transactions, and cold wallets, which are used for long term storage. There are various aspects and implications that CISOs and their teams will need to understand in order to keep money secure. Cryptocurrency is the "Wild West" of the digital world today. Companies need to prepare now for the impact it will have in the year ahead."
+++
Tobi Knaup, CEO, D2iQ
Putting forth a DevSecOps approach from the start
"The pandemic pushed us further into the cloud, which has made us more reliant on microservices and containers. However, the rapid proliferation of microservices has outpaced the cyber security capabilities of most organizations. In an effort to improve cloud native cyber security practices, organizations will begin to embed security from the very beginning of the development process, ensuring microservice remain secure wherever they are deployed. As organizations become more agile, putting forth a DevSecOps approach from the start ensures microservices are adequately secured."
+++
James Condon, Director of Research, Lacework
"Linux and cloud infrastructure are emerging targets of malware and ransomware attacks: Threat actors are looking for the path of least resistance - the easiest way to break through with the greatest return. The traditional methods of enterprise network intrusions to obtain data (or other valuable company information) is still resulting in success. However, cloud infrastructure is heavily Linux-based (80+ percent) and with cloud adoption increasing, especially as a result of the pandemic, threat actors are turning their focus to cloud-based targets. The Lacework team found that PYSA Ransomware Gang added Linux Support, which indicates that ransomware gangs and other attackers may be pivoting to cloud strategies. Furthermore, continued identification of new linux malware families are growing increasingly complex, adding to the mounting concerns."
Chris Hall, Cloud Security Researcher, Lacework
"Crimeware actors will continue leveraging initial access brokerage and crypto jacker techniques: Currently, we are seeing a lot of cloud environments being compromised by crypto jacker techniques. These aren't generating a ton of noise within the larger cyber community currently; however this is an area that attackers will continue to leverage and start to carry out on a larger scale in the coming year."
Eric O'Neill, National Security Strategist, VMware
If 2021 was the year of the Zero Day, 2022 will be the year of Zero Trust:
"In 2021, defenders caught the highest number of Zero Days ever recorded. We saw a massive proliferation of hacking tools, vulnerabilities, and attack capabilities on the Dark Web. As a response, 2022 will be the year of Zero Trust where organizations "verify everything" vs. trusting it's safe. We've seen the Biden administration mandate a Zero Trust approach for federal agencies, and this will influence other industries to adopt a similar mindset with the assumption that they will eventually be breached. A Zero Trust approach will be a key element to fending off attacks in 2022."
Karen Worstell, Senior Cybersecurity Strategist, VMware
Accelerated delivery of the benefits of 5G infrastructure will highlight IoT security needs.
"The pandemic made it abundantly clear how important 5G infrastructure is for rural areas in the U.S. The rollout of 5G will enable better access to healthcare, educational innovations, and public services. The Biden administration's infrastructure bill, which includes provisions for broadband delivery and access, provides the industry with another nudge in the right direction to roll it out. As 5G service delivery expands, there will be a growing demand for IoT security and engineering to ensure that network complexity does not become yet another security liability. We must also focus on securing the far edge much like we handle the data center edge today -- this will put new demands on incident detection and response. Future-ready capabilities like EDR (endpoint detection and response) will need to evolve in order to keep an expanding service level and constituency safe."
+++
Florindo Gallicchio, Managing Director, Head of Strategic Solutions, NetSPI
Cybersecurity budgets will rebound significantly from lower spend levels during the pandemic
"As we look to 2022, cybersecurity budgets will rebound significantly after a stark decrease in spending spurred by the pandemic. Ironically, while COVID-19 drove budget cuts initially, it also accelerated digital transformation efforts across industries - including automation and work-from-home infrastructure, which have both opened companies up to new security risks, leading to higher cybersecurity budget allocation in the new year. Decisions are being made in Fortune 500+ companies with CFOs on the ground, as these risk-focused enterprises understand the need for larger budgets, as well as thorough budgeted risk and compliance strategies. Smaller corporations that do not currently operate under this mindset should follow the lead of larger industry leaders to stay ahead of potential threats that emerge throughout the year."
+++
Stephen Cavey, Co-founder of Ground Labs
Awareness and gamification will lead the future of data security plans
"As employees went remote the amount of potential data exposure greatly increased. This increased risk highlighted the strongest security weakness that criminals were actively targeting the organization's people.
Traditional forms of mitigation of this risk in the form of physical training through classroom delivery have not been as effective as required to reduce the instances of data breaches caused by employees. In the coming year, CISOs and IT leaders will incorporate all parts of an organization into creating a well-rounded cybersecurity strategy that places employees at the center in order to mitigate risk. We're going to see more next-generation job roles such as "head of remote." These new roles will be tasked with improving the remote experience which can open up a strong opportunity to weave a culture of data security and good data hygiene and awareness practices that are driven through educating on the unique risks of working remotely in isolation for prolonged periods. Adding elements of gamification is also an excellent way to remind, engage and motivate employees to practice better cybersecurity habits."
[post_title] => VMBlog.com: 15 Experts Share 2022 Security Predictions [post_excerpt] => On December 2, 2021, NetSPI Managing Director Florindo Gallicchio was featured in an article written by David Marshall for VMBlog.com. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => vmblog-15-experts-share-2022-security-predictions [to_ping] => [pinged] => [post_modified] => 2023-06-22 18:32:32 [post_modified_gmt] => 2023-06-22 23:32:32 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26804 [menu_order] => 338 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [7] => WP_Post Object ( [ID] => 26665 [post_author] => 53 [post_date] => 2021-11-12 12:30:08 [post_date_gmt] => 2021-11-12 18:30:08 [post_content] =>What’s next for enterprise security professionals? No one can know for certain, but NetSPI’s expert bench of security pros – pulling from their decades of cybersecurity leadership and daily conversations with some of the world’s most prominent organizations – have a few ideas as to where the industry is headed.
Watch our 2022 cybersecurity predictions webinar, where our panel will tackle some of the most debated topics of the past 365 days and predict how each will evolve in the new year and beyond. Topics include:
- The cybersecurity hiring crisis
- Application security program maturity
- Attack surface management
- The evolution of ransomware
- Cybersecurity budget allocation
- And next generation architectures (see: blockchain)
[wonderplugin_video iframe="https://youtu.be/rLcwnJAO5Qo" lightbox=0 lightboxsize=1 lightboxwidth=1200 lightboxheight=674.999999999999916 autoopen=0 autoopendelay=0 autoclose=0 lightboxtitle="" lightboxgroup="" lightboxshownavigation=0 showimage="" lightboxoptions="" videowidth=1200 videoheight=674.999999999999916 keepaspectratio=1 autoplay=0 loop=0 videocss="position:relative;display:block;background-color:#000;overflow:hidden;max-width:100%;margin:0 auto;" playbutton="https://www.netspi.com/wp-content/plugins/wonderplugin-video-embed/engine/playvideo-64-64-0.png"]
[post_title] => 2022 Cybersecurity Predictions:What to Expect in the New Year [post_excerpt] => [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => 2022-cybersecurity-predictions-what-to-expect-in-the-new-year [to_ping] => [pinged] => [post_modified] => 2023-06-22 20:39:36 [post_modified_gmt] => 2023-06-23 01:39:36 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?post_type=webinars&p=26665 [menu_order] => 51 [post_type] => webinars [post_mime_type] => [comment_count] => 0 [filter] => raw ) [8] => WP_Post Object ( [ID] => 26220 [post_author] => 71 [post_date] => 2021-08-17 15:48:00 [post_date_gmt] => 2021-08-17 20:48:00 [post_content] =>
NetSPI managing director Florindo Gallicchio wrote an article that was featured in the August 2021 issue of Cyber Defense Magazine:
There’s no doubt about it: attack surfaces grow and evolve around the clock. With network configurations, new tools and applications, and third-party integrations coming online constantly, an atmosphere is being created that opens the possibility of unidentified security gaps. The fact is that cyberattacks can affect your business and are, unfortunately, more prevalent than natural disasters and extreme weather events. And we know from our own NetSPI research that nearly 70 percent of security leaders are concerned about network vulnerabilities after implementing new security tools.
Prevention is key to a mature cybersecurity program. In fact, according to a recent Ponemon Institute study, when cybersecurity attacks are prevented, organizations can save resources, costs, damages, time, and reputation. Yet, companies still may think they are protected by buying the latest cybersecurity technologies or just by working to change team behaviors that pose the most risk (i.e., using stronger passwords, avoiding phishing scams, etc.). While there is a place in a security program for these and other security measures, time and budget constraints create major barriers. Therefore, it is critical that an organization’s vulnerability management program is strongly built on a strategy that is risk-based and business aligned.
Florindo's article can be found on pg. 74 of the August Issue of Cyber Defense Magazine. Download the issue online here: https://cyberdefensemagazine.tradepub.com/free/w_cyba125/.
[post_title] => Cyber Defense Magazine: Align Business Logic with Vulnerability Management to Mature Your Security Program [post_excerpt] => NetSPI managing director Florindo Gallichio wrote an article that was featured in the August 2021 issue of Cyber Defense Magazine. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => cyber-defense-magazine-align-business-logic-with-vulnerability-management-to-mature-your-security-program [to_ping] => [pinged] => [post_modified] => 2022-12-16 10:51:54 [post_modified_gmt] => 2022-12-16 16:51:54 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=26220 [menu_order] => 372 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [9] => WP_Post Object ( [ID] => 24940 [post_author] => 71 [post_date] => 2021-04-20 07:00:00 [post_date_gmt] => 2021-04-20 07:00:00 [post_content] =>Unless you’re Pfizer, Moderna, or Johnson & Johnson, you may not consider your biotech or pharmaceutical organization a lucrative target for cyberattacks as COVID-19 vaccine production and distribution ramps up. However, it is important to note that the larger, well known organizations in the vaccine pipeline are well funded and staffed and have the ability to prioritize cyber security - and sophisticated adversaries know this well. In turn, this makes smaller organizations involved in vaccine development, distribution, and administration a prime target.
Notably, we expect to see increased threat activity among the small to midsized biotech organizations that are collecting patient data or have access to vaccine research and development (R&D) information. Whether or not your organization is working directly or indirectly with the COVID-19 vaccine, there’s a lot to learn from the security concerns and activity to date. In this article, we explore the motivations for vaccine cyber security threats, reasons why biotech organizations should prioritize security, and pragmatic steps organizations can take now to proactively prepare for imminent attacks.
The vaccine security threat landscape
Cybercrime is known to increase amid chaos or crisis, when people are the most vulnerable. And the COVID-19 pandemic is certainly no exception. Large-scale data breaches increased 273 percent in the first quarter of 2020 versus 2019. The U.N. Security Council reported a massive 350 percent increase in phishing websites in the first quarter of 2020, many targeting hospitals and healthcare systems. And now, capitalizing on the vaccine rollout, the number of phishing attacks targeting the healthcare industry increased by 189 percent from December 2020 to February 2021.
There are three realistic motivations for adversaries as it pertains to vaccine security: 1) the theft of personal health data, 2) to compromise business systems, and 3) to access intellectual capital. To gain a better understanding of the threat landscape, let’s take a deeper look at each scenario.
To steal sensitive health data:
Protected health information (PHI) includes identifiable information in a person’s health data records, such as health details, date of birth, Social Security number, fingerprints, and even financial information. Given biotech firms are working with patients to develop and test vaccines in a medical setting, they are also responsible for managing and securing PHI. PHI can be used by adversaries for identity theft, medical fraud, access computer networks, and to learn more about the capabilities and processes of an organization for future large-scale attacks.
To access intellectual capital:
An approved vaccine is a very valuable source of intellectual capital. COVID-19 vaccine production data is extremely valuable today as the global race to administer vaccines continues. Biotech firms house a lot of intellectual capital, from R&D information to vaccine formulas to testing and drug trial data, making them a lucrative target. According to research from F5, “threat actors in this case are advanced cyber attackers, either working for or hired by nation states. This makes them the most capable and well-resourced threat that organizations could face.”
In early 2021, the European Medicines Agency (EMA), a regulatory agency tasked with vaccine assessments and approvals for the EU, found that hackers stole COVID-19 vaccine data belonging to Pfizer and BioNTech. Further, leveraging intellectual capital for misinformation is another key motivator. The data in the EMA breach had been leaked online only after manipulating the exfiltrated data to undermine public trust in the vaccine.
To compromise business systems:
Whether it’s a ransomware attack on a healthcare organization or an attack on the vaccine appointment scheduling software, adversaries could also aim to interfere with business operations in the vaccine pipeline. Biotech firms have a critical role to play in ensuring the security of its partners.
Third-party security is a major challenge for healthcare organizations - and one that is very relevant to vaccine rollouts. A 2020 survey of healthcare CISOs, CIOs, and other C-suite leaders discovered that four out of five organizations experienced a cybersecurity breach precipitated by a third-party vendor over the past year.
Right now, there are many third-parties working hand-in-hand with biotech firms to coordinate the rollout of the COVID-19 vaccine, from logistics and transportation to the on-site distribution locations. How can we ensure each organization involved follows the right security protocols? A recent example of a third-party breach attempt is the targeted attacks on cold storage company Americold and global firm Miltenyi Biotec. The companies were targeted with cyberattacks in an apparent attempt to disrupt the vaccine supply chain.
Making the case for cyber security in biotech, pharma, and other healthcare industries
We recently attended a webinar on medical device security presented by Kevin McDonald, a cyber security advisor for Mayo Clinic. At the end of the discussion Kevin highlighted the core drivers for security investments in healthcare: patient care, revenue loss, and public perception.
Above all, continuation of patient care is the end goal of all security activities in healthcare organizations. Security is put in place to not hinder the quality of care, but to ensure it can continue without interruption from adversaries.
Revenue loss and public perception are fairly self-explanatory for most healthcare organization, but there are some nuances regarding the biotech industry. The goal of many biotech firms is to raise funds and eventually get purchased, and according to Silicon Valley Bank, in 2020 acquisitions of biotech startups increased. If your organization experiences a security breach, your chances and/or valuation may decrease given the increased risk and the reputational damage created.
4 security activities to implement to proactively protect your assets
Once you’re aware of the most likely risks, it’s important to understand the steps you can take to proactively protect your organization and its sensitive data. To get started, here are four activities we recommend:
- Red teaming: Red team operations allow you to test your security controls and processes for a specific target or goal, such as vaccine formulas or patient social security numbers. Hire a red team or equip your internal red team with the right tools to simulate the stealthy approach a real adversary would take.
- Detective control testing: Correctly configured detective controls are vital to network security. Test your detective controls against the tactics, techniques, and procedures (TTPs) used by real-world attackers to ensure your layers of
defense in depth are working as intended. - Internal network penetration tests: Given the increase in phishing attempts and the vulnerability of humans in a crisis scenario, it’s likely that sophisticated adversaries will inevitably find a way to access your network. This is where internal network penetration tests prove necessary. An internal network
penetration test evaluates a network for security vulnerabilities and provides actionable recommendations for remediation. It allows an organization to discover where your internal network gaps are before an adversary does. - Continuous testing: Often it is the case that an organization’s attack surfaces are only evaluated via a penetration test on an annual basis. Implementing more
frequent, lighter touch tests throughout the year, or when a new technology or partner is added to your infrastructure, helps teams stay up to date on any recently introduced vulnerabilities.

In the first installment of my vulnerability management blog series, I discuss the pitfalls of not having a vulnerability testing and tracking strategy and the serious consequences of failing to recognize what is meaningful to the business. In part two of the series, I will expand on the idea of recognizing what is meaningful to the business and discuss the importance of business context in vulnerability management.
It sounds nebulous, and for good reason. From my observations over the years, I’ve heard claims that the best approach to cyber security is either 1) purchasing more technology to keep ahead of the latest vulnerabilities or 2) changing behaviors that pose the most risk, such as clicking on unknown links or using stronger passwords. While there is a place in a security program for these and other security measures, time and budget constraints create major barriers. Instead of asking, “which new technologies do we need to add to our security stack?” or “why isn’t my organization getting a perfect score on our phishing assessments?”, the most important question that needs to be asked is, “So what?”
“So what?” is arguably one of the most elemental and important criteria in any cybersecurity situation, from policy to technical security controls. The question forms the basis of nearly every security decision and requires alignment to core business objectives to be determined and applied before a direction is taken. Recognizing how each security decision impacts your business is vital. To understand the importance of “So what?” we must first understand its place in your cyber security strategy.
Strategy is another concept that can mean different things to different people, in part because there is not a standard approach to cyber security program development. Each business has different security needs. As security leaders, we address the threats that pose imminent and perceived harm to the environment, and those that get noticed most, get attention first. And understandably so, given the ever-advancing threats companies face. Often is the case, however, that what is considered harmful to the environment is not always rooted in what is most important, or what poses the most risk to a business. That is where a business-aligned vulnerability management program comes into play.
How to Achieve a Business-Aligned Vulnerability Management Program
A business-aligned vulnerability management program takes into consideration the vulnerabilities that would have the most significant, negative impact on the business, the most relevant threats that could exploit those vulnerabilities, how to remediate, as well as the controls needed to counter those threats. Such a strategy is built on a framework that enables, implements, and maintains the program and informs all security initiatives, controls, and processes.
Once a business-aligned vulnerability management program is in place, we can ask, “So what?” when considering a potential risk, a discovered vulnerability, a detected event, a proposed initiative, or virtually any other consideration affecting security posture. Let’s look at a few hypothetical vulnerability findings:
| Vulnerability Finding | So What? | Remediation Recommendations |
| Poor Administrator Account Password | Attacker can gain access to and steal data. Poses enterprise risks to information, business operations, regulatory compliance, and business reputation. Regulatory non-compliance leading to financial sanctions. Legal action by affected customers leading to financial reparations. | Change the admin password. Strengthen the admin password. Use multifactor authentication. Use “zero trust” access model. Purchase technology to enhance identity and access controls. Conduct vulnerability testing more often. |
| Vulnerable Version - PHP | Successful exploitation of available vulnerabilities may allow a remote unauthenticated attacker to execute arbitrary commands directly or indirectly on the affected systems. As a result, the confidentiality, integrity, and availability of the affected systems and associated data may be compromised. | Disable or uninstall PHP if it is not required for a defined business purpose. If PHP is required, upgrade to the latest stable version of the software or apply vendor supplied patches. If no fix is available, contact the vendor for solutions and consider isolating the affected service via host based and network firewalls. |
| SQL Injection | SQL injection may allow an attacker to extract, modify, add, or delete information from database servers, causing the confidentiality and integrity of the information stored in the database to be compromised.Depending on the SQL implementation, the attacker may also be able to execute system commands on the affected host. In some circumstances, this provides the means to take control of the server hosting the database, leading to the complete compromise of the confidentiality, integrity, and availability of the affected host. | Employ a layered approach to security that includes using parameterized queries when accepting user input. Strictly define the data type that the application will accept. Also, disable detailed error messages that could give an attacker information about the database. Additionally, following the principle of least privilege when assigning permissions for the service account and database user helps limit the impact of a successful SQL injection attack. |
Eliminate the “So what?” column and it becomes difficult to choose which vulnerability to prioritize. Taking these examples further, we can use this same strategy to determine what the ramifications are for conducting certain types of vulnerability scans, from the resources needed to conduct the test to the large number of vulnerability instances that will require analysis. For example, if you target scans to detect just the vulnerabilities that pose a significant answer to “So what?” or in other words, has a major impact on the business, you can focus your resources – people, time, money – on the meaningful measures to manage risk to the business.
This is all ties back to risk-based security. By now, the security industry understands why risk-based security strategies are more effective than compliance-based strategies, but are often challenged as to how to make the shift. To mature your security program and achieve a risk-based strategy, it is essential to align business logic with vulnerability management and prioritize the vulnerabilities that pose the highest risk specific to your business.

 [post_title] => SC Magazine: From diversity efforts to pandemic recovery, workforce issues will evolve in 2021
[post_excerpt] => On January 4, 2021, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => sc-magazine-from-diversity-efforts-to-pandemic-recovery-workforce-issues-will-evolve-in-2021
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-14 05:28:37
[post_modified_gmt] => 2021-04-14 05:28:37
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=21092
[menu_order] => 439
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[12] => WP_Post Object
(
[ID] => 21086
[post_author] => 71
[post_date] => 2020-12-30 07:00:52
[post_date_gmt] => 2020-12-30 07:00:52
[post_content] => On December 30, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine:
As companies of all sizes prepare for more challenges tied to the pandemic, as well as an expected transition to a permanent hybrid workforce, security plans will need to adapt. So what kind of strategic shifts might we see in 2021? More sophisticated phishing campaigns will probably mean enhanced email security. Digital identities may grow more appealing. And a surge in M&A could introduce new security considerations.
At least, that’s some of what we heard from the experts. As part of our year in review, which looked at critical events during the last year and how they might influence 2021, SC Media collected predictions across a range of categories from cybersecurity experts. Here, the cyber community reads the tea leaves on evolving strategies of the enterprise.
Security budgets are not necessarily going to increase but will be reprioritized, says Florindo Gallicchio, managing director at NetSPI:
“More dollars will be specifically allocated to cloud security budgets due to the prolonged and, in many cases permanent, remote work opportunities – in other words, a distributed workforce. One exception to stagnant budgets is regulatory drivers. Certain states (e.g. California) and industries (e.g. health care) may need to increase budgets to comply with new or changing regulatory expectations.”
Read the full article here: https://www.scmagazine.com/home/year-in-review/2021-strategy-predictions-shifts-in-business-models-shifts-in-security-priorities/
[post_title] => SC Magazine: From diversity efforts to pandemic recovery, workforce issues will evolve in 2021
[post_excerpt] => On January 4, 2021, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => sc-magazine-from-diversity-efforts-to-pandemic-recovery-workforce-issues-will-evolve-in-2021
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-14 05:28:37
[post_modified_gmt] => 2021-04-14 05:28:37
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=21092
[menu_order] => 439
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[12] => WP_Post Object
(
[ID] => 21086
[post_author] => 71
[post_date] => 2020-12-30 07:00:52
[post_date_gmt] => 2020-12-30 07:00:52
[post_content] => On December 30, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine:
As companies of all sizes prepare for more challenges tied to the pandemic, as well as an expected transition to a permanent hybrid workforce, security plans will need to adapt. So what kind of strategic shifts might we see in 2021? More sophisticated phishing campaigns will probably mean enhanced email security. Digital identities may grow more appealing. And a surge in M&A could introduce new security considerations.
At least, that’s some of what we heard from the experts. As part of our year in review, which looked at critical events during the last year and how they might influence 2021, SC Media collected predictions across a range of categories from cybersecurity experts. Here, the cyber community reads the tea leaves on evolving strategies of the enterprise.
Security budgets are not necessarily going to increase but will be reprioritized, says Florindo Gallicchio, managing director at NetSPI:
“More dollars will be specifically allocated to cloud security budgets due to the prolonged and, in many cases permanent, remote work opportunities – in other words, a distributed workforce. One exception to stagnant budgets is regulatory drivers. Certain states (e.g. California) and industries (e.g. health care) may need to increase budgets to comply with new or changing regulatory expectations.”
Read the full article here: https://www.scmagazine.com/home/year-in-review/2021-strategy-predictions-shifts-in-business-models-shifts-in-security-priorities/
 [post_title] => SC Magazine: 2021 strategy predictions: Shifts in business models, shifts in security priorities
[post_excerpt] => On December 30, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => sc-magazine-2021-strategy-predictions-shifts-in-business-models-shifts-in-security-priorities
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-14 05:29:18
[post_modified_gmt] => 2021-04-14 05:29:18
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=21086
[menu_order] => 440
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[13] => WP_Post Object
(
[ID] => 20783
[post_author] => 71
[post_date] => 2020-12-28 07:00:07
[post_date_gmt] => 2020-12-28 07:00:07
[post_content] => On December 28, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine:
What might 2021 bring in term of technology?
Community and market experts found consensus on a few areas. First, cloud security will dominate strategies and investments even more that it did during 2020, as organizations big and small go all in on digital transformation. And second, technologies once deemed “on the horizon” – think automation, 5G and even the much hyped artificial intelligence – will officially arrive.
SC Media collected predictions across a range of categories from cybersecurity experts. Here we give you the tech roundup. Check back during the next couple of weeks to see community predictions for the threat landscape, strategic priorities, and privacy policy.
Automation continues to be a priority, but human context will be the key to security program management and success, says Florindo Gallicchio, managing director at NetSPI:
“By now, we all understand the value automation brings to any security tool. Yet, in 2021, the human element will be pushed to the forefront of security innovation, specifically for our intellect and ability to add context to security findings. Contextualizing security findings will be an invaluable tool to boost remediation efforts in the new year, as the number of vulnerabilities remains exponential and context is key to helping us prioritize.”
Read the full article here: https://www.scmagazine.com/home/year-in-review/2021-tech-predictions-the-conceptual-gets-real/
[post_title] => SC Magazine: 2021 strategy predictions: Shifts in business models, shifts in security priorities
[post_excerpt] => On December 30, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => sc-magazine-2021-strategy-predictions-shifts-in-business-models-shifts-in-security-priorities
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-14 05:29:18
[post_modified_gmt] => 2021-04-14 05:29:18
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=21086
[menu_order] => 440
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[13] => WP_Post Object
(
[ID] => 20783
[post_author] => 71
[post_date] => 2020-12-28 07:00:07
[post_date_gmt] => 2020-12-28 07:00:07
[post_content] => On December 28, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine:
What might 2021 bring in term of technology?
Community and market experts found consensus on a few areas. First, cloud security will dominate strategies and investments even more that it did during 2020, as organizations big and small go all in on digital transformation. And second, technologies once deemed “on the horizon” – think automation, 5G and even the much hyped artificial intelligence – will officially arrive.
SC Media collected predictions across a range of categories from cybersecurity experts. Here we give you the tech roundup. Check back during the next couple of weeks to see community predictions for the threat landscape, strategic priorities, and privacy policy.
Automation continues to be a priority, but human context will be the key to security program management and success, says Florindo Gallicchio, managing director at NetSPI:
“By now, we all understand the value automation brings to any security tool. Yet, in 2021, the human element will be pushed to the forefront of security innovation, specifically for our intellect and ability to add context to security findings. Contextualizing security findings will be an invaluable tool to boost remediation efforts in the new year, as the number of vulnerabilities remains exponential and context is key to helping us prioritize.”
Read the full article here: https://www.scmagazine.com/home/year-in-review/2021-tech-predictions-the-conceptual-gets-real/
 [post_title] => SC Magazine: 2021 tech predictions: The conceptual gets real
[post_excerpt] => On December 28, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => sc-magazine-2021-tech-predictions-the-conceptual-gets-real
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-14 05:29:24
[post_modified_gmt] => 2021-04-14 05:29:24
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=20783
[menu_order] => 441
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[14] => WP_Post Object
(
[ID] => 20716
[post_author] => 91
[post_date] => 2020-12-15 09:41:57
[post_date_gmt] => 2020-12-15 09:41:57
[post_content] =>
[post_title] => SC Magazine: 2021 tech predictions: The conceptual gets real
[post_excerpt] => On December 28, NetSPI Managing Director Florindo Gallicchio was featured in SC Magazine.
[post_status] => publish
[comment_status] => closed
[ping_status] => closed
[post_password] =>
[post_name] => sc-magazine-2021-tech-predictions-the-conceptual-gets-real
[to_ping] =>
[pinged] =>
[post_modified] => 2021-04-14 05:29:24
[post_modified_gmt] => 2021-04-14 05:29:24
[post_content_filtered] =>
[post_parent] => 0
[guid] => https://www.netspi.com/?p=20783
[menu_order] => 441
[post_type] => post
[post_mime_type] =>
[comment_count] => 0
[filter] => raw
)
[14] => WP_Post Object
(
[ID] => 20716
[post_author] => 91
[post_date] => 2020-12-15 09:41:57
[post_date_gmt] => 2020-12-15 09:41:57
[post_content] =>
As we write this post, you’ve likely heard about the FireEye and U.S. government agency breaches that occurred over the past week. We know now the breaches have been linked back to a supply chain attack on the SolarWinds Orion Platform, a software platform that manages IT operations and products for over 300,000 organizations, including over 425 of the Fortune 500, all ten of the top U.S. telecommunications companies, all five branches of the U.S. Military, all five of the top U.S. accounting firms, and many, many more.
While FireEye, the U.S. Treasury, and National Telecommunications and Information Administration (NTIA) were the first to report a security breach, the breadth of SolarWinds’ customer base is an indicator that the breaches are seemingly the tip of the iceberg.
For the sake of information sharing, here is an overview of the attacks, immediate steps you can take to identify whether you have fallen victim, and tips for protecting your organization as communicated by FireEye, SolarWinds, and NetSPI. For the full technical deep-dive, we highly recommend the FireEye blog post.
Overview: SolarWinds Orion Manual Supply Chain Attack
On December 13, SolarWinds issued a security advisory alerting to a manual supply chain attack on its Orion Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.
FireEye discovered the attack and suggests it is a state-sponsored global intrusion campaign by a group named UNC2452 - though many industry experts are attributing the attack to APT29, a group of hackers associated with the Russian Foreign Intelligence Service.
- Attack Origin: UNC2452 gained access to victims via trojan-based updates to SolarWinds’ Orion IT monitoring and management software, distributing malware called SUNBURST. Multiple trojanized updates were digitally signed and subsequently deployed via this URL: hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20574 /SolarWinds-Core-v2019.4.5220-Hotfix5.msp. The downloaded file is a standard Windows Installer Patch file, which includes the trojanized SolarWinds.Orion.Core.BusinessLayer.dll component.
- How It Works: The digitally signed SolarWinds.Orion.Core.BusinessLayer.dll file is a component of the Orion Improvement Program (OIP) software framework that contains a backdoor that communicates with third party servers via the HTTP protocol. The malicious DLL gets loaded into the legitimate SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe executables and can run dormant for up to two weeks before beaconing to a subdomain of avsvmcloud[.]com. To avoid possible detection, the C2 traffic between the beaconing server and the victim is made to resemble legitimate SolarWinds communications. This includes HTTP GET, HEAD, POST and PUT requests with JSON payloads in their bodies. The HTTP responses from the C2 server communicating with the victim contain XML data that resembles .NET assembly data used for normal SolarWinds operations. Within the XML, however, is obfuscated command information that is deobfuscated and then executed by the SolarWinds process on the victim’s system.
- Impact/Result: Following the initial compromise and deployment of SUNBURST, a variety of more capable payloads can be deployed to facilitate lateral movement and data theft. Common payloads include TEARDROP and Cobalt Strike BEACON, both of which can be loaded into memory to improve stealth of operations.
Known breaches include:
FireEye: On December 8, FireEye communicated a state-sponsored security breach through which the attackers accessed FireEye’s Red Team assessment tools used to test customers’ security. Following the breach, the company made its list of countermeasures public. FireEye has now confirmed that this attack was a result of the SolarWinds Orion supply chain attack.
U.S. Treasury and the National Telecommunications and Information Administration (NTIA): On December 13, Reuters reported that Russian-associated hackers broke into the U.S. Treasury and Commerce department’s Microsoft 365 software and have been monitoring internal email traffic. Following a National Security Council meeting at the White House over the weekend, the Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive for all federal agencies to power down SolarWinds Orion.
Organizations are frantically working to figure out if they have been a victim of the attack and how to protect themselves. Here are the immediate steps to take, according to SolarWinds, FireEye, and NetSPI’s team of offensive security experts:
- First, determine if SolarWinds Orion is deployed within your environment. If unsure, NetSPI recommends performing a network scan to identify the Orion agent. For example, this can be performed with Nmap by running: nmap --open -sT -p 17778,17790 x.x.x.x/xx, where x.x.x.x is the network address and xx is the subnet mask. If the Orion agent is found, follow SolarWinds’ recommendations.
- SolarWinds recommends customers upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible. It also asks customers with any of the products listed on the security advisory for Orion Platform v2019.4 HF 5 to update to 2019.4 HF 6. Additional suggestions can be found in the security advisory. While upgrading Orion will prevent future backdoored deployments from occurring, it will not remediate the potentially infected deployments that have already taken place via the Orion Platform.
- Additionally, FireEye provides a list of recommendations including its signatures to detect this threat actor and supply chain attack. Specific details on the YARA, Snort, and ClamAV signatures can be found on FireEye’s public GitHub page.
Get in Touch: To connect with NetSPI for support with testing efforts related to the SolarWinds Orion attack, email info@NetSPI.com.
[post_title] => FireEye, SolarWinds, U.S. Treasury: What’s Happening in the Cyber Security World Right Now? [post_excerpt] => As we write this post, you’ve likely heard about the FireEye and U.S. government agency breaches that occurred over the past week [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => fireeye-solarwinds-us-treasury-whats-happening-in-the-cyber-security-world-right-now [to_ping] => [pinged] => [post_modified] => 2021-05-04 17:03:39 [post_modified_gmt] => 2021-05-04 17:03:39 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=20716 [menu_order] => 442 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [15] => WP_Post Object ( [ID] => 32230 [post_author] => 71 [post_date] => 2020-12-05 17:35:00 [post_date_gmt] => 2020-12-05 23:35:00 [post_content] =>2020 is one for the books. We each navigated life amid a pandemic that brought its own trials, tribulations and a few silver linings. Moreover, 2020 tested IT and cybersecurity professionals: Organizations quickly enabled remote workforces, phishing attempts increased 350 percent, election security was scrutinized, and events like Black Hat USA were held entirely online. I name “unprecedented” as the word of the year.
Many unknowns remain as we shift to 2021. This time of year is a crucial opportunity for those of us in the cybersecurity field to hit pause and reflect on our industry. Based on conversations and observations in 2020, read on for my eight cybersecurity predictions for 2021 on the topics of:
- Balance between automation and human security testing
- Cybersecurity employment trends
- Cybersecurity budgets and priorities
- Compliance-based security versus risk-based security
- A shift in application security practices
- Tackling insider threats
- Pandemic meets cybersecurity
- Securing the external attack surface
2020: one for the books. We’ve each had to navigate life amid a public health pandemic which has come with its own trials, tribulations and even silver linings. Moreover, it was also a year of tests and new experiences for IT and cyber security professionals: Organizations quickly enabled remote workforces, phishing attempts increased 350 percent, election security is being scrutinized like never before, and events like Black Hat USA were held entirely online. At this point, presumably we can all agree that “unprecedented” should be deemed the word of the year.
No one could have predicted the way this year has played out and many unknowns remain as we shift our mindset to the approaching holiday season, and then to 2021. But, it’s important to remember that this time of year is one of the most crucial opportunities for those of us in the cyber security field to hit pause and reflect as an industry. Based on the conversations and observations I’ve experienced throughout the year, below are my eight cyber security predictions for 2021.
Prediction #1
Automation continues to be a priority, but human context will be the key to security program management and success in 2021.

By now, we all understand the value automation brings to any cyber security tool. Yet, in 2021, the human element will be pushed to the forefront of security innovation, specifically for our intellect and ability to add context to cyber security findings. Contextualizing cyber security findings will be an invaluable tool to boost vulnerability remediation efforts in the new year, as the number of vulnerabilities grows exponentially, and context is key to helping us prioritize.
Prediction #2
There will continue to be more cyber security jobs than people to fill the roles.

Cyber security leaders will be challenged by filling roles that require candidates with mid- to senior- level experience – and entry level job openings will continue to be in high demand. Because of this, companies will need to do more with fewer people. This will result in increased adoption of program-level partnerships with third parties or using vendors to fill in-house positions at scale.
Prediction #3
Cyber security budgets are not necessarily going to increase but will be reprioritized.

More dollars will be specifically allocated to cloud security budgets due to the prolonged and, in many cases permanent, remote work opportunities – in other words, a distributed workforce. One exception to stagnant budgets is regulatory drivers. Certain states [e.g. California] and industries [e.g. healthcare] may need to increase budgets to comply with new or changing regulatory expectations.
Prediction #4
There will be more cyber security teams pivoting from a compliance-based security approach to a risk-based security approach.

Financial institutions will continue leading in risk-based security, but we can expect to see increased adoption in the retail industry. This pivot is being triggered by increased visibility into risks and cyber security programs, better documentation, and more efficient opportunities to present risk to the business leaders.
Prediction #5
“Shift left” will become a more widely adopted term and application security practice in 2021.

Shift left, or the practice to discover and prevent problems earlier in the software development lifecycle (SDLC), will narrow the existing gap between development and cyber security teams. A further proof point: in the cyber security testing community, we are seeing the desire for more certifications in application security. In the new year, we should expect to have more discussions around putting greater emphasis on cyber security throughout the entire SDLC.
Prediction #6
Heightened awareness around insider threats and Identity and Access Management (IAM) will continue growing.

In early 2020, Ponemon Institute found that the frequency of insider incidents had tripled since 2016 and that the average cost of an insider threat was $11.45 million. These numbers will continue rising as threat actors increasingly solicit employees to gain access to an organization’s infrastructure and customer data in 2021. Expect to see more organizations increasing adoption of a zero-trust architecture to address this.
Prediction #7
The rate with which technology is developed continues to outpace security; the pandemic continues to drive this narrative.
The adoption of the cloud coupled with demand for convenience through technology innovation amid the pandemic is going to further increase the rate with which technology is developed. An ever-evolving challenge for the cyber security industry, we will need to ensure new technologies are being built with cyber security top-of-mind.
Prediction #8
Cyber security teams will be challenged by defining and securing the external attack surface in 2020.

As the scope of the perimeter continues to expand well beyond a traditional perimeter defense model, adversaries can now gain access through mobile devices, the cloud, and even user identities (e.g., targeting identities themselves as assets to further gain access to data). Teams will need to think strategically to find and remediate vulnerabilities on the external attack surface as the risk heightens.
[post_title] => 2021 Cyber Security Predictions: A Forecast for the Future [post_excerpt] => 2021 trends: Read on for eight cybersecurity predictions for 2021 from a director of a leading security testing company, NetSPI. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => 2021-cyber-security-predictions-a-forecast-for-the-future [to_ping] => [pinged] => [post_modified] => 2024-04-02 17:36:15 [post_modified_gmt] => 2024-04-02 22:36:15 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=32230 [menu_order] => 451 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [16] => WP_Post Object ( [ID] => 20478 [post_author] => 71 [post_date] => 2020-12-01 07:00:19 [post_date_gmt] => 2020-12-01 07:00:19 [post_content] =>I should have known better.
Eleven-some thousand findings, struggling inexorably to transform from scanner output to csv format. It was too late; the scanner tool was on a mission to dump megabytes of data into a spreadsheet and there was nothing I could do to cancel it.
As I sat there staring at the progress counter slowly creep upward, I questioned my life choices up until that point. I’ve been a security practitioner my entire adult life. I’ve (legally) stolen troves of data in many forms. I’ve discovered untold thousands of vulnerabilities in my penetration testing days, most of which didn’t amount to much; inconsequential findings that did not correlate to any meaningful risk to the organization I was testing. I’ve always weighed more the vulnerabilities I knew would net the golden ring, whether it was unauthorized access to sensitive data, privileged access to a network or system, or whatever prize the vulnerability du jour led to.
And yet there I was, wondering what made me even look for that many vulnerabilities. For some reason I enabled all vulnerability checks in the scanner configuration. The scanner categorized most of the findings as “information,” usually mundane tidbits of data more suited for asset inventories than vulnerability management. Of those 11,000 findings, maybe 25 were categorized as high risk, and maybe a few hundred or so as medium risk. After some threat modeling and other consideration, it turned out there were maybe five relevant vulnerabilities that required prioritized action. All those informational findings? No need to worry about those.
Except one. And man, it was a killer.
It was a simple thing, really. The scanner identified something my team and I had taken great pains to disable long ago. I was confident – arrogantly so! – that it was disabled, so I didn’t bother checking the scanner output to see if it was suddenly active again.
I think you can see where this is going.
It wasn’t until later during an internal audit that I discovered I made the mistake of not propagating my vulnerability management strategy wide enough to encompass a critical process in our security program framework: to periodically validate everything that could have the most adverse effect on the business. Thankfully, it was discovered internally but let’s be honest, nobody enjoys internal auditors finding anything at all, much less something significant.
To be fair, how do you sift through 11,000 findings to determine which are important? You don’t. At least, it certainly isn’t using spreadsheets, arguably the most common method of tracking vulnerabilities. Spreadsheets are the devil. Dumping vulnerability data into them leads to headaches and doesn’t provide the kind of tools needed to manipulate and correlate the data to produce meaningful outcomes in managing the vulnerabilities. And besides, it’s unnecessary. This entire approach is inefficient and ultimately unnecessary.

A Scanner is not the Equivalent of a Vulnerability Management Program
The truth is, many organizations consider vulnerability management to be running a scanner with all the checks turned on, and then addressing the high-risk findings. In my experience, this bottom-up approach presents a few problems:
- Scanner policy configurations are not one-size-fits-all. When set to scan for all possible technology vulnerabilities, the scanner can produce an enormous amount of noise in which meaningful vulnerabilities may be missed or ignored. This “spray and pray” method creates more confusion and eventually apathy toward purposeful vulnerability analysis.
- Similar vulnerabilities can pose drastically different risks. A discovered open share on a file server containing HR data may be categorized by a scanner as medium risk, but the actual risk to the business is high or even critical. A discovered open share on a print controller containing fonts or no files at all may also be categorized as medium risk but in fact is a low risk to the business. Without the proper context an organization may treat these two findings as equal and expend the same time and effort (cost) in addressing both when they do not merit equal treatment.
- Measured improvements in security maturity are an expensive undertaking. The costs in terms of money, time, and effort can skyrocket if guardrails aren’t applied to focus the process on specific goals, otherwise it is a continuous game of catching up each time a vulnerability scan is run.
The key is to understand the risks most likely to disrupt the business from meeting its objectives, identify the threats that would cause and amplify those risks, and select the controls most appropriate for managing those threats. The controls should then be regularly measured and audited to ensure they are implemented correctly and are effective in protecting the organization.
In the next blog in this vulnerability management series, we will look at how to align vulnerability management goals to meet the organization’s business objectives, and present considerations for maturing vulnerability management processes into risk-based program strategy.
[post_title] => What Not to Do When Ingesting and Prioritizing Vulnerability Data for Remediation [post_excerpt] => I should have known better... It was too late; the scanner tool was on a mission to dump megabytes of data into a spreadsheet and there was nothing I could do to cancel it. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => what-not-to-do-when-ingesting-and-prioritizing-vulnerability-data-for-remediation [to_ping] => [pinged] => [post_modified] => 2022-02-15 18:53:45 [post_modified_gmt] => 2022-02-16 00:53:45 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=20478 [menu_order] => 452 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [17] => WP_Post Object ( [ID] => 20466 [post_author] => 71 [post_date] => 2020-11-24 07:00:05 [post_date_gmt] => 2020-11-24 07:00:05 [post_content] =>Making its debut in 2018, the Ryuk ransomware strand has wreaked havoc on hundreds of businesses and is responsible for one-third of all ransomware attacks that took place in 2020. Now it is seemingly on a mission to infect healthcare organizations across the country, already having hit five major healthcare providers, disabling access to electronic health records (EHR), disrupting services, and putting sensitive patient data at risk.
The healthcare industry is surely bracing for what the U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning as, “an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” What can organizations do to preemptively protect themselves? Our recommendation:
- Analyze what makes the healthcare industry a key target for ransomware,
- Educate yourself to better understand Ryuk and TrickBot, and
- Implement proactive cyber security strategies to thwart ransomware attacks and minimize damage from an incident (we’ll get into this more later in this post).
We’ve pulled together this Guide to Ryuk as a resource to help organizations prevent future ransomware attacks and ultimately mitigate its impact on our nation’s healthcare systems.
Why are Healthcare Providers a Target for Ransomware?
Healthcare is widely known as an industry that has historically struggled to find a balance between the continuation of critical services and cyber security. To put this into perspective, doctors and physicians can’t stop everything and risk losing a life if their technology locks them out due to forgetting a recently changed password. So, security, while critically important in a healthcare environment, is more complex due to its “always on” operational structure.
We’ve seen a definite uptick in attention paid to security at healthcare organizations, but there’s much work to be done. The task of securing a healthcare systems is extremely challenging given its scale and complexity, consisting of many different systems and, with the addition of network-enabled devices, it becomes difficult for administrators to grasp the value of security relative to its costs. In addition, third parties, such as medical device manufactures also play a role. Historically, devices in hospitals, clinics, and home-healthcare environments had no security controls, but there has been more of a focus on “security features” as connectivity (network, Bluetooth, etc.) has increased. Yet most healthcare networks are still rife with these sorts of devices that have minimal, if any, built-in security capabilities.
Healthcare is by no means the only target industry: any organization can fall victim to ransomware. Though, healthcare is a prime target for two reasons:
- It’s a gold mine for sensitive data, including social security numbers, payment information, birth certificates, addresses, and more. While monetizing such data may require additional effort on the part of cybercriminals, breaches of such data is a major HIPAA compliance violation that can result in heavy fines and could also potentially have a negative impact to patients if their data is leaked.
- The criticality of the business is as high-risk as it gets. In other words, hospitals cannot afford downtime. Add a public health pandemic to the mix and the criticality increases drastically.
This sense of urgency to get systems back up and running quickly is a central reason why Ryuk is targeting the industry now. Hospitals are more likely to pay a ransom due to the potential consequence downtime can have on the organization and its patients.
Ransomware, Ryuk, and TrickBot:
To understand Ryuk, it is important to first understand ransomware attacks at a fundamental level. Ransomware gains access to a system only after a trojan or ‘botnet’ finds a vulnerable target and gains access first. Trojans gain access often through phishing attempts (spam emails) with malicious links or attachments (the payload). If successful, the trojan installs malware onto the target’s network by sending a beacon signal to a command and control server controlled by the attacker, which then sends the ransomware package to the Trojan.
In Ryuk’s case, the trojan is TrickBot. In this case, a user clicks on a link or attachment in an email, which downloads the TrickBot Trojan to the user’s computer. TrickBot then sends a beacon signal to a command and control (C2) server the attacker controls, which then sends the Ryuk ransomware package to the victim’s computer.
Trojans can also gain access through other types of malware, unresolved vulnerabilities, and weak configuration, though, phishing is the most common attack vector. Further, TrickBot is a banking Trojan, so in addition to potentially locking up the network and holding it for ransom, it may also steal information before it installs the ransomware.
How does an organization know if they have fallen victim to ransomware, more specifically Ryuk? It will be obvious if Ryuk has successfully infiltrated a system. It will take over a desktop screen and a ransom note will appear with details on how to pay the ransom via bitcoin:
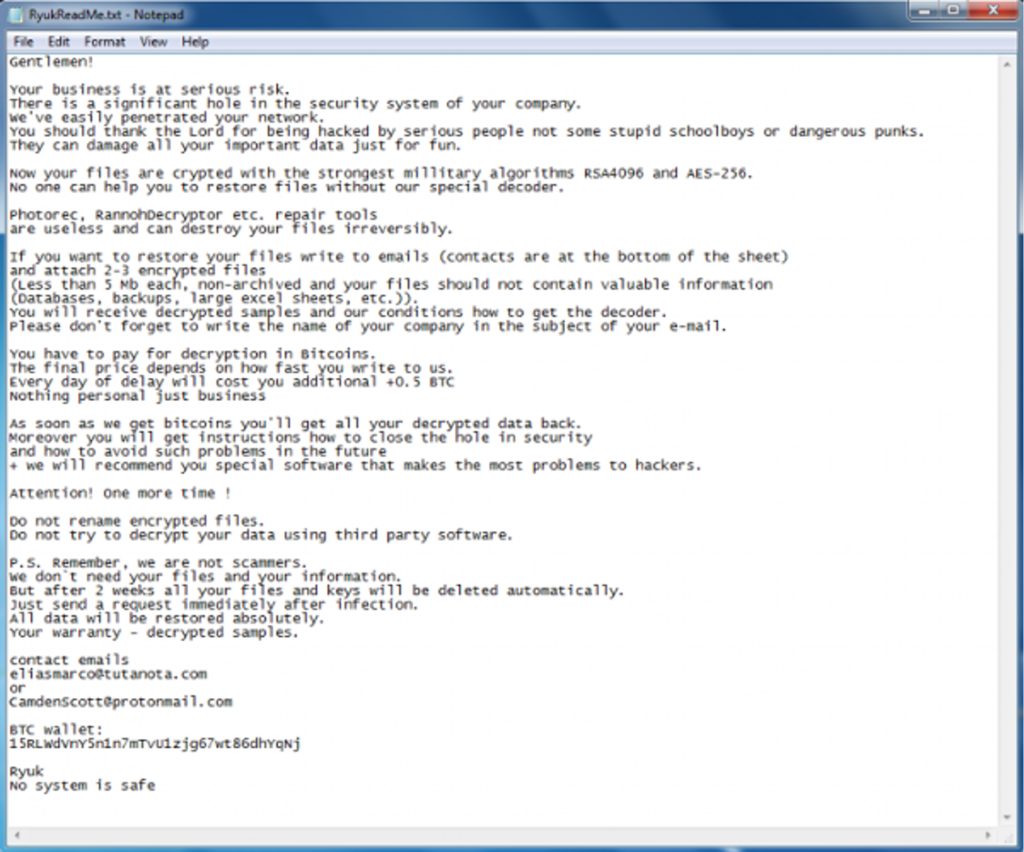
An early warning sign of a ransomware attack is that at the technical level, your detective controls, if effective, should alert to Indicators of Compromise (IoC). Within CISA’s alert, you can find TrickBot IoCs listed along with a table of Ryuk’s MITRE ATT&K techniques.
A threat to the increasing remote workforce: In order to move laterally throughout the network undetected, Ryuk relies heavily on native tools, such as Windows Remote Management and Remote Desktop Protocol (RDP). Read: COVID-19: Evaluating Security Implications of the Decisions Made to Enable a Remote Workforce
Implementing Proactive Cyber Security Strategies to Thwart Ransomware Attacks
We mentioned at the start of this post that one of the things organizations can do preemptively to protect themselves is to put in place proactive security strategies. While important, security awareness only goes so far, as humans continue to be the greatest cyber security vulnerability. Consider this: In past NetSPI engagements with employee phishing simulations, our click-rates, or fail-rates, were down to 8 percent. This is considered a success, but still leaves open opportunity for bad actors. It only takes one person to interact with a malicious attachment or link for a ransomware attack to be successful.
Therefore, we support defense-in-depth as the most comprehensive strategy to prevent or contain a malware outbreak. Here are four realistic defense-in-depth tactics to implement in the near- and long-term to prevent and mitigate ransomware threats, such as Ryuk:
- Revisit your disaster recovery and business continuity plan. Ensure you have routine and complete backups of all business-critical data at all times and that you have stand-by, or ‘hot,’ business-critical systems and applications (this is usually done via virtual computing). Perform table-top or live disaster recovery drills and validate that ransomware wouldn’t impact the integrity of backups.
- Separate critical data from desktops, avoid siloes: Ryuk, like many ransomware strands, attempts to delete backup files. Critical patient care data and systems should be on an entirely separate network from the desktop. This way, if ransomware targets the desktop network (the most likely scenario) it cannot spread to critical hospital systems. This is a long-term, and challenging, strategy, yet well worth the time and budgetary investment as the risk of critical data loss will always exist.
- Take inventory of the controls you have readily available – optimize endpoint controls: Assess your existing controls, notably email filtering and endpoint controls. Boost email filtering processes to ensure spam emails never make it to employee inboxes, mark incoming emails with a banner that notifies the user if the email comes from an external source, and give people the capability to easily report suspected emails. Endpoint controls are essential in identifying and preventing malware. Here are six recommendations for optimizing endpoint controls:
- Confirm Local Administrator accounts are strictly locked down and the passwords are complex. Ensure Domain Administrator and other privileged accounts are not used for routine work, but only for those tasks that require admin access.
- Enable endpoint detection and response (EDR) capabilities on all laptops and desktops.
- Ensure that every asset that can accommodate anti-malware has it installed, including servers.
- Apply all security patches for all software on all devices. Disable all RDP protocol access from the Internet to any perimeter or internal network asset (no exceptions).
- Test your detective controls, network, and workstations:
- Detective control testing with adversarial simulation: Engage in a purple team exercise to determine if your detective controls are working as designed. Are you able to detect and respond to malicious activity on your network?
- Host-based penetration testing: Audit the build of your workstations to validate that the user does have least privilege and can only perform business tasks that are appropriate for that individual’s position.
- Internal network penetration testing: Identify high impact vulnerabilities found in systems, web applications, Active Directory configurations, network protocol configurations, and password management policies. Internal network penetration tests also often include network segmentation testing to determine if the controls isolating your crown jewels are sufficient.
Finally, organizations that end up a victim to ransomware have three options to regain control of their systems and data.
- Best option: Put disaster recovery and business continuity plans in motion to restore systems. Also, perform an analysis to determine the successful attack vector and remediate associated vulnerabilities.
- Not advised: Pay the ransom. A quick way to get your systems back up and running, but not advised. There is no guarantee that your business will be unlocked (in fact, the offer may also be ransomware), so in effect you are funding adversarial activities and it’s likely they will target your organization again.
- Rare cases: Cracking the encryption key, while possible with immature ransomware groups, is often unlikely to be successful. Encryption keys have become more advanced and require valuable time to find a solution.
For those that have yet to experience a ransomware attack, we encourage you to use the recent Ryuk news as a jumping point to future-proof your security processes and prepare for the inevitability of a breach. And for those that have, now is the time to reevaluate your security protocols.
[post_title] => Healthcare’s Guide to Ryuk Ransomware: Advice for Prevention and Remediation [post_excerpt] => Making its debut in 2018, the Ryuk ransomware strand has wreaked havoc on hundreds of businesses and is responsible for one-third of all ransomware attacks that took place in 2020. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => healthcares-guide-to-ryuk-ransomware-advice-for-prevention-and-remediation [to_ping] => [pinged] => [post_modified] => 2021-05-04 17:06:19 [post_modified_gmt] => 2021-05-04 17:06:19 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=20466 [menu_order] => 454 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) ) [post_count] => 18 [current_post] => -1 [before_loop] => 1 [in_the_loop] => [post] => WP_Post Object ( [ID] => 27771 [post_author] => 71 [post_date] => 2022-05-14 10:41:00 [post_date_gmt] => 2022-05-14 15:41:00 [post_content] =>On May 14, 2022, NetSPI's VP of Strategic Solutions, Florindo Gallicchio, was featured in the Digital Journal article called Safeguarding Data from Dangerous Threats like Ryuk. Preview the article below, or read the full article online.
To maintain business continuity, each organization should develop a data protection and back-up strategy. To reduce the risk of data loss, firms need to back up files and databases. Firms will also want to back up their operating systems, applications, configuration. This ensures the protection of data from unauthorized access and data corruption throughout its lifecycle.
According to Florindo Gallicchio, Managing Director, Head of Strategic Solutions at NetSPI: “It’s time to acknowledge how critical data backup has become, especially since many ransomware strains attempt to delete backup files, as we witnessed with Ryuk.”
Ryuk is a type of ransomware known for targeting large, public-entity Microsoft Windows cybersystems. Here, the threat actors make sure that essential files are encrypted so they can ask for large ransom.
Expanding on the risks faced by the corporate sector, Gallicchio says: “Most businesses are faced with two significant risks when it comes to backups: the theft and public disclosure of sensitive data, and the disruption of critical business functions.”
In terms of the consequences, Gallicchio says: “If either of these risks occur, organizations could endure devastating consequences. To make sure that doesn’t happen, organizations need to proactively put strategies in place to bolster protection against these threat actors.”
Read the full article online.
[post_title] => Digital Journal: Safeguarding Data from Dangerous Threats like Ryuk [post_excerpt] => On May 14, 2022, NetSPI's VP of Strategic Solutions, Florindo Gallicchio, was featured in the Digital Journal article called Safeguarding Data from Dangerous Threats like Ryuk. [post_status] => publish [comment_status] => closed [ping_status] => closed [post_password] => [post_name] => digital-journal-safeguarding-data-from-dangerous-threats-like-ryuk [to_ping] => [pinged] => [post_modified] => 2023-01-23 15:10:38 [post_modified_gmt] => 2023-01-23 21:10:38 [post_content_filtered] => [post_parent] => 0 [guid] => https://www.netspi.com/?p=27771 [menu_order] => 270 [post_type] => post [post_mime_type] => [comment_count] => 0 [filter] => raw ) [comment_count] => 0 [current_comment] => -1 [found_posts] => 18 [max_num_pages] => 0 [max_num_comment_pages] => 0 [is_single] => [is_preview] => [is_page] => [is_archive] => [is_date] => [is_year] => [is_month] => [is_day] => [is_time] => [is_author] => [is_category] => [is_tag] => [is_tax] => [is_search] => [is_feed] => [is_comment_feed] => [is_trackback] => [is_home] => 1 [is_privacy_policy] => [is_404] => [is_embed] => [is_paged] => [is_admin] => [is_attachment] => [is_singular] => [is_robots] => [is_favicon] => [is_posts_page] => [is_post_type_archive] => [query_vars_hash:WP_Query:private] => 6fed9ad02d57ae2275f882f4f465613d [query_vars_changed:WP_Query:private] => [thumbnails_cached] => [allow_query_attachment_by_filename:protected] => [stopwords:WP_Query:private] => [compat_fields:WP_Query:private] => Array ( [0] => query_vars_hash [1] => query_vars_changed ) [compat_methods:WP_Query:private] => Array ( [0] => init_query_flags [1] => parse_tax_query ) )