Month: November 2021
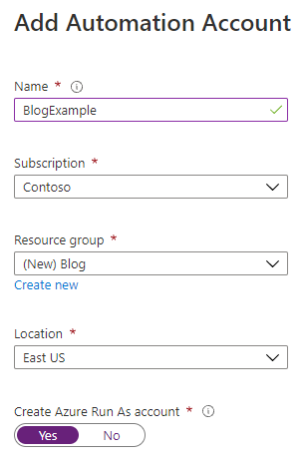
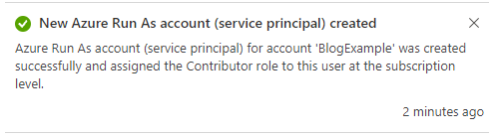
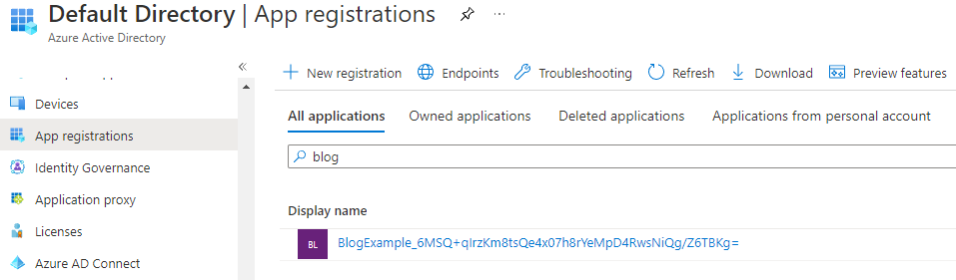
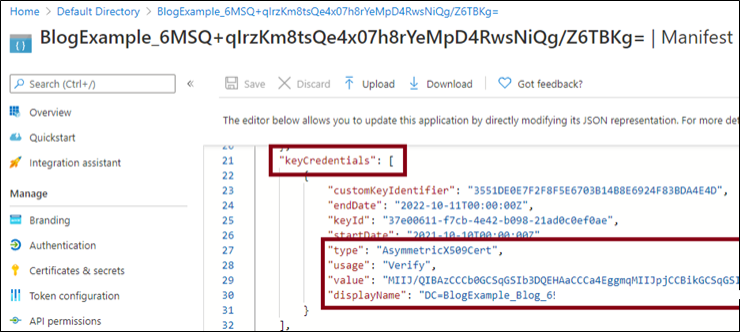
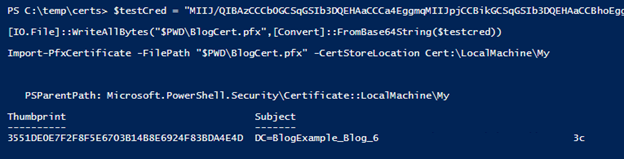
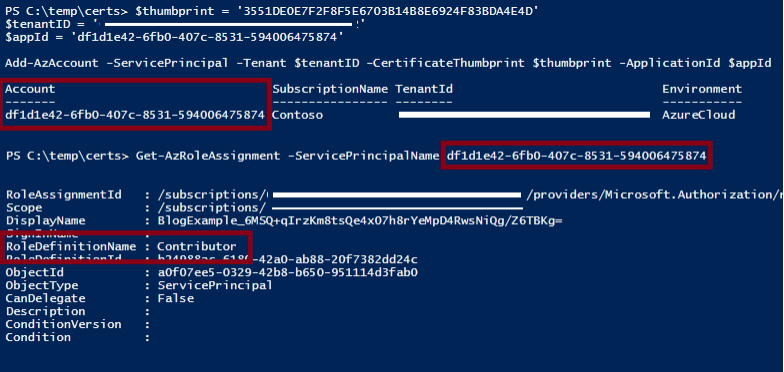
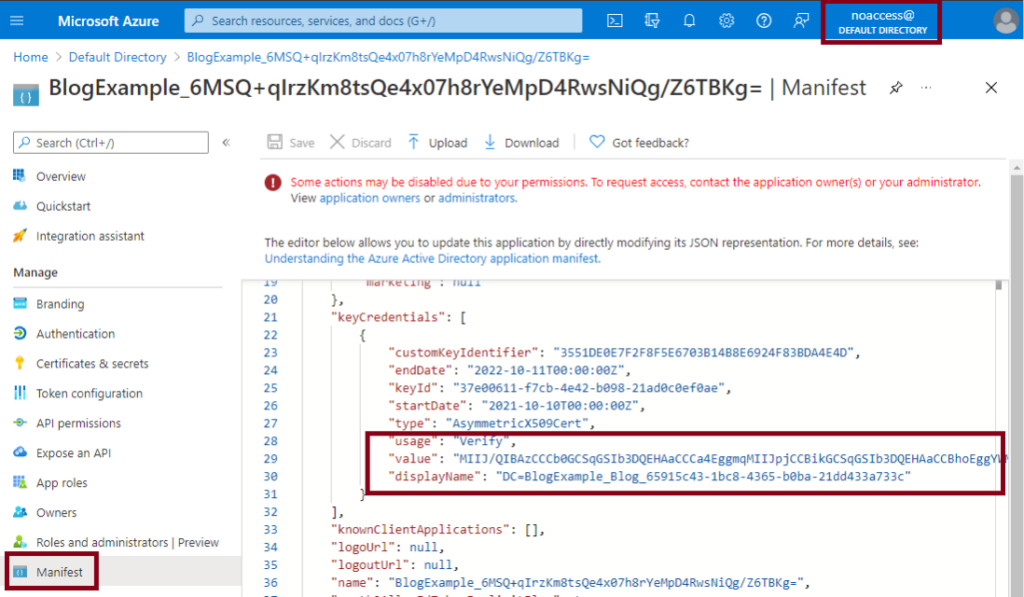
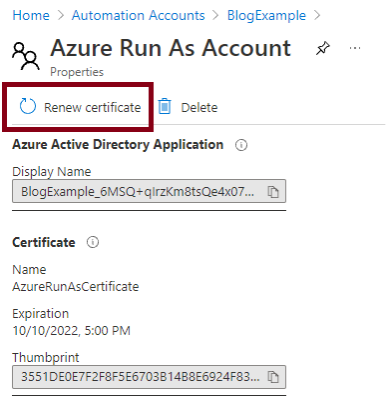
CVE-2021-42306 CredManifest: App Registration Certificates Stored in Azure Active Directory
Recent Posts
Q&A: Asset Management, Vulnerability Management, and Authentication are Changing the Game for this CISO
The number of security controls and activities any given cybersecurity leader manages is continuously evolving. For instance, this year, the Global InfoSec Awards features 212 different categories – from penetration testing to insider threat detection to breach and attack simulation. That’s 212 different technologies or security activities CISOs could be implementing dependent on their needs.
This highlights the importance of taking a step back to recognize the activities making the greatest difference in your security program. AF Group CISO Seth Edgar does just that during our Agent of Influence podcast interview. For Seth, asset management, vulnerability management, and authentication topped his list of cybersecurity best practices.
Continue reading to learn how these security activities are changing the game for Seth and for highlights from our discussion around his unconventional career path, lessons learned from reverse engineering, and cyberattack trends in the insurance space. For more, listen to the full episode on the NetSPI website, or wherever you listen to podcasts.
What have you learned from your experience as a middle school teacher that you apply to your role as a CISO?
Middle school is an area of your life that’s memorable for a lot of reasons. As a teacher, delivering materials to students in a manner they can consume is an ever-changing battle. Not only is there the struggle to remain interesting and relevant to a roomful of 12-year-olds, but also understanding how to communicate a complex subject or introduce a new, complex theme. I couldn’t stop at relaying the information. “I’ve put it out there, now it’s on you to consume,” was not an effective strategy. I had to make sure that the concepts were reinforced and delivered in a manner they could grasp because my goal was for them to be successful.
As CISO, I’m doing the exact same thing. Most of my job is education and a portion of my job is security, budget, and people management. I’m teaching people why security is important. What is higher or lower risk. I’m talking to executives and communicating the ROI of security. In doing so, I have to gauge on the fly whether they’re tracking with what I’m saying, or whether we’re going to need to revisit the topic from a different angle.
I get exposure to upper-tier leadership within my organization, but those interactions are limited. They have to be because they’re scheduled. It’s not like a classroom where I’m with the students every single day. If we missed it today, we’ll get it tomorrow – same time, same place. With business leaders I’ve got to get it right the first time.
Just like in a classroom, you have to get to know the students before you can truly teach them. And at the end of the day, you must make your material relevant and usable for them, make it understandable and draw upon their background. It must also be presented in a manner that makes sense, without oversimplification. All those techniques are exactly what I’m doing right now as a CISO, just with a different body of knowledge. Finding that the balance between simplification and understanding is a challenge, but it’s something that I can draw upon from my prior experience and from my undergraduate education to help me communicate complex security topics clearly to my leadership team.
Are there components of what you learned from reverse engineering that you apply in practice today?
I am a big fan of learning by doing. It’s way different completing a sample problem than it is touching real software. It is helpful to have a deep technical background to be able to have conversations with technical folks and establish credibility. However, the more important lesson that I pulled from those early days doing reverse engineering is that it’s okay to have trial and error. It’s okay to make mistakes and learn from them.
As a leader, I don’t punish mistakes, we learn from them. If that mistake is repetitive, I’m likely going to move you away from doing that that role within our organization. But mistakes are part of the learning process. They’re important. We too often think, ‘I’m not going to do anything because if I screw it up, I’m going to get in trouble.’ That’s not how we learn, that’s not the way that systems are developed, and it’s certainly not the way you have a breakthrough. So, the most important lesson I learned from reverse engineering was learning how to make a mistake, recover, and use it to inform the next steps going forward.
There’s been a lot of news recently about the insurance space, such as the CNA Financial ransomware attack. Are there certain attack trends that you’re paying close attention to today?
We are watching a lot right now. Ransomware is a high risk and a top-of-mind issue, not only from a perspective of ransomware prevention, but also from an insurance perspective. We don’t touch this area much in my role, but cybersecurity insurers are starting to realize that their model may need to change because the risk profile has ramped up significantly. If you look at how ransomware has grown, we have seen this crazy upward trend in financial impact and sophistication – nobody wants to get hit. At the same time, if it is not going to happen to you, it is very likely will happen to a third- or a fourth- or a fifth-party provider. That’s where supply chain security issues come into play.
With COVID-19, many went from a fully on premise workforce to a fully remote workforce almost overnight. There are inherent network risks and security models that bank on a perimeter-centric security. There’s a large knowledge exchange that had to happen with groups of people who always report into a building that have maybe never used a VPN or had to do any kind of multifactor authentication before, whereas other people have been doing it for a decade or more. There’s going to be that subset of your users that this is the first rodeo they’ve ever had with remote workforce security protocols.
We’ve seen interesting scams arise out of this. Wire fraud transfer scams have always been existent but are taking advantage of companies that have changed business models. Attackers try and monetize whatever it is they get their hands on. If I’m an attacker, if I compromise an email account, I want to turn that into some sort of monetization as quickly as possible.
There is one clever attack that I’ve heard described among my peers. Let’s say I compromise a mailbox and immediately search for the word “invoice” looking for unpaid invoices. I find out who the sender of that invoice is and create a look alike domain for that sender. Now I spoof that exact user that sent the invoice in the first place and say, “This invoice is overdue and needs to be paid.” It creates that sense of urgency just like a normal attack would and then, you get them to change the wire transfer number. Now they’re stuck in a position where they’re trying to describe a decently complex attack to probably an under resourced small- to medium-sized business.
Many organizations don’t have the capability to view and understand how the user got into their environment and it becomes a game of finger pointing. It’s an awkward and difficult situation to be in. This brings up the importance of validating senders and sources. A positive business best practice in this situation would be to reach out and validate the information with a verified contact.
What are the most effective security activities you’re implementing today?
The most effective security activities that are changing the game for me have revolved around strong asset management, patching, and vulnerability management practices.
Beyond that, having strong authentication is equally critical. Not only multifactor, but checking system state, user agent strings, consistent source IP, and similar practices. I can know, with relatively simple rule set, whether a log in is attempted with a new IP, device, or if it is a new source for this user’s authentication, and act accordingly. We’ve seen some incredible progress, just not only in our own development or tooling, but leveraging products we already have available. They’re not perfect, none of them are airtight. But it gives us a certain probability or a reasonable level of assurance that this user is who they claim to be – or not.
As mentioned earlier, moving your workforce to remote is a hard problem to solve in areas like vulnerability remediation and patch management. Getting software updated, especially if it was historically on-premise, is a major shift. If you’re working with an incomplete asset inventory right out of the gate, you have no indication what your success ratio is. This is an age-old problem that organizations still struggle with today. Whether you have good asset management can tell you whether your security program is successful.
The bright side? Vulnerability management and asset management are areas that can be improved and understanding your attack surface is a good first step. The Print Nightmare vulnerability is a great example of this. Once alerted, having a good understanding of the devices that need to get print drivers locked down on and what devices you need to make changes to rapidly reduce your exposure proved vital in that situation.

Recent Posts
VMblog.com: 6 Tech Leaders Share their Outlook on the Great Resignation and how to React
On November 11, 2021, NetSPI COO Charles Horton was featured in an article written by David Marshallfor VMblog.com. Read the full article below or online here.
Seventy-two percent of tech/IT workers are considering quitting their job in the next year. This shortage is leaving some business leaders uncertain and anxious. Below, you will find commentary from 6 leaders from various technology companies such as Raytheon, Ease, and Fuze, among others. They offer insights on trends they are seeing at their own companies as well as advice to navigate or mitigate future issues.
++
Sandra Slager, COO, Mindedge Learning
“Work location flexibility is the biggest paradigm shift of the pandemic for technical professionals and technology companies alike. Companies who have made this shift have likely built the communications and systems infrastructure to cast a nationwide net in their search for top talent. Similarly, talented tech workers-engineers, cybersecurity security experts, programmers, and the like- can extend their job hunt to more cities. To keep top talent, work location flexibility sits as the foundation. Companies must also be prepared to layer on competitive wages and bonuses, but also a corporate culture that genuinely cares about staff well-being which manifests in any number of benefits such as generous vacation time, paid family leave, and even tuition reimbursement.”
Jon Check, Senior director of cyber protection solutions, Raytheon Intelligence & Space
“Given the current climate, we should not be surprised by the high resignation rates we’re seeing in the technology sector. The gap within the cybersecurity industry is especially clear; there’s a shortage in the workforce, which means that many people are being stretched thin and expected to wear multiple hats- and maybe more than they can handle. This leads to feelings of burnout and dissatisfaction. With a market that is now favoring employees, people are going to look for new opportunities that offer more benefits and a better work-life balance.
I coined the term Cyberlandia as the ideal workplace culture within cybersecurity teams, where operations are at the optimum state of cyber readiness, with happy team members who feel empowered to face whatever threats they encounter. However, we can only make employees happy if everyone’s thoughts are valued and voice is heard, only then will we truly start to deliver what they need to thrive. Technology leaders should be opening two-way communication lines so that employees feel comfortable voicing their opinion on what needs to shift: team structure, changes to work schedules, training opportunities – and the list could go on.
We also need to react to the great resignation by looking for talent where we have failed to in the past, to both close the talent gap and diversify the workforce. Women and minorities currently underrepresented in cybersecurity positions. To combat this, technology companies can offer tuition reimbursement, scholarships, and student loan repayment programs as a tangible way to make sure that individuals of all backgrounds can help us fill the technology shortage that will continue to grow unless we create a more welcoming, inclusive and flexible workplace culture.”
Stephen Cavey, Co-founder, Ground Labs
“The great resignation poses a significant challenge to many organizations, but in particular, to technology companies, especially IT and cybersecurity teams. These organizations are already challenged to stay abreast of the latest trends and threats, not to mention ensuring an organization’s defenses are maintained. Often, these expectations and pressures leave IT and security teams feeling overwhelmed.
We are seeing major digitization efforts happening across technology companies in tandem with the “Great Resignation.” Within most teams, there are manual tasks that can be completed more efficiently with innovations in automation and improved workflow. To help alleviate employee burnout, leaders should ask: Have I done everything in my power to make my employees’ work life better? Acknowledging the situation and taking steps to better understand and improve your team’s workload is a critical first step to holistically address potential burnout that may be happening. In addition to helping employees manage workload, tech leaders should check in with employees to confirm whether they feel they have enough training, mentorship and support to succeed.
With the pandemic still in motion, leaders must also take into consideration employees’ personal wellbeing. Do all employees work in a role where they need to be measured on the basis of a 9 to 5 workday? Could you evaluate them on their deliverables and the quality of their work – and openly offer flexibility and let them know it’s ok if they need to take time to care for themselves or someone else. In this new remote by default world, being proactive in looking out for your team is not only critical for their wellbeing but might just help reduce the likelihood of your team being impacted by the Great Resignation that is happening at present.”
Mari Kemp, SVP of HR, Ease
“The 2021 talent market is ten times more competitive than it was a year ago and we’ve seen bargaining power shift from employers to employees. employees are winning. This is the first time in decades we’ve seen employees have power over their employers and the results are astounding. Employees are demanding more from their employers in terms of benefits, work-life balance, and culture. Employers can no longer dictate that their staff return to the in-office setting, and those that do risk losing employees.
Furthermore, the Great Resignation has drastically changed the way companies handle recruitment, onboarding, retention, and off-boarding. Moving forward, recruitment efforts will become more reliant on internal networks and may increase referral bonuses, in addition to increased marketing and branding efforts. As for onboarding, retention, and off-boarding, companies will need to welcome employee engagement and stay close to their people emotionally instead of physically. By meeting with departments individually, conducting employee surveys, and utilizing available employee data, companies can understand why employees are staying or leaving. Additionally, employee data such as age and demographics can aid in retention as it provides a snapshot of how to adjust current healthcare and benefit options.
Wellness in the workplace will be a major issue for companies in 2022, a recent Microsoft study showed that the average American’s work week has gotten 10% longer during the pandemic. To combat burnout, companies need to encourage employees to create boundaries and a better work-life balance. Additionally, managers and department heads alike need to ensure that they are not rewarding employees that are failing to create these boundaries.”
Charles Horton, COO, NetSPI
“The Great Resignation we’re seeing across the country has underscored a growing trend spurred by the COVID-19 pandemic: employees will leave their company if it cannot effectively meet their needs or fit into their lifestyle. While many are turning to innovative technologies to drive growth and retain employees, this effort alone will not solve the problem at-hand. Talent is now a business’ main asset, and corporate leadership must invest in it accordingly.
First, invest in entry level employees. With the Great Resignation pulling talent to new companies and new career paths, it’s more important than ever for companies to build a strong pipeline of emerging talent that can grow within the company, and in turn, keep retention rates high. Since security is a complex and sometimes challenging field to break into, organizations should develop entry level training programs that lower the barriers to entry and set junior employees up for long term success within the company.
Second, organizations must adjust their cultural mindset. While the tech and cybersecurity industries have historically been individual sports, companies win as teams, and they must operate as so. Department heads should foster a culture that’s built on principles like performance, accountability, caring, communication, and collaboration. Once this team-based viewpoint is established, employees will take greater pride in their work, producing positive results for their teams, the company and themselves – ultimately driving positive retention rates across the organization.”
Brian Day, CEO, Fuze
“As the Great Resignation continues, employees are seeking opportunities that provide more flexibility. A recent survey showed that 75% of all workers believe flexible work should be a standard practice, not a benefit, and 67% would consider finding a new job for greater flexibility.
Technology companies should be thinking about how to transform into employee-first organizations in order to both attract and retain talent. At Fuze, I’m continuing to give my employees the choice to dictate their own schedules and encourage our global workforce to remain working from home if that’s what’s best for them. In addition, we are taking an intentional laggard approach to our office re-opening, and are slowly re-opening each regional office based on local guidance and vaccination rates. While the Great Resignation remains a challenge, business leaders must realize that when they establish work-from-home policies, employees’ preferences and feelings go hand-in-hand with that process. When employees’ priorities are taken into consideration, businesses can avoid the impacts of a second wave of the “Great Resignation” and maintain an overall happier and engaged workforce, while also driving better business results.”
Recent Posts
Gartner Hype Cycle for Security Operations: Key Considerations When Selecting Your PTaaS Partner
We’re excited to announce that NetSPI was named as a key Penetration Testing as a Service (PTaaS) vendor in Gartner’s Hype Cycle for Security Operations, 2021. In the report, PTaaS was named an Innovation Trigger, with the technology-enabled service categorized as a “breakthrough” that “generates significant media and industry interest.” At NetSPI, our unique approach to PTaaS allows us to deliver a more specialized offering to customers than our peers in the space.
This report comes at a pivotal time where more organizations are beginning to understand the importance penetration testing plays in their overall cybersecurity strategy. For organizations looking at PTaaS solutions, it can be difficult to assess which solutions fit which needs, and what factors require careful consideration. Fortunately, Gartner’s report (in tandem with this article) can help business leaders and security practitioners better understand the PTaaS market and what the right solution can do for their organizations.
What is PTaaS?
PTaaS refers to enterprise security testing that is delivered through a technology platform. This tech-enabled approach combines traditional manual penetration testing techniques and the use of advanced technologies to detect vulnerabilities more efficiently and effectively, while delivering a modern, SaaS-like experience to end users. According to Gartner’s hype cycle analysis, PTaaS offers many benefits, providing “point-in-time and continuous application and infrastructure pentesting services which traditionally relied on human pentesters using commercial/proprietary tools.” With costly cyber-attacks increasing in prevalence, the importance of understanding and addressing cyber risk is greater than ever, making PTaaS a core component of enterprise attack surface management.
While penetration testing services themselves aren’t new, it is only recently that the industry has begun enabling penetration testing through software as-a-service (SaaS) platforms. Gartner lists the following as the top PTaaS penetration testing delivery model benefits:
- Faster scheduling and execution
- Real-time communications with testers
- Visibility of test results
- Workflow automation via tool integrations (DevOps, ticket management)
- Access to a large pool of testers with specific subject-matter expertise
- An outcome-driven approach
Bug Bounty vs. Traditional Pentesting vs. PTaaS
Just like all security testing approaches are not equal, all PTaaS providers aren’t equal either. When you look at the security testing industry as whole, we see 3 primary ways to leverage a third party for penetration testing from a manual perspective:
- PTaaS
- Traditional penetration testing
- Bug bounty
Many large programs will run a combination of testing from multiple sources. It is typical to see an enterprise use their internal testing team, bug bounty programs, and external/third party pentesting providers. This is where understanding the difference between PTaaS solutions and traditional penetration testing becomes important.
NetSPI is the only PTaaS provider rooted in traditional penetration testing. But because we are technology-driven, our customers receive all the PTaaS benefits Gartner identified that other traditional testing firms cannot offer. Most PTaaS providers are technology-driven, like NetSPI, but leverage a talent pool that consists of independent contractors (often “security researchers”), versus NetSPI which leverages vetted full-time employees.
Let’s put aside the fact that is it difficult to validate the motives and ethics of your pentesting team when they are not vetted as thoroughly as full-time employees are. The biggest challenge with bug bounty PTaaS programs is that service, quality, project management, and other key methodology factors often lack consistency. And with pentesting, consistency is key.
From our conversations within the industry, we’ve heard there are major gaps in completeness of PTaaS assessments that leverage a pool of independent contractors. The level of effort wanes as the rewarding, critical vulnerabilities are found, and researchers tend to move on to opportunities with greater opportunity for compensation. For organizations that need to show consistency and completeness, bug bounty driven PTaaS programs leave a lot to be desired. Add to this, the issue of bench depth and expertise limitations, and it becomes clear that you cannot build an enterprise testing program based around a self-service PTaaS model dependent on independent contractors.
Sound like somewhere you’d like to work? We’re hiring! Visit https://www.netspi.com/careers/ to learn more.
Considerations for Assessing PTaaS Solutions
As with any emerging technology or service, researching the various offerings in the market and deciding upon the right one can feel like a daunting task. To this effect, the Gartner report offers criteria prospective buyers can use to understand which PTaaS solution best meets their needs.
Pulling from Gartner’s criteria list and my personal experience in the pentesting space, here are five things business and security leaders should consider when evaluating PTaaS vendors:
- Evaluate whether your organization needs a vulnerability assessment exercise or penetration testing exercise: Both the services may appear similar at first glance, however there are significant differences in cost and deliverables. The vast majority of critical severity findings are found through human effort. Many providers will tell you they will run a pentest, but they just run scans on your environment, which will produce a lot of lower-level findings and noise, but it will not find the critical vulnerabilities that proper and sophisticated penetration testing through an expert will produce.
- Identify and evaluate the pentesting requirements that PTaaS vendors will be able to fulfill: PTaaS is well-aligned to application pentesting and external infrastructure testing. However, not all vendors can effectively scale to meet the needs of enterprise organizations, or provide the ongoing hands-on collaboration needed to effectively deter and manage vulnerabilities. This is where NetSPI’s traditional methodologies delivered through PTaaS help the most. Running tests through any organization is complicated and requires a high-level of communication and support. Many other PTaaS providers, offer a self-service model that doesn’t scale properly in an enterprise environment.
- Prioritize compliance and quality: Knowing compliance will remain a driving factor for pentesting programs, business leaders should select a PTaaS provider that fulfils all their compliance requirements while also going beyond “checking a box”.
- Seek true partners: No one has time to weed through hundreds of pages of PDFs to understand their organization’s current threat environment. Instead, look for PTaaS players that provide customized and tailored guidance throughout the lifecycle of their service. NetSPI’s PTaaS solution allows customers to login and see steps to remediation and instructions to re-create all vulnerabilities we identified during each engagement. A static PDF cannot offer that level of granularity or insight.
- Know what is important to your organization: Every company has unique challenges. The better your PTaaS provider understands the goals you are looking to accomplish and why, the better results you will see.
Final Words
PTaaS solutions are not one size fits all. Some might offer features that won’t be relevant to the specific or strategic needs of your organization, while others might have blind spots that will end up leaving your organization vulnerable.
In general, business and security leaders considering PTaaS solutions as a core component of their security program should seek those providers that offer a platform-driven approach with a well-organized team of subject matter experts driving the testing and execution of every engagement.
They should also look for solutions which offer flexible options for testing, which can be catered and scaled to meet their specific and strategic needs. By following the guidance here and in the Gartner Hype Cycle for Security Operations report, organizations will be well on their way to better and more efficient security outcomes.

For additional help and criteria to consider, download our guide: How to Choose a Penetration Testing Company.
Recent Posts
TechRepublic: US government orders federal agencies to patch 100s of vulnerabilities
On November 4, 2021, NetSPI Managing Director Nabil Hannan was featured in an article by TechRepublic:
In the latest effort to combat cybercrime and ransomware, federal agencies have been told to patch hundreds of known security vulnerabilities with due dates ranging from November 2021 to May 2022. In a directive issued on Wednesday, the Cybersecurity and Infrastructure Security Agency (CISA) ordered all federal and executive branch departments and agencies to patch a series of known exploited vulnerabilities as cataloged in a public website managed by CISA.
The directive applies to all software and hardware located on the premises of federal agencies or hosted by third parties on behalf of an agency. The only products that seem to be exempt are those defined as national security systems as well as certain systems operated by the Department of Defense or the Intelligence Community.
All agencies are being asked to work with CISA’s catalog, which currently lists almost 300 known security vulnerabilities with links to information on how to patch them and due dates by when they should be patched.
…
Within 60 days, agencies must review and update their vulnerability management policies and procedures and provide copies of them if requested. Agencies must set up a process by which it can patch the security flaws identified by CISA, which means assigning roles and responsibilities, establishing internal tracking and reporting and validating when the vulnerabilities have been patched.
However, patch management can still be a tricky process, requiring the proper time and people to test and deploy each patch. To help in that area, the federal government needs to provide further guidance beyond the new directive.
“This directive focuses on patching systems to meet the upgrades provided by vendors, and while this may seem like a simple task, many government organizations struggle to develop the necessary patch management programs that will keep their software and infrastructure fully supported and patched on an ongoing basis,” said Nabil Hannan, managing director of vulnerability management firm NetSPI.
“To remediate this, the Biden administration should develop specific guidelines on how to build and manage these systems, as well as directives on how to properly test for security issues on an ongoing basis,” Hannan added. “This additional support will create a stronger security posture across government networks that will protect against evolving adversary threats, instead of just providing an immediate, temporary fix to the problem at hand.”
Read the full TechRepublic article here: https://www.techrepublic.com/article/us-government-orders-federal-agencies-to-patch-100s-of-vulnerabilities/